Methods of dealing with DDoS attacks
I would like to talk with you on the topic that is relevant today, namely, about DDoS and methods of dealing with it. Ordinary administrators know what it is, but for most webmasters this abbreviation remains a mystery until they encounter this nuisance on personal experience. So, DDoS is an abbreviation for Distributed Denial of Service (Distributed Denial of Service), when thousands of infected computers send a lot of requests to the server that it later cannot cope with. The purpose of a DDoS attack is to disrupt the normal operation of the server, and in the future - the "fall" of the site or server entirely.
How to protect against this? Unfortunately, universal measures of protection against DDoS attacks still do not exist. It requires an integrated approach that will include measures of hardware, software and even organizational nature.
Software and hardware systems from the network giant Cisco are the most effective, but you have to fork out for them.
')
To protect IIS servers, you can use the (software) solution from Microsoft, but, knowing the generosity of this company, you can guess that they are also not free.
Currently, custom DDoS attacks have turned into a profitable and actively developing network crime niche. Searching in Google, you can find dozens of suggestions from the "experts" to eliminate the site of competitors.
What are the basic principles for protection against DDoS? First of all, you do not need to draw to yourself (your site) the extra attention of the radical public, publishing content that can hurt the racial, national or religious feelings of any individuals.
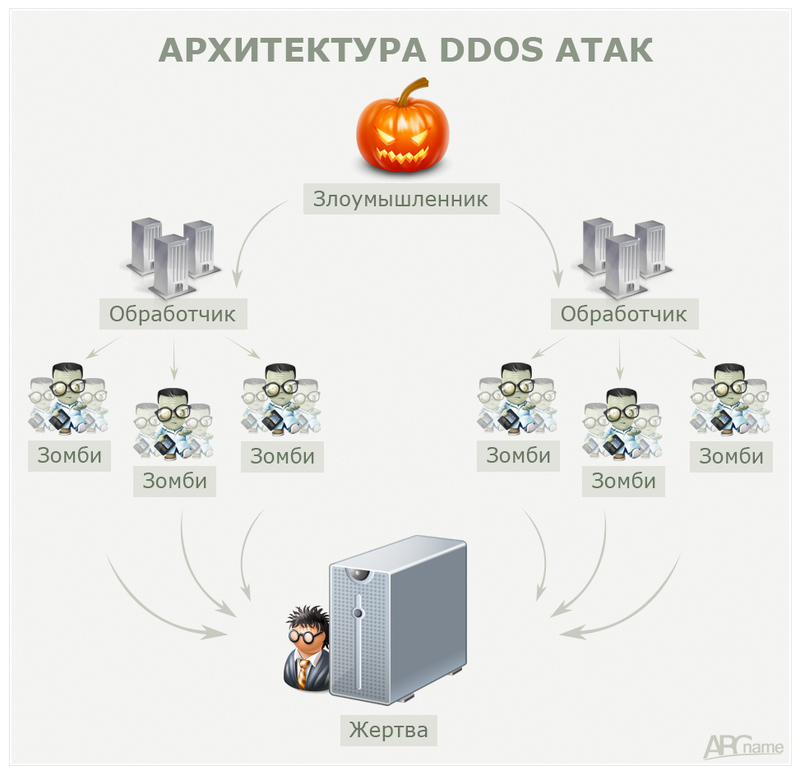
If you are “ordered”, or you have not obeyed the previous advice, beware - the web server's hardware resources must have some performance reserve, and distributed and duplicate systems are built as efficiently as possible. Without an understanding of the principles of DDoS, an effective protection is simply impossible to build. To implement DDoS attacks, a large number of computers infected with malicious code are used. These computers are combined into botnets (“bot-net” - networks of zombie machines), which, on the orders of the attacker, carry out DDoS-attacks, and the owners of computers often do not even suspect it.
We , as a hosting company, encounter DDoS attacks on the websites of our clients every day and have some experience in dealing with them. As mentioned above, there are simply no universal protection measures, but the attack can still be repelled. Suppose that on a certain site (let it be domain.ru) there is a DDoS attack. The logs show that a large number of GET requests go to the main page. In most of these cases, bots can be fooled by using a javascript redirect. For example:
As a result, with each section that is attacked by a GET request directly to the root, the file size will be only a few bytes, which is much better than when a bot comes in contact with a ~ 50-100kb page and at the same time pulls ~ 5-10 SQL queries. The legitimate users who have javascript not disabled in the browser are redirected to index.php.
But there is one big BUT - search bots are also not equipped with js interpreters and, just like attacking bots, will be buried in the js redirect. You can, using such UNIX utilities as tcpdump or netstat, write a small script that will count the number of connections from a specific IP address and ban it.
You can determine the bot, for example, by checking its host. A small example of an elementary IP blocking script that creates many connections to the server (this option was tested on Centos 5.6):
Crond entry
This command creates a list with the number of connections and the IP itself, for example:
10 209.232.223.117
1 209.85.161.191
2 212.113.39.162
1 212.78.78.78
61 213.142.213.19
5 213.151.240.177
1 210.169.67.225
1 216.179.59.97
The script itself, which can be run in a screen or be made daemon:
Let's also look at the Apache settings, which will help avoid some of the problems caused by a DDoS attack.
TimeOut - specify as low a value as possible for this directive (web server that is subject to DDoS attack).
KeepAliveTimeout directive - also need to lower its value or turn it off completely.
It is necessary to check the values of various timeout directives presented by other modules.
LimitRequestBody, LimitRequestFields, LimitRequestFieldSize, LimitRequestLine, LimitXMLRequestBody directives should be carefully configured to limit the resource consumption caused by customer requests.
Make sure you use the AcceptFilter directive (on OSes that support it). By default, it is enabled in the Apache httpd configuration, but for its work it may require rebuilding with the new kernel settings of your OS (* nix, * bsd).
Use the MaxClients directive to specify the maximum number of clients that can be simultaneously connected to the server - by reducing the value of the directive you can reduce the load on the web server.
It can be protected from DDoS at the software level. This will help you free script - DDoS Deflate. With it, you can easily get rid of child flooding and DDoS. The script uses the “netstat” command to detect DDoS and flood, and then blocks the IP addresses of pests using an iptables or apf firewall. But do not relax and assume that weak DDoS will not be able to damage your server. Take, for example, that the attacking zombie machines are only 10-50, but they are all with thick channels, and you, as luck would have it, went on a business trip, or you have dozens (or even hundreds) of servers, and you do not have time physically. ” monitor them all. In this case, even a small number of machines will be able to “flood” the channel or force the Apache web server to fail, mysql, etc. Another thing is when an administrator “monitors” the server around the clock and easily detects attacks. But this is extremely rare, so you need to connect the alarm system, and the process of blocking the attacking zombie machines - to automate.
PS The article was sent to me by the user offic . Questions on the article, recommendations on the following articles and topics and questions of interest, please send to him.
Thanks for attention!
How to protect against this? Unfortunately, universal measures of protection against DDoS attacks still do not exist. It requires an integrated approach that will include measures of hardware, software and even organizational nature.

Software and hardware systems from the network giant Cisco are the most effective, but you have to fork out for them.
')
To protect IIS servers, you can use the (software) solution from Microsoft, but, knowing the generosity of this company, you can guess that they are also not free.
Currently, custom DDoS attacks have turned into a profitable and actively developing network crime niche. Searching in Google, you can find dozens of suggestions from the "experts" to eliminate the site of competitors.
What are the basic principles for protection against DDoS? First of all, you do not need to draw to yourself (your site) the extra attention of the radical public, publishing content that can hurt the racial, national or religious feelings of any individuals.
If you are “ordered”, or you have not obeyed the previous advice, beware - the web server's hardware resources must have some performance reserve, and distributed and duplicate systems are built as efficiently as possible. Without an understanding of the principles of DDoS, an effective protection is simply impossible to build. To implement DDoS attacks, a large number of computers infected with malicious code are used. These computers are combined into botnets (“bot-net” - networks of zombie machines), which, on the orders of the attacker, carry out DDoS-attacks, and the owners of computers often do not even suspect it.
We , as a hosting company, encounter DDoS attacks on the websites of our clients every day and have some experience in dealing with them. As mentioned above, there are simply no universal protection measures, but the attack can still be repelled. Suppose that on a certain site (let it be domain.ru) there is a DDoS attack. The logs show that a large number of GET requests go to the main page. In most of these cases, bots can be fooled by using a javascript redirect. For example:
<script type="text/javascript">
window.location = "domain.ru/index.php"
</script>As a result, with each section that is attacked by a GET request directly to the root, the file size will be only a few bytes, which is much better than when a bot comes in contact with a ~ 50-100kb page and at the same time pulls ~ 5-10 SQL queries. The legitimate users who have javascript not disabled in the browser are redirected to index.php.
But there is one big BUT - search bots are also not equipped with js interpreters and, just like attacking bots, will be buried in the js redirect. You can, using such UNIX utilities as tcpdump or netstat, write a small script that will count the number of connections from a specific IP address and ban it.
You can determine the bot, for example, by checking its host. A small example of an elementary IP blocking script that creates many connections to the server (this option was tested on Centos 5.6):
Crond entry
*/1 * * * * netstat -an | grep tcp | awk '{print $5}' | cut -d: -f1 | sort -n | uniq -c > /var/log/ip.listThis command creates a list with the number of connections and the IP itself, for example:
10 209.232.223.117
1 209.85.161.191
2 212.113.39.162
1 212.78.78.78
61 213.142.213.19
5 213.151.240.177
1 210.169.67.225
1 216.179.59.97
The script itself, which can be run in a screen or be made daemon:
#!/bin/bash
connects=150 <- IP
while read name
do
// - IP
count=`echo $name | awk '{print $1 }'`
// IP
ip=`echo $name | awk '{print $2 }'`
//
hostname=`host $ip`;
// -
if [ "$count" -gt "$connects" ]
then
//, IP
if grep $ip /etc/white.list > /dev/null 2>&1
then
// google ( - )
if echo $hostname | grep "google" > /dev/null 2>&1
then
//
echo "$ip" >> /etc/white.list
echo `date +%H:%M_%d-%m-%Y` $ip "- ADDED TO WHITE LIST AS $hostname SEARCH BOT IP" >> /var/log/ddos_log
else
// -
route add $hostname reject
fi
fi
fi
done < /var/log/ip.listLet's also look at the Apache settings, which will help avoid some of the problems caused by a DDoS attack.
TimeOut - specify as low a value as possible for this directive (web server that is subject to DDoS attack).
KeepAliveTimeout directive - also need to lower its value or turn it off completely.
It is necessary to check the values of various timeout directives presented by other modules.
LimitRequestBody, LimitRequestFields, LimitRequestFieldSize, LimitRequestLine, LimitXMLRequestBody directives should be carefully configured to limit the resource consumption caused by customer requests.
Make sure you use the AcceptFilter directive (on OSes that support it). By default, it is enabled in the Apache httpd configuration, but for its work it may require rebuilding with the new kernel settings of your OS (* nix, * bsd).
Use the MaxClients directive to specify the maximum number of clients that can be simultaneously connected to the server - by reducing the value of the directive you can reduce the load on the web server.
It can be protected from DDoS at the software level. This will help you free script - DDoS Deflate. With it, you can easily get rid of child flooding and DDoS. The script uses the “netstat” command to detect DDoS and flood, and then blocks the IP addresses of pests using an iptables or apf firewall. But do not relax and assume that weak DDoS will not be able to damage your server. Take, for example, that the attacking zombie machines are only 10-50, but they are all with thick channels, and you, as luck would have it, went on a business trip, or you have dozens (or even hundreds) of servers, and you do not have time physically. ” monitor them all. In this case, even a small number of machines will be able to “flood” the channel or force the Apache web server to fail, mysql, etc. Another thing is when an administrator “monitors” the server around the clock and easily detects attacks. But this is extremely rare, so you need to connect the alarm system, and the process of blocking the attacking zombie machines - to automate.
PS The article was sent to me by the user offic . Questions on the article, recommendations on the following articles and topics and questions of interest, please send to him.
Thanks for attention!
Source: https://habr.com/ru/post/129181/
All Articles