Password research
Here I will try to put together and analyze all the information about user passwords on various resources.
The study of Troy Hunt, who took the Sony Pictures user base for his research, is worth noting that all passwords were stored in clear text. And then he analyzed the user passwords. Here are the results he had.
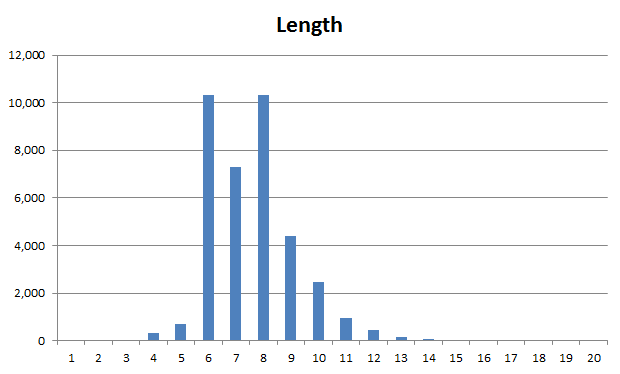
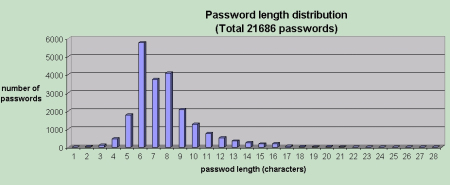
As we can see, the main number of passwords with a length of 6 to 10 characters. In addition, half of it is less than 8 characters.
')
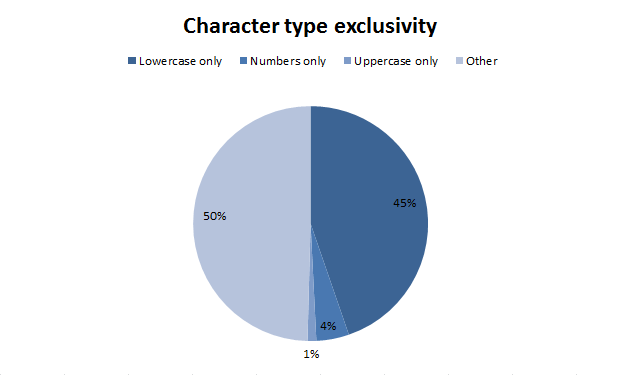
Cryptographic strength of a password is determined by the variation of letters of different registers + numbers + specials. characters ^ password length. In this example, we can observe that the same type of passes are used.
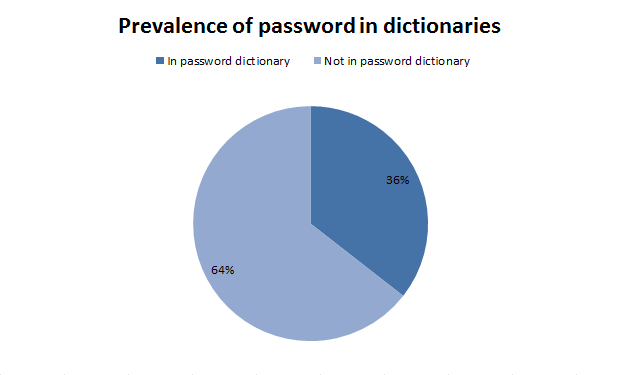
In this test, a dictionary of 1.7 million words was used. You can take it here dazzlepod.com/site_media/txt/passwords.txt As we see the result is disappointing, more than a third of the passes are vocabulary.
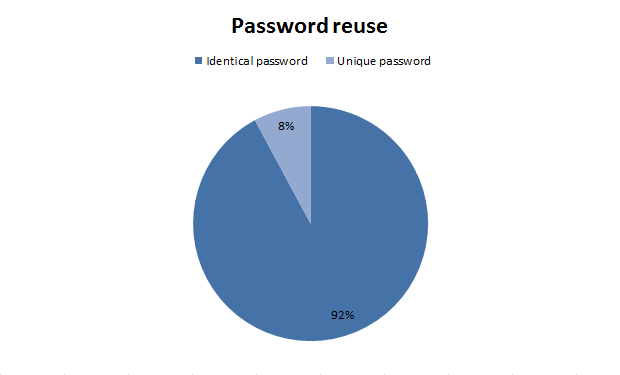
The Sony Pictures database also includes passwords for other services. Actually, the table shows how many users use the same pass everywhere.
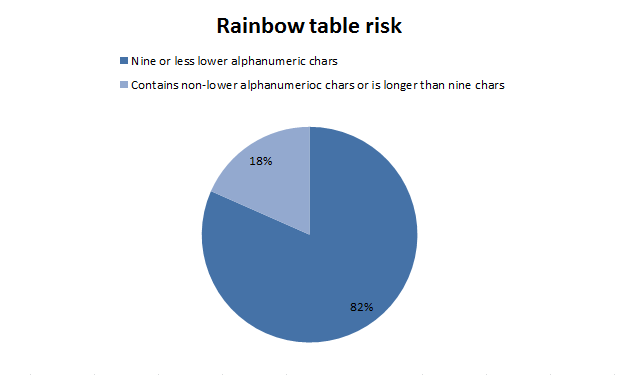
Since all the passwords were stored in clear form, but even if they were hashes, we would be able to decrypt approximately 82% of the total, using rainbow tables.
An independent researcher in the field of information security got into the hands of a list of + 20K accounts from various mailers, like email; pass. The lists are divided into 2 parts, you can take here:
Passwords can not even try to compare, because the whole thing was going to be mixed. Since the goal was not to compromise users, but to analyze the passwords used. Initially, the list consisted of 24,546 entries. All of them had the following username @ domain / password format. After a little cleaning, there are 23,573 accounts left. Then duplicates were removed and the output was a list of 21,686 account.
The bulk of these were mylniki popular foreign mailer hotmail.com. But it should be noted that other mail systems were also present, such as Yahoo, Gmail, AoL, etc. The top 20 domains and the number of accounts for each of them will be presented below.

If we look at user names, we can observe that the first 9,586 of them are arranged in alphabetical order. They begin with the letters “A” & “B”. Based on the passwords they use, it can be concluded that they belong to the Latin community. But there are also accounts from around the world.
The most frequently used password is still 123456. As you can see below, out of a total of 21,866 passwords, 91 of them are 123456. Here are the TOP-100 most frequently used passwords from the list.
According to the password format, you can extract the following statistics.
43.3% - letters, in lower case. Example: monkey
2.1% - letters, upper and lower case. Example: Thomas
15.8% - only numbers. Example: 123456
35.1% - letters and numbers. Example: j0s3ph
3.6% - letters, numbers and specials. characters. Example: sandra19_1961
30% - ends with a number. Example: hello1
If we look at the length of the password in the following graph, we will see that most of them are 6-character.

On February 6, 2011, as part of an attack on HBGary, the group Anonymous, using social engineering methods, Jussi Jaakonaho, one of their technical admins rootkit.com, was able to compromise. As a result, a full dump of the resource with the entire database, including users, was acquired.
John the Ripper was used for decryption. Most of the passwords were selected using the 17.5 MB dictionary, and the rest were achieved using other combined attacks. Below are the 10 most frequently used passwords.
As we can see, the already beaten 123456 is again lit up. It is also worth noting that the 3rd place in popularity has taken a password similar to the name of the resource, as many as 341 results. I also want to add, based on my numerous experiences, when working with databases, to decrypt passes, quite often there are resources that use the address of this resource as a password. However, this observation is not a rule. But in my practice there were already portals, where the% of such passes was quite large, and there were where they were never used at all. I have not yet found the dependence of this observation.
And the following link will give you the TOP-500 passwords used on the rootkit.com resource:
dazzlepod.com/rootkit/password
The speed of selection using a password can be described by a simple mathematical formula: the number of possible characters raised to the power of the password length divided by the number of passwords to be recruited per second. The result is an estimated time in seconds. However, in order to prove to a person what a simple password actually means, it is not necessary to load him with mathematics. Just go to the website How Secure Is My Password ?, enter <> (the word “password” in the Latin layout) and show that such a pass will be downloaded on a regular PC in 30 seconds. In general, it is quite interesting to test passwords: it becomes immediately clear that the password length is much more important than its complexity. Hacking "# R00t $ H3ll" will take 195 years, and the seemingly simple "abcdefg1234567" will take 5722 years.
Link:
howsecureismypassword.net
Related links [what to read]:
Analysis of password protection problems in Russian companies
Statistics from 10,000 leaked Hotmail passwords
And as once wrote admin insidepro:
An interesting observation - the last couple of weeks, our base hash.insidepro.com on the parameter "Webcrack today" daily leads, which is good news. Moreover, the “on the heels” service of www.md5decrypter.co.uk (a very worthy service, IMHO) has a base of 5 billion hashes, but it turns out that our 33 million base is more efficient, despite the fact that it is less than in 150 times. This once again confirms the thesis - “the matter is not in quantity, but in quality”.
Therefore, in order to successfully open and decrypt passwords, it is not necessary to immediately climb to download the rainbow table that weighs hundreds of gigabytes. And enough to understand the question, then a relatively small base, which you will replenish from time to time, will show very good penetrability results.
Resources from which material was scooped:
personal experience
wikipedia.org
troyhunt.com
stormsecurity.wordpress.com
dazzlepod.com
[parole] — , . . « — » .Sony Pictures database
The study of Troy Hunt, who took the Sony Pictures user base for his research, is worth noting that all passwords were stored in clear text. And then he analyzed the user passwords. Here are the results he had.
Password length

As we can see, the main number of passwords with a length of 6 to 10 characters. In addition, half of it is less than 8 characters.
')
Used characters

1% -
4% -
45% -
50% -Cryptographic strength of a password is determined by the variation of letters of different registers + numbers + specials. characters ^ password length. In this example, we can observe that the same type of passes are used.
Vocabulary passwords

36% -
64% -In this test, a dictionary of 1.7 million words was used. You can take it here dazzlepod.com/site_media/txt/passwords.txt As we see the result is disappointing, more than a third of the passes are vocabulary.
Uniqueness test

8% -
92% -The Sony Pictures database also includes passwords for other services. Actually, the table shows how many users use the same pass everywhere.
Bruteforce hash

18% -
82% -Since all the passwords were stored in clear form, but even if they were hashes, we would be able to decrypt approximately 82% of the total, using rainbow tables.
Email password's
An independent researcher in the field of information security got into the hands of a list of + 20K accounts from various mailers, like email; pass. The lists are divided into 2 parts, you can take here:
users - box.net/shared/m9fv11hcrc
passwords - box.net/shared/jek7g37fjkPasswords can not even try to compare, because the whole thing was going to be mixed. Since the goal was not to compromise users, but to analyze the passwords used. Initially, the list consisted of 24,546 entries. All of them had the following username @ domain / password format. After a little cleaning, there are 23,573 accounts left. Then duplicates were removed and the output was a list of 21,686 account.
The bulk of these were mylniki popular foreign mailer hotmail.com. But it should be noted that other mail systems were also present, such as Yahoo, Gmail, AoL, etc. The top 20 domains and the number of accounts for each of them will be presented below.

1. hotmail.com – 12478
2. yahoo.com – 3012
3. aol.com – 827
4. gmail.com – 512
5. msn.com – 443
6. hotmail.fr – 346
7. comcast.net – 321
8. aim.com – 287
9. sbcglobal.net – 275
10. hotmail.co.uk – 206
11. neomail.com – 153
12. hotmail.es – 117
13. cox.net – 116
14. verizon.net – 96
15. bellsouth.net – 95
16. live.com.mx – 71
17. yahoo.ca – 63
18. yahoo.co.uk – 63
19. charter.net – 47
20. earthlink.net – 46If we look at user names, we can observe that the first 9,586 of them are arranged in alphabetical order. They begin with the letters “A” & “B”. Based on the passwords they use, it can be concluded that they belong to the Latin community. But there are also accounts from around the world.
The most frequently used password is still 123456. As you can see below, out of a total of 21,866 passwords, 91 of them are 123456. Here are the TOP-100 most frequently used passwords from the list.
1. 123456 – 91
2. neopets – 39
3. monkey – 27
4. 123456789 – 26
5. 123321 – 24
6. password – 23
7. iloveyou – 17
8. princess – 16
9. horses – 16
10. tigger – 15
11. pokemon – 14
12. cheese – 14
13. 111111 – 13
14. kitty – 13
15. purple – 12
16. dragon – 12
17. nicole – 12
18. 1234567 – 11
19. alejandra – 11
20. daniel – 11
21. bubbles – 10
22. alejandro – 10
23. michelle – 10
24. 12345 – 10
25. hello – 10
26. c***** – 10
27. chocolate – 9
28. hottie – 9
29. alberto – 9
30. 12345678 – 9
31. fluffy – 9
32. buddy – 9
33. 123123 – 9
34. cassie – 9
35. andrea – 9
36. secret – 9
37. shadow – 9
38. tequiero – 9
39. ****llica – 9
40. poop – 8
41. hi – 8
42. sebastian – 8
43. jessica – 8
44. adopt – 8
45. 654321 – 8
46. justin – 7
47. newpw123 – 7
48. scooter – 7
49. soccer – 7
50. holly – 7
51. hannah – 7
52. flower – 7
53. 1234 – 7
54. jessie – 7
55. ashley – 7
56. tiger – 7
57. lauren – 7
58. football – 7
59. elizabeth – 7
60. casper – 7
61. roberto – 7
62. 000000 – 7
63. legolas – 7
64. estrella – 7
65. 159753 – 7
66. anime – 7
67. sabrina – 6
68. moomoo – 6
69. angelica – 6
70. cat123 – 6
71. bonita – 6
72. buster – 6
73. kitten – 6
74. killer – 6
75. qwerty – 6
76. chelsea – 6
77. sasuke – 6
78. olivia – 6
79. theresa – 6
80. america – 6
81. beatriz – 6
82. mariposa – 6
83. oscar – 6
84. rainbow – 6
85. yellow – 6
86. cool – 6
87. ginger – 6
88. maggie – 6
89. friends – 6
90. asdfgh – 6
91. abc123 – 6
92. neopet – 6
93. dancer – 6
94. amanda – 6
95. avatar – 6
96. boogie – 6
97. greenday – 6
98. thumper – 6
99. 666666 – 6
100. bob – 6According to the password format, you can extract the following statistics.
43.3% - letters, in lower case. Example: monkey
2.1% - letters, upper and lower case. Example: Thomas
15.8% - only numbers. Example: 123456
35.1% - letters and numbers. Example: j0s3ph
3.6% - letters, numbers and specials. characters. Example: sandra19_1961
30% - ends with a number. Example: hello1
If we look at the length of the password in the following graph, we will see that most of them are 6-character.

Rootkit.com

On February 6, 2011, as part of an attack on HBGary, the group Anonymous, using social engineering methods, Jussi Jaakonaho, one of their technical admins rootkit.com, was able to compromise. As a result, a full dump of the resource with the entire database, including users, was acquired.
John the Ripper was used for decryption. Most of the passwords were selected using the 17.5 MB dictionary, and the rest were achieved using other combined attacks. Below are the 10 most frequently used passwords.
Rank Password Accounts
1 | 123456 | 1023
2 | password | 392
3 | rootkit | 341
4 | 111111 | 190
5 | 12345678 | 181
6 | qwerty | 175
7 | 123456789 | 170
8 | 123123 | 99
9 | qwertyui | 92
10 | letmein | 91As we can see, the already beaten 123456 is again lit up. It is also worth noting that the 3rd place in popularity has taken a password similar to the name of the resource, as many as 341 results. I also want to add, based on my numerous experiences, when working with databases, to decrypt passes, quite often there are resources that use the address of this resource as a password. However, this observation is not a rule. But in my practice there were already portals, where the% of such passes was quite large, and there were where they were never used at all. I have not yet found the dependence of this observation.
And the following link will give you the TOP-500 passwords used on the rootkit.com resource:
dazzlepod.com/rootkit/password
To verify password strength
The speed of selection using a password can be described by a simple mathematical formula: the number of possible characters raised to the power of the password length divided by the number of passwords to be recruited per second. The result is an estimated time in seconds. However, in order to prove to a person what a simple password actually means, it is not necessary to load him with mathematics. Just go to the website How Secure Is My Password ?, enter <> (the word “password” in the Latin layout) and show that such a pass will be downloaded on a regular PC in 30 seconds. In general, it is quite interesting to test passwords: it becomes immediately clear that the password length is much more important than its complexity. Hacking "# R00t $ H3ll" will take 195 years, and the seemingly simple "abcdefg1234567" will take 5722 years.
Link:
howsecureismypassword.net
Related links [what to read]:
Analysis of password protection problems in Russian companies
Statistics from 10,000 leaked Hotmail passwords
And as once wrote admin insidepro:
An interesting observation - the last couple of weeks, our base hash.insidepro.com on the parameter "Webcrack today" daily leads, which is good news. Moreover, the “on the heels” service of www.md5decrypter.co.uk (a very worthy service, IMHO) has a base of 5 billion hashes, but it turns out that our 33 million base is more efficient, despite the fact that it is less than in 150 times. This once again confirms the thesis - “the matter is not in quantity, but in quality”.
Therefore, in order to successfully open and decrypt passwords, it is not necessary to immediately climb to download the rainbow table that weighs hundreds of gigabytes. And enough to understand the question, then a relatively small base, which you will replenish from time to time, will show very good penetrability results.
Resources from which material was scooped:
personal experience
wikipedia.org
troyhunt.com
stormsecurity.wordpress.com
dazzlepod.com
Source: https://habr.com/ru/post/129052/
All Articles