Hackers have cracked SSL encryption used by millions of sites
The researchers found a serious weakness in almost all sites protected by the Secure Sockets Layer protocol, which allows an attacker to silently decrypt data that passes between the web server and the user's browser.
The vulnerability is found in version 1.0, earlier versions of TLS and in the transport security level. Versions TLS 1.1 and 1.2 are not susceptible to vulnerabilities, but they are barely used, which makes sites such as PayPal, GMail and many others vulnerable if an attacker has the ability to control the connection between the user and the target site.
At the Ekoparty security conference in Buenos Aires at the end of the week, the Thai Duong and Juliano Rizzo researchers are planning to demonstrate evidence of their concept, which they called BEAST (translated as beast) from the first letters of the following words Browser Exploit Against SSL / TLS.
Duong said that the demonstration will show the decryption of the cookie to access the PayPal account.
')
BEAST is different from most other published “attacks” on HTTPS. Other hacking attempts are focused on spoofing the authentication feature in SSL. As far as we know, BEAST is the first of its kind attack, allowing to actually decrypt HTTPS requests.
At the moment, BEAST takes about 2 seconds to decrypt a byte of the encrypted cookie. This means that an authentication cookie of 1000-2000 characters will be decrypted for half an hour. However, this technique poses a threat to the millions of sites that use early versions of TLS.
Thai Duong and Juliano Rizzo said that almost all applications using TLS 1.0 encryption are vulnerable, and give the opportunity to use their technology to control and monitor private messages sent, for example, via instant messenger or VPN.
“The problem is that people will not improve anything until you give them a good reason,” said Ivan Ristic, director of Qualys , “it's terrible, isn't it?”
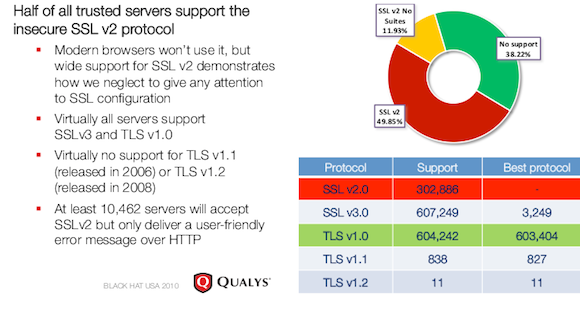
TLS 1.1 and 1.2 support schedule
While Mozilla and the OpenSSL developers must implement TLS 1.2 at all, Microsoft has achieved a little more. Secure TLS versions are available in the IE browser and IIS web server, but not by default.
Thai Duong: "Most browsers and websites use SSL 3.0 and TLS 1.0, respectively, if the owner of a website decides to upgrade to version 1.1 or 1.2, it will simply lose a significant portion of its customers."
update
From alist :
The exploit works as a Man-in-the-middle in combination with the implementation of JavaScript code on the page. An attacker listens to https traffic and adds JavaScript to the client’s page. Then this script continues to send requests for the same connection with the content known to the attacker. Knowing the contents of the request body, an attacker can decrypt HTTP headers, including the user's cookie.
This means all HTTPS connections remain secure if JavaScript is disabled on the page.
The vulnerability is found in version 1.0, earlier versions of TLS and in the transport security level. Versions TLS 1.1 and 1.2 are not susceptible to vulnerabilities, but they are barely used, which makes sites such as PayPal, GMail and many others vulnerable if an attacker has the ability to control the connection between the user and the target site.
At the Ekoparty security conference in Buenos Aires at the end of the week, the Thai Duong and Juliano Rizzo researchers are planning to demonstrate evidence of their concept, which they called BEAST (translated as beast) from the first letters of the following words Browser Exploit Against SSL / TLS.
Duong said that the demonstration will show the decryption of the cookie to access the PayPal account.
')
BEAST is different from most other published “attacks” on HTTPS. Other hacking attempts are focused on spoofing the authentication feature in SSL. As far as we know, BEAST is the first of its kind attack, allowing to actually decrypt HTTPS requests.
At the moment, BEAST takes about 2 seconds to decrypt a byte of the encrypted cookie. This means that an authentication cookie of 1000-2000 characters will be decrypted for half an hour. However, this technique poses a threat to the millions of sites that use early versions of TLS.
Thai Duong and Juliano Rizzo said that almost all applications using TLS 1.0 encryption are vulnerable, and give the opportunity to use their technology to control and monitor private messages sent, for example, via instant messenger or VPN.
“The problem is that people will not improve anything until you give them a good reason,” said Ivan Ristic, director of Qualys , “it's terrible, isn't it?”

TLS 1.1 and 1.2 support schedule
While Mozilla and the OpenSSL developers must implement TLS 1.2 at all, Microsoft has achieved a little more. Secure TLS versions are available in the IE browser and IIS web server, but not by default.
Thai Duong: "Most browsers and websites use SSL 3.0 and TLS 1.0, respectively, if the owner of a website decides to upgrade to version 1.1 or 1.2, it will simply lose a significant portion of its customers."
update
From alist :
The exploit works as a Man-in-the-middle in combination with the implementation of JavaScript code on the page. An attacker listens to https traffic and adds JavaScript to the client’s page. Then this script continues to send requests for the same connection with the content known to the attacker. Knowing the contents of the request body, an attacker can decrypt HTTP headers, including the user's cookie.
This means all HTTPS connections remain secure if JavaScript is disabled on the page.
Source: https://habr.com/ru/post/128833/
All Articles