Cisco ASA traffic accounting using NetFlow and nfdump on FreeBSD or Linux
Introduction
Almost every network administrator faces the challenge of traffic accounting. Either this is necessary for billing, or simply for monitoring activity.
To solve this problem, you can use the standard NetFlow protocol (RFC 3954), which is supported by network equipment manufacturers (Cisco, Juniper, 3Com, etc.), as well as Linux, * BSD and DD-WRT firmware. Netflow allows you to transfer traffic data (sender and recipient address, port, amount of information, etc.) from network equipment ( sensor ) to the collector . The collector, in turn, saves the received information. As a collector, you can use a normal server. I will illustrate the scheme with a picture from Wikipedia:
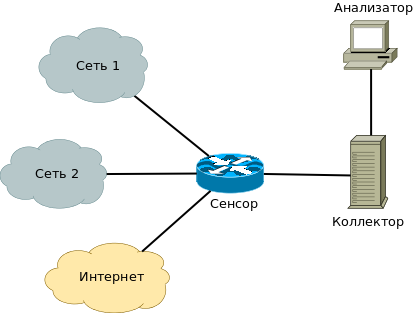
When I undertook to configure NetFlow, it turned out that opensource solutions for the implementation of the collector do not work well with Cisco ASA, and there is very little information on the Internet, which is the case in this case. I decided to fill this gap: it is possible to make friends FreeBSD / Linux with Cisco ASA in 20 minutes.
')
Let's start with the fact that I did not work:
Flow-tools - does not work at all, apparently does not support NetFlow v9.
flowd - does not save data on the number of bytes transferred and packets.
nfcapd - incorrectly saves the date and time, the number of bytes transferred.
I do not deny the possibility that my crooked hands are to blame, or that the new version of these programs will add bug-free support for the Cisco ASA.
Collector
After a long search, I came across a version of nfdump with NSEL support: nfdump-1.5.8-NSEL , which works fine with ASA.
The installation process is standard:
First we download and unpack nfdump-1.5.8-NSEL.
Then in the nfdump-1.5.8-NSEL folder:
./configure
make
make installAfter that we will get several programs:
nfcapd is a daemon collector, listens to the port, collects data and writes to files.
nfdump - reads and prints data collected by nfcapd.
nfexpire - rotates files created by nfcapd.
nfreplay - reads the collected nfcapd files and sends them over the network to another collector.
Start the collector:
nfcapd -l < > -t < ()> -Dnfcapd will start writing the resulting data to a temporary file nfcapd.current. PID in the folder specified by the -l option. When the time interval specified by -t passes, nfcapd will copy the contents of the temporary file to nfcapd. yyyymmddhhmm . Thus, each such file will contain information about traffic for the last -t seconds.
The -D switch indicates to work in daemon mode.
The -b parameter specifies the IP address to listen; -p allows you to change the default port.
Sensor
Now you need to configure the Cisco ASA. Because I am a layman in Cisco, I will provide links to ready-made manuals:
If you configure the ASA through the ASDM GUI.
If you configure ASA through the tru console.
Unfortunately, in my version of ASDM (6.3) there was a glitch that did not allow adding a collector to the policy rule, so I still had to climb into the console.
Now, if everything went well, the following packages should fall onto the collector:
tcpdump port 9995
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on em0, link-type EN10MB (Ethernet), capture size 96 bytes
18:22:36.909747 IP 192.168.4.1.56684 > 192.168.4.7.9995: UDP, length 1436
18:22:37.012687 IP 192.168.4.1.56684 > 192.168.4.7.9995: UDP, length 1464
18:22:37.065782 IP 192.168.4.1.56684 > 192.168.4.7.9995: UDP, length 1432
...
And in the folder where the nfcapd files are saved, the size of the files should start to grow.
Garbage collection
At ~ 30 connections per second (network 150 users), the log in 1 minute takes about 2 MB.
To avoid cluttering up the disk, add the nfexpire command to the crontab:
/usr/local/bin/nfexpire -e < > -s <. > -t <. >For example, running nfexpire with the -t 2w option will remove all files older than two weeks, and with -s 20g the oldest files, so that their total size is no more than 20 GB. These parameters can be used together.
Data processing
You can get data from nfcapd. * Files in a human-readable format using the nfdump utility:
nfdump -r < >
2011-09-04 19:53:45.484 TCP 192.168.2.11:1057 NA -> 217.20.152.98:80 DENIED I-ACL 0
2011-09-04 19:53:45.554 TCP 66.249.66.34:55383 NA -> 46.46.152.214:80 DELE-U Deleted 0
2011-09-04 19:53:30.887 TCP 192.168.4.183:63015 46.46.152.212:63015 -> 89.185.97.235:80 CREATE Ignore 214
...
As you can see, the output of nfdump is easily amenable to further parsing. It is necessary to take into account that each record contains information not about a single packet, but about a stream — a set of packets passing in one direction.
Nfdump can also read multiple files, collect statistics and filter entries.
There is also a web interface to nfdump - NfSen , which can draw beautiful graphics.
If you want to process the data yourself, you will need the -x key of the nfcapd daemon - it allows you to start the program when the next file is ready. For example, I wrote a php script to process the nfdump output, and my nfcapd startup line looks like this:
/usr/local/bin/nfcapd -t 600 -w -p 9999 -l /data/flows/ -D -x '/usr/local/bin/php /usr/local/share/sams/all_traf_stats.php %d/%f' &Note that the command is enclosed in single quotes, and that as parameters to the script,% d is transferred and% f is the nfcapd folder and the name of the last file, respectively.
Logging each packet in the database turned out to be very expensive, so my script simply counts the statistics for each host and protocol in bytes every 10 minutes. Thus, I track the airborne machines and lovers download the organization of the organization by downloading movies - in the morning I receive a letter from the top20 “rocking players”. Also, the data from nfdump complements the statistics of the transparent proxy server Squid, which serves only the 80th port.
If someone needs this script as an example, you can download it , but do not expect beautiful code :) The script does a good job at ~ 500 entries per second. If the load is very large, then he will begin to eat too much memory.
findings
Using NetFlow you can organize traffic accounting by retrieving information from routers and firewalls. This allows you to log traffic, get billing statistics, or detect suspicious activity on the network. Also in this topic, I tried to tell how to make Cisco ASA work in tandem with FreeBSD, because At one time I did not find such a howto on the network.
Source: https://habr.com/ru/post/127613/
All Articles