Virus without programming
Introduction
A good friend, in his spare time engaged in repairing computers, shared another caught virus. Popular antivirus did not define it, which is not surprising, and soon you will understand why.
The process was hidden from the Windows Task Manager, but the Auslogics Task Manager displayed it as upp1.exe, located in the System32 directory of the system. Moreover, if the OS is 64-bit or installed at the wrong address C: \ Windows, then Vir is still installed in C: \ Windows \ System32, creating non-existent directories along the way, respectively. The process was in the autorun list and the branch was deleted using Autoruns. But as soon as Autoruns is closed, a new copy of the virus named upp2.exe is launched. If you delete it, rundl132.exe appears and so on. Apparently, they run themselves and there is a check for the absence of a process. It was solved very simply - by killing the process tree.
Study
The first thing I noticed was the size of the executable files, which was a little more than 1 MB for each exe. I doubt that at least one self-respecting virus writer is capable of such.
')
We turn to the more interesting. Having loaded one of the executable files into the HEX editor, I began to look at it fluently from the end ... And for good reason from the end!
At the end of the file there were several hundred lines of text in UTF-8 encoding:

My HEX editor does not support UTF-8 encoding, so I opened the executable file as text:
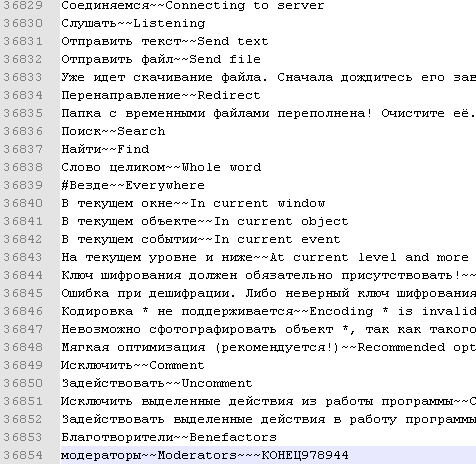
Among this text I was interested in the following:

That's right, look what is, "Algorithm2". Description from the author's website: " Algorithm 2 is a free program for creating programs and games at home! With its help, anyone can create programs without having any programming knowledge. ".
Some kind of application development environment with the mouse without entering any code written using .NET. I did not linger on that site, having downloaded and looked at examples, I launched upp1.exe in the IL disassembler:
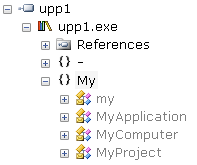
Unfortunately, apart from the names of classes and namespaces, nothing interesting was found.
In addition, it was discovered that the process downloads MDAC_TYP.EXE from microsoft.com. I can assume that the malware can update and works with MDAC .
In system32, the files upp1.ver, upp2.ver and the engine directory are created. In the engine directory at runtime, I found the g.obo, gm.obo, k.obo, ki.obo, t.obo files containing fragments of encrypted information, which I could not decrypt:
9tcLzYklFri4ABxuu0spYAad5Ed13rA + HUwS6 + fz3d 1JTRrhQ3eqHF4MwCU2k5pfE2FiOR6jz8 + NLOtK5YyIjBBo7RodD / 8r2G1KapUdSWfBzmH IauGuEQ53iweGHB3ooaFZVZwjeX2QMmWqPauhKidIJxBQeNT3LSzxYtZhlO4 =
9tcLzYklFri4ABxuu0spYAad5Ed13rA + HUwS6 + fz3d1JTRrhQ3eqHF4MwCU2k 5pfE2FiOR6jz8 + NLOtK5YyIjKRrAUB + hCDBr98XIlTn chf chf i2 chf i2fy2fy2fyfy2fyfy2fyfy2fyfy2fyfy2fyfy2fyour
And etc.
Conclusion
On this, perhaps, everything. If someone is interested in "digging", please - system32.zip ( system32 password). Please forgive that so little information has ever been interested in analyzing other people's applications and I have no experience in this.
The sad thing is this: a virus written without programming, weighing more than 1 MB, and even requiring .NET.
Source: https://habr.com/ru/post/127474/
All Articles