Bypassing the integrated protection of PIC microcontrollers
In the comments to the recent topic about opening the processor, an article was mentioned about how it was possible to bypass the built-in protection against reading the microcontroller firmware (the so-called Fuse bits). I liked it, below - translation with some additions and explanations.
I thought it would be nice to try some of the PIC microcontroller hacking techniques I've heard about. Typically, PIC microcontrollers have a number of so-called fuse-bits, which serve to protect against reading or modification of some parts of the memory. However, there are times when it becomes necessary to read the contents of an already programmed and protected controller (legally). A typical example is the loss by a company of technical documentation on a device, or the dismissal of those people who originally developed a secure microcontroller firmware. This also often happens when a company wants to update its product line.
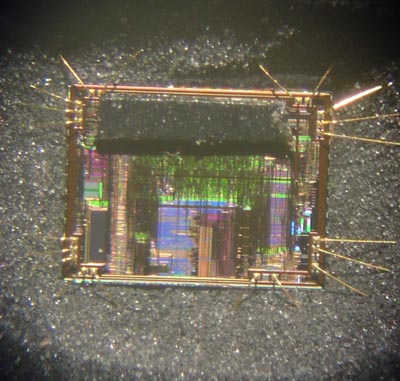
I bought four PIC18F1320 and started tormenting them. This is what the PIC18F1320 looks like in its original, not peeled form:
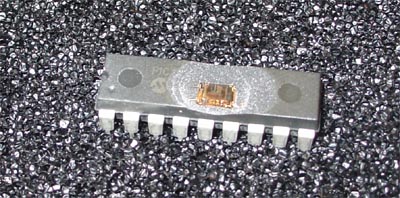
The first thing to do is to open the upper part of the case so that the silicon interiors of the microcontroller become available. Although there are many amateur ways to do this, they are usually based on the use of nitric or sulfuric acid. First, it is most likely not the things that you really want to see next to you. Secondly, they are not easy to get, because, for example, nitric acid is one of the components for the manufacture of explosives. I decided that the easiest and most reliable way was to send microcontrollers to a failure analysis lab, such as MEFAS , and get the “decapitated” components into my hands for $ 50 and 2 days. For this project, I removed the compound from three microcontrollers. Two of them remained completely working, and one lost the case completely, i.e. there was only the chip itself. This was dictated by the design features of my microscope at high magnifications.
A brief examination of the chip surface revealed some of the characteristic areas of the microcontroller, shown below:
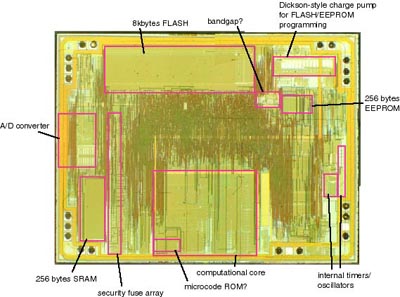
Visible (clockwise): 8 KB flash-memory, reference voltage source, charge pump for programming flash / EEPROM memory, 256 bytes EEPROM memory, built-in timers and clocking circuits, computing core, ROM with microcode, array with fuse-bits, 256 bytes of RAM, ADC. (
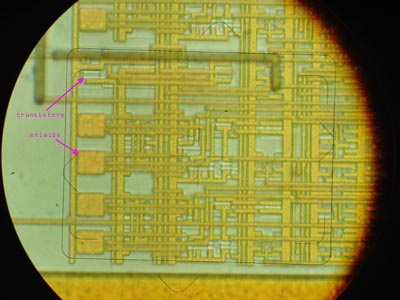
One structure immediately caught my attention: a series of metal screens above the transistors, which were arranged in the correct order, and the number of which coincided with the number of fuse-bits. The complete overlap of elements with metal screens on silicon crystals is very rare, and by itself such elements attract attention because contain something extremely important.
Think a little about these metal screens. What are they needed for? First, let's recall some interesting facts about flash technology (this type of memory is also used in PIC microcontrollers for storing fuse bits). Flash technology involves the use of floating gate transistors, very similar to those used in old ROM chips with IF-erasing (do you remember the 2616s in a ceramic case and with quartz glass?). Both in flash and in UV-EPROM, data is saved by injecting electrons into the floating gate using a tunnel effect, where these electrons can be located for decades. Additional electrons in the floating gate create noticeable changes in the characteristics of the transistor. The difference lies in the fact that in flash-memory for erasing information enough electrical pulses, while in the UV-EPROM in order to "expel" the electrons from the floating gate photons are needed with high energy. This requires ultraviolet from a wavelength of about 250 nm. In order to UV radiation is not too weakened, apply quartz glass (the same windows on the old ROM chips).
An important conclusion that can be drawn from the above facts: flash memory can also be erased with UV radiation, because it has almost the same transistor structure as the device's UV-EPROM. The case of devices with flash memory usually prevents UV from reaching the surface of the crystal, but since our PIC microcontroller is now deprived of a plastic top of the case, we can apply UV radiation and see what happens.
I conducted an experiment in which I programmed the PIC controller with consecutive values from 0x00 to 0xFF, and then exposed it to my UV-EPROM eraser while taking a shower and checking mail.
When I removed the controller from the eraser, I found that the flash memory was indeed cleared and returned to its original state (all values are 0xFF), and that the protective fuse bits were also deactivated. It should also be borne in mind that UV radiation acts on the EEPROM memory.
It is clear that the metal plates above the protective fuse-bits just serve as protection against dumping them separately from the flash-memory of programs.

The picture illustrates the problem (and its solution) that I encountered. In order to erase the information on the flash memory transistor, strong UV radiation must reach its floating gate. And metal screens prevent this by effectively reflecting UV rays.
However, due to the difference between the refractive indices of light for oxide and silicon, the light falling from a certain angle will be reflected from its surface. To better understand this effect you can jump into the pool and look at the water almost at eye level. Water will have a very good reflectivity just because of the difference in the refractive indices of water and air. This is called total internal reflection.
This reflection can just be used to cause UV radiation to reflect off the metal surface of the screen and fall back onto the floating gate of the transistor. So, turning the PIC microcontroller inside the eraser ROM, I can direct enough light so that it bounces around the flash memory transistor and erasing it. After several attempts, I developed a technology that seems to work quite well.

This is a photo of the microcontroller inside the eraser ROM (the blue glow around the controller is due to the operation of the UV lamp). The microcontroller is fixed at an angle in the antistatic material.
But all this can not protect against erasing the necessary data in the part of the flash-memory where the microcontroller program is stored. In order to prevent erasing of these data, a full mask is used, which was very carefully cut out of electrical tape and attached to the crystal with two tweezers, a microscope and an unwavering hand) The electrical tape effectively blocks the passage of ultraviolet radiation, thereby protecting absorbs ultraviolet reflected from the silicon substrate.
This is a photo of a crystal with an attached mask over the flash memory area.
Using this technique, I was finally able to reset the protection fuse-bits without erasing the main program of the microcontroller. The same way you can erase only some of the flash-memory. Hooray!
')
Obviously, the described method is suitable only for those devices that contain reprogrammable fuse-bits. If the protection bits are programmed only once (and this happens), then this technique is not suitable. In these devices, thin conductors on a chip are simply burned out. However, my colleague said that even in this case, their own methods of struggle were developed (I think, they restore contact in some similar microsurgical manner). I also know that this operation is worth a lot.
Just want to note that in the popularly popular AVR microcontrollers fuse-bits have a similar structure (they are reprogrammed in the same way), which allows us to hope that the described technique is suitable for them!
UPD: corrected the translation flaws whenever possible (about the width of the forbidden zone, magnetic tape and the method of filling the controller memory).
UPD 2: the same topic, but for AVR microcontrollers, is affected here and here . Here you can order reading the firmware and even buy specials. appliances.
Original article here .
Hacking MK PIC18F1320
I thought it would be nice to try some of the PIC microcontroller hacking techniques I've heard about. Typically, PIC microcontrollers have a number of so-called fuse-bits, which serve to protect against reading or modification of some parts of the memory. However, there are times when it becomes necessary to read the contents of an already programmed and protected controller (legally). A typical example is the loss by a company of technical documentation on a device, or the dismissal of those people who originally developed a secure microcontroller firmware. This also often happens when a company wants to update its product line.
Well, you know, there are still some situations where such skills can come in handy.
I bought four PIC18F1320 and started tormenting them. This is what the PIC18F1320 looks like in its original, not peeled form:

The first thing to do is to open the upper part of the case so that the silicon interiors of the microcontroller become available. Although there are many amateur ways to do this, they are usually based on the use of nitric or sulfuric acid. First, it is most likely not the things that you really want to see next to you. Secondly, they are not easy to get, because, for example, nitric acid is one of the components for the manufacture of explosives. I decided that the easiest and most reliable way was to send microcontrollers to a failure analysis lab, such as MEFAS , and get the “decapitated” components into my hands for $ 50 and 2 days. For this project, I removed the compound from three microcontrollers. Two of them remained completely working, and one lost the case completely, i.e. there was only the chip itself. This was dictated by the design features of my microscope at high magnifications.

A brief examination of the chip surface revealed some of the characteristic areas of the microcontroller, shown below:

Visible (clockwise): 8 KB flash-memory, reference voltage source, charge pump for programming flash / EEPROM memory, 256 bytes EEPROM memory, built-in timers and clocking circuits, computing core, ROM with microcode, array with fuse-bits, 256 bytes of RAM, ADC. (
it would be very interesting to learn how he defined all this by his appearance
)One structure immediately caught my attention: a series of metal screens above the transistors, which were arranged in the correct order, and the number of which coincided with the number of fuse-bits. The complete overlap of elements with metal screens on silicon crystals is very rare, and by itself such elements attract attention because contain something extremely important.

Think a little about these metal screens. What are they needed for? First, let's recall some interesting facts about flash technology (this type of memory is also used in PIC microcontrollers for storing fuse bits). Flash technology involves the use of floating gate transistors, very similar to those used in old ROM chips with IF-erasing (do you remember the 2616s in a ceramic case and with quartz glass?). Both in flash and in UV-EPROM, data is saved by injecting electrons into the floating gate using a tunnel effect, where these electrons can be located for decades. Additional electrons in the floating gate create noticeable changes in the characteristics of the transistor. The difference lies in the fact that in flash-memory for erasing information enough electrical pulses, while in the UV-EPROM in order to "expel" the electrons from the floating gate photons are needed with high energy. This requires ultraviolet from a wavelength of about 250 nm. In order to UV radiation is not too weakened, apply quartz glass (the same windows on the old ROM chips).
An important conclusion that can be drawn from the above facts: flash memory can also be erased with UV radiation, because it has almost the same transistor structure as the device's UV-EPROM. The case of devices with flash memory usually prevents UV from reaching the surface of the crystal, but since our PIC microcontroller is now deprived of a plastic top of the case, we can apply UV radiation and see what happens.
I conducted an experiment in which I programmed the PIC controller with consecutive values from 0x00 to 0xFF, and then exposed it to my UV-EPROM eraser while taking a shower and checking mail.
When I removed the controller from the eraser, I found that the flash memory was indeed cleared and returned to its original state (all values are 0xFF), and that the protective fuse bits were also deactivated. It should also be borne in mind that UV radiation acts on the EEPROM memory.
It is clear that the metal plates above the protective fuse-bits just serve as protection against dumping them separately from the flash-memory of programs.

The picture illustrates the problem (and its solution) that I encountered. In order to erase the information on the flash memory transistor, strong UV radiation must reach its floating gate. And metal screens prevent this by effectively reflecting UV rays.
However, due to the difference between the refractive indices of light for oxide and silicon, the light falling from a certain angle will be reflected from its surface. To better understand this effect you can jump into the pool and look at the water almost at eye level. Water will have a very good reflectivity just because of the difference in the refractive indices of water and air. This is called total internal reflection.
This reflection can just be used to cause UV radiation to reflect off the metal surface of the screen and fall back onto the floating gate of the transistor. So, turning the PIC microcontroller inside the eraser ROM, I can direct enough light so that it bounces around the flash memory transistor and erasing it. After several attempts, I developed a technology that seems to work quite well.

This is a photo of the microcontroller inside the eraser ROM (the blue glow around the controller is due to the operation of the UV lamp). The microcontroller is fixed at an angle in the antistatic material.
But all this can not protect against erasing the necessary data in the part of the flash-memory where the microcontroller program is stored. In order to prevent erasing of these data, a full mask is used, which was very carefully cut out of electrical tape and attached to the crystal with two tweezers, a microscope and an unwavering hand) The electrical tape effectively blocks the passage of ultraviolet radiation, thereby protecting absorbs ultraviolet reflected from the silicon substrate.

This is a photo of a crystal with an attached mask over the flash memory area.
Using this technique, I was finally able to reset the protection fuse-bits without erasing the main program of the microcontroller. The same way you can erase only some of the flash-memory. Hooray!
')
Remarks
Obviously, the described method is suitable only for those devices that contain reprogrammable fuse-bits. If the protection bits are programmed only once (and this happens), then this technique is not suitable. In these devices, thin conductors on a chip are simply burned out. However, my colleague said that even in this case, their own methods of struggle were developed (I think, they restore contact in some similar microsurgical manner). I also know that this operation is worth a lot.
Just want to note that in the popularly popular AVR microcontrollers fuse-bits have a similar structure (they are reprogrammed in the same way), which allows us to hope that the described technique is suitable for them!
UPD: corrected the translation flaws whenever possible (about the width of the forbidden zone, magnetic tape and the method of filling the controller memory).
UPD 2: the same topic, but for AVR microcontrollers, is affected here and here . Here you can order reading the firmware and even buy specials. appliances.
Original article here .
Source: https://habr.com/ru/post/127281/
All Articles