Read the QR code
 Sometimes there are such situations when you need to read a QR code, but there is no smartphone at hand. What to do? It only comes to mind to try to read by hand. If anyone has come across such situations or is simply wondering how the QR code is read by machines, then this article will help you understand this problem.
Sometimes there are such situations when you need to read a QR code, but there is no smartphone at hand. What to do? It only comes to mind to try to read by hand. If anyone has come across such situations or is simply wondering how the QR code is read by machines, then this article will help you understand this problem.The article discusses the basic features of QR codes and methods for decrypting information without using computers.
Illustration: 14, characters: 8 510.
For those who do not know what a QR code is , there is a good article in the English Wikipedia. You can also read the thematic blog on Habré and several good articles on related topics that can be found by searching .
')
The solution of the problem of directly reading information from a QR-picture will be considered on the example of two codes. The information was encoded in the online-generator QR Coder.ru .
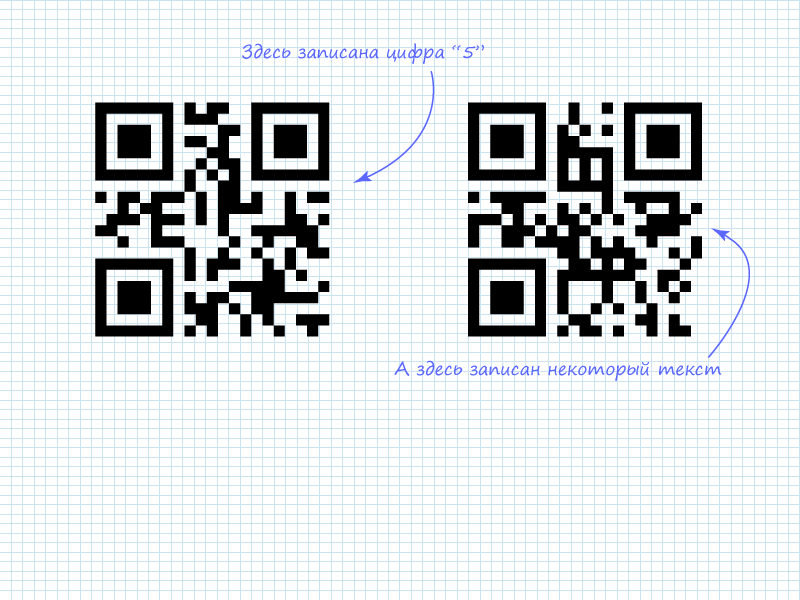
To understand how to extract data from code, you need to understand the algorithm. There are several standards in the family of QR codes, their basic principles can be found in the specifications. Let me briefly explain: the data that needs to be encoded is divided into blocks depending on the encoding mode. A header is added to the data divided into blocks, indicating the mode and number of blocks. There are also such modes in which more complex structure of information placement is used. These modes will not be considered in view of the fact that it is impractical to extract information from them manually. However, based on the principles described below, it is possible to adapt to these modes.
In case of incorrect data reading, special codes are used in QR that are able to correct the errors in reading. These are the so-called Reed-Solomon codes . The principle of calculating codes, as well as the correction of errors in blocks of information will not be considered, this is the topic of a separate article. Error-correcting Reed-Solomon (RS) codes are recorded after all informational data. This greatly simplifies the task of directly reading information: you can simply read the data without touching the codes. As practice shows, usually most of the QR-matrix is occupied by corrective RS-codes.
According to the standard, the data with RS-codes are “mixed up” before being written to the picture. For these purposes, use a special mask. There are 8 algorithms, among which the best is chosen. Selection criteria are based on a system of penalties, which can also be read in the specification.
“Mixed” data is recorded in a special sequence on a template image, where technical information is added for decoding devices. Based on the described algorithm, it is possible to distinguish a scheme for extracting data from a QR code:

Here, the green felt-tip pen underlines the points that will need to be performed while directly reading the code. The remaining items can be omitted due to the fact that reading is made by a person.
Step 0. QR code

Looking at the pictures, you can see several distinct areas. These areas are used to detect a QR code. These data are of no interest from the point of view of the recorded information, but they need to be deleted or just to remember their location so that they do not interfere. The rest of the code field already contains useful information. It can be divided into two parts: system information and data. There is also information about the code version. The maximum amount of data that can be written to the code depends on the version of the code. When upgrading, special blocks are added, for example, like this:

By them you can navigate and understand what version of QR is in front of you. High version codes are usually also not practical to read manually.
Placement of system information is shown in the figure:

The system information is duplicated, which makes it possible to significantly reduce the probability of errors occurring during code detection and reading. System information is 15 data bits, among which the first 5 are useful information, and the remaining 10 are BCH (15.5) code, which allows to correct errors in the system data. RS codes are also classified as BCH codes. Please note that in the figure the two bars of 15 bits do not intersect.
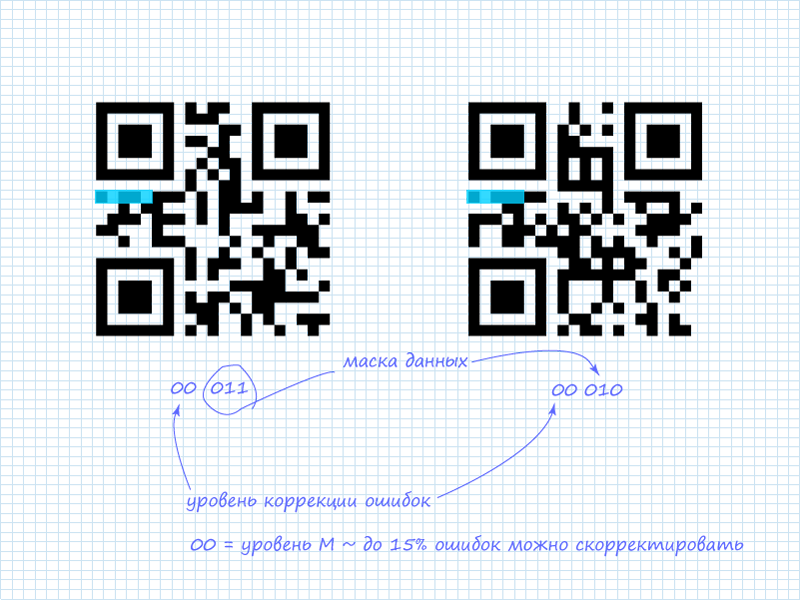
Step 1. Read 5 bits of system information
As already mentioned, only the first 5 bits are of interest. Of which 2 bits indicate the level of error correction, and the remaining 3 bits indicate which mask of the available 8 applies to the data. In the QR codes considered, system information contains:

Step 2. Mask for system information
In addition to the already announced schemes for the protection of system information, in addition, a static mask is used, which is applied to any system information. It looks like: 101010000010010 . Since only the first 5 bits are of interest, the mask can be reduced and easily remembered: 10101 (ten - one hundred one). After applying the operation "exclusive or" (xor) we obtain information.
Possible levels of error correction:
| L | 01 |
| M | 00 |
| Q | eleven |
| H | ten |
Possible masks:
| 000 | (i + j) mod 2 = 0 |
| 001 | i mod 2 = 0 |
| 010 | j mod 3 = 0 |
| 011 | (i + j) mod 3 = 0 |
| 100 | ((i div 2) + (j div 3)) mod 2 = 0 |
| 101 | (ij) mod 2 + (ij) mod 3 = 0 |
| 110 | ((ij) mod 2 + (ij) mod 3) mod 2 = 0 |
| 111 | ((i + j) mod 2 + (ij) mod 3) mod 2 = 0 |
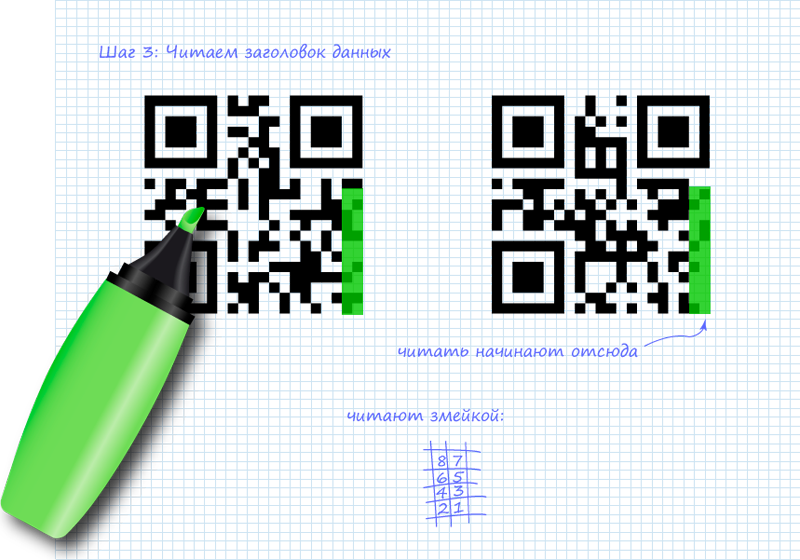
Step 3. Read the data header
To understand what data to deal with, you must initially read a 4-bit header, which contains information about the mode. The specificity of reading data is shown in the picture:
List of possible modes:
| ECI | 0111 |
| Numeric | 0001 |
| Alphanumeric | 0010 |
| 8-bit (byte) | 0100 |
| Kanji | 1000 |
| Structured addition | 0011 |
| FNC1 | 0101 (1st position) 1001 (2nd position) |
Step 4. Apply the mask to the header.
After extracting 4 bits describing the mode, it is necessary to apply a mask to them.
In our case, two masks are used for different codes. The mask is determined by the expression given in the table above. If this expression is reduced to TRUE (true) for a bit with coordinates (i, j) , then the bit is inverted, otherwise everything remains unchanged. The origin in the upper left corner (0,0) . Looking at the expression, you can see patterns in them. For the QR codes in question, the masks will look like this:
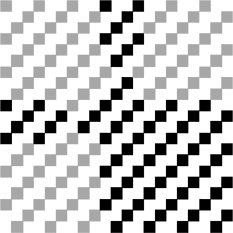

Get the modes:

Step 5. Read data
After receiving the data about the mode, you can start reading the information. It is necessary to stipulate that it is most interesting to read numerical and alphanumeric data, as they are easily interpreted. But also do not be afraid of 8-bit. It can also be easily interpreted information. For example, many online QR text generators are encoded in this mode using ASCII . Another reason why you should initially read the mode is that the number of data packets depends on it. Which also depends on the version of the code. For versions from the first to the ninth block lengths for more readable modes:
| Numeric | 10 bits / 4 bits |
| Alphanumeric | 9 bits |
| 8-bit (byte) | 8 bit |
The first block after the mode pointer is the number of characters. For the numeric mode, the number is encoded in the following 10 bits, and for the 8-bit mode in 8 bits (I apologize for the tautology).

The figure shows that in the left QR code, as noted, the number 5 is recorded. This can be seen from the pointer of the number of characters and 4 bits after it. In the numeric mode, along with 10-bit blocks, 4-bit blocks are used to save space if there is no need for a 10-bit volume. The right code is encrypted 4 characters. At the moment, it is not known what is encrypted in it. Therefore, it is necessary to proceed to reading the next column to extract all 4 blocks of information.

The figure shows, all 4 packages are ASCII codes of Latin letters, forming the word "habr"
Naturally, the best way is to get the phone out of your pocket and, pointing the camera at the QR picture, read all the information. However, in emergency cases, the described method may be useful. Of course, in your head you will not keep all indexes of modes and types of masks, as well as ASCII characters, but remember the popular combinations (at least those that are considered in the article).
Specification:
BS ISO / IEC 18004: 2006. Information technology. Automatic identification and data capture techniques. QR Code 2005 bar code symbology specification. London: BSI. 2007. p. 126. ISBN 978-0-580-67368-9.
PS Follow the resource rules and terms of the Creative Commons Attribution 3.0 Unported (CC BY 3.0)
PPS If you made a mistake with your blog, then tell me where I will transfer it.
Source: https://habr.com/ru/post/127197/
All Articles