microsoft.com: full disclosure of the paths of some files on a web server
I think many will be interested to know how the files are located on the Microsoft website itself. The minor bug I discovered by chance gives some insight into this.
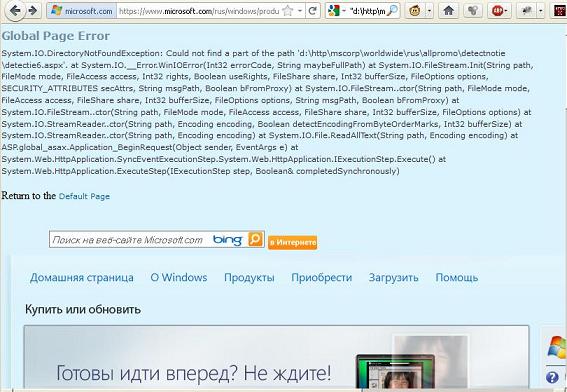
The www.microsoft.com/rus/windows/products/windowsvista/buyorupgrade/windowsanytimeupgrade/default.mspx page gives an error at the top of the page.
System.IO.DirectoryNotFoundException: Could not find a part of the path ' d: \ http \ mscorp \ worldwide \ rus \ allpromo \ detectnotie \ detectie6.aspx '.
After a bit of torment googol there were several more ways: at www.microsoft.com/rus/windows/products/windowsvista/wow
')
d: \ http \ mscorp \ worldwide \ rus \ windows \ products \ windowsvista \ wow \ webtrends.incl
by address (in the source page)
www.microsoft.com/canada/protect/protect- your own malware-or-phishing-scams
d: \ http \ mscorp \ worldwide \ canada \ protect \ protect-yourself \ spam-phishing-scams \ articles \ microsoft-smartscreen-for-urls-helps-you-avoid-websites-may-host-malware -or-phishing-scams.xml
by the address
www.microsoft.com/rus/office/podarki/?0
d: \ http \ mscorp \ worldwide \ rus \ licensing_old \ _components \ WhereToBuyProxy.cs
by the address
www.microsoft.com/Rus/Events/navision060425/default.mspx
d: \ http \ mscorp \ worldwide \ rus \ events \ navision060425 \ default.xml
by the address
www.microsoft.com/Rus/Events/automation060406/default.mspx
d: \ http \ mscorp \ worldwide \ rus \ events \ automation060406 \ default.xml
Facts do not pretend to the news, I think it is nothing more than a curiosity. However, any research and preparation for hacking begins, including with an analysis of the paths, and subsequently knowledge of the paths makes it easier for an attacker to attack. Those who are particularly clever can easily compile a map of the site's directories by comparing URIs with real paths. As you can see, basically, only the Russian segment of the portal suffers from exceptions. Microsoft.com would be better off hiding such things. What is scary full path disclosure can be read here:
hakipedia.com/index.php/Full_Path_Disclosure (English)
www.xakep.ru/post/36176/default.asp - “Path Disclosure: Travel Case”
The www.microsoft.com/rus/windows/products/windowsvista/buyorupgrade/windowsanytimeupgrade/default.mspx page gives an error at the top of the page.
System.IO.DirectoryNotFoundException: Could not find a part of the path ' d: \ http \ mscorp \ worldwide \ rus \ allpromo \ detectnotie \ detectie6.aspx '.

After a bit of torment googol there were several more ways: at www.microsoft.com/rus/windows/products/windowsvista/wow
')
d: \ http \ mscorp \ worldwide \ rus \ windows \ products \ windowsvista \ wow \ webtrends.incl
by address (in the source page)
www.microsoft.com/canada/protect/protect- your own malware-or-phishing-scams
d: \ http \ mscorp \ worldwide \ canada \ protect \ protect-yourself \ spam-phishing-scams \ articles \ microsoft-smartscreen-for-urls-helps-you-avoid-websites-may-host-malware -or-phishing-scams.xml
by the address
www.microsoft.com/rus/office/podarki/?0
d: \ http \ mscorp \ worldwide \ rus \ licensing_old \ _components \ WhereToBuyProxy.cs
by the address
www.microsoft.com/Rus/Events/navision060425/default.mspx
d: \ http \ mscorp \ worldwide \ rus \ events \ navision060425 \ default.xml
by the address
www.microsoft.com/Rus/Events/automation060406/default.mspx
d: \ http \ mscorp \ worldwide \ rus \ events \ automation060406 \ default.xml
Facts do not pretend to the news, I think it is nothing more than a curiosity. However, any research and preparation for hacking begins, including with an analysis of the paths, and subsequently knowledge of the paths makes it easier for an attacker to attack. Those who are particularly clever can easily compile a map of the site's directories by comparing URIs with real paths. As you can see, basically, only the Russian segment of the portal suffers from exceptions. Microsoft.com would be better off hiding such things. What is scary full path disclosure can be read here:
hakipedia.com/index.php/Full_Path_Disclosure (English)
www.xakep.ru/post/36176/default.asp - “Path Disclosure: Travel Case”
Source: https://habr.com/ru/post/126987/
All Articles