What is Prey and how it hunts for your computer

Good day reader.
Recently, on Habré, messages about how people find their stolen computer with the help of some magical services, presenting all the information about the attacker on a silver platter, have become frequent.
This is primarily about the events described here and here , but for those who like to do everything with their own hands
')
For some reason it seemed to me that there are reviews of such programs here, but the search did not give out anything, and I decided to tell the public about the wonderful service Prey . For those who know about him, use it, or some other suggest reading the conclusion of the article. There is some information about camels for all users of similar products.
For those who are interested in the details - I ask under the cat.
Briefly and clearly about the service stated on their website:
Prey allows you to keep track of your phone or laptop all the time and help you find if they are lost or stolen. This is an easy open source development, besides absolutely free. It just works.
What it is
Prey is a program that, while running on a computer / phone, sits quietly and keeps quiet, and in case of loss, at the signal of the host, begins to quietly follow the actions of the current user (will not be like some individuals and say “thief” - maybe it will be a person who looking for how to contact you). But first things first.
A few common words:
- Prey is an open source project located on Github.
- Everything is written mostly in Bash. Perl and Python present
- 2.5 year project (the first commit was on February 18, 2009)
- Cross-platform client. On the official website are available for download versions for Windows, Linux (separate package for Ubuntu), Mac OS, link to Android Market
- Current version 0.5.3
Next, I will do a review based on the Mac version, however, for Windows and Linux, everything is different only at the level of the installer.
Installation
When you start the installation, you will be asked to choose two options for setting up - to work through your personal account, or to send reports directly to the mail.
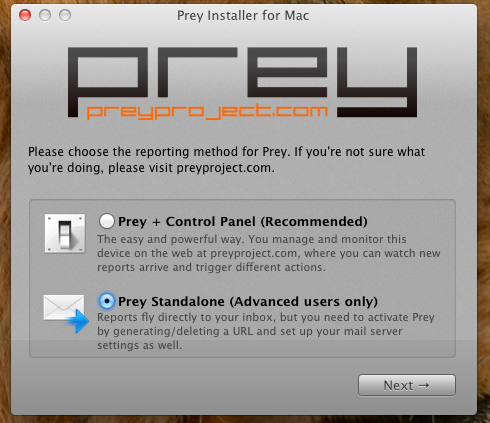
About the second option is to talk more. Here you need to specify the URL that the program will check for availability at a specified interval, as soon as the page is gone - starts monitoring. Well, it is natural to specify the SMTP details for sending mail.

After selecting the type of installation, entering account data or registering on preyproject.org (in the Prey + Control Panel version) and administrator password (to be able to run as root), the installation takes place. Further, in Mac OS (and Linux for sure), he settles in cron:
*/20 * * * * /usr/share/prey/prey.sh > /var/log/prey.logThis completes the installation. Prey has one small side effect caused by a cron settlement - it is not on the list of installed programs, but this is rather a plus. The removal does not take place through the basket, but with the help of the uninstaller that comes with the installer.
Control Panel
I did not use Standalone mode, so for those who work with it, please write in the comments how everything happens there.
So, having entered the control panel, we are shown general information about the attached devices, a button for adding a new one (although when they click on it they offer to connect the device during installation) and unobtrusive advertising of the pro-account. In general, nothing superfluous - everything is in moderation, intuitively clear, and most importantly - only the main thing.

Next, when you click on the name, the Prey copy control panel on this device opens. There are four tabs, which hide the settings and information about the device. On the left, a bit of general information quietly hangs, a list of reports and a device unlink button.
Unfortunately, I do not have a pro-account, and therefore some functions are not available to me, but you can read about them. At the end of the article I will give a short list of what you can do if you pay denyushku. Functions available in a paid subscription I will mark with an asterisk.
basic settings
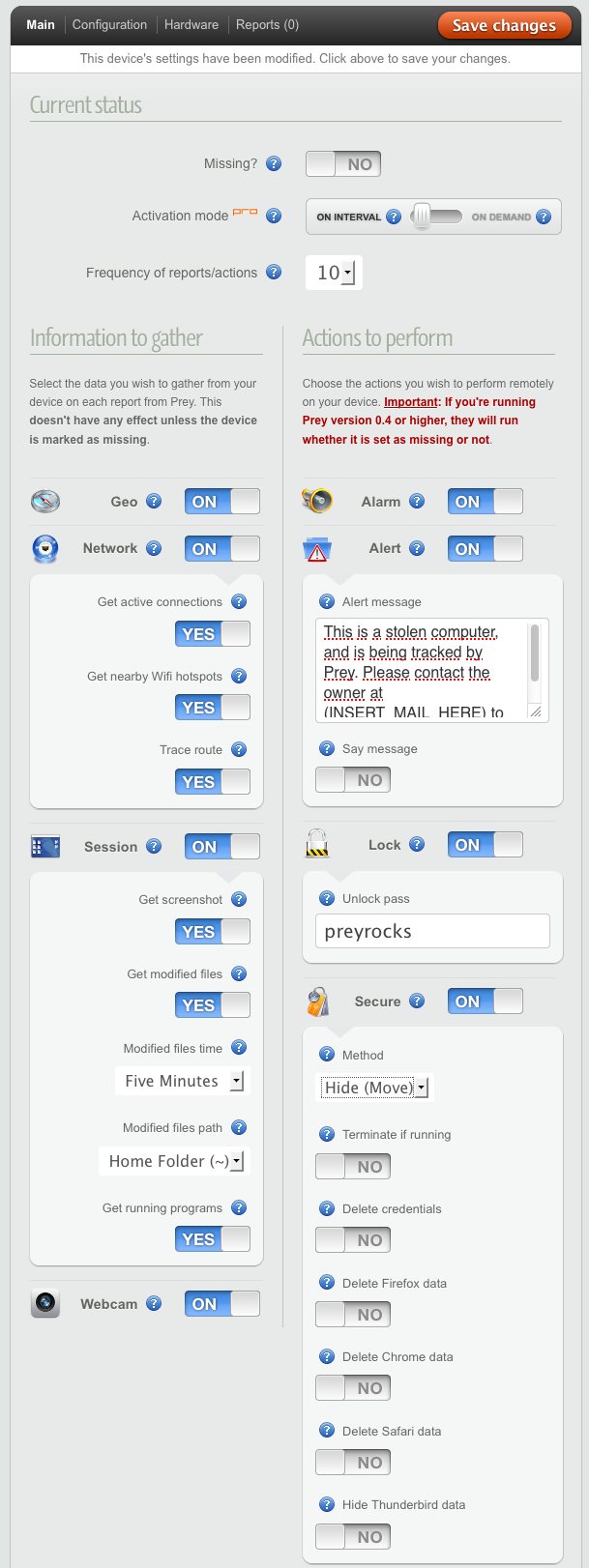
There are quite a few basic settings, everything is grouped.
At the very top are the current status settings, where you can “report” about the loss, change the update interval, request a report immediately (*).
Further settings are divided into two columns: information to collect, and actions to perform.
Information for collection:
- Information about your current location. GeoIP or built-in GPS
- Network information: active connections, Wi-Fi point information, tracing
- Information about the current session: a screenshot, running processes, information about modified files: period, folder for monitoring
- Snomok from camera
Steps to perform:
- Make sounds every 30 seconds
- Print a text message (where you can specify the coordinates or an ultimatum), speak this message
- Lock the device before entering the specified password
- You can delete or move (optionally) passwords, cookies, profiles Firefox, Safari, Chrome, Thunderbird
Configuration
Here is the configuration for the control panel and the script itself.
In addition, there are settings for the script itself:
- * Reports are sent over SSL
- * Encrypt instructions. Apparently for protection when transferring from server
- * Periodically scan the computer's hardware.
- * Automatic update
- Ability to work on the latest configuration received offline
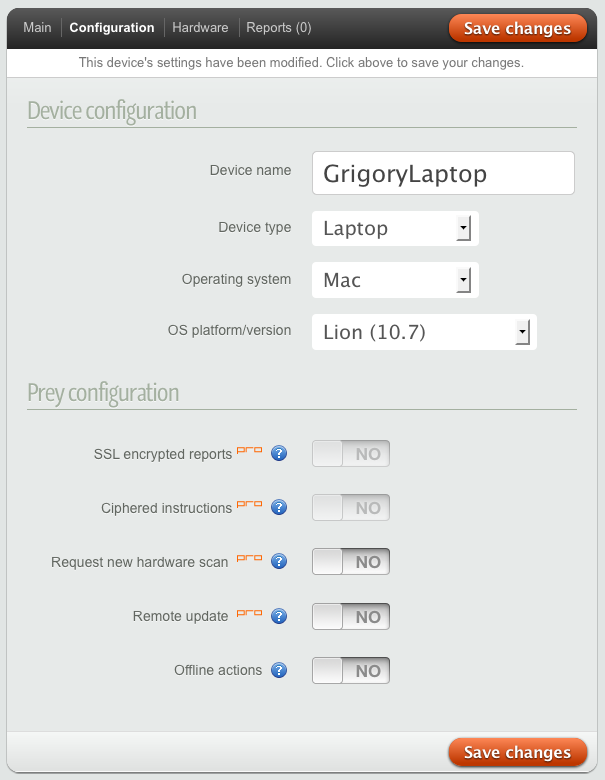
I note that Prey did not notice the update to OS X Lion - I had to change the pens.
Iron
There is nothing much to talk about, everything is very simple and clear.
So we got to the most interesting place for which everything was started!
Report
There is a lot of various information in the report (although it all depends on what was selected in the settings), so we will analyze in parts everything that I received.
When viewing a report, the information on the left is replaced with information about IP (private, public, gateway) and MAC addresses.
At the very beginning of the report, in the part of the proudly named Location , there is a map with the plotted intended location of the device. Presumptive because in this case he missed half a kilometer.

Below are a picture with a photo camera (if any) and a screenshot in Picture and Screenshot . I will not show here for two reasons - I did not make it in the photo, but on the screen is personal information.
Next come the blocks of information already for those who more or less understand what is written in them. I’ll go over them quickly and give pieces of information, because the majority of habrazhiteli and as clear as it looks.
Under the heading Uptime, it is expected that there is data about uptime of the system:
11:20 up 4 days, 11:52, 2 users, load averages: 0.21 0.42 0.39Under the heading Running Programs is a list of all running programs:
USER PID %CPU %MEM VSZ RSS TT STAT STARTED TIME COMMAND
...
grigory 1212 0.0 0.9 2520340 19316 ?? S Sun02PM 0:04.65 .../MacOS/Terminal -psn_0_491640
...
The Logged User section contains a list of all logged in users:
grigoryNext, the Logged User contains the output of the netstat command:
Active Internet connections (including servers)
Proto Recv-Q Send-Q Local Address Foreign Address (state)
...
tcp4 0 0 grigorylaptop.im.56649 checkip-pao.dynd.http LAST_ACK
tcp4 0 0 grigorylaptop.im.56392 186-011.skype.qu.34051 ESTABLISHED
...
Also there is information about the Wi-Fi network (if connected to it, of course):
agrCtlRSSI: -57
agrExtRSSI: 0
agrCtlNoise: -91
agrExtNoise: 0
state: running
op mode: station
lastTxRate: 18
maxRate: 54
lastAssocStatus: 0
802.11 auth: open
link auth: wpa2-psk
BSSID: 00:**:**:**:**:**
SSID: ******
MCS: -1
channel: 11
The Complete Trace block contains tracing to google.com:
traceroute: Warning: www.google.com has multiple addresses; using 74.125.232.18
traceroute to www.l.google.com (74.125.232.18), 64 hops max, 52 byte packets
1 .....
.....
6 *
7 msk-ix-gw1.google.com (193.232.244.232) 36.192 ms
8 *
9 74.125.232.18 (74.125.232.18) 33.950 msThis concludes the report, although it seems to me that this information is also sufficient.
pros
Regarding the benefits, I think everything is clear from the above, but there is one point that I would like to consider separately.
In the discussions, news about a network security expert expressed that someday the creators of the Prey would begin to monitor the user himself without his knowledge. In my opinion, with open source codes coupled with the Standalone mode, this situation becomes unlikely, but if paranoia really came up - correct the source code, removing the code for communicating with their server from there and there will be happiness.
Minuses
The advantages of using Prey are described, but by the way there are no minuses, that is, they certainly exist, but I have been overlooked. There is one unpleasant moment in the free version: the Control Panel is working over HTTP, but most likely I just overlooked them with my attention.
Pro account
With a paid subscription, all of the following options become available:
- Report on request
- Reports are transmitted via SSL (the site says "Full SSL encryption", apparently, the Control Panel will be via HTTPS)
- Encrypt instructions. Apparently for protection when transferring from server
- Periodically scan the computer's hardware.
- Automatic update
- Device Activity Monitor
- Report collection interval can be reduced to two minutes.
- Automatic installation on multiple devices
Are you a camel?
What is a camel? - you ask. It’s nice to keep track of your computer, to come up with a statement on a robber and a couple of reports, of course you can. But all this is there, abroad, and in our beloved Motherland everyone can understand exactly the opposite. Therefore, I suggested to glazkova to paint a picture of the harsh reality examined through the prism of Russian legislation. At the time of writing, Maria said that the article is under construction. So we calmly wait and DO NOT KNOW about this.
About yourself instead of the conclusion
I started using this service about two months ago - I installed it right after buying a laptop, and at the same time I threw it on HTC Desire. I must say that I remembered about them when I read about that London specialist . Everything is clear about computers - there he sits in cron and calmly does his job, but I don’t know about Android how everything works (there’s no time to pick the sources), but I can say the main thing - it doesn’t create problems with the battery and performance.
Due to the specifics of the service, it is difficult to say something about the comfort of use. In my unprofessional opinion, the work of the service does not cause any complaints except one: the control panel sometimes slows down - apparently they already have quite a lot of users, and the servers start failing to cope with the load. Everything else is wonderful.
UPD 1. Since comments in the style of “Duck they otfarmatirovat disk and everything.”, “Password root turns in three clicks,” I want to say that at the beginning of the post it is not by chance that there are links to articles from which it is clear that such people were, are, and the most important will be. Therefore, it makes sense to have such a program in your arsenal.
UPD 2. The article by glazkova on the legal aspects of the actions of the owners of laptops in case of their theft is ready.
Source: https://habr.com/ru/post/126841/
All Articles