Basics of biometrics
This article is to some extent a continuation of the past , and to some extent, its prequal. Here I will talk about the basics of building any biometric system and about what was left behind the frame of the previous article, but was discussed in the comments. The emphasis is not on the biometric systems themselves, but on their principles and scope.
For those who have not read the article, or have already forgotten - I advise you to look at what FAR and FRR are, as these concepts will be used here.
Any person authentication is based on three traditional principles:
1) By property . Property may include a pass, plastic card, key or civil documents.
2) By knowledge . Knowledge includes passwords, codes, or information (for example, mother's maiden name).
3) According to biometric characteristics . In more detail about what biometric characteristics happen I spoke in the previous article.
')
These three principles can be used separately or used in groups. This methodology generates two main directions of biometrics.
Verification is the confirmation of a person’s identity through a biometric attribute, where the primary authentication was performed using one of the first two methods mentioned above. The simplest verifier can be called a border guard verifying your face with your passport. Verification implies a significantly greater system reliability. The probability that the system will miss an intruder who does not use a means of overcoming is equal to the FAR of the biometric method used. Even for the weakest biometric systems, this probability is negligible. The main disadvantages of verification are two points. The first is that a person needs to carry a document with him or remember a system password. There is always the problem of losing or forgetting information. Also verification is fundamentally impossible for covert authentication.
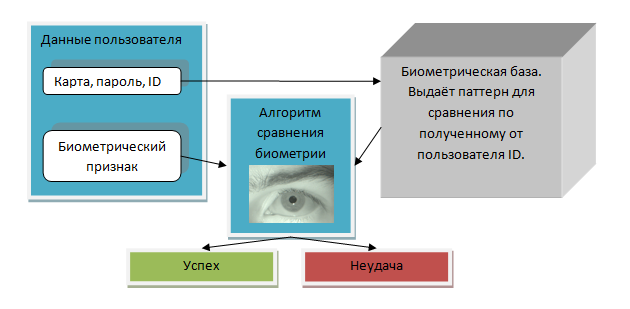
The operation of the access system based on biometric verification can be represented as follows:
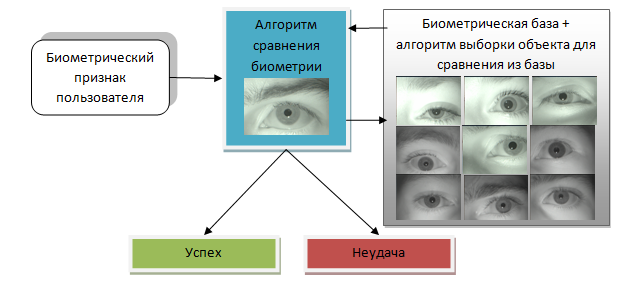
Biometric identification is the use of a biometric feature that does not require additional information. Object search is carried out across the entire database and does not require a preliminary key. It is clear that the main disadvantage of this is that the more people in the database, the greater the likelihood of false access of an arbitrary person. In the last article, we estimated the likelihood of such access when designing systems. For example, the system on the fingers makes it possible to contain a database of no more than 300 people, no more than 3000 in the eyes. Plus identification - all the keys will always be with you, no passwords or cards are needed.
Unlike verification, identification can be secretive to a person. How is it possible and is it worth being afraid of it? I will try to briefly tell the thoughts that occur among people involved in biometrics. In the last article, this thought remained unfinished.
Consider technologies that can allow at least in some cases covertly from a person to determine his personality. First of all, you should immediately discard all contact methods. Placing fingerprint scanners in the door handles is not a good idea. They are noticeable, many do not touch pens, contact scanners get dirty, and so on. Secondly, you can immediately discard methods where the maximum range is limited to 10-15 centimeters (for example, hand veins). Third, you can drop all dynamic biometrics, since FAR and FRR are too low.
Only two technologies remain. These are technologies where cameras act as data scanners: face recognition (2D, 3D) and iris recognition.
The first of these, recognition by 2D entities, has been repeatedly tried to implement (because of its simplicity), but all the time without success. This is due to the low statistical parameters of the system. If there are only 100 people in the base of wanted personalities, then every 10 passersby will be wanted. Even a policeman in the metro efficiency is much higher.
The following two technologies are very similar. Both can be used away from the person, but both must have a sufficient amount of equipment. Both the 3D face scanner and the iris scanner can be placed in places with narrow aisles. These are escalators, doors, stairs. An example of such a system is the system created by SRI International (now they have a dead site, but there is practically an analogue from AOptix ). I'm not 100% sure that the system from SRI International is working, there are too many errors in the video, but the basic possibility of creation exists. The second system works, although there is too low speed for a covert system. 3D face scanners work on the same principle: detection in a narrow passage. In the case of a 3D face and eye recognition, the reliability of work is quite high. If the base is 100 criminals, then only every 10,000 civilians will have to be checked, which is already quite effective.
The key feature of any hidden biometrics is that a person should not know about it. It is possible to insert lenses into the eyes, or to change the shape of the face with several patches imperceptibly to others, but noticeably for the biometric system. For some reason I have a suspicion that in the near future the demand for lenses that change the iris will increase significantly. The demand for bandanas has increased in Britain. And the events there are only the first swallows of biometrics.
Any biometric system will consist of several elements. In some of the systems, individual elements are spliced, in some they are separated into different elements.

If the biometric system is used only on one pass, then it makes no difference whether the system is divided into parts or not. On the spot, you can add a person to the database and check it. If there are several pass-throughs, then it is unreasonable to store a separate database on each pass-through. Moreover, such a system is not dynamic: adding or removing users requires crawling all scanners.
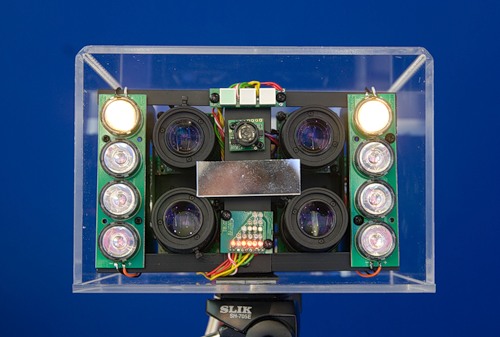
A biometric scanner is a part of any biometric system, without which it cannot exist. In some systems, a biometric scanner is just a video camera, and in some (for example, retinal scanners), it is a complex optical complex. The two main characteristics of a biometric scanner are its operating principle (contact, contactless) and its speed (the number of people per minute that it can serve). For those biometric characteristics whose use has already returned to normal, the scanner can be purchased separately from the logical system. If the scanner is physically divided with the comparison algorithm and the base, then the scanner can perform the initial processing of the obtained biometric characteristic (for example, for the eye, this is the selection of the iris). This action is performed in order not to overload the communication channel of the scanner and the main base. Also, in a scanner separated from the base, a data encryption system is usually built in to secure the transmission of biometric data.
These two parts of the biometric system usually live in the neighborhood and often complement each other. For some biometric features, the comparison algorithm may perform optimized searches on the database (finger comparison, face comparison). And in some (eyes), for a full comparison, in any case, he needs to go around the entire base.
The comparison algorithm has many characteristics. Its two main characteristics, FAR and FRR largely determine the biometric system. It is also worth noting:
1) Work speed. For some comparisons (eyes), the speed of work can reach hundreds of thousands of comparisons per second on a regular computer. This speed is enough to provide any needs of users, without noticing the time delay. And for some systems (a 3D face), this is already a significant enough characteristic of the system, which requires a lot of computational power to maintain the speed of work while increasing the base.
2) Convenience of work. In fact, the convenience of any system is largely determined by the ratio FAR, FRR. In the system, we can slightly change their value, so as to focus on speed or reliability. Roughly speaking, it turns out like this:
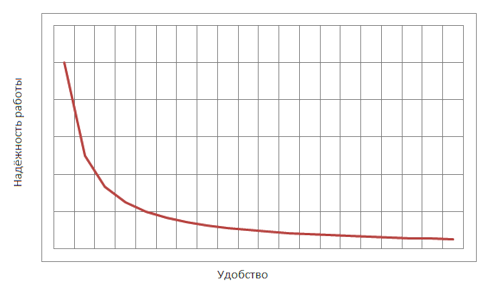
If we want a high level of reliability, we choose the position in its left part. And if there are few users, good indicators will be on the right side of the graph, where there will be high characteristics of convenience, and therefore high speed of work.
After comparison, the biometric system should give the results of the comparison to the governing bodies. Then it can be like the "open the door" command, and the information "such-and-such came to work." But what further to do with this information must be the installers of the system. But here it is not so simple, it is necessary to take into account the possibilities of attack:
Despite the fact that many biometric systems are equipped with algorithms that can determine the attack on them, it is not enough to be light-hearted about security. The simplest attack on an identification system is a multiple scan. Suppose the situation: in the company serves about a hundred people. The attacker approaches the biometric pass system and repeatedly scanned on it. Even for reliable systems, a couple of thousands of scans may be a false definition and pass the attacker to the object. To avoid this, many systems track failed scans and after 10–15 attempts to block input. But in cases where the system can not do this - this task falls on the user. Unfortunately, this is often forgotten.
The second method of attacking a biometric system is faking a scanned object. In case the system has anti-counterfeit algorithms, it is important to react correctly to them. Typically, these algorithms are also probabilistic and have their FAR and FRR. So do not forget to track the signals about the attack in time and send the guard.
In addition to attacks on the system itself, it is possible to attack the environment of the system. Once we came across a funny situation in this country. Many integrators do not really bother with data transfer. They use the standard Wiegand protocol for transmission. At the same time, they don’t even encrypt it, especially in most cases. So it is easier not to deceive the system, but to find the wire and send the key through it ...
I hope that my thoughts on what biometrics is like and what it is eaten with will someday help you. Or in order to set up such a system for yourself, or to deceive someone else's)
For those who have not read the article, or have already forgotten - I advise you to look at what FAR and FRR are, as these concepts will be used here.
General concepts
Any person authentication is based on three traditional principles:
1) By property . Property may include a pass, plastic card, key or civil documents.
2) By knowledge . Knowledge includes passwords, codes, or information (for example, mother's maiden name).
3) According to biometric characteristics . In more detail about what biometric characteristics happen I spoke in the previous article.
')
These three principles can be used separately or used in groups. This methodology generates two main directions of biometrics.
Verification
Verification is the confirmation of a person’s identity through a biometric attribute, where the primary authentication was performed using one of the first two methods mentioned above. The simplest verifier can be called a border guard verifying your face with your passport. Verification implies a significantly greater system reliability. The probability that the system will miss an intruder who does not use a means of overcoming is equal to the FAR of the biometric method used. Even for the weakest biometric systems, this probability is negligible. The main disadvantages of verification are two points. The first is that a person needs to carry a document with him or remember a system password. There is always the problem of losing or forgetting information. Also verification is fundamentally impossible for covert authentication.
The operation of the access system based on biometric verification can be represented as follows:

Identification
Biometric identification is the use of a biometric feature that does not require additional information. Object search is carried out across the entire database and does not require a preliminary key. It is clear that the main disadvantage of this is that the more people in the database, the greater the likelihood of false access of an arbitrary person. In the last article, we estimated the likelihood of such access when designing systems. For example, the system on the fingers makes it possible to contain a database of no more than 300 people, no more than 3000 in the eyes. Plus identification - all the keys will always be with you, no passwords or cards are needed.

Covert identification
Unlike verification, identification can be secretive to a person. How is it possible and is it worth being afraid of it? I will try to briefly tell the thoughts that occur among people involved in biometrics. In the last article, this thought remained unfinished.
Consider technologies that can allow at least in some cases covertly from a person to determine his personality. First of all, you should immediately discard all contact methods. Placing fingerprint scanners in the door handles is not a good idea. They are noticeable, many do not touch pens, contact scanners get dirty, and so on. Secondly, you can immediately discard methods where the maximum range is limited to 10-15 centimeters (for example, hand veins). Third, you can drop all dynamic biometrics, since FAR and FRR are too low.
Only two technologies remain. These are technologies where cameras act as data scanners: face recognition (2D, 3D) and iris recognition.
The first of these, recognition by 2D entities, has been repeatedly tried to implement (because of its simplicity), but all the time without success. This is due to the low statistical parameters of the system. If there are only 100 people in the base of wanted personalities, then every 10 passersby will be wanted. Even a policeman in the metro efficiency is much higher.
The following two technologies are very similar. Both can be used away from the person, but both must have a sufficient amount of equipment. Both the 3D face scanner and the iris scanner can be placed in places with narrow aisles. These are escalators, doors, stairs. An example of such a system is the system created by SRI International (now they have a dead site, but there is practically an analogue from AOptix ). I'm not 100% sure that the system from SRI International is working, there are too many errors in the video, but the basic possibility of creation exists. The second system works, although there is too low speed for a covert system. 3D face scanners work on the same principle: detection in a narrow passage. In the case of a 3D face and eye recognition, the reliability of work is quite high. If the base is 100 criminals, then only every 10,000 civilians will have to be checked, which is already quite effective.
The key feature of any hidden biometrics is that a person should not know about it. It is possible to insert lenses into the eyes, or to change the shape of the face with several patches imperceptibly to others, but noticeably for the biometric system. For some reason I have a suspicion that in the near future the demand for lenses that change the iris will increase significantly. The demand for bandanas has increased in Britain. And the events there are only the first swallows of biometrics.
Model of biometric access system and its parts
Any biometric system will consist of several elements. In some of the systems, individual elements are spliced, in some they are separated into different elements.

If the biometric system is used only on one pass, then it makes no difference whether the system is divided into parts or not. On the spot, you can add a person to the database and check it. If there are several pass-throughs, then it is unreasonable to store a separate database on each pass-through. Moreover, such a system is not dynamic: adding or removing users requires crawling all scanners.
Biometric scanner

A biometric scanner is a part of any biometric system, without which it cannot exist. In some systems, a biometric scanner is just a video camera, and in some (for example, retinal scanners), it is a complex optical complex. The two main characteristics of a biometric scanner are its operating principle (contact, contactless) and its speed (the number of people per minute that it can serve). For those biometric characteristics whose use has already returned to normal, the scanner can be purchased separately from the logical system. If the scanner is physically divided with the comparison algorithm and the base, then the scanner can perform the initial processing of the obtained biometric characteristic (for example, for the eye, this is the selection of the iris). This action is performed in order not to overload the communication channel of the scanner and the main base. Also, in a scanner separated from the base, a data encryption system is usually built in to secure the transmission of biometric data.
Comparison Algorithm + Database
These two parts of the biometric system usually live in the neighborhood and often complement each other. For some biometric features, the comparison algorithm may perform optimized searches on the database (finger comparison, face comparison). And in some (eyes), for a full comparison, in any case, he needs to go around the entire base.
The comparison algorithm has many characteristics. Its two main characteristics, FAR and FRR largely determine the biometric system. It is also worth noting:
1) Work speed. For some comparisons (eyes), the speed of work can reach hundreds of thousands of comparisons per second on a regular computer. This speed is enough to provide any needs of users, without noticing the time delay. And for some systems (a 3D face), this is already a significant enough characteristic of the system, which requires a lot of computational power to maintain the speed of work while increasing the base.
2) Convenience of work. In fact, the convenience of any system is largely determined by the ratio FAR, FRR. In the system, we can slightly change their value, so as to focus on speed or reliability. Roughly speaking, it turns out like this:

If we want a high level of reliability, we choose the position in its left part. And if there are few users, good indicators will be on the right side of the graph, where there will be high characteristics of convenience, and therefore high speed of work.
"Do something"
After comparison, the biometric system should give the results of the comparison to the governing bodies. Then it can be like the "open the door" command, and the information "such-and-such came to work." But what further to do with this information must be the installers of the system. But here it is not so simple, it is necessary to take into account the possibilities of attack:
Attack on the biometric system
Despite the fact that many biometric systems are equipped with algorithms that can determine the attack on them, it is not enough to be light-hearted about security. The simplest attack on an identification system is a multiple scan. Suppose the situation: in the company serves about a hundred people. The attacker approaches the biometric pass system and repeatedly scanned on it. Even for reliable systems, a couple of thousands of scans may be a false definition and pass the attacker to the object. To avoid this, many systems track failed scans and after 10–15 attempts to block input. But in cases where the system can not do this - this task falls on the user. Unfortunately, this is often forgotten.
The second method of attacking a biometric system is faking a scanned object. In case the system has anti-counterfeit algorithms, it is important to react correctly to them. Typically, these algorithms are also probabilistic and have their FAR and FRR. So do not forget to track the signals about the attack in time and send the guard.
In addition to attacks on the system itself, it is possible to attack the environment of the system. Once we came across a funny situation in this country. Many integrators do not really bother with data transfer. They use the standard Wiegand protocol for transmission. At the same time, they don’t even encrypt it, especially in most cases. So it is easier not to deceive the system, but to find the wire and send the key through it ...
I hope that my thoughts on what biometrics is like and what it is eaten with will someday help you. Or in order to set up such a system for yourself, or to deceive someone else's)
Source: https://habr.com/ru/post/126774/
All Articles