Exploited vulnerability in Mail.ru mail
Hearing today on one of the news sites that Mail.ru updated their search interface, I went there to see it.
I did not see anything new in the interface, there were no letters in the "Inbox". Lazily clicked on the spam daddy, looked at the letters and ... Found that a new letter had arrived. The letter was from Mail Delivery System (Mailer-Daemon@prof1.mail.ru). It contained a message that my letter was not delivered to a lot of recipients due to the fact that it was considered spam. I considered myself sane enough to understand that I did not send such a letter.
If you are interested in the preface, I will continue.
')
He returned to "Spam" on the same letter, pressed "F5". New spam letter. Looked at the source of the letter. I quote only the body:
Unpacking BASE64 we get the following HTML code:
Nothing really scary. Reference, picture. HTML body is different from text. Never mind.
I looked at the source of the page itself mail.ru ... And there among a lot of garbage code:

Also, as it turned out, there is nothing terrible here.
And the problem lies in this very picture, friend.gif. In the presence of a referrer from mail.ru, it gives a redirect to
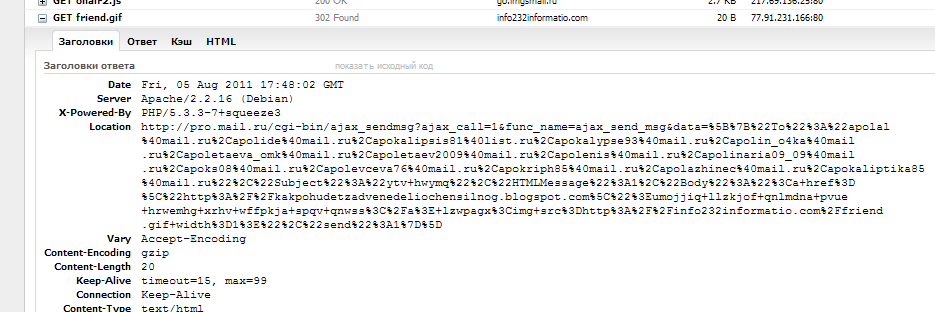
And this GET request (!) Sends mail to a large number of recipients.
Hopefully, the problem will be fixed quickly. I will send a copy to Mail.ru, I share it with a respected community, because vulnerability is already exploited.
The moral of this fable is simple. You should always comply with the RFC, according to which GET requests should not change the state of the server. Hopefully novice developers will correctly understand the importance of this simple rule.
I did not see anything new in the interface, there were no letters in the "Inbox". Lazily clicked on the spam daddy, looked at the letters and ... Found that a new letter had arrived. The letter was from Mail Delivery System (Mailer-Daemon@prof1.mail.ru). It contained a message that my letter was not delivered to a lot of recipients due to the fact that it was considered spam. I considered myself sane enough to understand that I did not send such a letter.
If you are interested in the preface, I will continue.
')
He returned to "Spam" on the same letter, pressed "F5". New spam letter. Looked at the source of the letter. I quote only the body:
----ALT--ZBQj2NTm1312448872
Content-Type: text/plain; charset=koi8-r
Content-Transfer-Encoding: base64
dnRpankgZml1cHcga3ZrZHpvIHNsc2J2ciBxY25odCA=
----ALT--ZBQj2NTm1312448872
Content-Type: text/html; charset=koi8-r
Content-Transfer-Encoding: base64
CjxIVE1MPjxCT0RZPnZ0aWp5IGZpdXB3IDxhIGhyZWY9Imh0dHA6Ly9wb2h1ZGV0Zm9ydW1mb3Rr
aW0uYmxvZ3Nwb3QuY29tIj5rdmtkem8gc2xzYnZyIHFjbmh0IDwvYT48aW1nIHNyYz1odHRwOi8v
aW5mbzIzMmluZm9ybWF0aW8uY29tL2ZyaWVuZC5naWYgd2lkdGg9MT48L0JPRFk+PC9IVE1MPgo=
----ALT--ZBQj2NTm1312448872--
Unpacking BASE64 we get the following HTML code:
<HTML><BODY>vtijy fiupw <a href="http://pohudetforumfotkim.blogspot.com">kvkdzo slsbvr qcnht </a><img src=http://info232informatio.com/friend.gif width=1></BODY></HTML>
Nothing really scary. Reference, picture. HTML body is different from text. Never mind.
I looked at the source of the page itself mail.ru ... And there among a lot of garbage code:

Also, as it turned out, there is nothing terrible here.
And the problem lies in this very picture, friend.gif. In the presence of a referrer from mail.ru, it gives a redirect to

And this GET request (!) Sends mail to a large number of recipients.
Hopefully, the problem will be fixed quickly. I will send a copy to Mail.ru, I share it with a respected community, because vulnerability is already exploited.
The moral of this fable is simple. You should always comply with the RFC, according to which GET requests should not change the state of the server. Hopefully novice developers will correctly understand the importance of this simple rule.
Source: https://habr.com/ru/post/126740/
All Articles