Admission to the department of information security in Moscow State Technical University named after NE Bauman through the program “Step into the Future. Moscow"
Good day everyone.
In this article I want to continue the popularization of the program “Step into the Future”, started last night by the user vaboretti, as well as dispel the myth that it is impossible for an ordinary person to enter the department IU8 at MSTU.

To begin with, briefly about the program: “The Russian scientific and social program for young people and schoolchildren“ Step into the Future ”is a whole complex of all kinds of research aimed at the following goals:
Here is a brief information about the recruitment of this year: about 25,000 applications were submitted to 115 departments (if you suddenly confused the numbers, please forgive. Error + 5%). Of these 25,000 applications, more than 2,000 are for the IU-8 “Information Security” department only. Budget places in the department 80.
Good news: 41 out of 80 budget places are the winners and prize-winners of the Step. Another 27 - beneficiaries and target, and only 12 - for the total set.
')
The Olympiad takes place in two stages: the defense of the project and the competition in physics. Both tests are rated at a maximum of 50 points, i.e. 100 points in total - maximum. Then the participant who scores the passing points for each trial receives a benefit of some type:
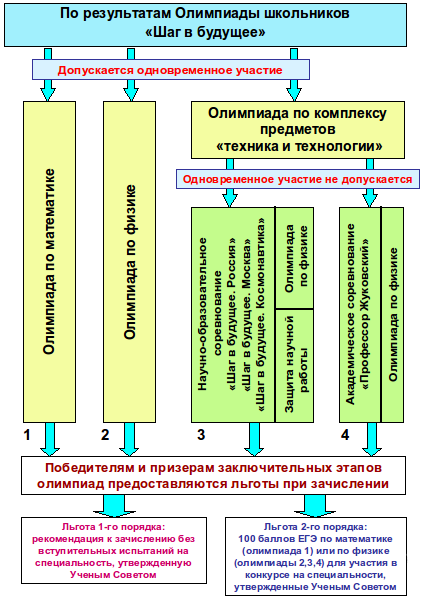
On the competition in physics can not talk. I think, so everyone understands everything: the usual Olympiad (test work in physics).
The main (and most difficult) part of the Olympiad is project defense. Actually, the defense is as follows: at the table sit the jury members, before whom it is necessary to fully present their project, i.e. explain its pros / cons, newness, uniqueness, etc. etc. Depending on how serious the project is and how effectively its presentation takes place, the jury will award points.
The topic of the project was recommended by my supervisor. The work was called “Software of an automated workplace of the expert in enciphering and masking of information“, and represented the software written only by me (ie without use of another's codes).
I decided to write in C # as the most appropriate and fast-learning language.
For writing the program used the following literature:
The general plan of the program is approximately as follows:
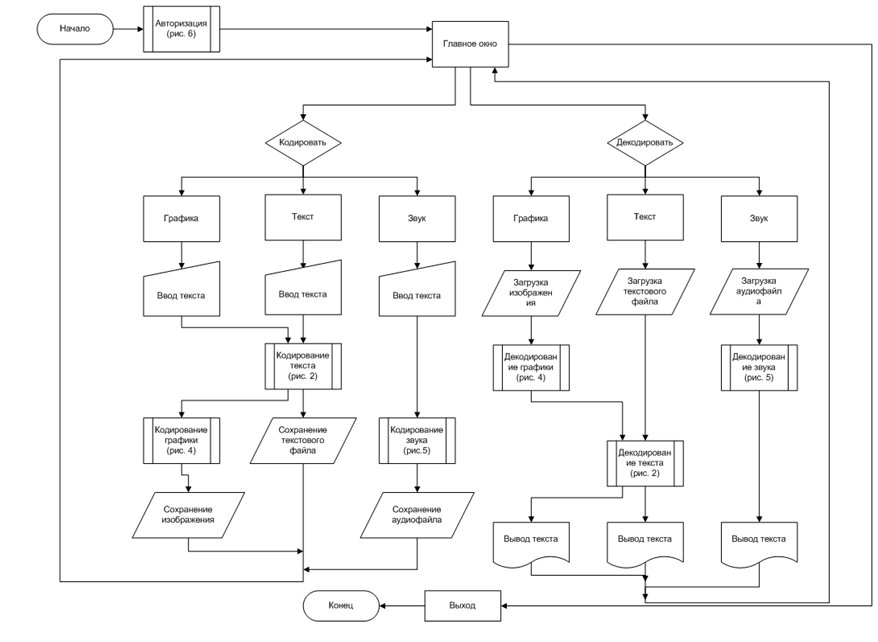
The main essence of the project, as seen on the diagram above, was to impose several encryption methods on top of one another.
Security encryption was carried out by imposing an unlimited number of ciphers of each type on each other:
At the same time, an extensive cipher library was used, adapted specifically for understanding by the program.
Over the search and adaptation of ciphers worked a little over a month.
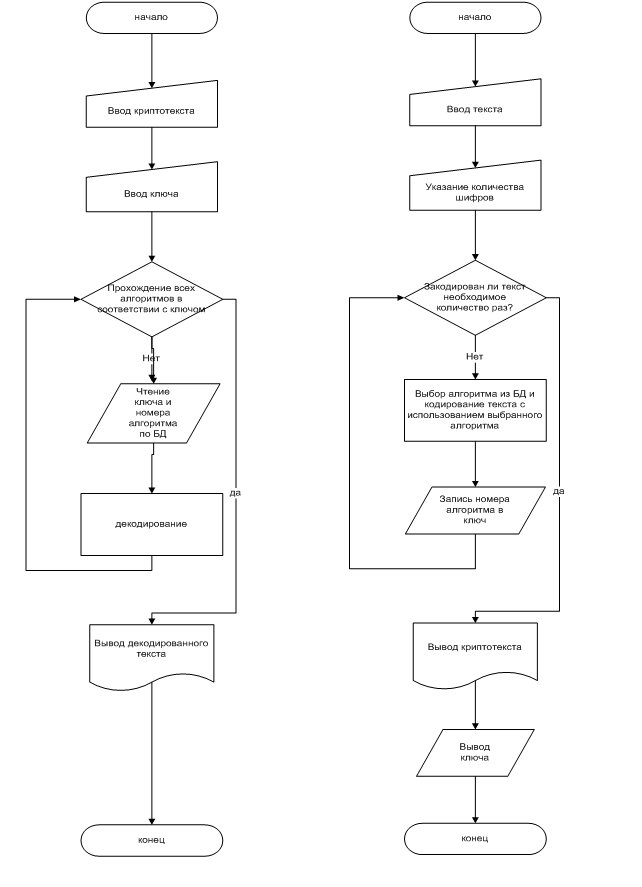
For example, below is the scheme with the possible number of combinations of decrypting the source text, encrypted with different numbers of ciphers of the same type (ie, only text, only graphics, or only sound):

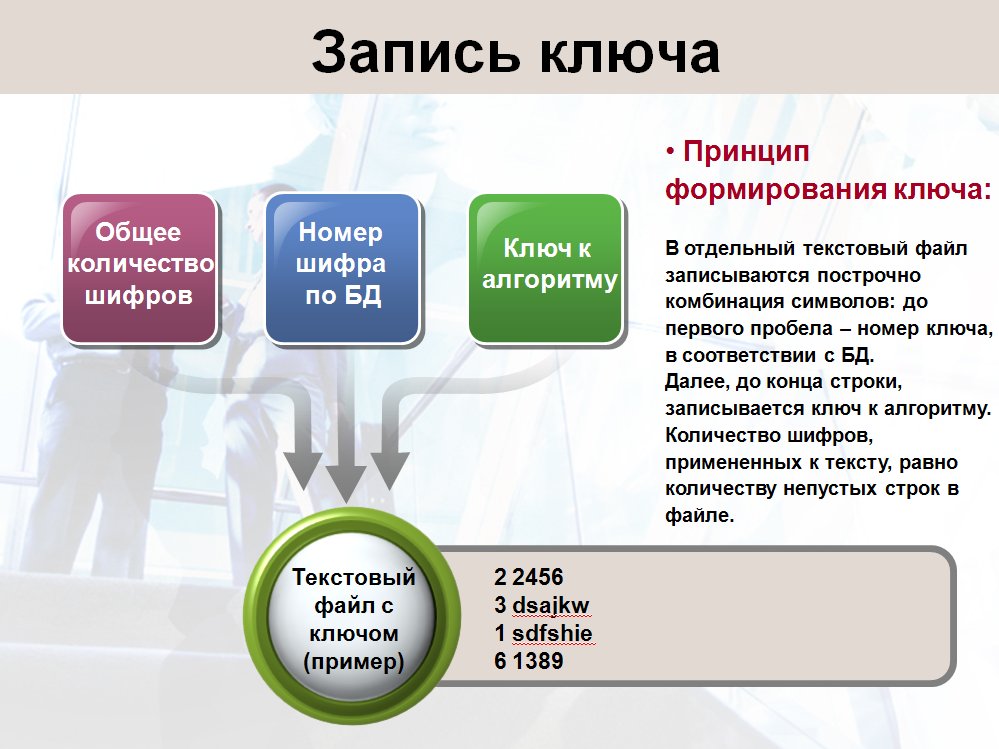
To write the key, it was decided to use a separate text file in which all numbers of all encryption algorithms with the keys to each algorithm were recorded. Accordingly, decryption occurred in the reverse order using the key file:
True, on the night before the defense, the long-awaited insight had come down, and another module was added to the program, allowing to encrypt not only graphics / text / sound, but in principle any file stored on the computer. I will definitely write about this module in the coming days, as This requires a separate post. As a result, I presented the protection of the project with four types of encryption.
And as a result, at the moment I am a student in the direction of the IU8 department "Information Security of Automated Systems" of MSTU named after NE Bauman.
PS: IU8 is really very difficult to enter the department according to a general competition, but this does not mean that the department takes only thieves. Thieves go to business and management, but not to technical specialties. The Step into the Future Olympiad is probably one of the most accessible ways to get into MGTU. The main thing is to make yourself spend a year writing and defending a project and a physics competition.
PPS: When writing the article, graphic files from the MSTU named after NE Bauman (the first 2) and clippings from the presentation accompanying the project's protection (all other images) were used.
In this article I want to continue the popularization of the program “Step into the Future”, started last night by the user vaboretti, as well as dispel the myth that it is impossible for an ordinary person to enter the department IU8 at MSTU.

To begin with, briefly about the program: “The Russian scientific and social program for young people and schoolchildren“ Step into the Future ”is a whole complex of all kinds of research aimed at the following goals:
- support for vocational training and intellectual development of Russian youth in the unified scientific and educational space of Russia, promoting the reproduction of personnel for the scientific and technical complex of the country;
- the development of effective mechanisms for the interaction between science, higher and secondary education, interregional cooperation in the field of youth creativity and professional mentoring;
- ensuring one of the principles of state policy in the field of education - the state-public nature of education management.
Here is a brief information about the recruitment of this year: about 25,000 applications were submitted to 115 departments (if you suddenly confused the numbers, please forgive. Error + 5%). Of these 25,000 applications, more than 2,000 are for the IU-8 “Information Security” department only. Budget places in the department 80.
Good news: 41 out of 80 budget places are the winners and prize-winners of the Step. Another 27 - beneficiaries and target, and only 12 - for the total set.
')
The Olympiad takes place in two stages: the defense of the project and the competition in physics. Both tests are rated at a maximum of 50 points, i.e. 100 points in total - maximum. Then the participant who scores the passing points for each trial receives a benefit of some type:

On the competition in physics can not talk. I think, so everyone understands everything: the usual Olympiad (test work in physics).
The main (and most difficult) part of the Olympiad is project defense. Actually, the defense is as follows: at the table sit the jury members, before whom it is necessary to fully present their project, i.e. explain its pros / cons, newness, uniqueness, etc. etc. Depending on how serious the project is and how effectively its presentation takes place, the jury will award points.
The topic of the project was recommended by my supervisor. The work was called “Software of an automated workplace of the expert in enciphering and masking of information“, and represented the software written only by me (ie without use of another's codes).

I decided to write in C # as the most appropriate and fast-learning language.
For writing the program used the following literature:
- M. Abrahamyan - "Visual C # with examples";
- Yu.M. Krakovsky - “Information Security and Information Security”;
- A.Yu. Shcherbakov - “Modern Computer Security”;
- N.Smart - “The World of Programming. Cryptography".
The general plan of the program is approximately as follows:

The main essence of the project, as seen on the diagram above, was to impose several encryption methods on top of one another.
Security encryption was carried out by imposing an unlimited number of ciphers of each type on each other:

At the same time, an extensive cipher library was used, adapted specifically for understanding by the program.
Over the search and adaptation of ciphers worked a little over a month.
For example, below is the scheme with the possible number of combinations of decrypting the source text, encrypted with different numbers of ciphers of the same type (ie, only text, only graphics, or only sound):

To write the key, it was decided to use a separate text file in which all numbers of all encryption algorithms with the keys to each algorithm were recorded. Accordingly, decryption occurred in the reverse order using the key file:

True, on the night before the defense, the long-awaited insight had come down, and another module was added to the program, allowing to encrypt not only graphics / text / sound, but in principle any file stored on the computer. I will definitely write about this module in the coming days, as This requires a separate post. As a result, I presented the protection of the project with four types of encryption.
And as a result, at the moment I am a student in the direction of the IU8 department "Information Security of Automated Systems" of MSTU named after NE Bauman.
PS: IU8 is really very difficult to enter the department according to a general competition, but this does not mean that the department takes only thieves. Thieves go to business and management, but not to technical specialties. The Step into the Future Olympiad is probably one of the most accessible ways to get into MGTU. The main thing is to make yourself spend a year writing and defending a project and a physics competition.
PPS: When writing the article, graphic files from the MSTU named after NE Bauman (the first 2) and clippings from the presentation accompanying the project's protection (all other images) were used.
Source: https://habr.com/ru/post/126548/
All Articles