Http Parameter Contamination (more)
Continuing the research of the Http Parameter Contamination (HPC) attack, I carried out a primitive fuzzing, including in those environments that were not affected by Ivan Markovic in his original research. It is worth noting immediately that nothing fundamentally new was found. On the other hand, an interesting feature of the Python interpreter was revealed, and also, the combat received will be denied to service against the Tomcat server :) But by the last, so far non disclosure.
The results are presented in the picture below.
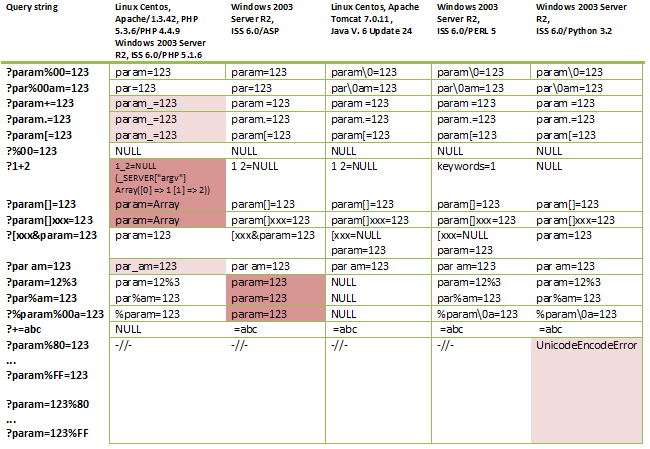
* The symbol "\ 0" means that null-byte is correctly processed by the application.
')
The most interesting features are highlighted in dark red. Less interesting, but noteworthy, highlighted in pale red. Consider the results in more detail.
The greatest value for an attacker is the processing of incoming data by an ASP web application. The fact is that an application on an ASP, having encountered the symbol "%" in the parameter name or in its value, simply deletes it, if it in turn does not form the "correct" symbol in URL decoding . This makes it quite easy to bypass the various security filters and Web Application Firewalls that are used before the application processes the incoming data. Ivan Markovic in his study gives the following example of bypassing the Mod_Security rules when exploiting the Path traversal vulnerability:
More vital for the IIS platform is the use of the MSSQL database and the appearance of vulnerabilities in an application such as SQL Injection. Similarly, using this method, you can use this vulnerability to bypass the corresponding Mod_Security rules:
? id = 1; selec% t + @% @ version--
? id = 1; selec% t + convert (int, (selec% t + table% _name + from (selec% t + row_number () + over + (order + by + table% _name) + as + rownu% m, table % _name + from + information_schema.tables) + as + t + where + t.rownu% m = 1)) -
...
Here it is necessary to make a reservation that we are talking only about bypassing the base rules Mod_Security (base rules). In the case of the use of advanced rules (optional and experimental) such feints no longer pass.
Another, no less useful feature of processing incoming data is found in the PHP interpreter. This is an implicit type conversion ( ? Param [] = 123 -> param = Array ), which everyone should have known for a long time and the ability to control the $ _SERVER ["argv"] array ( ? 1 + 2 ) when set to the "register_argc_argv" configuration "On". The PHP PHP attacker can use the first feature in order to bypass various kinds of restrictions (for example, with implicit comparison of variables), as well as to force an error message to be displayed (for disclosing the web server root directory). The second PHP feature allows you to access a script through a web server and pass parameters to it that the script accepts from the command line.
A less interesting feature of PHP is the replacement of the characters "+", ".", "[" And "space" with an underscore ("_"). Why is it not so dangerous? The fact is that this PHP behavior is observed only in the names of the parameters passed to the web server, but not in their values. This greatly reduces the likelihood of using this feature in "wildlife".
And the last thing I wanted to pay attention to is the Python interpreter. During fuzzing, it was found that Python encountering characters from the range of% 80-% FF returns an error message (ala disclosure ... and blah blah):

(Application)
For testing we used scripts that are listed below.
PHP:
<? php
$ G = & $ _ GET;
foreach ($ G as $ k => $ v)
{
print $ k. "=". $ v;
}
?>
ASP:
<%
for each var in Request.QueryString
Response.Write (var & "=" & Request.QueryString (var))
next
%>
JAVA:
<%
java.util.Enumeration names = request.getParameterNames ();
while (names.hasMoreElements ()) {
String keyx = names.nextElement (). ToString ();
out.println (keyx + "=" + request.getParameter (keyx)); }
%>
PERL:
use CGI;
my $ cgi = new CGI;
my @params = $ cgi-> param ();
print << ENDOFTEXT;
HTTP / 1.0 200 OK
Content-Type: text / html
ENDOFTEXT
foreach my $ parameter (sort @params) {
print $ parameter. "=". $ cgi-> param ($ parameter);
}
PYTHON:
import cgi, os
print ('Status: 200 OK')
print ('Content-type: text / html; charset = utf-8;')
print ("")
query = os.environ.get ('QUERY_STRING')
pairs = cgi.parse_qs (query)
for key, value in pairs.items ():
print (key, value)
The results are presented in the picture below.

* The symbol "\ 0" means that null-byte is correctly processed by the application.
')
The most interesting features are highlighted in dark red. Less interesting, but noteworthy, highlighted in pale red. Consider the results in more detail.
The greatest value for an attacker is the processing of incoming data by an ASP web application. The fact is that an application on an ASP, having encountered the symbol "%" in the parameter name or in its value, simply deletes it, if it in turn does not form the "correct" symbol in URL decoding . This makes it quite easy to bypass the various security filters and Web Application Firewalls that are used before the application processes the incoming data. Ivan Markovic in his study gives the following example of bypassing the Mod_Security rules when exploiting the Path traversal vulnerability:
192.168.2.105/test.asp?file=.%./bla.txtMore vital for the IIS platform is the use of the MSSQL database and the appearance of vulnerabilities in an application such as SQL Injection. Similarly, using this method, you can use this vulnerability to bypass the corresponding Mod_Security rules:
? id = 1; selec% t + @% @ version--
? id = 1; selec% t + convert (int, (selec% t + table% _name + from (selec% t + row_number () + over + (order + by + table% _name) + as + rownu% m, table % _name + from + information_schema.tables) + as + t + where + t.rownu% m = 1)) -
...
Here it is necessary to make a reservation that we are talking only about bypassing the base rules Mod_Security (base rules). In the case of the use of advanced rules (optional and experimental) such feints no longer pass.
Another, no less useful feature of processing incoming data is found in the PHP interpreter. This is an implicit type conversion ( ? Param [] = 123 -> param = Array ), which everyone should have known for a long time and the ability to control the $ _SERVER ["argv"] array ( ? 1 + 2 ) when set to the "register_argc_argv" configuration "On". The PHP PHP attacker can use the first feature in order to bypass various kinds of restrictions (for example, with implicit comparison of variables), as well as to force an error message to be displayed (for disclosing the web server root directory). The second PHP feature allows you to access a script through a web server and pass parameters to it that the script accepts from the command line.
A less interesting feature of PHP is the replacement of the characters "+", ".", "[" And "space" with an underscore ("_"). Why is it not so dangerous? The fact is that this PHP behavior is observed only in the names of the parameters passed to the web server, but not in their values. This greatly reduces the likelihood of using this feature in "wildlife".
And the last thing I wanted to pay attention to is the Python interpreter. During fuzzing, it was found that Python encountering characters from the range of% 80-% FF returns an error message (ala disclosure ... and blah blah):

(Application)
For testing we used scripts that are listed below.
PHP:
<? php
$ G = & $ _ GET;
foreach ($ G as $ k => $ v)
{
print $ k. "=". $ v;
}
?>
ASP:
<%
for each var in Request.QueryString
Response.Write (var & "=" & Request.QueryString (var))
next
%>
JAVA:
<%
java.util.Enumeration names = request.getParameterNames ();
while (names.hasMoreElements ()) {
String keyx = names.nextElement (). ToString ();
out.println (keyx + "=" + request.getParameter (keyx)); }
%>
PERL:
use CGI;
my $ cgi = new CGI;
my @params = $ cgi-> param ();
print << ENDOFTEXT;
HTTP / 1.0 200 OK
Content-Type: text / html
ENDOFTEXT
foreach my $ parameter (sort @params) {
print $ parameter. "=". $ cgi-> param ($ parameter);
}
PYTHON:
import cgi, os
print ('Status: 200 OK')
print ('Content-type: text / html; charset = utf-8;')
print ("")
query = os.environ.get ('QUERY_STRING')
pairs = cgi.parse_qs (query)
for key, value in pairs.items ():
print (key, value)
Source: https://habr.com/ru/post/126319/
All Articles