Can you believe your eyes? (Unicode in file names)
A few days ago, one of our users sent a sample (SHA1: fbe71968d4c5399c2906b56d9feadf19a35beb97, defined as TrojanDropper: Win32 / Vundo.L ). This is a phishing trojan from vk.com and vkontakte.ru , requests for which are redirected to 92.38.209.252 in an unusual way.
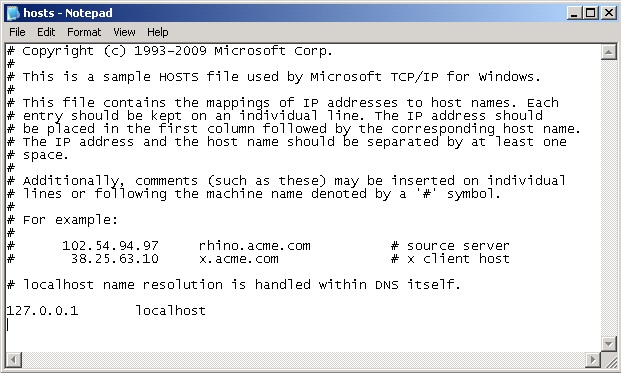
The usual method of redirecting traffic is to add an entry to the hosts file , which is located in the % SystemRoot% \ system32 \ drivers \ etc folder . However, when we open this file on an infected computer, there are no entries for vk.com and vkontakte.ru :
But if you enable the display of hidden files, then another hosts file appears:
')

We see two files with the same name in the same folder. But after all, one directory cannot contain two files with the same name. If you copy the file names in Notepad, save as Unicode text and open it in a Hex editor, the following picture will appear (the top line for the first hosts file , the bottom line for the second):

In Unicode (UTF-16), the character 0x006F looks the same as 0x6F in ASCII, where it corresponds to the letter “o”. But what is 0x043E in Unicode? This can be viewed in the Unicode table, here is its fragment.

In table 0x043E corresponds to a Cyrillic character that looks the same as the English "o". That is, the real hosts file is actually a hidden file, it is used by the operating system. If you open this file, you immediately see the difference from the fake one, these are two lines downstairs on several screens from the beginning:

The riddle is solved.
This is not the first time we have discovered that hackers use Unicode encoding for malicious purposes. In August 2010, a Chinese hacker demonstrated a trick on how to use Unicode control characters to convince users of file security. Using the control character 0x202E (RLO), you can change the order of characters when displaying the file name in Windows Explorer.
For example, here is the potentially dangerous picgpj.exe file .

If you insert a control character before the part of the name “gpj.exe”, the order of the characters changes and the file name is displayed in the Explorer in a different way:

Hackers usually use the picture as an icon for this file. A careless user can take it as a photo and open it with a double click, thereby launching the program. Obviously, this technique is useless for programs with Unicode support, but users are not always able to recognize the danger themselves.
Can you believe your eyes? It turns out that not always.
The usual method of redirecting traffic is to add an entry to the hosts file , which is located in the % SystemRoot% \ system32 \ drivers \ etc folder . However, when we open this file on an infected computer, there are no entries for vk.com and vkontakte.ru :

But if you enable the display of hidden files, then another hosts file appears:
')

We see two files with the same name in the same folder. But after all, one directory cannot contain two files with the same name. If you copy the file names in Notepad, save as Unicode text and open it in a Hex editor, the following picture will appear (the top line for the first hosts file , the bottom line for the second):

In Unicode (UTF-16), the character 0x006F looks the same as 0x6F in ASCII, where it corresponds to the letter “o”. But what is 0x043E in Unicode? This can be viewed in the Unicode table, here is its fragment.

In table 0x043E corresponds to a Cyrillic character that looks the same as the English "o". That is, the real hosts file is actually a hidden file, it is used by the operating system. If you open this file, you immediately see the difference from the fake one, these are two lines downstairs on several screens from the beginning:

The riddle is solved.
This is not the first time we have discovered that hackers use Unicode encoding for malicious purposes. In August 2010, a Chinese hacker demonstrated a trick on how to use Unicode control characters to convince users of file security. Using the control character 0x202E (RLO), you can change the order of characters when displaying the file name in Windows Explorer.
For example, here is the potentially dangerous picgpj.exe file .

If you insert a control character before the part of the name “gpj.exe”, the order of the characters changes and the file name is displayed in the Explorer in a different way:

Hackers usually use the picture as an icon for this file. A careless user can take it as a photo and open it with a double click, thereby launching the program. Obviously, this technique is useless for programs with Unicode support, but users are not always able to recognize the danger themselves.
Can you believe your eyes? It turns out that not always.
Source: https://habr.com/ru/post/126198/
All Articles