Overview of free tools for pentest web-resources and not only v2
Some time ago I wrote about this , but a bit poorly and messy. After I decided to expand the list of tools in the review, add a structure to the article, take into account criticism (many thanks to Lefty for the advice) and sent it to the contest for SecLab (and published the link , but for obvious reasons nobody saw it). The contest is over, the results have been announced and I can, with a clear conscience, publish it (article) on Habré.
In this article I will talk about the most popular tools for pentesting (penetration tests) of web applications using the black box strategy.
To do this, we consider utilities that will help in this type of testing. Consider the following product categories:
Some products have a universal “character”, so I will attribute them to the category in which they have the best result (subjective opinion).
')
The main task is to reveal the available network services, install their versions, determine the OS, etc.
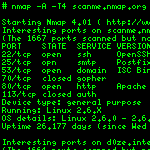
Nmap ("Network Mapper") is a free open source utility for network analysis and system security auditing. Furious opponents of the console can use Zenmap, this is a GUI to Nmap.
This is not just a "smart" scanner, it is a serious extensible tool (from "unusual chips" - the presence of a script to check the node for the presence of the worm " Stuxnet " (mentioned here ). Typical use case:
-A to determine the OS version, scanning using scripts and tracing
-T4 time management setting (more - faster, from 0 to 5)
localhost - target host
Anything tougher?
This is a set of options from the “slow comprehensive scan” profile in Zenmap. It takes a long time to complete, but it also gives you more detailed information that you can learn about the target system. Reference guide in Russian , if you decide to go deep, as well as advise translation of the article Beginner's Guide to Nmap .
Nmap has received the status of “Security Product of the Year” by such magazines and communities as Linux Journal, Info World, LinuxQuestions.Org and Codetalker Digest.
An interesting moment, Nmap can be seen in the films "The Matrix: Reload", "Die Hard 4", "The Bourne Ultimatum", "Hottabych" and others .

IP-Tools - a kind of set of various network utilities, comes with a GUI, “dedicated” to windows users.
Port scanner, shared resources (shared printers / folders), WhoIs / Finger / Lookup, telnet client and much more. Just a convenient, fast, functional tool.
It makes little sense to consider other products, since there are a lot of utilities in this area and they all have a similar working principle and functionality. Yet the most frequently used is nmap.
Trying to find popular vulnerabilities (SQL inj, XSS, LFI / RFI, etc.) or errors (not deleted temporary files, indexing directories, etc.)

Acunetix Web Vulnerability Scanner - by the link it is noticeable that this is an xss scanner, but this is notquite so. The free version available through the link provides quite a lot of functionality. Usually, the person who launched this scanner for the first time and received a report on its resource for the first time covers a small shock, and you will understand why by doing this. This is a very powerful product for analyzing just all sorts of vulnerabilities on the site and works not only with familiar php sites, but also in other languages (although the difference in language is not an indicator). It makes no sense to describe the instruction, since the scanner simply “picks up” the user's actions. Something similar to “further, further, further, ready” in a typical installation of any software.

Nikto is an Open Source (GPL) web scanner. Eliminates the routine of manual work. Searches on the target site uninstalled scripts (some test.php, index_.php, etc.), DB administration tools (/ phpmyadmin /, / pma and the like), etc., that is, it checks the resource for the most frequent errors that are usually caused by the human factor.
Plus, if it finds some popular script, then it checks for the released exploits (which are in the database).
Report available unwanted methods such as PUT and TRACE
Well, and so on. It is very convenient if you work as an auditor and spend every day analyzing websites.
Of the minuses I would like to note a high percentage of false positives. For example, if your site instead of 404 errors (when it should arise) gives all the time home, the scanner will say that your site has all the scripts and all the vulnerabilities from its base. In practice, this is not so common, but as a matter of fact, much depends on the structure of your site.
Classic use:
If you need to be authorized on the site, you can set a cookie in the nikto.conf file, the variable STATIC-COOKIE.

Wikto - Nikto under Windows, but with some additions, as “fuzzy” logic when checking code for errors, using GHDB, getting links and resource folders, real-time monitoring HTTP requests / responses. Wikto is written in C # and requires the .NET framework.

skipfish is a web vulnerability scanner from Michal Zalewski (known by the nickname lcamtuf). Written in C, crossplatformin (for Win you need Cygwin). Recursively (and very long, about 20 ~ 40 hours, although the last time I worked 96 hours) bypasses the entire site and finds all sorts of security holes. It also generates a lot of traffic (several GB of incoming / outgoing). But all means are good, especially if there is time and resources.
Typical use:
In the folder “reports” there will be a report in html, an example .

w3af - Web Application Attack and Audit Framework, open-source web vulnerability scanner. It has a GUI, but you can work from under the console. More precisely, this is a framework with a bunch of plugins .
You can talk about its advantages for a long time, it is better to try it:]
Typical work with him comes down to choosing a profile, specifying a target and, in fact, launching.

Mantra is a dream that came true . A collection of free and open information security tools embedded in a web browser.
Very useful when testing web applications at all stages.
Use comes down to installing and launching a browser.
In fact, there are a lot of utilities in this category and it is rather difficult to select a specific list from them. Most often, each pentester himself determines the set of tools he needs.
For automated and more convenient use of vulnerabilities in software and scripts, they write exploits that only need to pass parameters in order to exploit a security breach. And there are products that eliminate the manual search for exploits, and they also use them on the fly. About this category now and will be discussed.

The Metasploit® Framework is a monster in our business. He knows so much that the instruction will be released on several articles. We will look at auto-exploit (nmap + metasploit). The essence is that Nmap will analyze the port we need, install the service, and metasploit will try to apply exploits to it, based on the class of service (ftp, ssh, etc.). Instead of text instructions, I will insert a video that is quite popular on autopwn.
And you can just automate the work of the exploit we need. For example:
In fact, the capabilities of this framework are very extensive, so if you decide to go deeper, follow the link

Armitage -OVA cyberpunk GUI for Metasploit. Visualizes the target, recommends exploits and provides advanced features of this framework. In general, for those who love everything to look beautiful and spectacular.
Screencast:

The Tenable Nessus® vulnerability scanner does a lot of things, but we need one of its capabilities from it — determining which services have exploits for. Free version of the product “home only”
Using:
To check the practical vulnerability of services to exploits, you can use the above described Metasploit Framework or try to find an exploit (for example on Explot-db , packet storm , explot search , etc.) and use it manually against your system
IMHO: too cumbersome. He brought him as one of the leaders in this direction of the software industry.
Injection searches are made by many of the web app sec scanners, but they are still just generic scanners. And there are utilities that are specifically engaged in the search and operation of injections. About them now and will be discussed.

sqlmap is an open-source utility for searching and exploiting SQL injections. Supports database servers such as: MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, SQLite, Firebird, Sybase, SAP MaxDB.
Typical use comes down to the line:
Enough manuals, including in Russian. Softina greatly facilitates the work of pentester when working on this area.
Add an official video demonstration:
bsqlbf-v2 - perl script, bruteformer of “blind” Sql injections. It works both with integer values in url and with string (string).
Supports DB:
-url www.somehost.com/blah.php?u=5 - Link with parameters
-blind u - parameter for injection (by default, the last one is taken from the address bar)
-sql "select table_name from imformation_schema.tables limit 1 offset 0" is our arbitrary query to the base
-database 1 - DB server: MSSQL
-type 1 - type of attack, “blind” injection, based on True and Error (for example, syntax errors) responses
These tools are mainly used by developers, with problems with the results of the execution of their code. But this direction is also useful during pentesting, when you can replace the data we need on the fly, analyze what comes in response to our input parameters (for example, when fuzzing), etc.
Burp Suite - a set of tools that help with penetration tests. The web has a good overview in Russian from Raz0r (true for 2008).
The free version includes:

Fiddler - Fiddler is a debugging proxy that logs all HTTP (S) traffic. Allows you to explore this traffic, set breakpoints and play with incoming or outgoing data.
There is also Firesheep , the Wireshark monster and others, the choice is up to the user.
Naturally, each pentester has its own arsenal and its own set of utilities, since there are simply a lot of them. I tried to bring some of the most convenient and popular. But so that anyone can get acquainted with other utilities in this direction, I will provide the links below.
upd : BurpSuite documentation in Russian from the Hack4Sec team (added by AntonKuzmin )
PS You can not keep silent about the XSpider. It does not participate in the review, although it is conditionally free (I found out when I sent the article to SecLab, because of this (not knowledge, and the lack of the latest version 7.8), and did not include it in the article). And in theory, his review was planned (I have hard tests for him), but I don’t know if he will see his world.
PPS Some material from the article will be used for its intended purpose in the upcoming report at CodeFest 2012 in the QA section, which will include tools not mentioned here (free, essno), as well as an algorithm, what order to use, what result to expect, what configurations use all sorts of hints and tricks when working (I reflect on the report almost every day, I will try to tell myself the best on the topic)
By the way, this article was a lesson on Open InfoSec Days ( tag on Habré , site ), you canrob korovany look materials .
Free Pentester Web Application Tools
In this article I will talk about the most popular tools for pentesting (penetration tests) of web applications using the black box strategy.
To do this, we consider utilities that will help in this type of testing. Consider the following product categories:
- Network scanners
- Web Script Scanners
- Exploiting
- Injection automatization
- Debuggers (sniffers, local proxies, etc.)
Some products have a universal “character”, so I will attribute them to the category in which they have the best result (subjective opinion).
')
Network scanners.
The main task is to reveal the available network services, install their versions, determine the OS, etc.
Nmap

Nmap ("Network Mapper") is a free open source utility for network analysis and system security auditing. Furious opponents of the console can use Zenmap, this is a GUI to Nmap.
This is not just a "smart" scanner, it is a serious extensible tool (from "unusual chips" - the presence of a script to check the node for the presence of the worm " Stuxnet " (mentioned here ). Typical use case:
nmap -A -T4 localhost-A to determine the OS version, scanning using scripts and tracing
-T4 time management setting (more - faster, from 0 to 5)
localhost - target host
Anything tougher?
nmap -sS -sU -T4 -A -v -PE -PP -PS21,22,23,25,80,113,31339 -PA80,113,443,10042 -PO --script all localhostThis is a set of options from the “slow comprehensive scan” profile in Zenmap. It takes a long time to complete, but it also gives you more detailed information that you can learn about the target system. Reference guide in Russian , if you decide to go deep, as well as advise translation of the article Beginner's Guide to Nmap .
Nmap has received the status of “Security Product of the Year” by such magazines and communities as Linux Journal, Info World, LinuxQuestions.Org and Codetalker Digest.
An interesting moment, Nmap can be seen in the films "The Matrix: Reload", "Die Hard 4", "The Bourne Ultimatum", "Hottabych" and others .
IP Tools

IP-Tools - a kind of set of various network utilities, comes with a GUI, “dedicated” to windows users.
Port scanner, shared resources (shared printers / folders), WhoIs / Finger / Lookup, telnet client and much more. Just a convenient, fast, functional tool.
It makes little sense to consider other products, since there are a lot of utilities in this area and they all have a similar working principle and functionality. Yet the most frequently used is nmap.
Web Script Scanners
Trying to find popular vulnerabilities (SQL inj, XSS, LFI / RFI, etc.) or errors (not deleted temporary files, indexing directories, etc.)
Acunetix Web Vulnerability Scanner

Acunetix Web Vulnerability Scanner - by the link it is noticeable that this is an xss scanner, but this is not
Nikto

Nikto is an Open Source (GPL) web scanner. Eliminates the routine of manual work. Searches on the target site uninstalled scripts (some test.php, index_.php, etc.), DB administration tools (/ phpmyadmin /, / pma and the like), etc., that is, it checks the resource for the most frequent errors that are usually caused by the human factor.
Plus, if it finds some popular script, then it checks for the released exploits (which are in the database).
Report available unwanted methods such as PUT and TRACE
Well, and so on. It is very convenient if you work as an auditor and spend every day analyzing websites.
Of the minuses I would like to note a high percentage of false positives. For example, if your site instead of 404 errors (when it should arise) gives all the time home, the scanner will say that your site has all the scripts and all the vulnerabilities from its base. In practice, this is not so common, but as a matter of fact, much depends on the structure of your site.
Classic use:
./nikto.pl -host localhostIf you need to be authorized on the site, you can set a cookie in the nikto.conf file, the variable STATIC-COOKIE.
Wikto

Wikto - Nikto under Windows, but with some additions, as “fuzzy” logic when checking code for errors, using GHDB, getting links and resource folders, real-time monitoring HTTP requests / responses. Wikto is written in C # and requires the .NET framework.
skipfish

skipfish is a web vulnerability scanner from Michal Zalewski (known by the nickname lcamtuf). Written in C, crossplatformin (for Win you need Cygwin). Recursively (and very long, about 20 ~ 40 hours, although the last time I worked 96 hours) bypasses the entire site and finds all sorts of security holes. It also generates a lot of traffic (several GB of incoming / outgoing). But all means are good, especially if there is time and resources.
Typical use:
./skipfish -o /home/reports www.example.comIn the folder “reports” there will be a report in html, an example .
w3af

w3af - Web Application Attack and Audit Framework, open-source web vulnerability scanner. It has a GUI, but you can work from under the console. More precisely, this is a framework with a bunch of plugins .
You can talk about its advantages for a long time, it is better to try it:]
Typical work with him comes down to choosing a profile, specifying a target and, in fact, launching.
Mantra Security Framework

Mantra is a dream that came true . A collection of free and open information security tools embedded in a web browser.
Very useful when testing web applications at all stages.
Use comes down to installing and launching a browser.
In fact, there are a lot of utilities in this category and it is rather difficult to select a specific list from them. Most often, each pentester himself determines the set of tools he needs.
Exploiting
For automated and more convenient use of vulnerabilities in software and scripts, they write exploits that only need to pass parameters in order to exploit a security breach. And there are products that eliminate the manual search for exploits, and they also use them on the fly. About this category now and will be discussed.
Metasploit Framework

The Metasploit® Framework is a monster in our business. He knows so much that the instruction will be released on several articles. We will look at auto-exploit (nmap + metasploit). The essence is that Nmap will analyze the port we need, install the service, and metasploit will try to apply exploits to it, based on the class of service (ftp, ssh, etc.). Instead of text instructions, I will insert a video that is quite popular on autopwn.
And you can just automate the work of the exploit we need. For example:
msf > use auxiliary/admin/cisco/vpn_3000_ftp_bypass
msf auxiliary(vpn_3000_ftp_bypass) > set RHOST [TARGET IP]
msf auxiliary(vpn_3000_ftp_bypass) > run
In fact, the capabilities of this framework are very extensive, so if you decide to go deeper, follow the link
Armitage

Armitage -
Screencast:
Tenable Nessus®

The Tenable Nessus® vulnerability scanner does a lot of things, but we need one of its capabilities from it — determining which services have exploits for. Free version of the product “home only”
Using:
- They downloaded (for their system), installed, registered (the key comes in the mail).
- Launched a server, added a user to Nessus Server Manager (button Manage users)
- Go to the address
https: // localhost: 8834 /
and get the flash client in the browser - Scans -> Add -> fill in the fields (by selecting the appropriate scanning profile) and click Scan
To check the practical vulnerability of services to exploits, you can use the above described Metasploit Framework or try to find an exploit (for example on Explot-db , packet storm , explot search , etc.) and use it manually against your system
IMHO: too cumbersome. He brought him as one of the leaders in this direction of the software industry.
Injection automation
Injection searches are made by many of the web app sec scanners, but they are still just generic scanners. And there are utilities that are specifically engaged in the search and operation of injections. About them now and will be discussed.
sqlmap

sqlmap is an open-source utility for searching and exploiting SQL injections. Supports database servers such as: MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, SQLite, Firebird, Sybase, SAP MaxDB.
Typical use comes down to the line:
python sqlmap.py -u "http://example.com/index.php?action=news&id=1"Enough manuals, including in Russian. Softina greatly facilitates the work of pentester when working on this area.
Add an official video demonstration:
bsqlbf-v2
bsqlbf-v2 - perl script, bruteformer of “blind” Sql injections. It works both with integer values in url and with string (string).
Supports DB:
- MS-SQL
- Mysql
- PostgreSQL
- Oracle
./bsqlbf-v2-3.pl -url www.somehost.com/blah.php?u=5 -blind u -sql "select table_name from imformation_schema.tables limit 1 offset 0" -database 1 -type 1
-url www.somehost.com/blah.php?u=5 - Link with parameters
-blind u - parameter for injection (by default, the last one is taken from the address bar)
-sql "select table_name from imformation_schema.tables limit 1 offset 0" is our arbitrary query to the base
-database 1 - DB server: MSSQL
-type 1 - type of attack, “blind” injection, based on True and Error (for example, syntax errors) responses
Debuggers
These tools are mainly used by developers, with problems with the results of the execution of their code. But this direction is also useful during pentesting, when you can replace the data we need on the fly, analyze what comes in response to our input parameters (for example, when fuzzing), etc.
Burp suite
Burp Suite - a set of tools that help with penetration tests. The web has a good overview in Russian from Raz0r (true for 2008).
The free version includes:
- Burp Proxy - local proxy, allows you to modify already generated requests from the browser
- Burp Spider - spider searches for existing files and directories.
- Burp Repeater - manually send HTTP requests
- Burp Sequencer - analysis of random values in forms
- Burp Decoder - standard codec (html, base64, hex, etc.), of which there are thousands that can be quickly written in any language
- Burp Comparer - string matching component
Feeddler

Fiddler - Fiddler is a debugging proxy that logs all HTTP (S) traffic. Allows you to explore this traffic, set breakpoints and play with incoming or outgoing data.
There is also Firesheep , the Wireshark monster and others, the choice is up to the user.
Conclusion
Naturally, each pentester has its own arsenal and its own set of utilities, since there are simply a lot of them. I tried to bring some of the most convenient and popular. But so that anyone can get acquainted with other utilities in this direction, I will provide the links below.
Various tops / lists of scanners and utilities
- Security and Hacking Tools
- Top 100 Network Security Tools
- Top 10 Web Vulnerability Scanners .
- Top 10 Vulnerability Scanners
- OWASP Top 10 Tools and Tactics
- Web-based Application Security Scanners
- Web Application Security Scanner List by WebAppSec
- Infosec tools on the RDot forum
- Vulnerability Scanners (Wikipedia)
Linux distributions, which already include a bunch of different utilities for pentesting
upd : BurpSuite documentation in Russian from the Hack4Sec team (added by AntonKuzmin )
PS You can not keep silent about the XSpider. It does not participate in the review, although it is conditionally free (I found out when I sent the article to SecLab, because of this (not knowledge, and the lack of the latest version 7.8), and did not include it in the article). And in theory, his review was planned (I have hard tests for him), but I don’t know if he will see his world.
PPS Some material from the article will be used for its intended purpose in the upcoming report at CodeFest 2012 in the QA section, which will include tools not mentioned here (free, essno), as well as an algorithm, what order to use, what result to expect, what configurations use all sorts of hints and tricks when working (I reflect on the report almost every day, I will try to tell myself the best on the topic)
By the way, this article was a lesson on Open InfoSec Days ( tag on Habré , site ), you can
Source: https://habr.com/ru/post/125317/
All Articles