Overview of free tools for auditing web-resources and not only

The issue of security will always be relevant, especially on the web. Therefore, in order not to get such a picture on your resource, you need to be able to check for yourself.
Under the cut - a brief overview and typical examples of the use of free utilities that will help (or more precisely already help)
The article has a rather low entry threshold for understanding and use, so I hope many will like it. Only the basic functionality of the program is revealed.
')
Let's get started
Before starting, I would like to draw attention to the Top 100 Network Security Tools list and Top 10 Web Vulnerability Scanners . Perhaps they are already outdated, but many of the utilities are still alive and you can try to use them.
1) Nmap
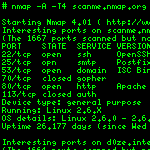
Nmap ("Network Mapper") is a free open source utility for network analysis and system security auditing. Furious opponents of the console can use Zenmap, this is a GUI to Nmap.
This is not just a "smart" scanner, it is a serious extensible tool (from "unusual chips" - the presence of a script to check the node for the presence of the worm " Stuxnet " (mentioned here ). Typical use case:
nmap -A -T4 localhost-A to determine the OS version, scanning using scripts and tracing
-T4 time management setting (more - faster, from 0 to 5)
localhost - target host
Anything tougher?
nmap -sS -sU -T4 -A -v -PE -PP -PS21,22,23,25,80,113,31339 -PA80,113,443,10042 -PO --script all localhostThis is a set of options from the “slow comprehensive scan” profile in Zenmap. It takes a long time to complete, but it also gives you more detailed information that you can learn about the target system. Reference guide in Russian , if you decide to go deep, as well as advise translation of the article Beginner's Guide to Nmap .
Nmap has received the status of “Security Product of the Year” by such magazines and communities as Linux Journal, Info World, LinuxQuestions.Org and Codetalker Digest.
An interesting moment, Nmap can be seen in the films "The Matrix: Reload", "Die Hard 4", "The Bourne Ultimatum", "Hottabych" and others .
2) Tenable Nessus®

Tenable Nessus® vulnerability scanner is a very powerful scanner. Talk about the available services running on the target system, check for possible misconfiguration (in the area of security), tell you what exploits are for them (services) and more. The only thing is the free version of “home only”, just for our article;)
Using:
- They downloaded (for their system), installed, registered (the key comes in the mail).
- Launched a server, added a user to Nessus Server Manager (button Manage users)
- Go to the address
https: // localhost: 8834 /
and get the flash client in the browser - Scans -> Add -> fill in the fields (by selecting the appropriate scanning profile) and click Scan
To check the practical vulnerability of services to exploits, you can use the Metasploit Framework or try to find an exploit (for example on Explot-db , packet storm , explot search , etc.) and use it manually against your system
3) Acunetix Web Vulnerability Scanner

Acunetix Web Vulnerability Scanner - by the link it is noticeable that this is an xss scanner, but this is not
four) Metasploit Framework

The Metasploit® Framework is a monster in our business. He knows so much that the instruction will be released on several articles. We will look at auto-exploit (nmap + metasploit). The essence is that Nmap will analyze the port we need, install the service, and metasploit will try to apply exploits to it, based on the class of service (ftp, ssh, etc.). Since I promised a low threshold of entry, instead of text instructions, I will insert a video that is quite popular on autopwn.
Want more? Then here
5) Nikto

Nikto is an Open Source (GPL) web scanner. Eliminates the routine of manual work. Searches on the target site uninstalled scripts (some test.php, index_.php, etc.), DB administration tools (/ phpmyadmin /, / pma and the like), etc., that is, it checks the resource for the most frequent errors that are usually caused by the human factor.
Plus, if it finds some popular script, then it checks for the released exploits (which are in the database).
Report available unwanted methods such as PUT and TRACE
Well, and so on. It is very convenient if you work as an auditor and spend every day analyzing websites.
Of the minuses I would like to note a high percentage of false positives. For example, if your site instead of 404 errors (when it should arise) gives all the time home, the scanner will say that your site has all the scripts and all the vulnerabilities from its base. In practice, this is not so common, but as a matter of fact, much depends on the structure of your site.
Classic use:
./nikto.pl -host localhostIf you need to be authorized on the site, you can set a cookie in the nikto.conf file, the variable STATIC-COOKIE.
There are, of course, more utilities, so I gave 2 links to the tops of programs in this area at the very beginning of the article. But I can not keep silent about our domestic product MaxPatrol from Positive Technologies, which have released such a sensational product as XSpider . This software is paid, so it is not in the review.
Afterword
A separate article deserves the topic of frequent developer errors (low or no filtering of incoming data, directory indexing, filling docs folder with scripts, etc.), automating the audit of the source code ("white box"), as well as why even popular Open Source should be checked do-it-yourself scripts. If the topic will be in demand - I will try to write a relevant article after some time.
Series:
- Overview of free tools for auditing web-resources and not only
- Audit "Black box"
- Likbez on vulnerabilities in web applications, as well as the most frequent mistakes of developers
- Overview of free tools for pentest web-resources and not only v2
Update:
1) Armitage - digestible software-interlayer. Works in conjunction with metasploit (by RPC) and nmap. Written in JAVA, uses postgreSQL / mysql. Included in the backtrack distro recently. What resembles the same XSpider (in terms of does not require special knowledge of information security) is only richer in functionality due to metasploit. © Ierixon
Source: https://habr.com/ru/post/125206/
All Articles