Methods and tools for the protection of customers' personal data in solutions on the Bitrix platform
Today we will talk about the protection of personal data of customers and other equally important aspects of information security of web projects.
Recently, the field of development has been undergoing a rather rapid transition from classical software development practices - a long, slow, thorough, thorough approach, in which everything is carefully designed, thought out, tested dozens of times - to Agile techniques that ensure rapid product development with a simultaneous constant flow of changes. in its functionality both during development and after the first release.
Many more clearly understand that if you write software for a long time and correctly, then it may be simply unnecessary and outdated by the time it enters the market. Therefore, the following approach is increasingly being observed, including in the development of web projects:
In addition to the obvious advantages of "fast" development:
There are risks and threats, the importance of which is often difficult to assess for a non-professional:
The situation is aggravated by the fact that information technologies are becoming more and more complicated and confusing, and the programmer must be able to understand the rapidly increasing cone of adjacent, often dissimilar, technologies. But time for study is either not allocated, or is given inadequately little. People are actually forced to learn from ... real projects.
')
One of the possible solutions to the above problem: “make web projects quickly, efficiently and without holes” - use ready-made tools, libraries and frameworks designed and implemented by experts in the field of information security. Tools that keep up with the times and protect us from the constantly emerging threats.
The Bitrix platform is simply stuffed with effective information security tools for web projects.
Probably many people know that in our company there is an information security department, whose task is to thoroughly audit the entire generated code of the Bitrix platform. Therefore, the core of the platform is maximally protected, as evidenced by the good results at the hacker festival CC9 and the results of an independent audit by renowned security expert Positive Technologies .

Moreover, due to the policy of total verification of data transmitted by the platform's core API (yes, to the detriment of performance), the common threat of web-based SQL Injection projects is excluded (if the web project code works strictly through the API, which is included in our standards integration quality), and the likelihood of XSS attacks is seriously reduced.
Also, information security specialists constantly monitor external information threats and create / develop proactive tools to protect web projects - which we will consider further.
You have “Security Panel” in front of your eyes and your task is to perform the recommended settings to increase, if necessary, the “current security level” from “Initial” to “Standard” and above. Simply and clearly - if you want more security, then increase the level by following the recommendations of the expert system.
This panel looks like this:

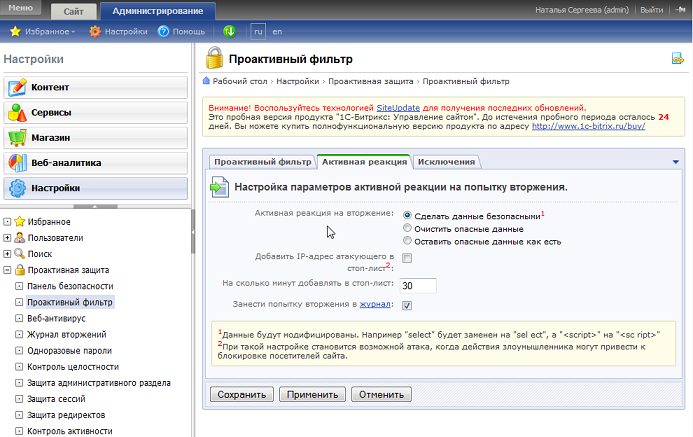
“Proactive Filter (Web Application Firewall)” - the subsystem filters all data transmitted to a web project (posts, cookies, etc.) for exploiting known vulnerabilities: XSS, SQL Injection, PHP Including, and several others. Of course, false positives can occur, so the tool is customizable.
It is important to note that the tool does not protect the core of the Bitrix platform, which is safe by itself (see above), namely, the “add-on platform”, made by programmers - a web project based on 1C-Bitrix. Unfortunately, due to lack of budget, time and qualification, the program code “sometimes” is not well enough checked by programmers for information security - and this powerful tool insures against possible errors and holes of this kind. Therefore, if development on the platform is led, in your opinion, by a “weak” development team - a tool for you!
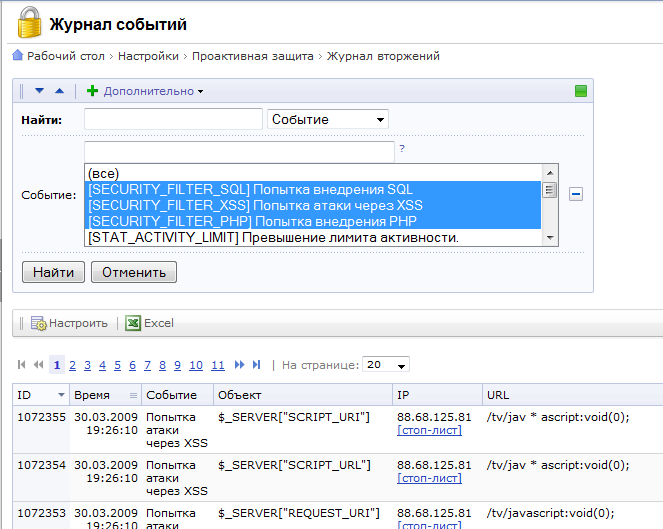
And of course, all attacks are recorded in the event log.
This is how it works:
This tool works a little differently from the previous one - it filters the information transmitted to the web project client browser.
Unfortunately, the computers of administrators and managers of web projects are often infected with viruses. Viruses extract passwords from browsers, FTP clients and other web project management tools and ... infect web project files themselves. In the morning, customers start calling you and say that you cannot go to the site, because it is infected and instead of the site a red window opens with a warning - all due to the fact that one of the web project managers came home from an infected computer at night and added ... infected news to the site.
This tool, of course, does not replace anti-virus software, but acts in unison with it and definitely insures you against errors in the security policy of the web project. And, like any antivirus, it is periodically updated via the Internet.
The idea here is that user accounts and administrators of a web project are tied to groups with different security levels (the higher the security, the lower the convenience of working with the system).
You can select a group's security level from the list, or you can play with “tasty” parameters manually (if you understand what they mean). The more authority the group has, the more security it should, in an amicable way, be:

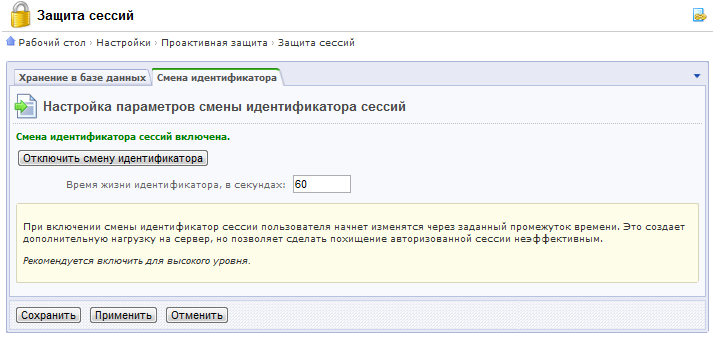
After authorization between the client and the web project, the session identifier begins to walk, which is often the goal of hackers. To protect the session on shared hosting, we offer to store them in a database, and to make it more difficult for attacks on a session, we give the opportunity to change its identifier.
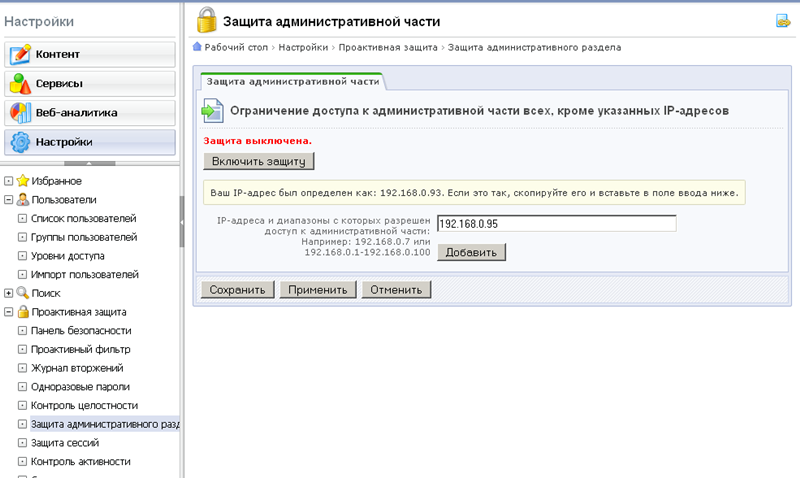
It is useful to allow access to the administrative section of a web project with certain subnets by means of system administration - but we also provide a tool that facilitates this task. The tool is quite popular and convenient - especially on shared hosting:
And this is how you like. It is wasteful and inconvenient to encrypt all client traffic with a web project (although some really want to do this to ensure security). But certain sections containing personal data and authorization points are very useful.
Directly in the platform, we do not do this - placing the task of providing SSL to the system administration service and the web solution designer.
At the summer partner conference, we announced the release in the next release of the platform technology to protect the password from being transmitted in clear text (not everyone has the opportunity to configure SSL) - based on asymmetric cryptography (we encrypt the password with JavaScript in the client browser, RSA 1024 bit).
Of course, you can protect the authorization procedure on a web project using SSL from intercepting passwords by formidable hackers, but ... it will not save you from password leaks, especially administrative ones, via other channels - e-mail, papers on the table and in the nightstand, desktop recordings etc.
For maximum password protection, they often use two-factor authentication. The Bitrix platform implements a variation of this technology . You distribute cute key chains to employees or use software to generate one-time passwords . Now you can be sure that (to a certain extent) that a) intercepting a password becomes a useless task, b) if Vasily Pupkin logged in to the site, then it is he who chooses himself, or Vasily - but at gunpoint.
Thanks to the professional tools for ensuring information security and personal data protection built into the Bitrix platform, mass-produced solutions based on it can be considered “fairly durable and sustainable.”
By creating a web project on 1C-Bitrix you (or our Partner) can concentrate efforts and budget on the problem being solved, trusting the security issues of the platform and its tools.
However, you need to be well aware that the struggle for the security of a web project must constantly go on all fronts, there is no silver bullet and only a systematic approach, well-thought-out business processes and information security policies will make your web project an impregnable strength of ... 99.9%.
Sincerely, Head of Integration and Implementation Quality Control
Alexander Serbul
The speed and complexity of development is constantly growing
Recently, the field of development has been undergoing a rather rapid transition from classical software development practices - a long, slow, thorough, thorough approach, in which everything is carefully designed, thought out, tested dozens of times - to Agile techniques that ensure rapid product development with a simultaneous constant flow of changes. in its functionality both during development and after the first release.
Many more clearly understand that if you write software for a long time and correctly, then it may be simply unnecessary and outdated by the time it enters the market. Therefore, the following approach is increasingly being observed, including in the development of web projects:
- Intense short brainstorming project concept
- A rough “guessing” of the plan of release iterations (for 1-6 months) with the ordering of the web project features described by a simple language in descending order of priority. And they are trying to release the first release in production as quickly as possible, even “piece by piece”.
- Selection and rapid assessment of the most priority features that can be done in 2-4 weeks by the development team (no more than a day)
- Fast design (no more than a day) with the use of boards and other means of collective communication and the development of the selected priority functionality
- Demonstration of "quickly done" functionality, receiving feedback from users (first within the company), testing by users
- Conclusion of the made functional in production for the fastest receiving feedback and ... more intensive testing :-)
- Go to step 3 and so on in a circle
Problems of "fast" development of web projects
In addition to the obvious advantages of "fast" development:
- Users get the most requested functionality as quickly as possible.
- Developers deal only with the highest priority tasks.
- The web project keeps pace with the times, promptly responding to market challenges and user requests and adequately changing
- Bureaucracy, medium-term and long-term planning are reduced to almost zero - all efforts are devoted to identifying and planning immediate tasks.
There are risks and threats, the importance of which is often difficult to assess for a non-professional:
- Due to lack of time and limited budget, the architecture of a web project is poorly thought out, which can cause it, for example, to “slow down” or it will become difficult and expensive to develop
- Due to the lack of time and limited budget, as well as possibly insufficient qualification of IT specialists, insufficient attention is paid to the security of web projects.
The situation is aggravated by the fact that information technologies are becoming more and more complicated and confusing, and the programmer must be able to understand the rapidly increasing cone of adjacent, often dissimilar, technologies. But time for study is either not allocated, or is given inadequately little. People are actually forced to learn from ... real projects.
')
What to do?
One of the possible solutions to the above problem: “make web projects quickly, efficiently and without holes” - use ready-made tools, libraries and frameworks designed and implemented by experts in the field of information security. Tools that keep up with the times and protect us from the constantly emerging threats.
The Bitrix platform is simply stuffed with effective information security tools for web projects.
The core of the platform Bitrix - "Die Hard"
Probably many people know that in our company there is an information security department, whose task is to thoroughly audit the entire generated code of the Bitrix platform. Therefore, the core of the platform is maximally protected, as evidenced by the good results at the hacker festival CC9 and the results of an independent audit by renowned security expert Positive Technologies .

Moreover, due to the policy of total verification of data transmitted by the platform's core API (yes, to the detriment of performance), the common threat of web-based SQL Injection projects is excluded (if the web project code works strictly through the API, which is included in our standards integration quality), and the likelihood of XSS attacks is seriously reduced.
Also, information security specialists constantly monitor external information threats and create / develop proactive tools to protect web projects - which we will consider further.
"Visualization" of the security status of a web project
You have “Security Panel” in front of your eyes and your task is to perform the recommended settings to increase, if necessary, the “current security level” from “Initial” to “Standard” and above. Simply and clearly - if you want more security, then increase the level by following the recommendations of the expert system.
This panel looks like this:

We filter the input data of the web project
“Proactive Filter (Web Application Firewall)” - the subsystem filters all data transmitted to a web project (posts, cookies, etc.) for exploiting known vulnerabilities: XSS, SQL Injection, PHP Including, and several others. Of course, false positives can occur, so the tool is customizable.
It is important to note that the tool does not protect the core of the Bitrix platform, which is safe by itself (see above), namely, the “add-on platform”, made by programmers - a web project based on 1C-Bitrix. Unfortunately, due to lack of budget, time and qualification, the program code “sometimes” is not well enough checked by programmers for information security - and this powerful tool insures against possible errors and holes of this kind. Therefore, if development on the platform is led, in your opinion, by a “weak” development team - a tool for you!
And of course, all attacks are recorded in the event log.
This is how it works:


Web antivirus
This tool works a little differently from the previous one - it filters the information transmitted to the web project client browser.
Unfortunately, the computers of administrators and managers of web projects are often infected with viruses. Viruses extract passwords from browsers, FTP clients and other web project management tools and ... infect web project files themselves. In the morning, customers start calling you and say that you cannot go to the site, because it is infected and instead of the site a red window opens with a warning - all due to the fact that one of the web project managers came home from an infected computer at night and added ... infected news to the site.
This tool, of course, does not replace anti-virus software, but acts in unison with it and definitely insures you against errors in the security policy of the web project. And, like any antivirus, it is periodically updated via the Internet.
Group security policies
The idea here is that user accounts and administrators of a web project are tied to groups with different security levels (the higher the security, the lower the convenience of working with the system).
You can select a group's security level from the list, or you can play with “tasty” parameters manually (if you understand what they mean). The more authority the group has, the more security it should, in an amicable way, be:

Session Security
After authorization between the client and the web project, the session identifier begins to walk, which is often the goal of hackers. To protect the session on shared hosting, we offer to store them in a database, and to make it more difficult for attacks on a session, we give the opportunity to change its identifier.

Administrative section protection
It is useful to allow access to the administrative section of a web project with certain subnets by means of system administration - but we also provide a tool that facilitates this task. The tool is quite popular and convenient - especially on shared hosting:

SSL or not SSL?
And this is how you like. It is wasteful and inconvenient to encrypt all client traffic with a web project (although some really want to do this to ensure security). But certain sections containing personal data and authorization points are very useful.
Directly in the platform, we do not do this - placing the task of providing SSL to the system administration service and the web solution designer.
At the summer partner conference, we announced the release in the next release of the platform technology to protect the password from being transmitted in clear text (not everyone has the opportunity to configure SSL) - based on asymmetric cryptography (we encrypt the password with JavaScript in the client browser, RSA 1024 bit).
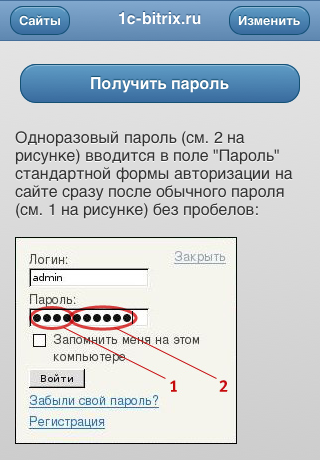
One-time passwords
Of course, you can protect the authorization procedure on a web project using SSL from intercepting passwords by formidable hackers, but ... it will not save you from password leaks, especially administrative ones, via other channels - e-mail, papers on the table and in the nightstand, desktop recordings etc.
For maximum password protection, they often use two-factor authentication. The Bitrix platform implements a variation of this technology . You distribute cute key chains to employees or use software to generate one-time passwords . Now you can be sure that (to a certain extent) that a) intercepting a password becomes a useless task, b) if Vasily Pupkin logged in to the site, then it is he who chooses himself, or Vasily - but at gunpoint.

findings
Thanks to the professional tools for ensuring information security and personal data protection built into the Bitrix platform, mass-produced solutions based on it can be considered “fairly durable and sustainable.”
By creating a web project on 1C-Bitrix you (or our Partner) can concentrate efforts and budget on the problem being solved, trusting the security issues of the platform and its tools.
However, you need to be well aware that the struggle for the security of a web project must constantly go on all fronts, there is no silver bullet and only a systematic approach, well-thought-out business processes and information security policies will make your web project an impregnable strength of ... 99.9%.
Sincerely, Head of Integration and Implementation Quality Control
Alexander Serbul
Source: https://habr.com/ru/post/124952/
All Articles