Security system, smart home project (part 2)
 In the previous post, the initial stage of creating a security system was described, with a detailed description of the selection and connection of sensors to the microcontroller, the transfer of information to a computer and the creation of a room layout for testing and debugging the system itself. You can read about it here on Habré and in more detail here on the project website . And at the end of that article, we shared our plans for the further development of the project, which were adjusted after some comments (thank you so much for that).
In the previous post, the initial stage of creating a security system was described, with a detailed description of the selection and connection of sensors to the microcontroller, the transfer of information to a computer and the creation of a room layout for testing and debugging the system itself. You can read about it here on Habré and in more detail here on the project website . And at the end of that article, we shared our plans for the further development of the project, which were adjusted after some comments (thank you so much for that).Below, after the habrakat, there will be a short story about how social resources can be used for notifications, in particular twitter, as well as making a turntable controlled by a microcontroller out of available tools, and at the end there will be results and development plans.
We use Twitter for communication
When developing a security system, the task was not only to display data on a computer, but also the ability to view the status of a protected object in any place and at any time. In this case, two ways of notification were considered: the first is to report via SMS, and the second is to receive messages through social services and networks (Vkontakte, twitter, facebook).
As you can guess from the header was chosen the second way. And for the beginning, 3 ways of solving messages were allocated (they all use the functions of the Twitter API):
1) Direct .
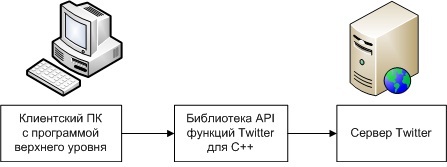
direct connection method
Here, I think, comments are not required.
2) Consistent .
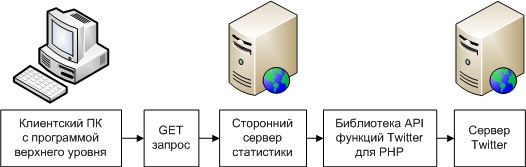
serial connection method
This path was allocated for debugging equipment, collecting and analyzing the data (false positives, etc.).
3) Sequential independent .
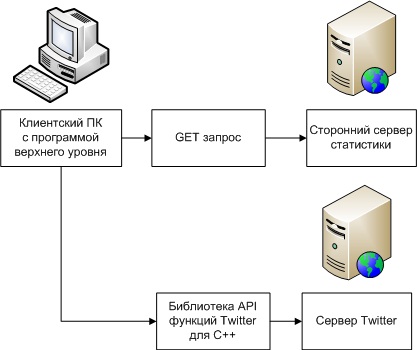
serial independent connection method
Here, we see that the data is first sent to the Twitter server, and then to a third-party statistics server.
Due to the fact that a statistical tool was needed, the choice was between the 2 and 3 way. In our opinion, the second method (sequential) was simpler to implement. We took up its development.
To implement the server part, the TwitterOAuth library (a Twitter API library) was used by Abraham Williams dev.twitter.com/docs/twitter-libraries#php and the GET method.
And for the top-level program written for the computer, the standard Windows API functions and the winsock2.h library were used.
And here's the result

')
Creating a PTZ camera
In our project, the engine should perform the following function - webcam rotation, that is, it was planned to create a cheap analogue of the dome camera.
When choosing a stepper motor, the main attention was paid to two main parameters - size and cheapness. Size, as the main purpose - the rotation of the camera, the weight of which is not more than 150 grams. Cheapness due to the fact that the entire security system should not be expensive, but to pay 30 - 40 dollars only for the engine itself is an obvious overkill. A way out of this situation was found.
Suffice it to recall that almost everyone has an old computer with disk drives, and the components we need are there. If not, you can go to the radio market, or to the commission shop, where you can buy for $ 3-4 apiece, agree 3 and 30 there is a difference.
To control the stepper motor, a circuit consisting of a processor, an ILN2003 chip (a seven-channel driver and an analogue of ULN2003A) and the stepper motor “bitten out” from the printer was used.

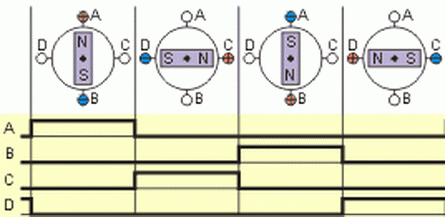
To control the engine, the “one phase on full step” mode was selected; the operation diagram for this mode is shown below:
Video, quality is not very, filmed on the phone
How the whole system works
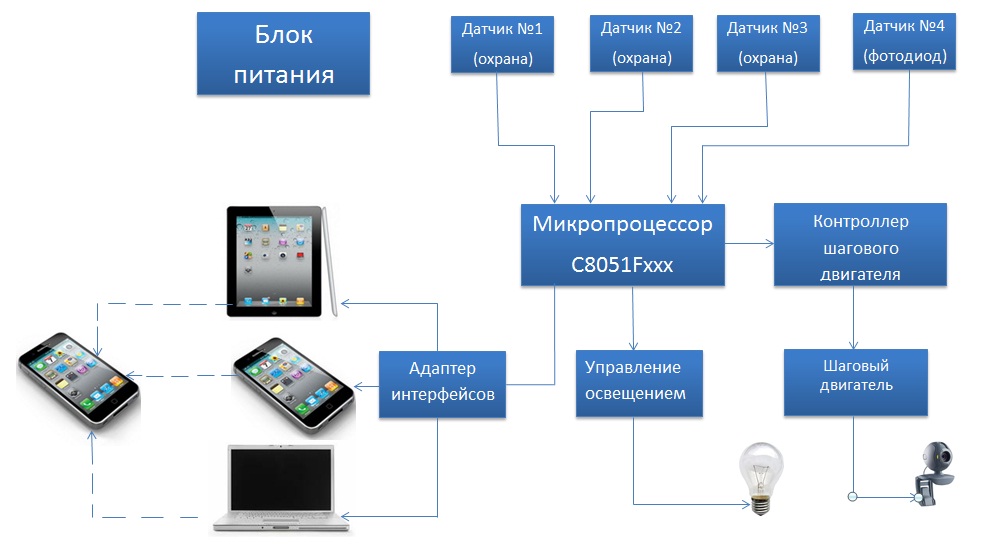
The system was developed on the basis of what will be used in small spaces. In this case, the sensors are installed in places of possible penetration (doors, windows), then they are all connected to the security loop. Information from the sensors goes to a control panel that processes the received data and if a penetration attempt occurs, it performs the following sequence of commands:
- re-check the status of the loop;
- turn the camera to the place where the sensor is installed;
- sending a message to a computer, iPhone, where a special application is installed that can send information to your twitter account or mail;
- checking the illumination in the room using a connected photodiode and, if necessary, switching on the light;
- sending a message to a computer, iPhone, where a special application is installed that can send a photo taken by a webcam to your twitpick account;
- switch to polling mode of other sensors.
The scheme of the system is presented below.
Conclusion and Plans
Above, we have considered notification methods, stepper motor control and the algorithm of the system itself. In the third and final part, we will show the video work of all the previously described elements and prepare the final video presentation.
For the development of the project, a new website was created - make-smart-room.com , where detailed materials on each reviewed component of the security system were posted. A huge request to help with tips and suggestions for further development.
Source: https://habr.com/ru/post/124446/
All Articles