New types of attacks based on technology clickjacking
Clickjacking - a mechanism to deceive users, in which clicking on a link on a website redirects a user to a malicious page - has become very effective. It is often used to distribute links to malicious sites via Facebook. Recently, such techniques have shown their effectiveness in deanonymizing visitors to the site. Also, clicking on a tricky link can lead to an attacker gaining access to OAuth data. Let's see how this happens.
In the classic clickjacking scenario, an attacker hides the “Like” or “Share” button in a transparent iframe. This iframe is located above the element of the page that the user should click on; also the iframe can be moved behind the mouse cursor. When you click on an item, the click is redirected to the invisible “Like” or “Share” button. Such actions are not limited to Facebook, the attacker only needs to be able to hide the elements of another site in the iframe.
Below is a typical message that can be seen on Facebook if one of your connections was intercepted using clickjacking:
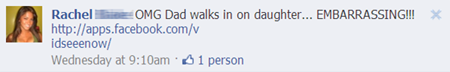
')
Following the link shared by your friend, you will be taken to the site with YouTube videos. However, you will not see the “Like” buttons that I highlighted in the screenshot below:

“Like” buttons are located where the user usually clicks to view the video: in the middle of the window and in the lower left corner. The victim will not see these buttons, because they are in an invisible transparent iframe. By launching this video, the user clicks the “Like” button, increasing the popularity of the site on Facebook.
In the work of Clickjacking Attacks Unresolved , Lin-Shung Huang and Collin Jackson considered more subtle variations of clickjacking. For example, they demonstrated how an attacker can identify a user of a malicious site by requesting his information from Facebook.
I recorded a demo video deanonymization user. The video shows a “Like” button, which moves behind the victim’s cursor, but in a real attack, the button would be invisible. When a user inadvertently presses this button, he will become a friend of the attacker on Facebook (I apologize for possible inaccuracy in terms of Facebook, I don’t use Facebook myself - comment. Trans. ).
Then the attacker's page via FB.Event.subscribe ('edge.create', ...) finds out that the victim pressed the “Like” button, sends a message to the attacker's server, which receives the list of friends and identifies the new friend. The server requests the user's public information through the Facebook Graph API, and removes the user from the list of friends.
These actions allow an attacker to obtain public user data, including user id. The authors of the work demonstrate this attack by conducting it using the Twitter button “Follow”:

Huang and Jackson described a click-timing attack, called double-click jacking, in which the user is redirected to the OAuth providers via an attacker's request. According to the document, this approach works even if such measures are taken against clickjacking using an iframe, such as X-Frame-Options .
Although the attacker cannot insert an iframe on such sites, he can load the OAuth page in the pop-under window. The pop-under window after opening is hidden behind the browser window. Since browsers began to block pop-ups that open without user intervention, this attack requires a large number of clicks to bypass pop-up blocking.
To see the conceptual double clickjacking attack code, click on the Clickjacking Attacks Unresolved link.
Clickjacking has done and continues to do a lot of damage. Most of the attacks used the distribution of malicious links through Facebook. But this approach can be used for more tricky scenarios. In the work of Huang and Jackson are recommendations that will allow developers of sites and browsers to reduce the risk of clickjacking. However, these techniques are not comprehensive. The worst thing is that you can not give practical advice, the use of which will protect users.
The classic use of clickjacking is to spread links via Facebook.
In the classic clickjacking scenario, an attacker hides the “Like” or “Share” button in a transparent iframe. This iframe is located above the element of the page that the user should click on; also the iframe can be moved behind the mouse cursor. When you click on an item, the click is redirected to the invisible “Like” or “Share” button. Such actions are not limited to Facebook, the attacker only needs to be able to hide the elements of another site in the iframe.
Below is a typical message that can be seen on Facebook if one of your connections was intercepted using clickjacking:

')
Following the link shared by your friend, you will be taken to the site with YouTube videos. However, you will not see the “Like” buttons that I highlighted in the screenshot below:

“Like” buttons are located where the user usually clicks to view the video: in the middle of the window and in the lower left corner. The victim will not see these buttons, because they are in an invisible transparent iframe. By launching this video, the user clicks the “Like” button, increasing the popularity of the site on Facebook.
New variations of clickjacking techniques
In the work of Clickjacking Attacks Unresolved , Lin-Shung Huang and Collin Jackson considered more subtle variations of clickjacking. For example, they demonstrated how an attacker can identify a user of a malicious site by requesting his information from Facebook.
I recorded a demo video deanonymization user. The video shows a “Like” button, which moves behind the victim’s cursor, but in a real attack, the button would be invisible. When a user inadvertently presses this button, he will become a friend of the attacker on Facebook (I apologize for possible inaccuracy in terms of Facebook, I don’t use Facebook myself - comment. Trans. ).
Then the attacker's page via FB.Event.subscribe ('edge.create', ...) finds out that the victim pressed the “Like” button, sends a message to the attacker's server, which receives the list of friends and identifies the new friend. The server requests the user's public information through the Facebook Graph API, and removes the user from the list of friends.
These actions allow an attacker to obtain public user data, including user id. The authors of the work demonstrate this attack by conducting it using the Twitter button “Follow”:

Clickjacking and timing attacks
Huang and Jackson described a click-timing attack, called double-click jacking, in which the user is redirected to the OAuth providers via an attacker's request. According to the document, this approach works even if such measures are taken against clickjacking using an iframe, such as X-Frame-Options .
Although the attacker cannot insert an iframe on such sites, he can load the OAuth page in the pop-under window. The pop-under window after opening is hidden behind the browser window. Since browsers began to block pop-ups that open without user intervention, this attack requires a large number of clicks to bypass pop-up blocking.
To see the conceptual double clickjacking attack code, click on the Clickjacking Attacks Unresolved link.
What's next?
Clickjacking has done and continues to do a lot of damage. Most of the attacks used the distribution of malicious links through Facebook. But this approach can be used for more tricky scenarios. In the work of Huang and Jackson are recommendations that will allow developers of sites and browsers to reduce the risk of clickjacking. However, these techniques are not comprehensive. The worst thing is that you can not give practical advice, the use of which will protect users.
Source: https://habr.com/ru/post/123923/
All Articles