Asymmetric cryptography for subscription software licensing with a practical example

 It will be about how the protection of desktop programs, as well as a typical system of licensing and activation of keys. Activation is used in almost any commercial software, and the principles on which it is built is quite interesting, so I decided to write this article.
It will be about how the protection of desktop programs, as well as a typical system of licensing and activation of keys. Activation is used in almost any commercial software, and the principles on which it is built is quite interesting, so I decided to write this article.In the article read:
- About "license", "activation", "hash functions", "digital signature", "asymmetric cryptography" and (in short) about RSA and DSA, without formulas and mathematics.
- How subscription mechanism (subscription) differs from traditional licensing.
- Application of the described principles on the example of the VMProtect EXE protector.
So let's get started.
')
How the subscription program works with the license server
Because we promote the idea of monthly micro listings for the use of commercial software (instead of the traditional sale of expensive “one-time” keys), we are interested in how the program should interact with the license server on a periodic basis so that it cannot be “fooled”.
Subscription is the ability to run the program for a monthly subscription. When the payment is not received, the program is blocked - and vice versa, if the money has arrived, it continues to work.Naturally, the product must somehow determine whether it can be launched at any given time or not (whether the subscription was blocked due to lack of funds in the account). To do this, he uses Internet access and regular (for example, once every 5 days) calls to a special license server .
 There is one unreliable way to determine if a program is allowed to work. She may ask the license server: “Here is the key that the user entered into me. Can I work with him now? ” The license server will respond - "Yes, you can" or "No, subscription is blocked." Of course, this method is bad because it allows an attacker to easily fake the server’s response, and the same program will need access to the Internet every time it starts (after all, it cannot easily maintain the “can work” status without the attacker finding this place).
There is one unreliable way to determine if a program is allowed to work. She may ask the license server: “Here is the key that the user entered into me. Can I work with him now? ” The license server will respond - "Yes, you can" or "No, subscription is blocked." Of course, this method is bad because it allows an attacker to easily fake the server’s response, and the same program will need access to the Internet every time it starts (after all, it cannot easily maintain the “can work” status without the attacker finding this place). To ensure security, a different scheme is used, when the license server does not issue a yes / no answer, but a certain quantum of information - as if a temporary work permit for a short period (the same 5 days), and the program already decides when making a decision on this quantum.
To ensure security, a different scheme is used, when the license server does not issue a yes / no answer, but a certain quantum of information - as if a temporary work permit for a short period (the same 5 days), and the program already decides when making a decision on this quantum.But in order to understand the whole scheme, we will conduct a brief excursion into the traditional ways of working with "perpetual" keys and asymmetric cryptography mechanisms.
What is key activation?
Traditionally, when an electronic purchase of a program is sent to the user, a key generated specifically for it (or a license, or a serial number - as someone calls). The user then enters this key into the running product and, ultimately, activates it (makes it work).
How does the program, by accepting the key, determine that it is authentic? There are two main ways to do this:
- You can verify that the key was generated by a special algorithm known to the program, and, if it is not, to block the work. They acted like this in the old days, when there was not yet a general internet. Naturally, in this case, the key can be stolen and later used on another computer, so this method is unreliable.
- The program can ask for the activation of “feedback” from its developer: the user will inform the developer of the key and some additional information about himself, and the developer, on the basis of this information, will understand whether to allow the program to work ( activate it or not).
 It is clear that the second method is better protected from theft of the key: the developer can control the number of activations. The presence of “feedback” in this case is mandatory: the user must somehow tell the developer his key and other information about himself, and the developer must give the activation permission. Earlier, when the Internet was not yet so common, everything was done on the phone : the user called support service, dictated his key and, for example, the identifier of the equipment of his computer. Instead, he was informed of the activation code - a certain sequence of characters, which, when entered into the program along with the key, activates it.
It is clear that the second method is better protected from theft of the key: the developer can control the number of activations. The presence of “feedback” in this case is mandatory: the user must somehow tell the developer his key and other information about himself, and the developer must give the activation permission. Earlier, when the Internet was not yet so common, everything was done on the phone : the user called support service, dictated his key and, for example, the identifier of the equipment of his computer. Instead, he was informed of the activation code - a certain sequence of characters, which, when entered into the program along with the key, activates it.Please note that in this example, the equipment identifier was used as “additional information about yourself” - a hash code that more or less uniquely identifies the user's machine. The one who steals the key will have a different hash code, so if he calls the support service, he will not achieve anything - they will understand that they are trying to re-activate.
Internet activation
With the advent of the Internet in every home, the need for telephone calls has disappeared: now the program itself “calls” to the so-called developer license server , “dictates” the key and equipment code to it, and in exchange, it is “informed” by the activation code, which activates itself. According to this scheme, the vast majority of programs now work, and it is quite reliable.
In general, we have formed the following entities:
- Key: what is issued to the user upon purchase.
- Equipment identifier: a certain number, with varying degrees of uniqueness, which characterizes a user's computer (on different computers it will be different).
- Activation code: the coded "permission" for the program to start if the user has a certain key and a certain hardware identifier in his hands.
- License server: some server on the Internet, controlled by the developer and able to use a pair of “key” + “hardware identifier” to return the activation code to the user.
Public and private key: asymmetric digital signature
It would seem that it is possible to calculate the value of
activationCode = md5(key + hardwareID) : in this case, the license server will be able to generate it, and the program at the client will check the correctness.However, there is a serious danger here: since the license server can calculate this value, then the attacker too. This means that an attacker can make his own license server, “substitute” it instead of the original one and ... gain unlimited control over the program. What to do?
They say that every complex task has one simple, logical, easy to understand ... wrong decision. In this case, such a wrong decision would be the formula
activationCode = md5(key + hardwareID + salt)where
salt is a certain “secret” string known only to the developer’s license server.Unfortunately, such a trick with the “salt” will not work, because the client’s program must also be able to calculate theIn general, the value
S = md5(X + salt)is called the “digital signature of theXdata with the salt ofsalt”. Verify the digital signatureSmeans again to calculatemd5(X + salt), already on the other side, and compare the result withS: if it coincides, then the signature is correct, if not - then there is a fake.
md5(key + hardwareID + salt) value md5(key + hardwareID + salt) , which means that the salt must be “sewn” into it initially. Of course, an attacker will be able to disassemble the product and find salt in it, and then organize a fake license server. We returned to the same, where we started.But there is a solution, and it is called DSA . It turns out that there is such an algorithm, which, roughly speaking, allows you to get an
activationCode hash code using a single salt0 value, and to check the "correctness" of this hash code - already with a completely different salt1 value. The salt0 value needs to be kept secret - it is stored only on the license server, while salt1 does not represent any value for the attacker - knowing it, he still will not be able to get salt0 and calculate the correct activation codes.Thus, the license server calculates the digital signature
activationCode = DSA(X, salt0) and transfers the value to the client program, and the program checks its correctness using the DSA_check(activationCode, X, salt1) algorithm DSA_check(activationCode, X, salt1) . In this case, salt0 is called the “private key” (private key), and salt1 is called the “public key”. The “public” key is called because it can even be printed in a newspaper - it will not harm security.Details about the DSA digital signature algorithm and the RSA data encryption algorithm based on the same principle can be found on Wikipedia in Russian. In short, the RSA principle of operation is based on the so-called “factorization problem” - the complexity of decomposing large numbers into factors. Indeed, having two 2000-digit prime numbersXandY, you can calculate their 4000-digit productS = X * Yin a microsecond. However, having this productSand not knowingXorYinitially, during the existence of the Universe it is impossible to restore the originalXandYfrom which it is composed. At a qualitative level, we can assume that the numbersXandY(the private key) are used to compile a DSA digital signature, and the well-knownSfor verification.
Back to the subscription
At the very beginning we said that a subscription is just a more frequent access to the license server, which returns all new and new activation codes, while the old activation codes become obsolete. For such obsolescence, the algorithm for creating an activation code should be more complicated: in the code, at least, the start and end dates of its validity are “sewn up” (the start is for the user not to translate the clock too far back).
 The operation of the “subscription” program with the license server is as follows:
The operation of the “subscription” program with the license server is as follows:- Regularly and in the background, the program attempts to contact the license server to get a fresh activation code from it. The key and the hardware identifier are transmitted to the server;
GET / license_server? Key = abcdef & hwid = 1234
- If the attempt was unsuccessful, then nothing happens - no messages are issued.
- In the case of luck, the fresh activation code issued by the server is recorded in some permanent storage (for example, in the Registry) - anyway, it is of no interest to the attacker, since he will not be able to use it in his (the activation code depends on the equipment identifier that the attacker will have on the other).
- Regardless, the program takes the current activation code from the persistent store and verifies its digital signature using the key, the equipment identifier and the public parameter salt1. If the activation code is correct, then the program continues to work (perhaps, simultaneously removing some necessary data from the code - for example, the encryption settings of the virtual machine code, as is done in VMProtect).
Those. when working on a subscription, the activation code is requested regularly, and in the case of the operation of the “traditional” scheme with key activation - one time. This is the technical difference. Of course, the license server must work reliably and withstand high loads, so we have two of them in balancing, they are written in Java Netty - a framework for creating asynchronous web servers, the one to which Twitter has recently transferred its search. But this is a topic for a separate article.
An example of creating a subscription version of your program
Above was the theory of how a license server can handle serving requests for checking subscription status. Now let's touch on the practice and see how the developers of VMProtect Software implemented this theory when creating a subscription version of the VMProtect protector for our RentSoft platform .
Creating a HelloWorld application and its MAP file
To begin with, we will create a program like “Hello, world!”, Which we will protect with VMProtect. We will use MS Visual Studio 2010: we will create a new project in it like “Win32 Application” and call it HelloWorld. The main file will look something like this:
#include "stdafx.h"Immediately switch the project build mode to Release in the Configuration Manager. After that, we will enable the generation of the MAP file : it will contain the addresses of all functions inside the EXE file, so that VMProtect can then find them. This is done in the project properties, in the Russian version the path is as follows: right-click on the project name in the Solution Explorer, then select Configuration Properties - Linker - Debug - Create Mapping File.
...
ATOM MyRegisterClass ( HINSTANCE hInstance )
{ ... }
...
LRESULT CALLBACK WndProc ( HWND hWnd, UINT message, WPARAM wParam, LPARAM lParam )
{ ... }
...
Now press F5 and make sure that the project is compiled and run. We received in the Release directory 2 files:
HelloWorld.exe and HelloWorld.map , with which we will work.
Product Registration Wizard on RentSoft License Server
The subscription version of the program works closely with the license server, which, in fact, checks the status of the key and determines whether the program can work or not. The license server must have product information: for example, the RSA encryption private key and other licensing parameters, so the product needs to be registered on it.
It's quite simple: at the address http://rentsoft.ru/soft/add/, choose the option “VMProtect RentSoft Edition (free for RentSoft clients)”, enter your e-mail (you will not need to confirm it, by the way) and get into the Master product registration. In it, we enter the following data:
- The name of the product, a brief and detailed description (you can use HTML).
- Image of the box with the product (or its logo).
- Choose the desired subscription price per month - for example, 79 rubles.
The license file is required to associate the protected program with the product that we have just registered on the license server. Save it to the project source directory - in our case, next to
HelloWorld.cpp .Launch VMProtect to create a subscription version
Next, launch VMProtect RentSoft Edition (the link to its installer download is given in the next step of the wizard). This is an .exe file protector created by our partners VMProtect Software. Open through the File - Open EXE project file
Release/HelloWorld.exe and set the parameters as in the screenshot (the main thing is to specify the path to the project license file):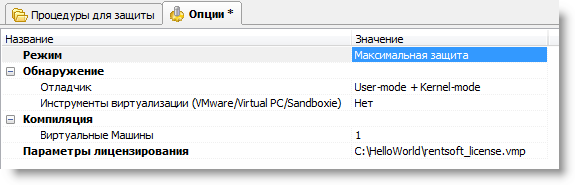
Now go to the Procedures tab for protection and select the procedures and functions on it that you want to protect with VMProtect (the code of these procedures will be translated into the code of the VMProtect virtual machine and linked to the product registered earlier on the license server).

In our case, we specified 2 functions:
MyRegisterClass and WndProc - it is them that the hacker will not be able to “hack” now. Please note: you need to select the Ultra type of compilation (the most reliable), and also check the “Snap to serial number” checkbox to “Yes”. Try to protect those features of the program that are not critical to performance, because the virtual machine runs naturally slower than the “native” processor. (Do not forget, after all the manipulations, to save the VMProtect project file: it contains all the options that you chose, so that with the next protection you do not need to select them again: File - Save project as ...)What happens if an attacker can still decipher the VMProtect virtual machine code for some kind of protected program (which is extremely difficult in itself - remember how many attempts were made to decrypt, for example, Skype, which also uses code virtualization technology)? This will not give it access to other programs: after all, the virtual machine requires information contained in the activation code, and it is different for each program. So, without having an activation code issued by the license server, it is physically impossible to make the program work. Forging a license server also does not work - remember about the technology of public / private keys?Finally, choose Project - Compilation and wait a few seconds. As a result, the
HelloWorld.exe file, its protected version, will appear next to HelloWorld.exe . This file is the "subscription" version of your product.Checking what happened
If we now run
HelloWorld.vmp.exe , we will see this: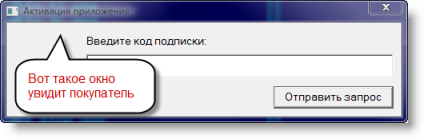
Those. the program at the first launch asks the user to enter the "subscription code", which he received on one of the RentSoft windows when he connected his product to himself. Naturally, RentSoft license server is aware of all active subscription codes, which allows it to process requests from the program and verify the code entered by the user.
Now you need to enter the subscription code. Where can I get it to check? We could send the reader to the product showcase here and say “subscribe to the product - get the subscription code”, but you can do it easier. The RentSoft product registration wizard in which we have just been located allows you to create test subscriptions on the license server. Those. all you need is to click the Create button in the form:
As a result, you will receive a test subscription code, which will remain entered in the program activation window:
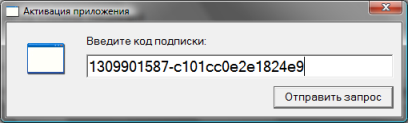
After that, the program will start and will no longer ask the user anything as long as there is money on his account (that is, while the subscription is active).
Suppose there is no money in the account for renewal ...
What happens when a user runs out of money and a subscription is blocked? It is not necessary to wait a month to see it: you can use the same form of work with test subscriptions, which now takes this form:
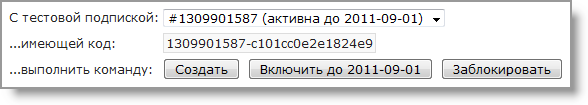
Block the test subscription, and then restart the program twice: the second time it will be blocked with a message about the lack of funds in the account. (Why twice? Consider, you are given the last chance to use the product before it is blocked.)
You may ask what will happen if a subscription is blocked, and the Internet is disabled, and after that start the program. Then the program, of course, does not know that it cannot function, and will work ... but only for the next 5 days. After 5 days, the program will require mandatory Internet access and will refuse to start if there is no connection: the so-called “tolerance period” will expire. So the user will still have to replenish his account, sooner or later.
As for the automatic unlocking when funds are credited to the account, you can check how it works by clicking the "Enable" button and restarting the program. If there is an Internet connection, the program will immediately continue working.
In conclusion - about our sales channels
 Good protection without high sales has, perhaps, an academic interest. We at RentSoft understand this, that is why we provide developers of desktop software with not only a subscription licensing mechanism, but also sales channels - showcases of fifty large Internet providers with a total subscriber base of more than 4 million people . By the way, when we published the previous article , there were 2 less of them: this week, a large Moscow provider NetByNet and St. Petersburg InterZet were added (links lead to our windows in them). On average, we have 2-3 providers each week who connect to us completely independently - we no longer have time to moderate them.
Good protection without high sales has, perhaps, an academic interest. We at RentSoft understand this, that is why we provide developers of desktop software with not only a subscription licensing mechanism, but also sales channels - showcases of fifty large Internet providers with a total subscriber base of more than 4 million people . By the way, when we published the previous article , there were 2 less of them: this week, a large Moscow provider NetByNet and St. Petersburg InterZet were added (links lead to our windows in them). On average, we have 2-3 providers each week who connect to us completely independently - we no longer have time to moderate them.The main advantage of selling under the monthly subscription scheme via Internet providers is that subscribers already bring 400-500 rubles of payment for the Internet to the provider every month. We are able to write off payment for software (which in this case looks like an additional service provider) directly from the subscriber's account. Therefore, when a user connects your program on the provider's website or in his personal account, he pays for it in the same check he pays for the Internet! In short, this is a very effective channel.
So, if you develop desktop software, but sell it mainly to the West, we provide you with free tools to try to sell in Russia using a monthly subscription scheme . We, like any payment system, work for a commission with transactions made by users, but, because you decide the monthly price for your product, this should not be a problem.
Join now!
Source: https://habr.com/ru/post/123908/
All Articles