SCADA under the gun: Analysis of the security of automated process control systems
The Stuxnet worm, found at the Bushehr nuclear power plant, made a lot of noise. “Who was behind all this?” - perhaps this question will not be answered for several decades. Objects of critical infrastructures are of great interest today for many: from competing corporations to the special services of the warring states. 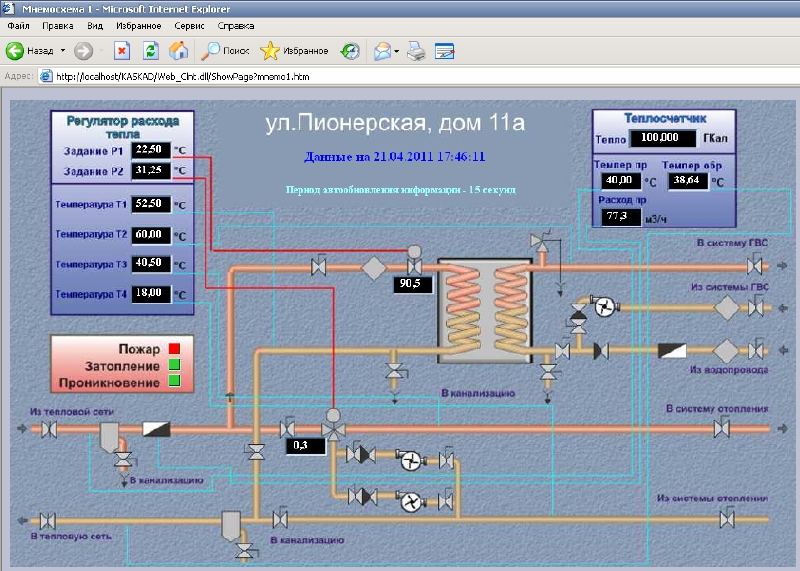
Objects of critical infrastructures are carefully guarded, so it is extremely difficult to pass there or carry something outside into the territory. In this regard, the possibility of a remote attack is of the greatest interest. Today, each state determines for itself a list of the most important objects. And although this list is a state secret, its content is absolutely obvious: electric power facilities, nuclear and nuclear industries, the hydrocarbon transportation sector, petrochemicals, strategic military facilities. Naturally, many of these objects undergo an automation process using information technologies, which in complex is an automated process control system (APCS).
A typical process control system consists of three main components: a dispatch system (SCADA), a telemetry subsystem, and a communication infrastructure based on available industrial data transfer protocols. Often in the foreign literature the term “automated process control system” is omitted, referring only to SCADA systems, although it is important to understand that dispatching does not allow interactive control of the process of the entire control system.
What tools will be required for analyzing the safety of the automated process control system, taking into account that we will have to deal with control and process control systems? Here you will have to work at the junction of technologies and individual special solutions known to you, because 60% of well-known process control systems and SCADA systems are deployed on traditional platforms (Windows, Linux). If necessary, use real-time platforms (hard, soft), such as QNX, which guarantee the execution of a particular operation with a specified time interval in the conditions of the SRV (real-time system), although they still find greater use in military products (UAV, onboard control).
To date, there are not so many highly specialized software for analyzing the security of an automated process control system / SCADA:
In addition, you can use a scanner created by Trend Micro specialists to detect infected sites. You can take it on the website of the company . How do these scanners work and how does Stuxnet work?
Stuxnet registers its RPC server for internal and external interaction with infected nodes as a separate node. The RPC server functionality is configured to issue (check) a version of the worm, as well as to perform the update function (download new instances). The corresponding RPC calls can be made from the control center of this “industrial” botnet.

The center gives the command to check the version (0x00), in case of its “old age” the update function is called (0x04). The availability of the SMB-over-TCP service (TCP 445) is preliminarily checked, after which the vulnerabilities in this version of Stuxnet (for example, MS10-061) are exploited, and a specific named pipe is bind to DCE / RPC (“// browser” - in most cases), search for UUID and its subsequent analysis. Handsomely!
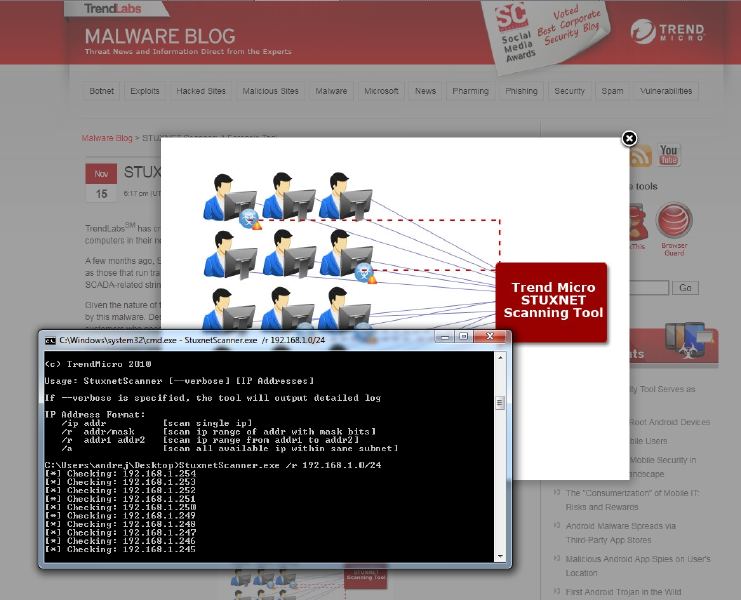
The second way is to search for “loaded” malicious Stuxnet code in task schedulers. Based on this methodology, the Trend Micro scanner works.
Consider visually what threats entails the typical topology of the technological network. It singles out (depending on the nature of technological processes) three zones - corporate (has no relation to management, deals exclusively with business processes), executive (direct link where technological processes are carried out, for example, ammonia is processed or oil is controlled ) and dispatching zone (there are Operators of Industrial Control Systems that are sitting there, which may affect the progress of the technological process).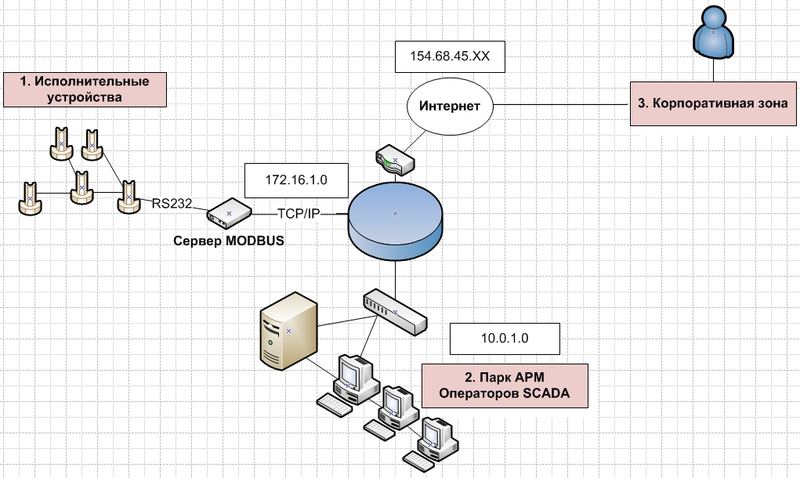
I will share with you a practical story about how I conducted an audit of the system for dispatching the management of heat energy consumption for residential buildings. My main task was to detect existing vulnerabilities in the system and make remote access to key elements of the system.
Designating for itself the range of the network, it was decided to identify the border access gateway in it. It did not take long to search, it was the Cisco Router and Security Device Manager on the Cisco 7301 router, popularly known as CISCO SDM. I needed to access it, if possible to study its configuration file, designate for myself the ranges of internal networks and identify the most valuable there.
Oddly enough, there were two vulnerabilities at the gateway itself:
')
After examining the subnets, I immediately took up the analysis of the network directly from the border router. Naturally, this procedure could be carried out in two ways:
Having discovered lines with TCP port 502 in traffic, it became clear to me a lot, because this port is typical for the MODBUS TCP protocol. By packet routing and destination address it was possible to judge where the control center is located. Actually, this way you can conduct a fully-fledged passive network intelligence from the routing equipment, in particular - from any CISCO router that has the current firmware version.
Having launched the scanner, I realized that someone had already been productively there before me: several nodes were infected with a worm, each of which figuratively told me: “We are waiting for our owner”. It should be noted an interesting fact that the default settings of many SCADA systems recommend organizing anonymous access to DCOM Microsoft Windows OS, which creates huge security holes. Also, many of the industrial protocols do not support encryption for a number of reasons (complexity of implementation on telemetry equipment, increased traffic). In the meantime, hashes taken from the SDM configuration were decrypted. This time, as a hashing algorithm, MD5 was used instead of the native CISCO “secret 7”.
It is easy to see that the hashing algorithm is similar to md5 (unix), so in this case you can resort to using modern software that can recover such types of hashes, namely Passwords Pro, John The Ripper, EGB, and so on, to perform a dictionary attack. Structurally, it looks like this:
A self-made brute forcing might look something like this:
openssl passwd -1 -salt FKKk cisco (in the place of “cisco” - moving words from the dictionary with passwords, if the final hash coincides with the original researched one — luck of selection, absence — continuation of the brut).
Having deciphered the passwords, I began to study the perimeter of the network. Some of the hosts had aliases of external IP addresses, which allowed me to connect to them from the outside. Having gained access to one of the workstations within the network, I began to conduct active reconnaissance of all the devices of the automated process control systems using the SCADA-Auditor software. Any other scanner would show me the available TCP 502 ports that are typical for MODBUS, but I’m not able to establish a native connection and find out the service information from there.
Using the “SCADA-Auditor”, it was required to identify those nodes in the network ranges that contain signs of the placement of dispatch systems or telemetry elements. This can be done on a variety of grounds, if you know what to look for. One of the possible criteria for the search is the output of the SNMP protocol polling if it is available. Also within the network itself, through the administrative panel and the embedded web server, I found the SCADA itself — it was Cascade-ACS. After studying this software package, I identified a number of vulnerabilities:
Having discovered the telemetry nodes controlled by MODBUS, I set to work. Having picked up in the protocol, it is possible to reveal many interesting features.
The trouble with the existing regulatory framework is obvious: there are no clear and explicit requirements for such critical systems as the automated process control system and SCADA in particular. Recently, our experts discovered a typical TZ, which has found its implementation in one of the automated information and measuring systems for commercial metering of electricity (AIIS KUE). Requirements for protection against unauthorized access, according to the RD FSTEC of the Russian Federation, which were taken into account by developers, - 2B. Unfortunately, this class does not take into account many issues, such as signaling attempts to breach security, control subjects' access to programs, network nodes, communication channels, and much more. Problem!
On March 7, 2008 , Unit 2 of the Hatch nuclear station (Georgia, USA), a freelance emergency shutdown for 48 hours after installing the software update (a similar incident occurred in 2006 at the Browns Ferry nuclear station due to an irregular failure of the programmable logical controller when receiving abnormal output network traffic from the production network);
May 2008 , the Tennessee Valley Authority Corporation (TVA) (11 coal-fired power plants, 8 thermal power plants, 3 nuclear power plants, 29 US hydropower plants) are in the statement of this energy corporation, the regulators check (GAO, HHS) revealed about 2000 vulnerabilities of varying degrees of criticality. Among the security holes were identified segments of the production network connected to the Internet, multiple application software vulnerabilities, lack of security updates, errors in the design of the network architecture and data exchange channels;
On August 26, 2008 , the Flight Planning Center of the United States Federal Aviation Administration, the dispatching offices of three dozen American airports, were disabled by a computer malfunction at the Flight Planning Center.
Many facts of hacker penetration into such systems remain behind the scenes. What escaped the public, falls into a special base, one of them - RISI .

Hacker Magazine, July (07) 150
Yuri Kaminkov, STC "Stankoinformzashchita"
Subscribe to "Hacker"

How wide is the hole?
Objects of critical infrastructures are carefully guarded, so it is extremely difficult to pass there or carry something outside into the territory. In this regard, the possibility of a remote attack is of the greatest interest. Today, each state determines for itself a list of the most important objects. And although this list is a state secret, its content is absolutely obvious: electric power facilities, nuclear and nuclear industries, the hydrocarbon transportation sector, petrochemicals, strategic military facilities. Naturally, many of these objects undergo an automation process using information technologies, which in complex is an automated process control system (APCS).
A typical process control system consists of three main components: a dispatch system (SCADA), a telemetry subsystem, and a communication infrastructure based on available industrial data transfer protocols. Often in the foreign literature the term “automated process control system” is omitted, referring only to SCADA systems, although it is important to understand that dispatching does not allow interactive control of the process of the entire control system.
Tool preparation
What tools will be required for analyzing the safety of the automated process control system, taking into account that we will have to deal with control and process control systems? Here you will have to work at the junction of technologies and individual special solutions known to you, because 60% of well-known process control systems and SCADA systems are deployed on traditional platforms (Windows, Linux). If necessary, use real-time platforms (hard, soft), such as QNX, which guarantee the execution of a particular operation with a specified time interval in the conditions of the SRV (real-time system), although they still find greater use in military products (UAV, onboard control).
To date, there are not so many highly specialized software for analyzing the security of an automated process control system / SCADA:
- PC "SCADA-Auditor" (domestic scanner of analysis of security of technological networks, automated process control systems / SCADA);
- Teenable Nessus (contains several modules for testing SCADA systems and a number of programmable logic controllers in the commercial version);
- Rapid7 Metasploit Project (everything is quite sad there: in the “exploits / scada /” section there are only a few pairs of narrowly focused sploits).
How to find nodes infected with Stuxnet
The new version (5.51) of NMAP includes an interesting plugin written in the LUA programming language for NMAP Scripting Engine, its name is “stuxnet-detect”. It is very easy to examine the node for the presence of the Stuxnet worm via an SMB session:nmap --script stuxnet-detect -p 445 <host>In addition, you can use a scanner created by Trend Micro specialists to detect infected sites. You can take it on the website of the company . How do these scanners work and how does Stuxnet work?
Stuxnet registers its RPC server for internal and external interaction with infected nodes as a separate node. The RPC server functionality is configured to issue (check) a version of the worm, as well as to perform the update function (download new instances). The corresponding RPC calls can be made from the control center of this “industrial” botnet.

The center gives the command to check the version (0x00), in case of its “old age” the update function is called (0x04). The availability of the SMB-over-TCP service (TCP 445) is preliminarily checked, after which the vulnerabilities in this version of Stuxnet (for example, MS10-061) are exploited, and a specific named pipe is bind to DCE / RPC (“// browser” - in most cases), search for UUID and its subsequent analysis. Handsomely!

The second way is to search for “loaded” malicious Stuxnet code in task schedulers. Based on this methodology, the Trend Micro scanner works.
Typical threats
Consider visually what threats entails the typical topology of the technological network. It singles out (depending on the nature of technological processes) three zones - corporate (has no relation to management, deals exclusively with business processes), executive (direct link where technological processes are carried out, for example, ammonia is processed or oil is controlled ) and dispatching zone (there are Operators of Industrial Control Systems that are sitting there, which may affect the progress of the technological process).

Typical technological network topology
- Actuators and telemetry subsystem
Very often, the electronic component base of the devices used does not allow introducing there such popular technologies as IPSec, SSL, to organize a VPN. However, access to these devices is always needed. Moreover, some of these devices act as devices for collecting information (telemetry) on the performance indicators of the technological process with sensors and so on. They can also accumulate messages about alarms and accidents, which is very critical. In this regard, it is very important to assign them a publicly available IP address, which, unfortunately, occurs very often. In some situations, this can not be avoided with the assumptions of network design errors. For example, modern industrial controllers can be connected directly or via modem. When connected via modem, they are often combined with GPRS / GSM modems, which by default gives the device the IP address of the mobile operator. With this configuration, they are very vulnerable to attacks from outside. Specialized utilities and methods of the attacker can identify such devices and mess things up a lot of bad things. The actuators themselves, as a rule, are connected via a serial interface (RS-232 / RS-485) to the MODBUS server, and the MODBUS server itself has TCP / IP control via an Ethernet / Industrial Ethernet channel with Operators. - Park ARM-Operators and SCADA systems
These comrades are in the most difficult situation, because questions of the regime among them are often not respected. The second problem is that they are often admitted by foreign specialists who may have no good intentions at all. As the practice of introducing the Stuxnet worm at a nuclear power plant in Bushehr has shown, a malicious program from a USB flash drive was introduced as an engineer for the maintenance unit. How many such comrades wandering around nuclear power plants in the world remains a question. Operators have the ability to connect to the SCADA system, as a rule, with different levels of privileges, plan and implement new projects, change existing ones. Despite the many vulnerabilities in software dispatch systems, the main threat is still insiderism. - Corporate zone (BAN zone - Business Area Network)
In it sit people who, as a rule, are the organization-owner of all that we considered. In the sector of energy or oil transporting organizations, this is especially obvious - their entire economy can be located on very different continents in the form of lines of energy generating complexes or oil rigs in Libya, while they themselves sit in some kind of warm, harmless country like ours :). BAN is directly concerned with making profit, why they spend most of their time studying billing, financial and economic issues of their business.
The beginning of time
I will share with you a practical story about how I conducted an audit of the system for dispatching the management of heat energy consumption for residential buildings. My main task was to detect existing vulnerabilities in the system and make remote access to key elements of the system.
Designating for itself the range of the network, it was decided to identify the border access gateway in it. It did not take long to search, it was the Cisco Router and Security Device Manager on the Cisco 7301 router, popularly known as CISCO SDM. I needed to access it, if possible to study its configuration file, designate for myself the ranges of internal networks and identify the most valuable there.
Oddly enough, there were two vulnerabilities at the gateway itself:
- authorization bypass level 15;
- integrated account "cisco" (the gateway was only put into operation, why the administrators themselves have not yet managed to establish anything with security there).
')
#
show running configAfter examining the subnets, I immediately took up the analysis of the network directly from the border router. Naturally, this procedure could be carried out in two ways:
- actively, using TCL scripts that would run across network nodes and connect to well-known ports to collect information about services;
- passively, everything is a bit more complicated here, because only modern CISCO firmwares contain Cisco IOS Embedded Packet Capture (EPC) - a very useful thing acting as a packet analyzer for network diagnostics.
# EXEC
enable
# «pktrace1», 256 , 100
monitor capture buffer pktrace1 size 256 max-size 100 circular
# , FastEthernet, ,
monitor capture point ip cef ipceffa0/1 fastEthernet-type 0/1 both
#
monitor capture point associate ipceffa0/1 pktrace1
#
monitor capture point start ipceffa0/1
#
show monitor capture buffer pktrace1dumpHaving discovered lines with TCP port 502 in traffic, it became clear to me a lot, because this port is typical for the MODBUS TCP protocol. By packet routing and destination address it was possible to judge where the control center is located. Actually, this way you can conduct a fully-fledged passive network intelligence from the routing equipment, in particular - from any CISCO router that has the current firmware version.
Having launched the scanner, I realized that someone had already been productively there before me: several nodes were infected with a worm, each of which figuratively told me: “We are waiting for our owner”. It should be noted an interesting fact that the default settings of many SCADA systems recommend organizing anonymous access to DCOM Microsoft Windows OS, which creates huge security holes. Also, many of the industrial protocols do not support encryption for a number of reasons (complexity of implementation on telemetry equipment, increased traffic). In the meantime, hashes taken from the SDM configuration were decrypted. This time, as a hashing algorithm, MD5 was used instead of the native CISCO “secret 7”.
How MODBUS Transmits Data
In MODBUS networks, one of two data transfer methods can be used: ASCII or RTU. The user selects the desired mode along with other parameters (transmission rate, parity mode, etc.) during the configuration of each controller. When using the ASCII mode, each byte of the message is transmitted as two ASCII characters. The main advantage of this method is that the time between the preload of characters can be up to a second without any transmission errors. In ASCII mode, the message begins with a colon (:, ASCII 3A hex) and ends with a carriage return-line feed sequence (CRLF, ASCII 0D and 0A hex). Valid characters for transmission are hexadecimal digits 0-9, AF. The network device monitor on the network continuously monitors the colon character. When it is received, each device decodes the following message fields (address field), etc.Passwords on CISCO routers
Sometimes instead of the expected “secret 7” hashes, there are “secret 5” (CISCO type “5” passwords) on the CISCO routers. The process of obtaining a password for a hash is different from the “secret 7” hacking, which can be decrypted using well-known scripts, Cain and Abel, and many other programs. An example of how password hashes look and are stored:username jbash enable secret 5 $1$iUjJ$cDZ03KKGh7mHfX2RSbDqP.
username jbash password 7 07362E590E1B1C041B1E124C0A2F2E206832752E1A01134DIt is easy to see that the hashing algorithm is similar to md5 (unix), so in this case you can resort to using modern software that can recover such types of hashes, namely Passwords Pro, John The Ripper, EGB, and so on, to perform a dictionary attack. Structurally, it looks like this:
$1$FKKk$t2NOQP.vSScMbwJWERNU0/ (type "5"),
«FKKk» - (salt)A self-made brute forcing might look something like this:
openssl passwd -1 -salt FKKk cisco (in the place of “cisco” - moving words from the dictionary with passwords, if the final hash coincides with the original researched one — luck of selection, absence — continuation of the brut).

Dispatch system
Having deciphered the passwords, I began to study the perimeter of the network. Some of the hosts had aliases of external IP addresses, which allowed me to connect to them from the outside. Having gained access to one of the workstations within the network, I began to conduct active reconnaissance of all the devices of the automated process control systems using the SCADA-Auditor software. Any other scanner would show me the available TCP 502 ports that are typical for MODBUS, but I’m not able to establish a native connection and find out the service information from there.
Using the “SCADA-Auditor”, it was required to identify those nodes in the network ranges that contain signs of the placement of dispatch systems or telemetry elements. This can be done on a variety of grounds, if you know what to look for. One of the possible criteria for the search is the output of the SNMP protocol polling if it is available. Also within the network itself, through the administrative panel and the embedded web server, I found the SCADA itself — it was Cascade-ACS. After studying this software package, I identified a number of vulnerabilities:
- Unauthorized reading of the directory with the project process KASKAD / Web_Clnt.dll / ShowPage? Web_Clnt.ini. From it you can find the full path to the base:
Project="C:\Program Files\Kaskad\Projects\KVisionDemoProject\kaskad.kpr" - Disclosure of user information KASKAD / Web_Clnt.dll / ShowPage? ../../../ Projects / KVisionDemoProject / Configurator / Events.ini.
- Reading password and user to the database:
UserName=sysdba
Password= ( XOR' 0x1B) - KASKAD / Web_Clnt.dll / ShowPage service information disclosure? ../../../ Projects / KVisionDemoProject / Configurator / Stations.ini:
ClntIPAdr1=127.0.01
= 3050 - Denial of service by writing through the socket to TCP port 3050 "
\x00\x00\x00\x35\x4a\x4a\x4a\x4a\x4a\x4a\x4a\x4a\x4a\x4a\x4a\x4a\x4a". Vulnerability is characteristic for Firebird DBMS. - Unauthorized addition of a SCADA user:
INSERT INTO USERLIST (USERNAME, USERPASSW, NAME, GRPNAME, FULLNAME, FLAGS, FLAGS_, ALLOWTIME, REGISTERTIME, LASTENTERTIME, LASTPWDCHANGETIME, PWDKEEPPERIOD, STATIONS, DROPTIMEOUT, PSPRDACCESS, PSPWRACCESS, PSPRDACCESS_, PSPWRACCESS_) VALUES ('ITD', '745F87A6B56BACAB', 'itd', '', ', 3, null, null, '2002-01-30 13:11:36.0', '2002-01-30 13:11:36.0', '2002-01-30 13:11:36.0', 0, null, null, null, null, null, null);

In SCADA settings - many options for the development of alarms and alerts
Not MODBUS'om one!
Having discovered the telemetry nodes controlled by MODBUS, I set to work. Having picked up in the protocol, it is possible to reveal many interesting features.
- For example, it is possible to switch PLC devices to “listen only” mode. This mode allows you to disable the PLC from processing and executing commands for a certain period of time, which can lead to a system shutdown as a whole. According to the MODBUS architecture, only one device (Master) can initiate a transfer (make a request). Other devices (Slave) transmit the data requested by the main device or perform the requested actions. A typical host device includes a host (HOST) processor and programming panels. A typical slave device is a programmable controller.
The transfer of PLC devices to the “listen only” mode is implemented by sending special packets either to a specific Slave device, or to all slave devices at once using a broadcast request. Slave device returns a message in response to a request addressed to him. With broadcast requests, no responses are returned. - Another characteristic error, however, in no way related to the implementation of the protocol, is incorrect processing of input data on the side of the device working with the industrial protocol. Developers often forget to control packet size limits, which leads to crash and disrupts the operation of the device. For example, the Modbus SCADAPack driver of the famous ClearSCADA package is capable of processing packets from 60 to 260 bytes. What will happen to the device, if you send him longer packages, you can check it yourself :).
- A similar problem is the design errors of full-time services and services used on controllers, ranging from integrated Web servers, to FTP daemons. Say, the famous Appweb Embedded Web Server crashes using a flood generated by the Apache Benchmarking Tool (ab) utility, for example:
ab -n 1000 -c 50 xxx.xxx.xxx.xxx/index.html
-n –
-c – - I will share with you one sly trick. If you disable one of the MODBUS telemetry controllers, the Administrator will panic and he will definitely climb there to reboot the controller, and then go to the admin panel to see all the settings. This is where you can intercept his password by sniffing traffic on the LAN segment using ARP spoofing.
We have a problem
The trouble with the existing regulatory framework is obvious: there are no clear and explicit requirements for such critical systems as the automated process control system and SCADA in particular. Recently, our experts discovered a typical TZ, which has found its implementation in one of the automated information and measuring systems for commercial metering of electricity (AIIS KUE). Requirements for protection against unauthorized access, according to the RD FSTEC of the Russian Federation, which were taken into account by developers, - 2B. Unfortunately, this class does not take into account many issues, such as signaling attempts to breach security, control subjects' access to programs, network nodes, communication channels, and much more. Problem!

The most interesting incidents
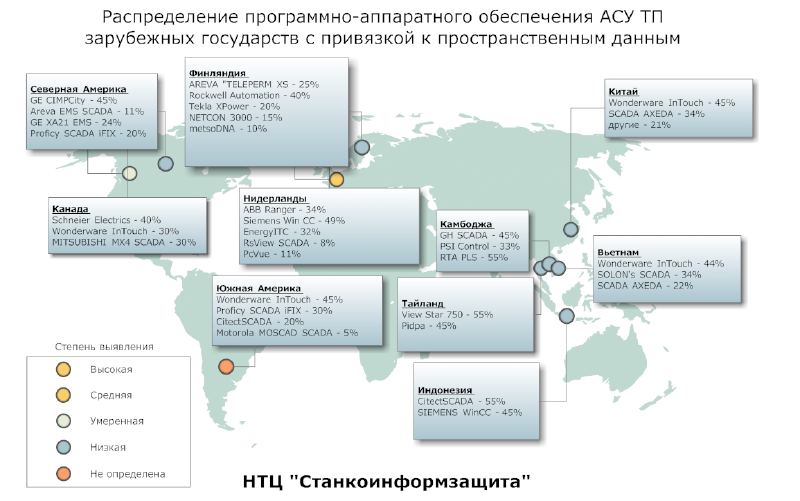
The Russian company STC “Stankoinformzaschita”, which deals with the security of the automated process control system, has published an analytical report analyzing information security incidents of the automated process control system of foreign countries for 2008-2010. The most interesting of them are:On March 7, 2008 , Unit 2 of the Hatch nuclear station (Georgia, USA), a freelance emergency shutdown for 48 hours after installing the software update (a similar incident occurred in 2006 at the Browns Ferry nuclear station due to an irregular failure of the programmable logical controller when receiving abnormal output network traffic from the production network);
May 2008 , the Tennessee Valley Authority Corporation (TVA) (11 coal-fired power plants, 8 thermal power plants, 3 nuclear power plants, 29 US hydropower plants) are in the statement of this energy corporation, the regulators check (GAO, HHS) revealed about 2000 vulnerabilities of varying degrees of criticality. Among the security holes were identified segments of the production network connected to the Internet, multiple application software vulnerabilities, lack of security updates, errors in the design of the network architecture and data exchange channels;
On August 26, 2008 , the Flight Planning Center of the United States Federal Aviation Administration, the dispatching offices of three dozen American airports, were disabled by a computer malfunction at the Flight Planning Center.
Many facts of hacker penetration into such systems remain behind the scenes. What escaped the public, falls into a special base, one of them - RISI .

Hacker Magazine, July (07) 150
Yuri Kaminkov, STC "Stankoinformzashchita"
Subscribe to "Hacker"
Source: https://habr.com/ru/post/123672/
All Articles