Fast flux DNS or new cybercrime technology
One of the most active threats we face today on the Internet is cyber crime. More often criminals are developing more sophisticated means of making a profit from online criminal activity. This article demonstrates the rise in popularity of a complex method called the Fast-Flux Network, which, as we have seen, is becoming more and more widely used in the “wild”. Fast-Flux networks are networks of hacked computer systems with public DNS records that are constantly changing, in some cases every 3 minutes. Constantly changing architecture makes it much more difficult to monitor criminal activity and closed it.
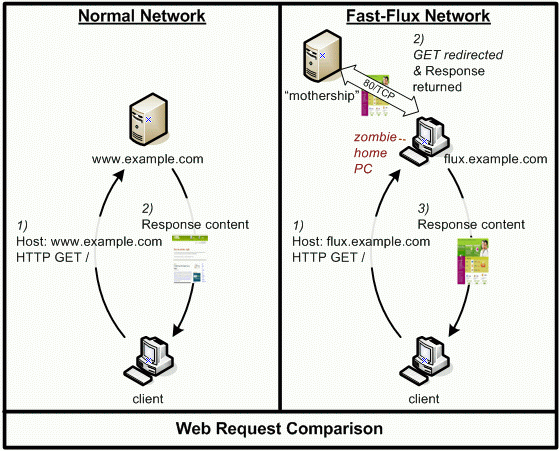
Fast flux DNS is a method that an attacker can use to prevent the identification of the IP address of his computer. By abusing the DNS technology, a criminal can create a botnet with nodes, connect through them and change them faster than law enforcement officers can trace.
Fast flux DNS uses the load balancing method built into the domain name system. DNS allows an administrator to register the nth number of IP addresses with a single host name. Alternate addresses are legally used to distribute Internet traffic across multiple servers. As a rule, the IP addresses associated with the domain host do not change very often, if at all.
However, criminals discovered that they could hide key servers using 1/62 of the lifetime (TTL) of the DNS resource record associated with the IP address and change them extremely quickly. Because abuse of the system requires domain name registrar cooperation, most Fast flux DNS botnets are believed to occur in developing countries or in other countries without laws for cybercrime.
')
According to the Honeypot Project, Fast flux DNS botnets are responsible for many illegal activities, including phishing websites, illegal sale of online medications, extremist or illegal content for adult sites, malicious sites using vulnerabilities browsers and web traps for spreading malicious programs.
Having explained the underlying principles, we will now look at the Fast Flux networks from the point of view of crime and take a look at the basic steps required to install Fast Flux services. First, criminals register a domain for an attack. An example would be a domain with a fake domain name that is similar to the name of a bank, or a website for promoting the sale of pharmaceuticals. In our case, we will use example.com. Based on our research, the .info and .hk domains are among the most commonly used top-level domains (TLD's). This may be due to the fact that brokers for these domain registrars have a weaker control system than other TLDs. Often, these fake domains are registered with fraudulent means, such as using stolen credit cards and forged documents or other means. Criminals often already have a network of hacked systems that can act as redirectors, or they can temporarily rent a botnet. In addition, the cheapest domains are often registered. The criminals then publish the Name Server (NS) records, or point to the abuz sustainable hosting and any of the proxy / redirects flux-agent under their control. Examples of a bulletproof hosting provider may include DNS services from Russia, China and many other countries around the world. If criminals do not have access to this type of service, they create DNS services on their own hacked systems, and often the Mothership sites that host sites. Now we look at the two-part actual deployment.
First we will look at DNS records for single-flux. This is a real example of a money mule scam set. Money mule someone who acts as an intermediary in the transfer or withdrawal of money, often involved in fraud. For example, a criminal will steal money from a bank account, someone will transfer it to a bank account in a money mule, that is, money, a mule will withdraw and transfer it to the criminal’s place, perhaps in another country. The uniqueness of some modern money mule frauds is that the money mule may think that they work for legitimate companies, not realizing they are acting on behalf of criminals in money laundering schemes. Often the money mule is actually just another victim in the chain of other victims.
The following are single-flux DNS records typical of such an infrastructure. The DNS tables of divewithsharks.hk snapshots change approximately every 30 minutes, the five records returned cyclically demonstrate clear penetrations into the home / business networks of dial-up and broadband network access. Note that the NS records are not changed, but some of the A records are different. This is the money mule website:
Single-Flux networks try to apply some form of logic in deciding which of their IP addresses will be advertised in the next set of answers. This can be based on continuous monitoring of the quality of communication and, possibly, a load balancing algorithm. New flux-agent IP addresses are inserted into the fast flow of the service network to replace low-capacity nodes to be mitigated or otherwise communicated by nodes. Now let's take a look at the DNS records of the same domain name after 30 minutes and see what has changed:
As we can see, two of the advertised IP addresses have changed. Again, these two IP addresses belong to the switched or broadband network segment. Another 30 minutes later, the search area, returns the following information:
Now we are seeing four new IP addresses and one IP address that we saw in the first request. This indicates a cyclic response address mechanism used in fast fast-flux networks. As we have seen in this example, the records for the domain are constantly changing. Each of these systems represents a threat, the host acts as a redirector, and the redirector eventually points to the money mule website. The important point here is the fact that analysts are not able to find out the actual address of the site until they have access to one of the redirector nodes, which creates a dynamically changing and therefore strong protective shell for cybercriminals. Next, we consider two-stream fast-flux networks in whose architecture attackers introduce an additional level of protection to strengthen their own security.
- This is only a small part of the description of the capabilities of this technology. If any of you are interested, then add.
Or you can try to comprehend yourself by following the link .
* money mule is essentially a creature known onnot- entirely-illegal forums, like drop, adjustable drop, etc. Those. a person who is used for his unlawful purposes, without his knowledge.
What is fast flux DNS?

Fast flux DNS is a method that an attacker can use to prevent the identification of the IP address of his computer. By abusing the DNS technology, a criminal can create a botnet with nodes, connect through them and change them faster than law enforcement officers can trace.
Fast flux DNS uses the load balancing method built into the domain name system. DNS allows an administrator to register the nth number of IP addresses with a single host name. Alternate addresses are legally used to distribute Internet traffic across multiple servers. As a rule, the IP addresses associated with the domain host do not change very often, if at all.
However, criminals discovered that they could hide key servers using 1/62 of the lifetime (TTL) of the DNS resource record associated with the IP address and change them extremely quickly. Because abuse of the system requires domain name registrar cooperation, most Fast flux DNS botnets are believed to occur in developing countries or in other countries without laws for cybercrime.
')
According to the Honeypot Project, Fast flux DNS botnets are responsible for many illegal activities, including phishing websites, illegal sale of online medications, extremist or illegal content for adult sites, malicious sites using vulnerabilities browsers and web traps for spreading malicious programs.
Real life examples
Having explained the underlying principles, we will now look at the Fast Flux networks from the point of view of crime and take a look at the basic steps required to install Fast Flux services. First, criminals register a domain for an attack. An example would be a domain with a fake domain name that is similar to the name of a bank, or a website for promoting the sale of pharmaceuticals. In our case, we will use example.com. Based on our research, the .info and .hk domains are among the most commonly used top-level domains (TLD's). This may be due to the fact that brokers for these domain registrars have a weaker control system than other TLDs. Often, these fake domains are registered with fraudulent means, such as using stolen credit cards and forged documents or other means. Criminals often already have a network of hacked systems that can act as redirectors, or they can temporarily rent a botnet. In addition, the cheapest domains are often registered. The criminals then publish the Name Server (NS) records, or point to the abuz sustainable hosting and any of the proxy / redirects flux-agent under their control. Examples of a bulletproof hosting provider may include DNS services from Russia, China and many other countries around the world. If criminals do not have access to this type of service, they create DNS services on their own hacked systems, and often the Mothership sites that host sites. Now we look at the two-part actual deployment.
Single-Flux: A Money Mule
First we will look at DNS records for single-flux. This is a real example of a money mule scam set. Money mule someone who acts as an intermediary in the transfer or withdrawal of money, often involved in fraud. For example, a criminal will steal money from a bank account, someone will transfer it to a bank account in a money mule, that is, money, a mule will withdraw and transfer it to the criminal’s place, perhaps in another country. The uniqueness of some modern money mule frauds is that the money mule may think that they work for legitimate companies, not realizing they are acting on behalf of criminals in money laundering schemes. Often the money mule is actually just another victim in the chain of other victims.
The following are single-flux DNS records typical of such an infrastructure. The DNS tables of divewithsharks.hk snapshots change approximately every 30 minutes, the five records returned cyclically demonstrate clear penetrations into the home / business networks of dial-up and broadband network access. Note that the NS records are not changed, but some of the A records are different. This is the money mule website:
;; WHEN: Sat Feb 3 20:08:08 2007
divewithsharks.hk. 1800 IN A 70.68.187.xxx [xxx.vf.shawcable.net]
divewithsharks.hk. 1800 IN A 76.209.81.xxx [SBIS-AS - AT&T Internet Services]
divewithsharks.hk. 1800 IN A 85.207.74.xxx [adsl-ustixxx-74-207-85.bluetone.cz]
divewithsharks.hk. 1800 IN A 90.144.43.xxx [d90-144-43-xxx.cust.tele2.fr]
divewithsharks.hk. 1800 IN A 142.165.41.xxx [142-165-41-xxx.msjw.hsdb.sasknet.sk.ca]
divewithsharks.hk. 1800 IN NS ns1.world-wr.com.
divewithsharks.hk. 1800 IN NS ns2.world-wr.com.
ns1.world-wr.com. 87169 IN A 66.232.119.212 [HVC-AS - HIVELOCITY VENTURES CORP]
ns2.world-wr.com. 87177 IN A 209.88.199.xxx [vpdn-dsl209-88-199-xxx.alami.net]
Single-Flux networks try to apply some form of logic in deciding which of their IP addresses will be advertised in the next set of answers. This can be based on continuous monitoring of the quality of communication and, possibly, a load balancing algorithm. New flux-agent IP addresses are inserted into the fast flow of the service network to replace low-capacity nodes to be mitigated or otherwise communicated by nodes. Now let's take a look at the DNS records of the same domain name after 30 minutes and see what has changed:
;; WHEN: Sat Feb 3 20:40:04 2007 (~30 minutes/1800 seconds later)
divewithsharks.hk. 1800 IN A 24.85.102.xxx [xxx.vs.shawcable.net] NEW
divewithsharks.hk. 1800 IN A 69.47.177.xxx [d47-69-xxx-177.try.wideopenwest.com] NEW
divewithsharks.hk. 1800 IN A 70.68.187.xxx [xxx.vf.shawcable.net]
divewithsharks.hk. 1800 IN A 90.144.43.xxx [d90-144-43-xxx.cust.tele2.fr]
divewithsharks.hk. 1800 IN A 142.165.41.xxx [142-165-41-xxx.msjw.hsdb.sasknet.sk.ca]
divewithsharks.hk. 1800 IN NS ns1.world-wr.com.
divewithsharks.hk. 1800 IN NS ns2.world-wr.com.
ns1.world-wr.com. 85248 IN A 66.232.119.xxx [HVC-AS - HIVELOCITY VENTURES CORP]
ns2.world-wr.com. 82991 IN A 209.88.199.xxx [vpdn-dsl209-88-199-xxx.alami.net]
As we can see, two of the advertised IP addresses have changed. Again, these two IP addresses belong to the switched or broadband network segment. Another 30 minutes later, the search area, returns the following information:
;; WHEN: Sat Feb 3 21:10:07 2007 (~30 minutes/1800 seconds later)
divewithsharks.hk. 1238 IN A 68.150.25.xxx [xxx.ed.shawcable.net] NEW
divewithsharks.hk. 1238 IN A 76.209.81.xxx [SBIS-AS - AT&T Internet Services] This one came back!
divewithsharks.hk. 1238 IN A 172.189.83.xxx [xxx.ipt.aol.com] NEW
divewithsharks.hk. 1238 IN A 200.115.195.xxx [pcxxx.telecentro.com.ar] NEW
divewithsharks.hk. 1238 IN A 213.85.179.xxx [CNT Autonomous System] NEW
divewithsharks.hk. 1238 IN NS ns1.world-wr.com.
divewithsharks.hk. 1238 IN NS ns2.world-wr.com.
ns1.world-wr.com. 83446 IN A 66.232.119.xxx [HVC-AS - HIVELOCITY VENTURES CORP]
ns2.world-wr.com. 81189 IN A 209.88.199.xxx [vpdn-dsl209-88-199-xxx.alami.net]
Now we are seeing four new IP addresses and one IP address that we saw in the first request. This indicates a cyclic response address mechanism used in fast fast-flux networks. As we have seen in this example, the records for the domain are constantly changing. Each of these systems represents a threat, the host acts as a redirector, and the redirector eventually points to the money mule website. The important point here is the fact that analysts are not able to find out the actual address of the site until they have access to one of the redirector nodes, which creates a dynamically changing and therefore strong protective shell for cybercriminals. Next, we consider two-stream fast-flux networks in whose architecture attackers introduce an additional level of protection to strengthen their own security.
- This is only a small part of the description of the capabilities of this technology. If any of you are interested, then add.
Or you can try to comprehend yourself by following the link .
* money mule is essentially a creature known on
Source: https://habr.com/ru/post/123350/
All Articles