Trojan using the computing power of a PC to generate bitcoin
It happened to me yesterday to bring one trojan from a business trip, Trojan.Win32.Powp.rdf (according to the classification of LC). There I defeated him, but he managed to impress me with flash drives. So that the good did not do anything, I decided to pick it up at leisure.
As always, the name of the malware in LK turned out not to be all right, it belongs more to the Trojan-Downloader class, since The main task is to download files from fileave.com . I put on a virtual player to play, among a heap of mediocre junk downloaded by them onto the machine, I noticed one sfx-archive and as it turned out not in vain ...
The link http_: //pasic.fileave.com/BTxDEF.exe downloads a self-extracting archive.

We look, what is inside ...
')

And inside we have the Hidden Start 3.2 program (hstart.exe), which is launched by the archive script, with the

We look that we have in a batch file ...

So far, nothing is clear, although btc.mobinil.biz already suggests some thoughts. The last file remains - taskmgr.exe, which, apparently, strenuously mows under the Windows Task Manager.
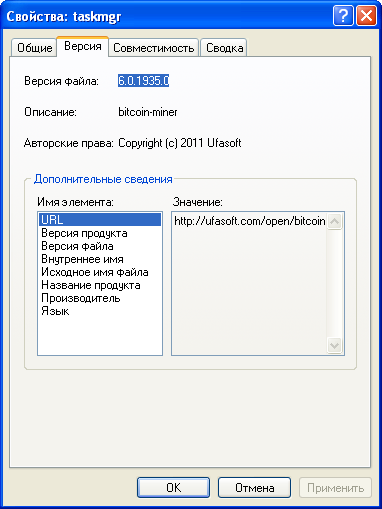
Opanki! The file is BitCoin Miner 'ohm, designed to generate Bitcoins. The batch file starts it with parameters:
Where
So, the timeout is 5 seconds, url - btc.mobinil.biz : 8332 /, user - redem_guild, pass - redem, 2 threads.
With the Internet, BitCoin Miner begins to work hard for the benefit of the unknown ...

And so, now the computing power of computers began to bring in income to cybercriminals. The user pays not only for botnet traffic, for example, but also for electricity, and his uncle is dripping money at the other end of the world :)
The most interesting thing is that both programs from the archive are legitimate, and a trojan can only be considered a batch file that runs the whole farm ... KIS 2011 will detect the entire archive, using KSN, without a name.
Now it is disguised as svchost.exe. Some antiviruses began to detect a batch file inside the archive as malicious.
As always, the name of the malware in LK turned out not to be all right, it belongs more to the Trojan-Downloader class, since The main task is to download files from fileave.com . I put on a virtual player to play, among a heap of mediocre junk downloaded by them onto the machine, I noticed one sfx-archive and as it turned out not in vain ...
The link http_: //pasic.fileave.com/BTxDEF.exe downloads a self-extracting archive.

We look, what is inside ...
')

And inside we have the Hidden Start 3.2 program (hstart.exe), which is launched by the archive script, with the
/NOCONSOLE test.bat , which allows you to silently execute test.bat.
We look that we have in a batch file ...

So far, nothing is clear, although btc.mobinil.biz already suggests some thoughts. The last file remains - taskmgr.exe, which, apparently, strenuously mows under the Windows Task Manager.

Opanki! The file is BitCoin Miner 'ohm, designed to generate Bitcoins. The batch file starts it with parameters:
bitcoin-miner [-a seconds] [-g|l yes|no] [-t threads] [-v] [-o url] [-x proxy] -u user -p password ,Where
-a #seconds# time between getwork requests 1..60, default 15
-g yes|no set 'no' to disable GPU, default 'yes'
-h this help -l yes|no set 'no' to disable Long-Polling, default 'yes'
-t #threads# Number of threads for CPU mining, by default is number of CPUs (Cores), 0 - disable CPU mining
-v Verbose output
-o url in form server.tld:port/path, by default 127.0.0.1:8332
-x type=host:port Use HTTP or SOCKS proxy.
Thread number should be 0..32So, the timeout is 5 seconds, url - btc.mobinil.biz : 8332 /, user - redem_guild, pass - redem, 2 threads.
With the Internet, BitCoin Miner begins to work hard for the benefit of the unknown ...

And so, now the computing power of computers began to bring in income to cybercriminals. The user pays not only for botnet traffic, for example, but also for electricity, and his uncle is dripping money at the other end of the world :)
PS
The most interesting thing is that both programs from the archive are legitimate, and a trojan can only be considered a batch file that runs the whole farm ... KIS 2011 will detect the entire archive, using KSN, without a name.
Upd
Now it is disguised as svchost.exe. Some antiviruses began to detect a batch file inside the archive as malicious.
Source: https://habr.com/ru/post/123244/
All Articles