The game "Terraria" and its "good" profile encryption system
One day I was sitting and preparing for the upcoming exam. But the band mate wanted me to throw him down. Knowing that I was "avid" for games in the style of Minecraft, he threw me the game Terraria. Initially, interest in it went off scale, but a little later, because of the “wretchedness” in my opinion of a single game, it fell, and I decided to play multiplayer, where an interesting feature was discovered: inventory even on different servers in multiplayer. This led me to the idea to collect in the inventory of more "cool" things. How this was achieved - under the cut.
First, the user data file was fed to WinHex and the following result was obtained from it:
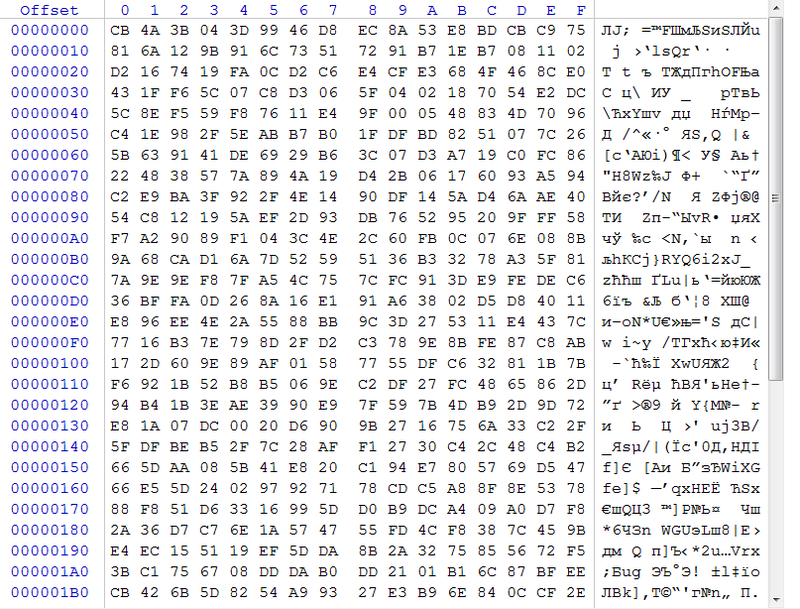
From here, there is no easy way to decrypt this file.
Therefore, ProcessMonitor from SYSInternals was involved. He showed that the bcrypt.dll library is used to encrypt the user file. After reading about this library and the algorithm that it uses, it became clear that without the key I could not decrypt the file. Therefore, it was decided to disassemble the file Terraria.exe. Well, I think at least the assembler code more or less sheds light on it. I wanted to take IDA Pro Advanced 6.1 and wield them, but they stopped me in time and poked my nose at the fact that the game itself was written on .Net, which allows us to get a better program code. All the same, CIL is easier to parse than assembler code.
Therefore, looking for guidance for this action, I read this article from avaver . Fortunately, Visual Studio 2010 was installed on the computer, where the necessary ilasm.exe and ildasm.exe were,
I follow this article, drove into the command line (open through the item in the Start menu from the MS Visual Studio group) this:
')
Having received a fairly clear CIL code, I found the methods Player :: EncryptFile and Player :: DecryptFile. Their research and the context of their use showed how the process of loading / saving user data goes.
Reading data when loading occurs according to the following algorithm:
The procedure for writing data is similar in the reverse order:
Looking at such an algorithm, it becomes clear that all the “snacks” are contained in the file player1.plr.dat. But, unfortunately, all actions with him occur so quickly that you do not even have time to notice him in the "Explorer". And then in the source code was found a function that deletes the file. Commenting out this function and rebuilding the file, the goal was achieved.
By the way, to rebuild the file, the following command was entered into the console that was still running:
Well, after starting the game, the file player1.plr.dat is finally in my hands.
As expected, it has all the sweets:
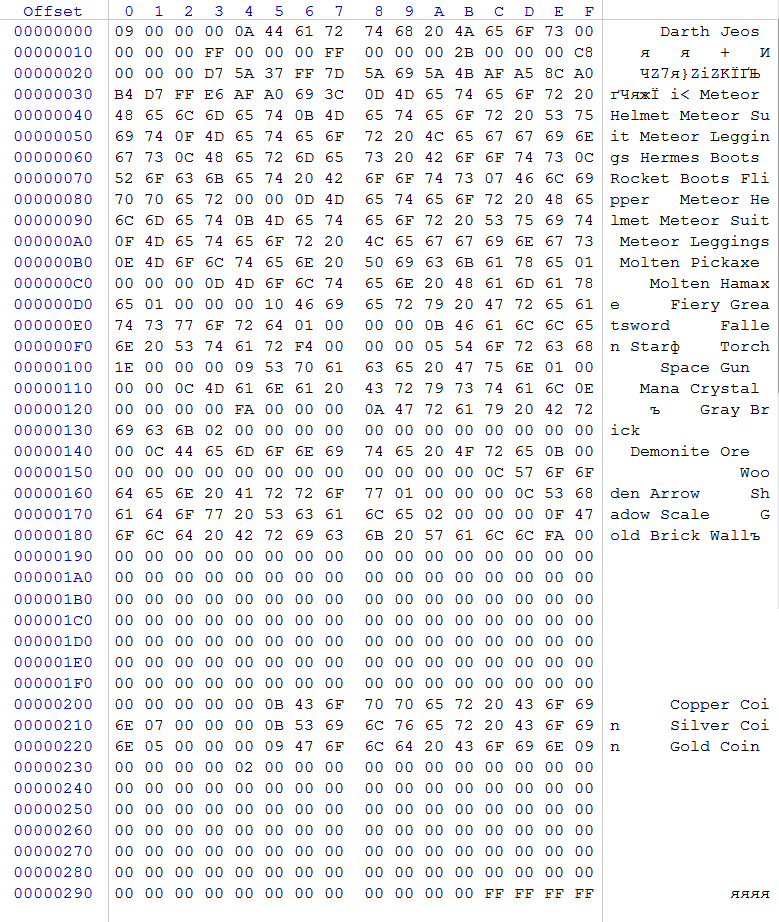
Well, we got the file, and now we’ll try to figure it out.
I understood far from there, but what I understood is:
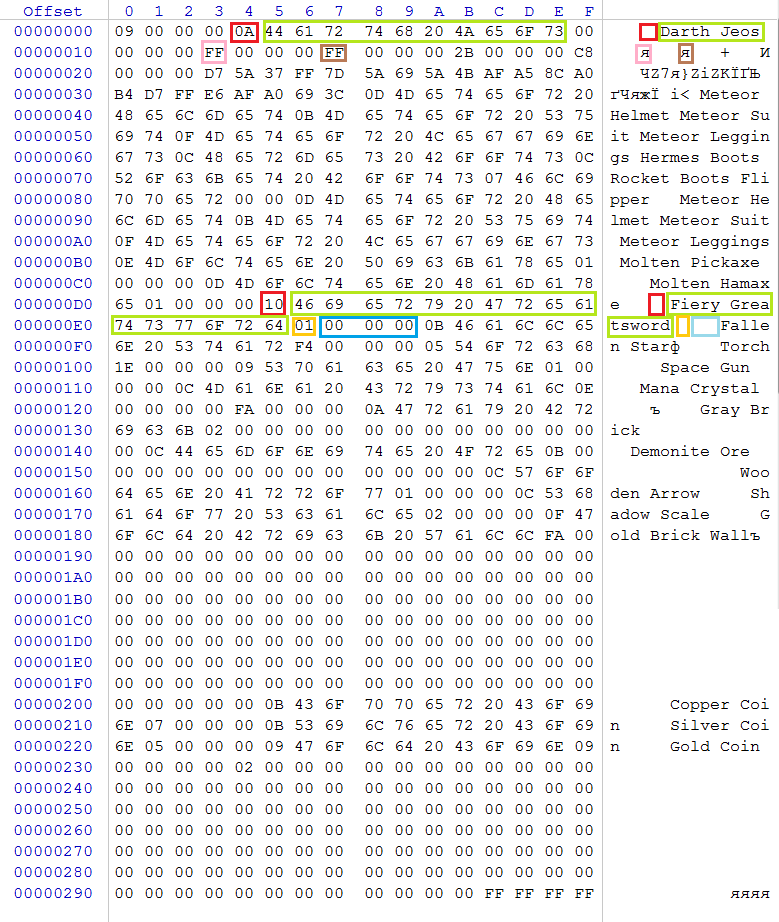
Since this is a user file, it contains data about the user: first, the length of the nickname (red), then the nickname itself (green). Next comes the character's “health” at the time of leaving the game (pink) and generally the maximum health value (brown).
After that, there is information about the "equipment" of the character, his "accessories" and the very contents of the inventory, which is described as follows:
If there are several (n) free cells in the inventory, then n * 5 zero bytes are inserted (this is the name length equal to zero + the number of items, also 0 + indent 3 zero bytes).
But we need not only to “read” the file, but also to apply it for our own purposes. For this, the procedure call that decrypts the original player1.plr file and overwrites player1.plr.dat was simply commented out. Thus, the read is always from the file player1.plr.dat and it is not deleted. Therefore, we can make changes to it without worrying about the original player1.plr - it will not spoil the picture for us.
As you can see from my screenshots, I have done some “cool things” to myself and played with them in multiplayer. But it quickly got bored, and the interest in the game dried up completely. Preparation for the exam continues!
First attempts
First, the user data file was fed to WinHex and the following result was obtained from it:

From here, there is no easy way to decrypt this file.
Therefore, ProcessMonitor from SYSInternals was involved. He showed that the bcrypt.dll library is used to encrypt the user file. After reading about this library and the algorithm that it uses, it became clear that without the key I could not decrypt the file. Therefore, it was decided to disassemble the file Terraria.exe. Well, I think at least the assembler code more or less sheds light on it. I wanted to take IDA Pro Advanced 6.1 and wield them, but they stopped me in time and poked my nose at the fact that the game itself was written on .Net, which allows us to get a better program code. All the same, CIL is easier to parse than assembler code.
Therefore, looking for guidance for this action, I read this article from avaver . Fortunately, Visual Studio 2010 was installed on the computer, where the necessary ilasm.exe and ildasm.exe were,
I follow this article, drove into the command line (open through the item in the Start menu from the MS Visual Studio group) this:
')
ildasm.exe Terraria.exe /source /out:Terraria.ilHaving received a fairly clear CIL code, I found the methods Player :: EncryptFile and Player :: DecryptFile. Their research and the context of their use showed how the process of loading / saving user data goes.
Reading data when loading occurs according to the following algorithm:
- First, the file player1.plr is decoded into player1.plr.dat
- Then the data from player1.plr.dat is read and written to the RAM (file size <1KB)
- After these actions, the file player1.plr.dat is deleted.
The procedure for writing data is similar in the reverse order:
- Writing data from RAM to player1.plr.dat
- Encrypting player1.plr.dat to player1.plr
- Uninstall player1.plr.dat
Looking at such an algorithm, it becomes clear that all the “snacks” are contained in the file player1.plr.dat. But, unfortunately, all actions with him occur so quickly that you do not even have time to notice him in the "Explorer". And then in the source code was found a function that deletes the file. Commenting out this function and rebuilding the file, the goal was achieved.
By the way, to rebuild the file, the following command was entered into the console that was still running:
ilasm.exe Terraria.il /exe /out:Terraria.exeWell, after starting the game, the file player1.plr.dat is finally in my hands.
As expected, it has all the sweets:

Use for their own purposes
Well, we got the file, and now we’ll try to figure it out.
I understood far from there, but what I understood is:

Since this is a user file, it contains data about the user: first, the length of the nickname (red), then the nickname itself (green). Next comes the character's “health” at the time of leaving the game (pink) and generally the maximum health value (brown).
After that, there is information about the "equipment" of the character, his "accessories" and the very contents of the inventory, which is described as follows:
- First the length in bytes of the item name (red)
- Then the name itself (in green). By the way, this name can be simply copied from the official wiki
- After that, the number of units of this item (orange)
- And at the end of the indent 3 null bytes to the next item of the inventory (blue)
If there are several (n) free cells in the inventory, then n * 5 zero bytes are inserted (this is the name length equal to zero + the number of items, also 0 + indent 3 zero bytes).
But we need not only to “read” the file, but also to apply it for our own purposes. For this, the procedure call that decrypts the original player1.plr file and overwrites player1.plr.dat was simply commented out. Thus, the read is always from the file player1.plr.dat and it is not deleted. Therefore, we can make changes to it without worrying about the original player1.plr - it will not spoil the picture for us.
Conclusion
As you can see from my screenshots, I have done some “cool things” to myself and played with them in multiplayer. But it quickly got bored, and the interest in the game dried up completely. Preparation for the exam continues!
Source: https://habr.com/ru/post/122839/
All Articles