OAuth VKontakte: mercenary use

There are many ways to spread malicious spam in VKontakte. But the pests are not asleep, more and more interesting ideas are coming to their heads. And support for the OAuth 2.0 Vkontakte platform was somehow the way. Scammers have learned to use it to crawl the warning page about malicious sites.
And it all started with the fact that once a message appeared on my wall:

Out of curiosity, I clicked the link and got to the next phishing site. But the link itself seemed strange to me; it looked like (half of the characters in ASCII):
vkontakte.ru/away.php ? to = http% 3A% 2F% 2FApi.vKontakte.Ru% 2F% 2Fo% 2561u% 2574% ...
Consider the link in detail:
- vkontakte.ru/away.php - a page with a warning about clicking on a link;
- The parameter to the link itself. In recoded form, it looked like this:
Api.vKontakte.Ru/oauth/authorize?client_id=2376***&cgpopcvkqdjut4&redirect_uri=vgostivk.dyndns**&display=popup?390852
This is where the most interesting begins ...
Let's sort the second link in parts:
- Api.vKontakte.Ru/oauth/authorize - access to the VK API, authorization through OAuth 2.0;
- client_id = 2376 *** & cgpopcvkqdjut4 & redirect_uri = vgostivk.dyndns ** & display = popup? 390852 - authorization parameters.
What does each of the parameters mean:
- client_id - ID of the application that requires authorization;
- redirect_uri - the address to which the access_token will be transmitted (via redirect);
- display - view authorization window (page, popup, touch and wap).
Actually redirect_uri contained the address of the phishing site. Since an error was made in the display parameter (garbage "? 390852" was sent to it), the authorization window was not displayed, but a redirect was immediately redirected to the phishing site with parameters: error = invalid_request & error_description = Invalid + display + passed
This is the whole point of bypassing the blacklist of malicious sites on VKontakte. Only an alert about switching to api.vk.com appears. And as a result of the transition, we directly go to the phishing site that is on the black list. When you click on the link vkontakte.ru/away.php?to=vgostivk.dyndns**:

')
As it turned out, the application allegedly requiring authorization hung on a hacked user:

Yes, and the phishing site was arranged quite interesting. Design according to the custom was contact and offered to log in. I passed authorization through random mail and password, fake perfectly swallowed. Then it was even more interesting, on the main there was news from "Pavel Durov":
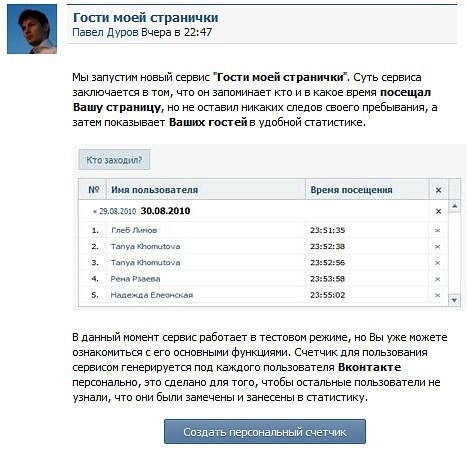
After clicking on the button "Create a personal counter," followed by a wonderful progress bar. Then it was proposed to indicate your number and send sms:
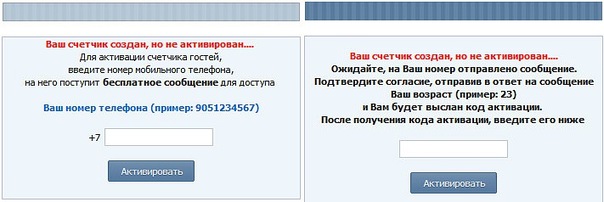
In theory, after a successful "activation" was supposed to be transferred to the activ.php page, but I could not get there. Excerpts from JS scripts phishing site:
...
if (req.status == 200) {
// 200 () -
if (req.responseText == 'ok' ) {
//statusElem.innerHTML = ' !';
get_activation();
}
if (req.responseText == 'not' ) {statusElem.innerHTML = " " ;}
//statusElem.innerHTML = " : "+req.responseText;
...
function get_activation() {
document .location= "activ.php" ;
}
* This source code was highlighted with Source Code Highlighter .Bottom line : Fraudsters use warning bypass through OAuth 2.0, get a password and user email, and even try to send SMS messages (most likely using a subscription system).
Source: https://habr.com/ru/post/122834/
All Articles