Password Recovery on Cisco Routers
Almost any Cisco start-uper sooner or later finds himself in a situation where he has a router with a completely forgotten or unknown, alien password. Personally, I, being a teacher of Cisco courses, meet this situation very often after laboratory work. Pupils build topology, set up access passwords, play with the grid and ... forget to erase the configuration file before leaving. Of course, before the next lab, everyone successfully forgot their passwords. For some strange reason, Cisco does not pay enough attention to this topic in its educational material, and the documentation on the off-site often scares newbies. I would like to eliminate this deficiency today.
If you have reached at least the level of CCENT, you should be aware of such a thing as configuration register. This is a 16-bit register located in NVRAM that is responsible for the boot sequence of the router. Namely - from where and in what order the router will load its operating system and settings file. Its default value is 2102. Its third digit is responsible for the settings file, the fourth for the OS. Our goal is to force the router to ignore the settings file at boot (it is in it that the passwords are located) and to open access to privileged mode for us. We achieve this by changing the third number of the register to "4".
That's all. The whole process takes about 5 minutes.
At first glance, the way it is. But note that you can get into Rommon only through the console and in the recovery process we needed to reboot the router “iron”, which means that the attacker must have physical access to the equipment in order to use this “hole”. And even if it happened, then the hacked password on the tsiska is at least not your only problem.
But if this did not convince you, there is a way to close the possibility of password recovery in this way. This is the no service password-recovery command. It will close the opportunity to change the register to 2142. But note that if you lose the password now, to return the router from the dead you will need very massive dances with a tambourine.
Hope that was helpful.
See you on the pages of Habr!
Introduction
If you have reached at least the level of CCENT, you should be aware of such a thing as configuration register. This is a 16-bit register located in NVRAM that is responsible for the boot sequence of the router. Namely - from where and in what order the router will load its operating system and settings file. Its default value is 2102. Its third digit is responsible for the settings file, the fourth for the OS. Our goal is to force the router to ignore the settings file at boot (it is in it that the passwords are located) and to open access to privileged mode for us. We achieve this by changing the third number of the register to "4".
Algorithm
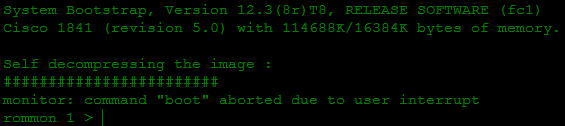
- Reboot the router, wait for the line "Self decompressing the image: ###" and press Ctrl-C or Ctrl-Break. By this we have suspended the loading of the router and are now in ROM Monitor (rommon) mode:
')
- Change the register value to 2142 with the command confreg 0x2142 (do not forget that the number is a hexadecimal number) and reboot again:
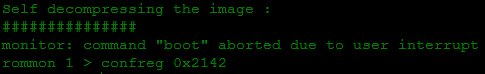
- After the reboot, we end up in setup mode (which means that the router did not load the settings file, which we were trying to achieve). Exit this mode and go to privileged mode:
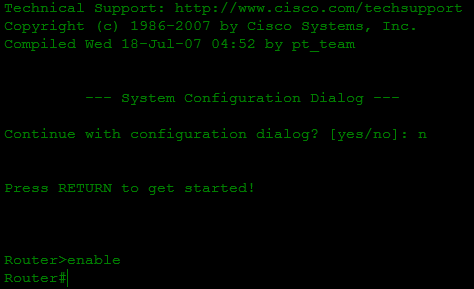
- Now we have full access to the settings of the router. If you care about your settings (which are still stored in the startup-config), it's time to restore them with the copy start run command. All passwords are now in force, but since we are already “inside”, we have the right to configure, this password will no longer be asked:
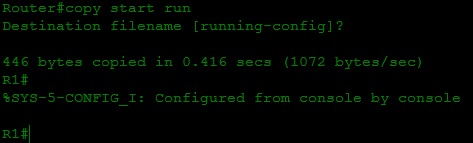
- We change all passwords we are interested in to new ones and save our settings in NVRAM:
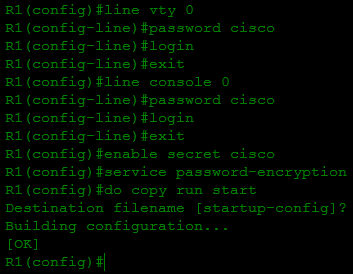
- Change the register to its previous value with the command config-register 0x2102 and reboot to check for new passwords:
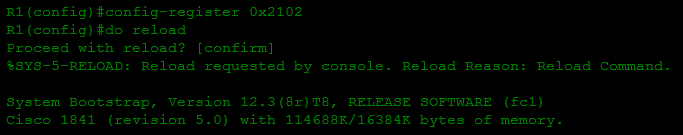
That's all. The whole process takes about 5 minutes.
"But this is a hole!"
At first glance, the way it is. But note that you can get into Rommon only through the console and in the recovery process we needed to reboot the router “iron”, which means that the attacker must have physical access to the equipment in order to use this “hole”. And even if it happened, then the hacked password on the tsiska is at least not your only problem.
But if this did not convince you, there is a way to close the possibility of password recovery in this way. This is the no service password-recovery command. It will close the opportunity to change the register to 2142. But note that if you lose the password now, to return the router from the dead you will need very massive dances with a tambourine.
Hope that was helpful.
See you on the pages of Habr!
Source: https://habr.com/ru/post/122348/
All Articles