Hide 1C for the fireproof wall
 Many system administrators, thinking about the security of their company's data and, in particular, about the security of the 1C database, neglect a simple but effective solution - isolate the server from users. This article analyzes security threats arising when placing the client part of 1C and 1C servers in one network segment, and discusses the process of transferring the server part of 1C to another network segment. This article does not contain fundamentally new solutions, but can serve as a reference tool that combines information from various sources.
Many system administrators, thinking about the security of their company's data and, in particular, about the security of the 1C database, neglect a simple but effective solution - isolate the server from users. This article analyzes security threats arising when placing the client part of 1C and 1C servers in one network segment, and discusses the process of transferring the server part of 1C to another network segment. This article does not contain fundamentally new solutions, but can serve as a reference tool that combines information from various sources.Initial data
- 1C Enterprise 8 client-server version;
- 1C Enterprise server deployed on the basis of the operating system Windows Server 2003;
- 1C Enterprise uses a dedicated MS SQL server deployed based on the Windows Server 2003 operating system;
- user access to 1C through terminal servers deployed based on Windows Server 2003;
- all servers are located in a segment of a single network deployed based on an Active Directory domain.
Security threats
To identify security threats, we draw up a traffic flow pattern in the existing network.
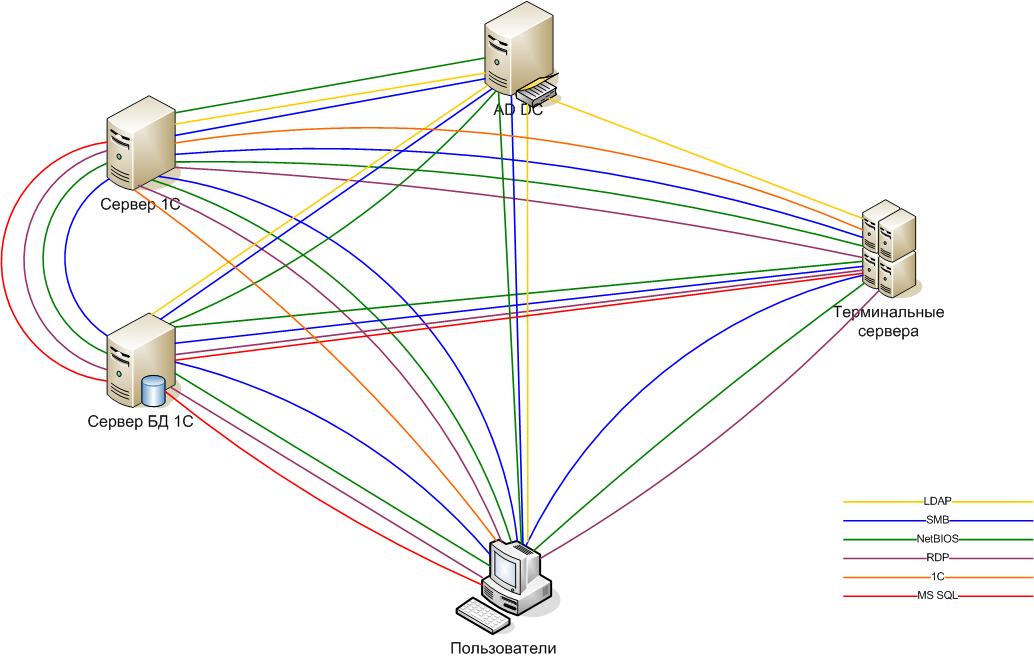
Figure 1. Initial traffic flows
Notes to illustration
- By "LDAP" is meant not one port, but a collection. Ports and protocols used in Active Directory are described in the Microsoft Knowledge Base article Services and Network Ports in Microsoft Windows Server Systems. Depending on what the terminal server requires from the domain controller, these may be different sets. In this article I will use the following set of ports and protocols:
Port Protocol Purpose 88 UDP Kerberos. This port listens on the lsass.exe process (Local Security Authority Service). 135 Tcp RPC 139 Tcp NetBIOS Session Service 389 TCP / UDP Domain Controller Locator 445 Tcp SMB 1025 Tcp Used by the lsass.exe process. More information here . - ICMP ICMP is used to obtain various information, so packets of this protocol must freely pass in the direction of the domain controllers.
This list is enough to log in to the domain and run netlogon scripts. - By "SMB" is meant a set of ports through which the file exchange via the SMB protocol is implemented. This set of ports is a subset of the “LDAP” set and is shown in places for clarity.
- By “RDP” is meant connection via RDP protocol. Ports 3389: 3390 are used for this (why two are described below).
- By "1C" refers to the ports necessary for the 1C client to work with the server. These are ports 1541, 1560: 1591 (Information about ports is obtained from “1C: Enterprise 8.2 - Client-server version of the Administrator's Guide”).
- By “MS SQL” is meant the port for working with MS SQL Server (by default, port 1433).
What we have:
- Windows Server 2003 operating system has vulnerabilities that are not related to 1C and MS SQL, but attacks using these vulnerabilities can help to gain control over the data of the listed applications;
- users can transfer files from a remote session to computers on the network via SMB protocol;
- various network viruses also pose security risks;
- since users are in the same network segment with servers, especially smart ones can try to connect to them via MS SQL and 1C ports.
Tasks
- Minimize the risks of implementation of operating system vulnerabilities.
- Make it impossible to transfer files using SMB protocol from terminal servers to users' computers.
- Exclude the possibility of user access to the servers 1C and MS SQL.
- Minimize the number of users who can transfer files to their computers using the RDP protocol.
Requirements for implementation
Provide simplicity and ease of use of 1C Enterprise resources.
')
Decision
Let's make the scheme of movement of necessary traffic flows.
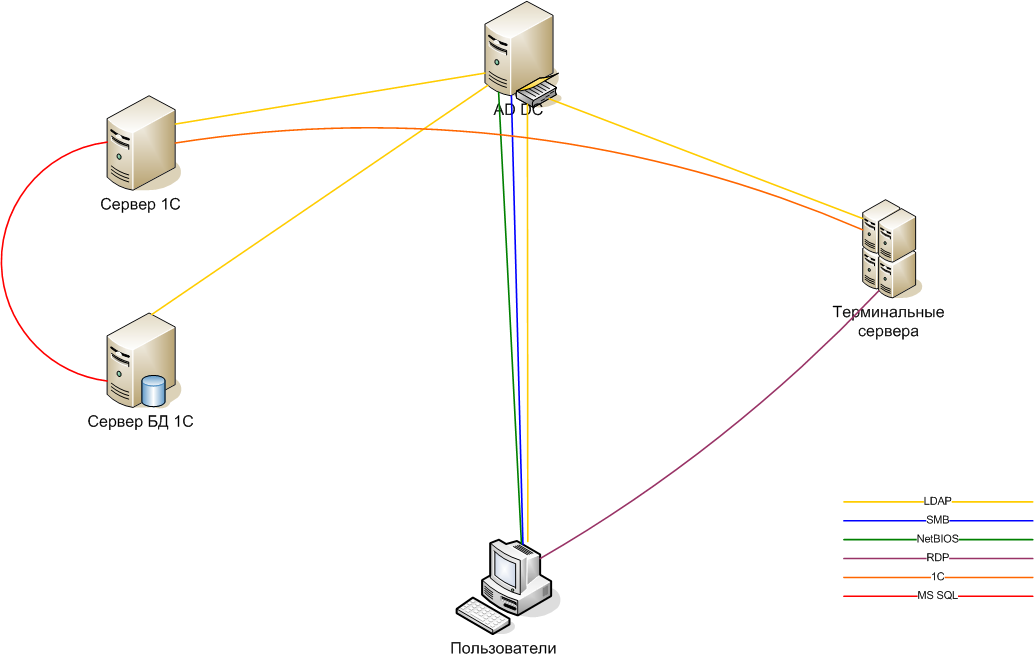
Figure 2. Required traffic flows
As you can see, for the full functioning of 1C you need not so much.
| Computer | Outgoing connections | Inbound connections |
| AD DC | Not required | All network computers |
| 1C server | Database Server 1C | Terminal servers |
| Database Server 1C | Not required | 1C server |
| Terminal servers | 1C server | Users |
The table shows that the network can be divided into three segments:
- "Server 1C" + "Database Server 1C";
- "Terminal Servers";
- "Users" + "AD DC".
Next, I will use the terminology from the Information Technology Security Guideline. Network Security Zoning :
Operation Zone (OZ) is a standard environment for everyday operations, in which most user systems and servers are located. Confidential information can be processed here, but it is not suitable for storing large amounts of confidential information or for critical applications.
Restricted Zone (RZ) - provides a controlled network environment for critical services or for large amounts of confidential information.
To perform tasks 1-3, we divide the network into several zones:
- RZ1C - this zone will include “1C Server” and “DB 1C Server”.
- RZTS - this zone will include terminal servers.
- OZ - the AD DC domain controller and users will enter this zone.
Traffic will be regulated by a router, in which we will enter the necessary rules.

Figure 3. Network zoning scheme
To solve problem 4, do the following:
- we will create a new connection on each terminal server in addition to the standard one, it will function on port 3390;
- let's allow all users to connect to port 3389 and only TerminalDisk users to port 3390;
- in the properties of connections on terminal servers, disable the ability for clients to mount local disks on port 3389 and allow local disks on port 3390.
In this way, we can only allow local users to mount local disks.
Implementation
Routing
As a router in this article, I will use a computer with three network cards with the operating system of the GNU / Linux family. Routing software - iptables. The iptables configuration script is shown below.
#!/bin/sh echo 1 > /proc/sys/net/ipv4/ip_forward OZ=192.168.0.0/24 RZTS=192.168.2.0/24 RZ1C=192.168.1.0/24 ADDC=192.168.0.1 # iptables –F iptables –X iptables –-flush # iptables –P INPUT DROP iptables –P OUTPUT DROP iptables –P FORWARD DROP # ESTABLISHED RELATED TCP UDP iptables –A FORWARD –p tcp –m state --state ESTABLISHED,RELATED –j ACCEPT iptables –A FORWARD –p udp –m state --state ESTABLISHED,RELATED –j ACCEPT # RDP OZ->RZTS iptables –A FORWARD --src $OZ --dst $RZTS –p tcp --dport 3389:3390 –j ACCEPT # DNS- RZTS->ADDC, RZ1C->ADDC iptables -A FORWARD –-src $RZTS --dst $ADDC -p udp --dport 53 -j ACCEPT iptables –A FORWARD --src $RZ1C –-dst $ADDC –p udp --dport 53 –j ACCEPT # Active Directory iptables –A FORWARD --src $RZTS --dst $ADDC –p udp --dport 88 –j ACCEPT iptables –A FORWARD --src $RZ1C --dst $ADDC –p udp --dport 88 –j ACCEPT iptables –A FORWARD --src $RZTS --dst $ADDC –p tcp --dport 135 –j ACCEPT iptables –A FORWARD --src $RZ1C --dst $ADDC –p tcp --dport 135 –j ACCEPT iptables –A FORWARD --src $RZTS --dst $ADDC –p tcp --dport 139 –j ACCEPT iptables –A FORWARD --src $RZ1C --dst $ADDC –p tcp --dport 139 –j ACCEPT iptables –A FORWARD --src $RZTS --dst $ADDC –p tcp --dport 389 –j ACCEPT iptables –A FORWARD --src $RZ1C --dst $ADDC –p tcp --dport 389 –j ACCEPT iptables –A FORWARD --src $RZTS --dst $ADDC –p udp --dport 389 –j ACCEPT iptables –A FORWARD --src $RZ1C --dst $ADDC –p udp --dport 389 –j ACCEPT iptables –A FORWARD --src $RZTS --dst $ADDC –p tcp --dport 445 –j ACCEPT iptables –A FORWARD --src $RZ1C --dst $ADDC –p tcp --dport 445 –j ACCEPT iptables –A FORWARD --src $RZTS --dst $ADDC –p tcp --dport 1025 –j ACCEPT iptables –A FORWARD --src $RZ1C --dst $ADDC –p tcp --dport 1025 –j ACCEPT # 1 iptables –A FORWARD --src $RZTS --dst $RZ1C –p tcp --dport 1541 –j ACCEPT iptables –A FORWARD --src $RZTS --dst $RZ1C –p tcp --dport 1560:1591 –j ACCEPT # , iptables –A FORWARD --src $RZTS --dst $ADDC –p icmp –j ACCEPT iptables –A FORWARD --src $RZ1C --dst $ADDC –p icmp –j ACCEPT iptables –A FORWARD --src $OZ --dst $ADDC –p icmp –j ACCEPT # REJECT iptables –A FORWARD –j REJECT # REJECT iptables –A INPUT –j REJECT Script Notes
The DROP action simply “drops” the packet and iptables “forgets” about its existence. “Discarded” packages stop their movement completely, i.e. they are not transferred to other tables, as is the case with the ACCEPT action. It should be remembered that this action can have negative consequences, since it can leave unclosed "dead" sockets both on the server side and on the client side, the best method of protection would be to use the REJECT action especially when protecting against port scans ( Iptables Tutorial ).
If the HASP keys are not installed on the terminal server and the license manager is located on another network, you need to perform several actions.
- Allow UDP and TCP packets to pass through the router on port 475 in the two-way direction License_server <-> Client_1C.
iptables –A FORWARD --src _ --dst _ –p udp --dport 475 –j ACCEPT
iptables –A FORWARD --src _ --dst _ –p tcp --dport 475 –j ACCEPT
iptables –A FORWARD –-src _ --dst _ –p udp --sport 475 –j ACCEPT
iptables –A FORWARD –-src _ --dst _ –p tcp --sport 475 –j ACCEPT - Specify the address of the license server in the nethasp.ini file (should be located in the same directory with the executable file of the program).
--------------------- nethasp.ini-------------------------------
[NH_COMMON]
NH_TCPIP = Enabled
...
[NH_TCPIP]
NH_SERVER_ADDR = 168.192.1.10 // ip- , .
NH_TCPIP_METHOD = TCP
NH_USE_BROADCAST = Disabled
---------------------------------------------------------------
Map Local Client Disks
Through visual wizards, we cannot simply add a new listening port on the terminal server: for this, these connections must be available from different interfaces or using different protocols, which is what the error that appears when trying to deceive fate says.
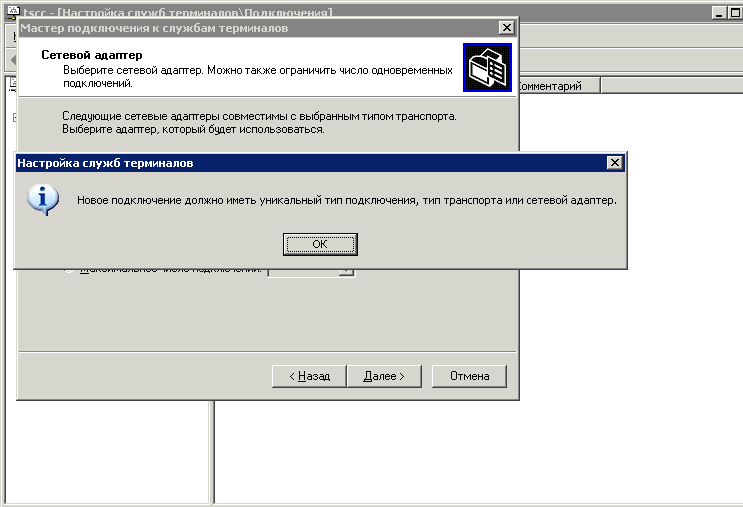
Figure 4. Attempting to create a new connection with existing parameters
However, we are not satisfied with this scenario.
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\_ connection is named “RDP-Tcp”, and information about it is stored in the registry key HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\_To create a new connection, you must:
- export the specified registry branch to a file with the extension * .reg;
- open this file with a text editor;
- change in the export file
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\_toHKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\_2 - find the PortNumber line in the export file and change the numeric value to 0xd3e (3390 in the decimal system, although any other can be used);
- import the resulting file into the registry.
After the described manipulations, we will create a
TerminalDisk group and add to it those whom we will entrust the local disk mapping.Then, in the properties of our new connection, we indicate that only the
TerminalDisk group can connect to it and allow the mapping of local disks, and in the properties of the old connection, we prohibit the mapping of disks and the clipboard.Conclusion
In the future, you can strengthen the scheme by introducing an intrusion detection system.
That's all. I hope someone this material will be useful. Regards and best regards.
Sources
- Information Security Technology Guideline (ITSG-38) - Network Security Zoning (Design Considerations for Services within Zones) - http://www.cse-cst.gc.ca/its-sti/publications/itsg-csti/itsg38- eng.html .
- Services and network ports in Microsoft Windows server systems - http://support.microsoft.com/kb/832017 .
- Restricting Active Directory replication traffic to a specific port - http://support.microsoft.com/kb/224196/en-us .
- Guide to iptables (iptables Tutorial 1.1.19) - http://www.opennet.ru/docs/RUS/iptables/ .
- How can I add a new RDP terminal server to Windows 2000/2003? - http://www.petri.co.il/add_a_new_rdp_listening_port_to_terminal_server.htm .
- 1C: Enterprise 8.2. Client-server option. Admin Guide.
- 1C typical problems when working with HASP - http://itunion.com.ua/article.php?id=39 .
Source: https://habr.com/ru/post/122037/
All Articles