Web authentication with USB tokens
Developing the theme started here and here , I will talk about one more authentication mechanism on web-resources. The mechanism is simple, it is based on the use of digital signature, for storing keys using a USB-token.

The main task of the algorithms described in previous articles was to protect the password from interception and securely store the secret (for example, password hash) in the server database. However, there is another serious threat. This is an insecure environment in which we use passwords. Software and hardware keyloggers, spyware that controls browser input forms, MitM attack, which controls not only the authentication protocol, but also the structure of the html page on which the password is entered, and just the neighbor who oversees you is a threat, which no password authentication scheme can not oppose. This problem was solved at the time by inventing multifactor authentication. Its essence lies in the fact that for successful authentication, you need to know the secret and own any item (in our case, usb-token and its pin-code).
')
This is what developers of information security tools offer.
USB token - a hardware device that can generate a key pair and implements an electronic digital signature requires a PIN code to perform operations. When forming EDS, cryptography on elliptic curves is used. Does not require installation of drivers, is defined as a HID device.
Cross-browser plugin - able to work with usb-token, has a software interface to access cryptographic functions. Does not require administrative rights to install.
The proposed components are a kind of constructor for embedding various cryptographic functions in web applications. With their help, you can implement encryption, authentication and EDS with a high level of security.
For example, the authentication scheme might look like this.
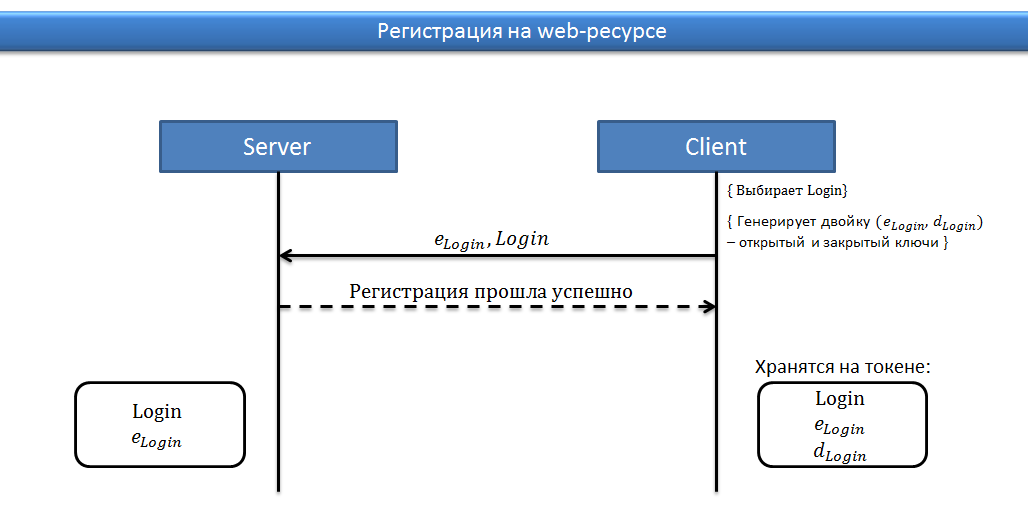
Check in:
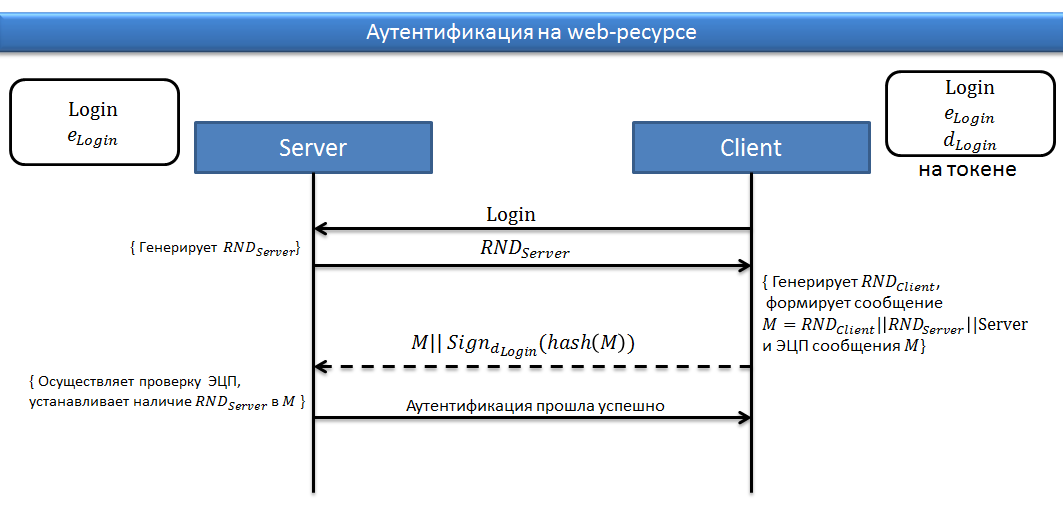
Authentication:
For those who are suspicious of “bicycles” - google “ISO public-Key Two-pass Unilateral Authentication Protocol”.
As usual - a demonstration . To work, you must have a USB-token and install the plugin. Tokens for testing can be taken from me, there are 10 pieces - write in a personal. You can buy here .

The main task of the algorithms described in previous articles was to protect the password from interception and securely store the secret (for example, password hash) in the server database. However, there is another serious threat. This is an insecure environment in which we use passwords. Software and hardware keyloggers, spyware that controls browser input forms, MitM attack, which controls not only the authentication protocol, but also the structure of the html page on which the password is entered, and just the neighbor who oversees you is a threat, which no password authentication scheme can not oppose. This problem was solved at the time by inventing multifactor authentication. Its essence lies in the fact that for successful authentication, you need to know the secret and own any item (in our case, usb-token and its pin-code).
')
This is what developers of information security tools offer.
USB token - a hardware device that can generate a key pair and implements an electronic digital signature requires a PIN code to perform operations. When forming EDS, cryptography on elliptic curves is used. Does not require installation of drivers, is defined as a HID device.
Cross-browser plugin - able to work with usb-token, has a software interface to access cryptographic functions. Does not require administrative rights to install.
The proposed components are a kind of constructor for embedding various cryptographic functions in web applications. With their help, you can implement encryption, authentication and EDS with a high level of security.
For example, the authentication scheme might look like this.
Check in:
- The client generates the key pair e, d in the token;
- The public key e client sends to the server;

Authentication:
- The client sends a login to the server;
- The server generates the RND and sends it to the client;
- The client generates the RND and sends the signed message to the server ( RND-server || RND-client || Server-name );
- The server verifies the authenticity of the EDS using the client's public key;

For those who are suspicious of “bicycles” - google “ISO public-Key Two-pass Unilateral Authentication Protocol”.
As usual - a demonstration . To work, you must have a USB-token and install the plugin. Tokens for testing can be taken from me, there are 10 pieces - write in a personal. You can buy here .
Source: https://habr.com/ru/post/120990/
All Articles