Removing the unlock key from the MBR-blocker
We decided to take into account the wishes of readers of our blog and prepared a short article on how to extract the unlock code from the blocker. Vyacheslav Zakorzhevsky, senior virus analyst at Kaspersky Lab, is responding! ..
To parse, I selected one of the representatives of the new Trojan-Ransom.Win32.Mbro family. These blockers infect the MBR and extort money from the user for unlocking the computer.
I decided not to go into the analysis of the process of hitting the computer on the computer and the algorithm for infecting the boot sector, but immediately proceed to analyze the modified MBR. So, after starting the blocker in question, the operating system will reboot, and the next text will be displayed upon the next boot of the computer.
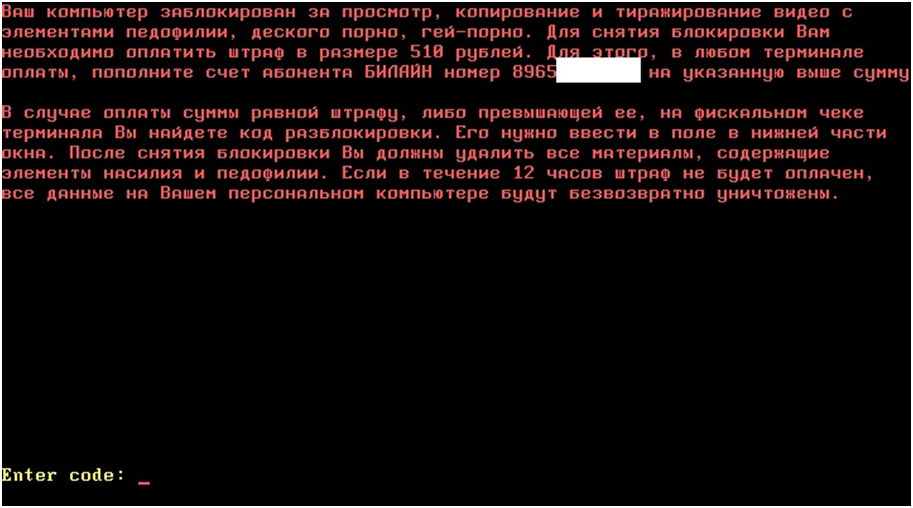
The message that appears when the computer starts after the blocker starts
')
Below are screenshots of the initial sectors of the hard disk before and after their infection with a blocker.

Initial hard disk sectors before infection
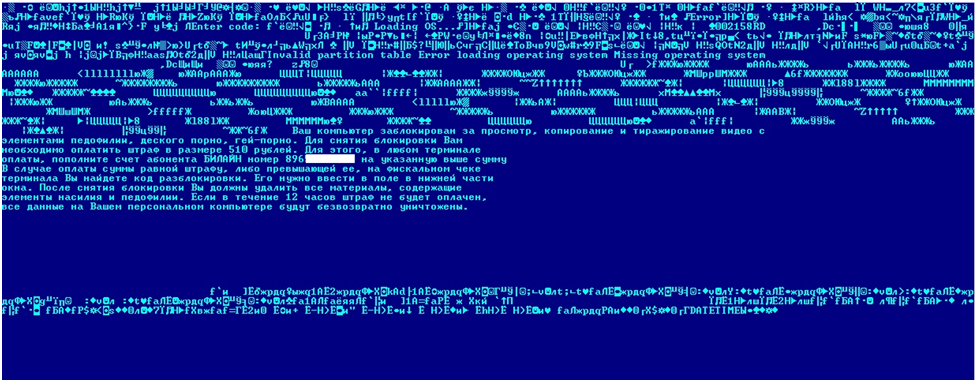
Fragment of the same hard drive area after infection
It is clearly seen that the beginning of the hard disk has been significantly transformed - an additional code has been added, EGA patterns and the text that was shown in the first picture.
Below, I will gradually describe all the functionality of the modified Master Boot Record, and at the end of the article there will be a complete diagram containing the sectors used by the blocker and their purpose. To debug MBR, I used a combination of IDA and Bochs for Windows.
First of all, the malicious code reads the ninth sector and stores it at 0186A: 0000. Then, a transition is performed to it using CALLF 0186A: 0000.
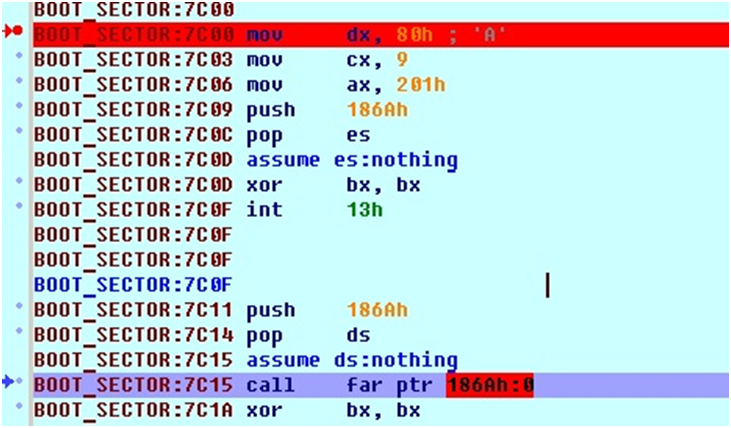
A snippet of code that reads the ninth sector
Next, the current date and time is checked with a reference value. In my case, this value (obviously, presented in a convenient form) was 04.06.2011 15:04. A message requesting payment will appear only if the current time stamp is less than the reference. And if it is more, then the blocker restores the original ICBM and loads the computer, as if nothing had happened. The time and date are obtained directly from the BIOS using the following sequence of commands:
mov al, x
out 70h, al
in al, 71h
aam 10h
aad
Where 'x' takes different values depending on what you want to get. It is worth noting that the BIOS returns numbers in BCD format. The AAM and AAD instructions convert these numbers to hex.
If the check for time and date was successful, then the malware reads the sectors from the third to the fifth inclusive. The third and fourth contain the so-called “user font table”, and the fifth contains the text displayed at startup. To use your own “style” (loudly) writing the text, INT 10h is called. Further, sectors 5–8 inclusive are read out, and the text contained in the fifth and zero sectors (“Enter Code:”) is displayed.
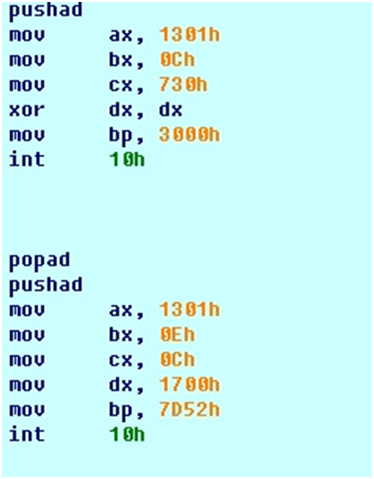
Code snippet that displays text
After that, the cycle of checking the entered text starts working. The cycle is implemented as follows. Initially, the INT 16h instruction is called. This interrupt returns to AX the value of the pressed button (AH = scan code, AL is the character) of the keyboard:
mov ah, 0
push di
int 16h
pop di
jmp short loc_7CC7
Then there is a check on the entered character. If it is between 20h and 7Fh, then its value is written in ES: DI using the STOSB instruction. If the Enter key (0Dh) was pressed, then the input and reference lines are checked using REPE CMPSB.
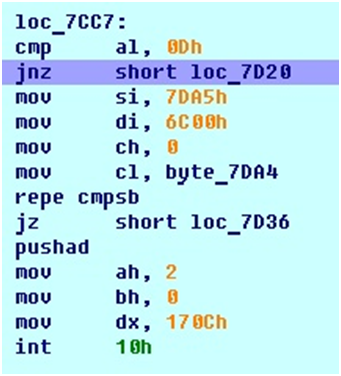
Comparison of the entered string and unlock code
From the screenshot it can be seen that at the address ES: 7DA5 there is a line necessary to unlock the computer boot. Here is what is located at this address: '002158RD', 0. And since the number “6” is entered in CL, this means that it is enough to enter only “002158”.
If the correct code is entered, then the malware takes the original MBR from the second sector and writes it to the beginning of the hard disk.
Sectors used by the blocker:
1 - the main code;
2 - the original first sector;
3 - 4 - user font tables;
5 - 6 - text displayed to the user;
7 - 8 - sectors filled with zeros;
9 - code that performs verification of the current date and time;
PS And it was just possible to look at the beginning of the hard disk from the Hiew "eyes" and find the notorious code.
Now, if by some miracle you pick up a similar thing, it will not be difficult for you to unlock it yourself. But in case of infection with unidentified objects, you should follow the link http://support.kaspersky.ru/viruses/deblocker . I will be glad to answer all the questions in the comments.
To parse, I selected one of the representatives of the new Trojan-Ransom.Win32.Mbro family. These blockers infect the MBR and extort money from the user for unlocking the computer.
I decided not to go into the analysis of the process of hitting the computer on the computer and the algorithm for infecting the boot sector, but immediately proceed to analyze the modified MBR. So, after starting the blocker in question, the operating system will reboot, and the next text will be displayed upon the next boot of the computer.

The message that appears when the computer starts after the blocker starts
')
Below are screenshots of the initial sectors of the hard disk before and after their infection with a blocker.

Initial hard disk sectors before infection

Fragment of the same hard drive area after infection
It is clearly seen that the beginning of the hard disk has been significantly transformed - an additional code has been added, EGA patterns and the text that was shown in the first picture.
Below, I will gradually describe all the functionality of the modified Master Boot Record, and at the end of the article there will be a complete diagram containing the sectors used by the blocker and their purpose. To debug MBR, I used a combination of IDA and Bochs for Windows.
First of all, the malicious code reads the ninth sector and stores it at 0186A: 0000. Then, a transition is performed to it using CALLF 0186A: 0000.

A snippet of code that reads the ninth sector
Next, the current date and time is checked with a reference value. In my case, this value (obviously, presented in a convenient form) was 04.06.2011 15:04. A message requesting payment will appear only if the current time stamp is less than the reference. And if it is more, then the blocker restores the original ICBM and loads the computer, as if nothing had happened. The time and date are obtained directly from the BIOS using the following sequence of commands:
mov al, x
out 70h, al
in al, 71h
aam 10h
aad
Where 'x' takes different values depending on what you want to get. It is worth noting that the BIOS returns numbers in BCD format. The AAM and AAD instructions convert these numbers to hex.
If the check for time and date was successful, then the malware reads the sectors from the third to the fifth inclusive. The third and fourth contain the so-called “user font table”, and the fifth contains the text displayed at startup. To use your own “style” (loudly) writing the text, INT 10h is called. Further, sectors 5–8 inclusive are read out, and the text contained in the fifth and zero sectors (“Enter Code:”) is displayed.

Code snippet that displays text
After that, the cycle of checking the entered text starts working. The cycle is implemented as follows. Initially, the INT 16h instruction is called. This interrupt returns to AX the value of the pressed button (AH = scan code, AL is the character) of the keyboard:
mov ah, 0
push di
int 16h
pop di
jmp short loc_7CC7
Then there is a check on the entered character. If it is between 20h and 7Fh, then its value is written in ES: DI using the STOSB instruction. If the Enter key (0Dh) was pressed, then the input and reference lines are checked using REPE CMPSB.

Comparison of the entered string and unlock code
From the screenshot it can be seen that at the address ES: 7DA5 there is a line necessary to unlock the computer boot. Here is what is located at this address: '002158RD', 0. And since the number “6” is entered in CL, this means that it is enough to enter only “002158”.
If the correct code is entered, then the malware takes the original MBR from the second sector and writes it to the beginning of the hard disk.
Sectors used by the blocker:
1 - the main code;
2 - the original first sector;
3 - 4 - user font tables;
5 - 6 - text displayed to the user;
7 - 8 - sectors filled with zeros;
9 - code that performs verification of the current date and time;
PS And it was just possible to look at the beginning of the hard disk from the Hiew "eyes" and find the notorious code.
Now, if by some miracle you pick up a similar thing, it will not be difficult for you to unlock it yourself. But in case of infection with unidentified objects, you should follow the link http://support.kaspersky.ru/viruses/deblocker . I will be glad to answer all the questions in the comments.
Source: https://habr.com/ru/post/120964/
All Articles