The life cycle of cryptographic hash algorithms
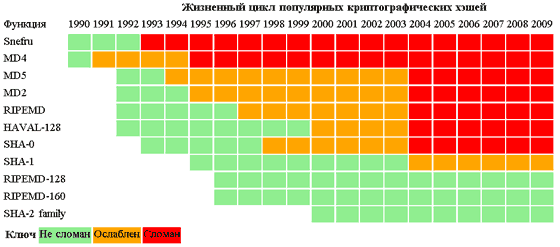
Each technology has its own life cycle, and hash functions are no exception. The programmer and writer Valerie Aurora (in the past she worked as a lead programmer at Red Hat, now she is the director of The Ada Initiative and a freelance journalist) made up a little sign . Apparently, the owners of web services have no choice but to change the hash algorithm every couple of years in search of the optimal ratio of performance and security (in the sense of being protected for at least several years ahead).
The comment on the tablet is even more interesting. How different stages of the life cycle of hash algorithms are perceived by expert cryptologists, programmers and non-experts (the general public on computer forums).
| Stage | Expert response | Developer Reaction | Geek reaction |
|---|---|---|---|
| First sentence | Express skepticism, do not recommend to use in practice | Waiting for expert opinions before adding to OpenSSL | SHA-what? |
| Public analysis | Moderate attempts to find holes and publish an article without much effort. | Most adventurous developers are starting to use hash for specific tasks. | Mention new hash functions on parties to impress other geeks |
| General acceptance | Top-class researchers begin serious work on finding weaknesses (and international recognition) | Even Microsoft now uses this hash function. | Mothers of everyone who tries to suggest that a new hash algorithm can be cracked throughout our lives. |
| Minor vulnerability detected | Mass download preprint of scientific work with arXiv, call for the development of a new hash function | Begin to consider other hashes as an alternative. | Long semi-mathematical posts comparing the complexity of the attack with the number of protons in the Universe |
| Serious vulnerability detected | Hot debate on crypto conferences. Full hacking is considered unreal | Immediately migrate to new hash functions where necessary. | Notice that no real collisions have yet been found. |
| First collision found | Uncork champagne. Interested in details of hacking, but not surprising | Colleagues gather around a computer, compare data that generates a collision and run a hash function on it. | They explain why a simple attack to obtain a collision remains meaningless, they consider that only the second such case can have any meaning. |
| Specific collisions that can be generated on a home PC | Charming! But I'm actually busy breaking into a new hash function. | Send matching X.509 certificates to each other as pranks. | They say at parties that they always knew that this hash algorithm would inevitably be hacked |
| Manual collisions | Memorize method to show fun focus at the next university meeting | Are amazed | Try to remember how to divide large numbers in a column. |
')
Source: https://habr.com/ru/post/120697/
All Articles