Forensic examination of computers infected with TDL4
It all started with the fact that at the beginning of last summer we had a number of tasks related to the quick extraction of the hidden container of the Win32 / Olmarik rootkit file system, then still in the TDL3 version. After a bit of thought, we developed the first version of the TdlFsReader utility, which handles TDL3 and TDL3 +. After some time, it was published in the public domain and helped a lot in the tasks of forensic examinations. However, at the end of the summer, the fourth version of this rootkit appeared, which already had fundamental differences in the file system: now it looked more like a full-fledged file system.
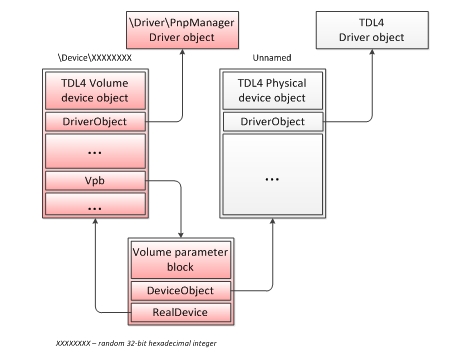
And we delved into the study of the new version of the rootkit, because it was fundamentally different from the previous one. After some time, the internal version of TdlFsReader was updated. And last month we had the opportunity to speak at the wonderful CONFidence'2011 conference in Krakow, where the report “ Defeating x64: The Evolution of the TDL Rootkit ” was presented and within which a new version of TdlFsReader was presented (hxxp: //eset.ru/tools /TdlFsReader.exe).
')
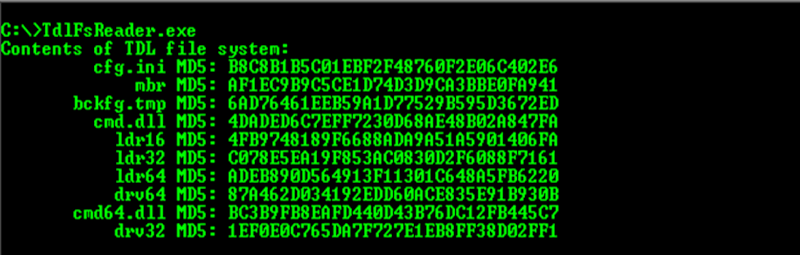
So, now we will tell you more about the tool itself. Actually, the new version is able to cope with all known modifications at the time of publication. And this is TDL3 / 3 + / 4, and it copes not only with x86 versions, but also x64.
Now, a little about the TdlFsReader architecture, in fact, it is divided into two parts, the one in the kernel and the one that is not :)

The main point is to determine the version of the rootkit, remove the mechanisms that counteract the analysis, and only then gain access to the file system and parse it.
Well, as a bonus, another video with debugging the bootkit code in TDL4, which, in fact, bypasses the digital signature verification in the drivers for x64 systems.

And we delved into the study of the new version of the rootkit, because it was fundamentally different from the previous one. After some time, the internal version of TdlFsReader was updated. And last month we had the opportunity to speak at the wonderful CONFidence'2011 conference in Krakow, where the report “ Defeating x64: The Evolution of the TDL Rootkit ” was presented and within which a new version of TdlFsReader was presented (hxxp: //eset.ru/tools /TdlFsReader.exe).
')
So, now we will tell you more about the tool itself. Actually, the new version is able to cope with all known modifications at the time of publication. And this is TDL3 / 3 + / 4, and it copes not only with x86 versions, but also x64.

Now, a little about the TdlFsReader architecture, in fact, it is divided into two parts, the one in the kernel and the one that is not :)

The main point is to determine the version of the rootkit, remove the mechanisms that counteract the analysis, and only then gain access to the file system and parse it.
Well, as a bonus, another video with debugging the bootkit code in TDL4, which, in fact, bypasses the digital signature verification in the drivers for x64 systems.
Source: https://habr.com/ru/post/120569/
All Articles