A beautiful example of phishing in Vkontakte
Not so long ago, an article entitled “ Memories of an ex-spammer ” was published in Chaskor. In it, one of the Internet entrepreneurs who earned spam on Vkontakte announced that such a business would very soon have no air left.
To some extent you can agree with him - now spam is really significantly less than it was even last year. But the remaining spammers resort to more sophisticated methods. Now I want to talk about one of these methods that I met today.
Everything starts in a rather innocent way, one of your friends writes you a banal “hello. how are you?". You no less trivially say that everything is fine with you, and you are interested in the interlocutor's affairs, he clarifies: “are you at the computer now?”, Asks: “do you want to laugh?” And throws a link like

')
At this stage it is already impressive that the bot with a obviously cracked account writes three quite relevant replicas before throwing the link. Link redirects to page
The page to which the link is given is personalized. The numbers 10737644 in the link is my id. In the name and description of the allegedly-video inserted my name:
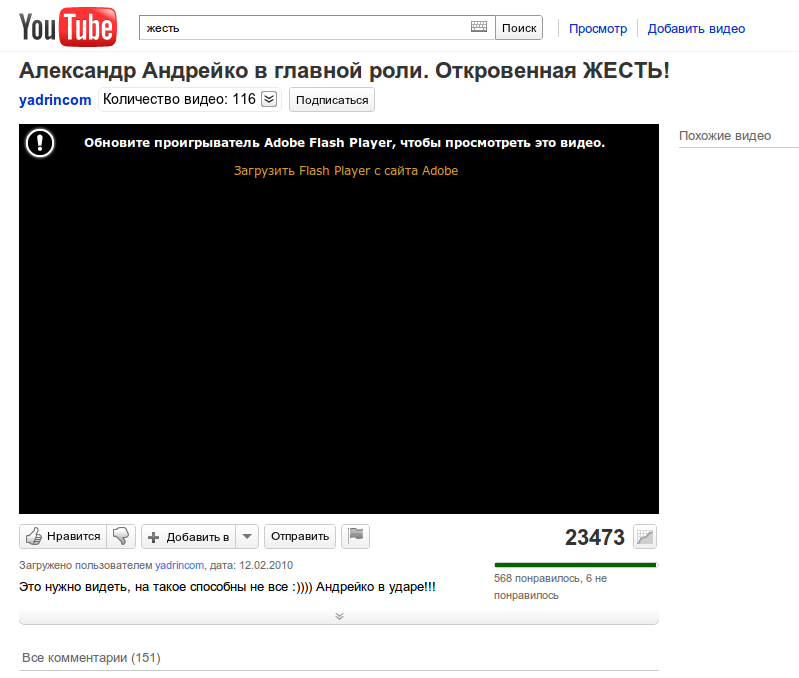
The video cannot be watched, because it turns out that I have an outdated Flash Player. It is proposed to download it "from the Adobe site" at the link
No less wonderful are the “comments”. As the authors of the comments, my real friends from Vkontakte with their avatars are indicated:
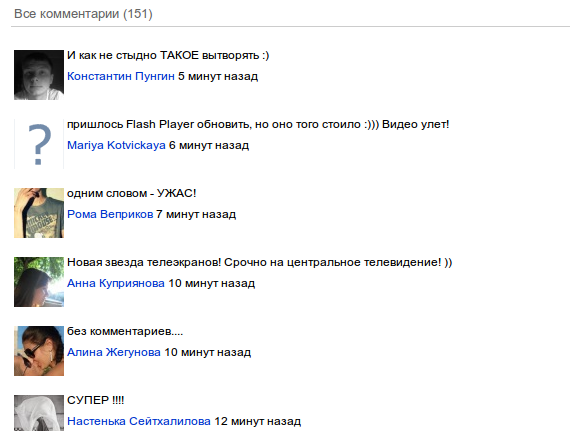
Of particular note is the second comment, which should finally convince me that this “Flash Player” still needs to be downloaded.
I turned to Onthar - the author of the previous topics about malicious spam in "V Kontakte", here is his comment:
To some extent you can agree with him - now spam is really significantly less than it was even last year. But the remaining spammers resort to more sophisticated methods. Now I want to talk about one of these methods that I met today.
Everything starts in a rather innocent way, one of your friends writes you a banal “hello. how are you?". You no less trivially say that everything is fine with you, and you are interested in the interlocutor's affairs, he clarifies: “are you at the computer now?”, Asks: “do you want to laugh?” And throws a link like
http://tinyurl.com/home-video-10737644-html

')
At this stage it is already impressive that the bot with a obviously cracked account writes three quite relevant replicas before throwing the link. Link redirects to page
http://46.98.28.65/home-video/10737644with a YouTube interface. The attentive user, of course, will notice the inconsistency of the URL of the site, but the calculation is obviously done on those who do not pay such attention.
The page to which the link is given is personalized. The numbers 10737644 in the link is my id. In the name and description of the allegedly-video inserted my name:

The video cannot be watched, because it turns out that I have an outdated Flash Player. It is proposed to download it "from the Adobe site" at the link
http://46.98.28.65/Flash-Player.exe
No less wonderful are the “comments”. As the authors of the comments, my real friends from Vkontakte with their avatars are indicated:

Of particular note is the second comment, which should finally convince me that this “Flash Player” still needs to be downloaded.
I turned to Onthar - the author of the previous topics about malicious spam in "V Kontakte", here is his comment:
This file is a trojan downloader. That is, it downloads and launches malicious files from the network. The fact is that there is some kind of affiliate program or something else. The files are loaded unusually(2-3 in only 5 minutes of analysis), and they all continue to be active in the system. While I can say for sure one thing - this is the botnet from the bootloaders, all files are being addressed to different domains (n-78.ru, vn-66.ru ...), but for one ip - 91.223.89.99.
It is no secret that the most diverse malware can be uploaded to the victim’s system, including the famous TDSS bootkit.
Source: https://habr.com/ru/post/120233/
All Articles