Myths about responsibility for pirated software
Hello! Today we want to raise the topic of responsibility for illegal software.

2 weeks ago we held a webinar for the SmartCIO community on this topic, and judging by the record (for the community) of 170 simultaneous listeners, this topic is very, very relevant.
')
In today's post we will write and dispel the main myths associated with the issue, as well as leave for those who wish to link to the full record of the webinar.
So let's go.
However, some statistics. In 2000, 875 crimes were recorded under article 146 of the Criminal Code of the Russian Federation, as a result of which 87 people were convicted. In 2007, 5,216 criminal cases were filed, of which 3,182 cases went to court (for reference: the acquittal is passed in less than 1% of cases).
Further more. So, for 6 months of 2010, more than 4 thousand “criminals” were revealed.
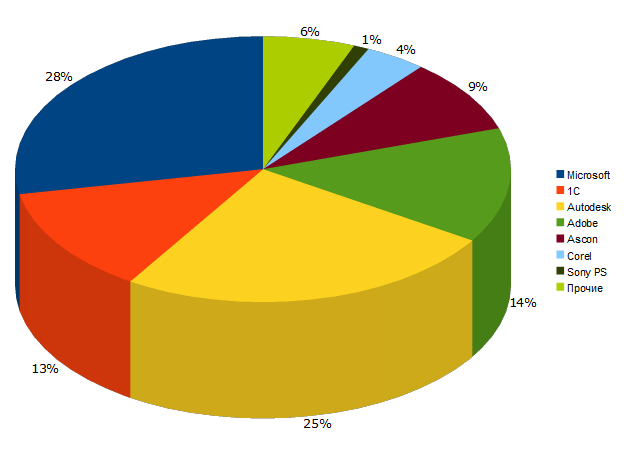
The statistics of the “K” for crimes in 2010 seem to hint to us that this is not true.
By itself, ignorance of the law is no excuse. But we are talking about something else. Those. the man does not deny that it is illegal to use pirated software, but he claims that he did not know that software is pirated. As evidence, the competent authorities use:
If neither the first nor the second has come to you, then the following approach is quite successfully used as evidence. Since you are a CIO or system administrator, then you have the appropriate education and experience, and you, by virtue of your position, could not be unaware of the unlicensed software used.
In the chat at the webinar, many people really expressed the opinion that if they wrote a memo to the company’s director that due to insufficient funding (or some other reason) the company does not use licensed software, then there will be nothing responsible for IT.
By itself, it is a myth. Moreover, the presence of such an official note aggravates the position of its author, because it becomes a material evidence of the intentional nature of the crime (once wrote a note, it means he knew that the software is pirated).
In general, the position of an IT nickname in an organization in this case is much worse than that of a manager — it is much harder for him to prove that he “did not know.”
The first statement: a crime related to art. 146 of the Criminal Code of the Russian Federation relates to public prosecution cases, which means that the application of the victim is not required to initiate a criminal case.
The second statement: guided by the law on the police (which, in terms of the topic under discussion, is no different from the law on the police), the employees of the Ministry of Internal Affairs have the right and the obligation to prevent offenses.
Consequently, to verify the application is enough even homeless Vasily from a nearby basement (although Vasily may need a passport). To initiate a criminal case, following the first statement, the application of the right holder is also not required.
The bottom line is this. A check came to you, a pirate, say, a photoshop, was suddenly found on the computer. And here you valiantly declare that this computer is not a computer of the company, but belongs personally to the employee (or is owned by another company and you rent it).
Do not ride, because:
Art. 1270 of the Civil Code of the Russian Federation tells us that the fact that the program is on the carrier is the use of the program (the method of use is reproduction). Well, during the examination it will still be established that you turned on the computer. And at the time of operation, the pirated software was installed on it.
The seizure of computer equipment can be carried out on the basis of:
None of the listed legal acts speak about the need for a court decision. So, it is not necessary.
It is nevertheless simpler, although an important note: tax authorities may interpret the use of free software by commercial organizations as profit and require tax payment on an amount equivalent to the cost of similar products.
Those who wish to get acquainted with the recording of the webinar, as well as ask the moderator questions to follow the link .

2 weeks ago we held a webinar for the SmartCIO community on this topic, and judging by the record (for the community) of 170 simultaneous listeners, this topic is very, very relevant.
')
In today's post we will write and dispel the main myths associated with the issue, as well as leave for those who wish to link to the full record of the webinar.
So let's go.
Myth 1. Everyone does not sit down.
However, some statistics. In 2000, 875 crimes were recorded under article 146 of the Criminal Code of the Russian Federation, as a result of which 87 people were convicted. In 2007, 5,216 criminal cases were filed, of which 3,182 cases went to court (for reference: the acquittal is passed in less than 1% of cases).
Further more. So, for 6 months of 2010, more than 4 thousand “criminals” were revealed.
Myth 2. Planted only for Microsoft
The statistics of the “K” for crimes in 2010 seem to hint to us that this is not true.

Myth 3. It is impossible to prove the intentional nature of the crime.
By itself, ignorance of the law is no excuse. But we are talking about something else. Those. the man does not deny that it is illegal to use pirated software, but he claims that he did not know that software is pirated. As evidence, the competent authorities use:
- Warning letters from copyright holders;
- Written warnings from police officers.
If neither the first nor the second has come to you, then the following approach is quite successfully used as evidence. Since you are a CIO or system administrator, then you have the appropriate education and experience, and you, by virtue of your position, could not be unaware of the unlicensed software used.
Myth 4: Memo saves you risks
In the chat at the webinar, many people really expressed the opinion that if they wrote a memo to the company’s director that due to insufficient funding (or some other reason) the company does not use licensed software, then there will be nothing responsible for IT.
By itself, it is a myth. Moreover, the presence of such an official note aggravates the position of its author, because it becomes a material evidence of the intentional nature of the crime (once wrote a note, it means he knew that the software is pirated).
In general, the position of an IT nickname in an organization in this case is much worse than that of a manager — it is much harder for him to prove that he “did not know.”
Myth 5. The check can be carried out only with the application of the copyright holder.
The first statement: a crime related to art. 146 of the Criminal Code of the Russian Federation relates to public prosecution cases, which means that the application of the victim is not required to initiate a criminal case.
The second statement: guided by the law on the police (which, in terms of the topic under discussion, is no different from the law on the police), the employees of the Ministry of Internal Affairs have the right and the obligation to prevent offenses.
Consequently, to verify the application is enough even homeless Vasily from a nearby basement (although Vasily may need a passport). To initiate a criminal case, following the first statement, the application of the right holder is also not required.
Myth 6. The computer is not mine
The bottom line is this. A check came to you, a pirate, say, a photoshop, was suddenly found on the computer. And here you valiantly declare that this computer is not a computer of the company, but belongs personally to the employee (or is owned by another company and you rent it).
Do not ride, because:
- The employee is not likely to take the blame and will testify against the organization;
- You will not be trusted anyway, and as a result of the check (including the contents on the PC hard disk) it will be found out in the interests of which organization and by which person this PC was used;
- If you rent a computer (together with software) from another company, then the use is still illegal, since a special license agreement with the copyright holder is required for the rental.
Myth 7. The computer is off / not working, which means there is no guilt.
Art. 1270 of the Civil Code of the Russian Federation tells us that the fact that the program is on the carrier is the use of the program (the method of use is reproduction). Well, during the examination it will still be established that you turned on the computer. And at the time of operation, the pirated software was installed on it.
Myth 8. You can remove a computer only by a court decision.
The seizure of computer equipment can be carried out on the basis of:
- The Police Act;
- Code of Administrative Offenses;
- Criminal Procedure Code of the Russian Federation.
None of the listed legal acts speak about the need for a court decision. So, it is not necessary.
Myth 9. Free software = free software
It is nevertheless simpler, although an important note: tax authorities may interpret the use of free software by commercial organizations as profit and require tax payment on an amount equivalent to the cost of similar products.
Those who wish to get acquainted with the recording of the webinar, as well as ask the moderator questions to follow the link .
Source: https://habr.com/ru/post/118686/
All Articles