Anonymous networks and timing attacks: Tarzan and MorphMix
Introduction | Tor | Tarzan and MorphMix | Low-cost attack | Low-cost attack on Tarzan and Morphmix | Principles of building secure systems (conclusion)
Tarzan is another low latency anonymizing system. It is also based on the ideas of Chaum and, like others, was created to ensure anonymity when using web applications and instant messengers. Unlike Tor, Tarzan is based on peer-to-peer architecture. Each Tarzan-node can be both a client and a transfer node. This eliminates the timing of the analysis of traffic between the input and output nodes. After all, at any moment, anyone can join or leave the network, and any node can be a potential flow initiator (client). A protocol based on the gossip mechanism (similar to that described in the work (Harchol-Balter, Leighton & Lewin 1999)) is used to disseminate information about the nodes available in the network. Due to the peer-to-peer architecture, an attacker can pose as many Tarzan nodes as he wants. Therefore, Tarzan has a mechanism for reducing the likelihood of choosing a malicious node. The mechanism involves categorizing nodes based on the hashes of their IP addresses.
The final recipient of an anonymous stream does not have to be a Tarzan node - access to the outside world is carried out using PNAT (see below). Tarzan authors argue that their network is able to withstand a global observer. This is achieved through a variety of covering traffic, which is called “mimic traffic”. To ensure that the fake traffic does not overload the network, each Tarzan node establishes a fake connection with only a few other nodes.
Here's how it works: when a node connects to the network, after receiving a list of all other Tarzan nodes, it selects some of them to simulate traffic (generates a list of simulators). One of these selected nodes will be used later, when an anonymous connection is required, as the next transfer node.
')
For example, Tarzan a wants to establish an anonymous connection with the srv web server. At the same time, node a wants the length of the tunnel to be l + 1, where l is the number of nodes in the tunnel. Then a performs the following actions:
This results in the following way: a -> n1 -> n2 -> ... -> nl -> PNAT -> svr
It is important that PNAT is selected from all nodes, and not just from among the nl node simulators. Figure 2 shows the Tarzan network and the tunnel created. In the example, each Tarzan node has 6 simulators.
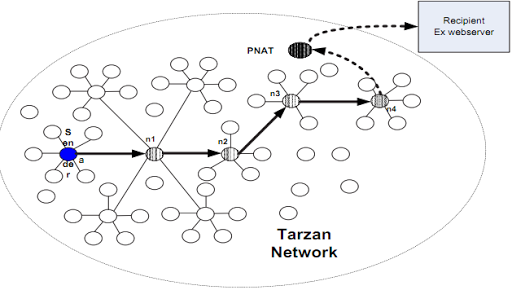
Figure 2. Tarzan architecture based on simulators
MorphMix (Rennhard & Plattner 2002, Rennhard & Plattner 2004) is another system for anonymous communication with low latency. MorphMix follows peer-to-peer architecture. Like Tor, MorphMix uses chains of fixed-length transmission nodes and layer-by-layer encryption (each node can only deploy its own layer). As in Tor, there is no cover traffic in MorphMix - it is considered that it is ineffective.
MorphMix developers use the following terminology:
chain of transmission nodes - anonymous tunnel ( anonymous tunnel )
the first node is the initiator
the last node is the last node
the nodes between the first and the last node are intermediate nodes
Unlike Tor and Tarzan, where the initiator assigns nodes for the organization of the tunnel, in MorphMix each intermediate node chooses its own successor. To confirm that the choice of the next node is honestly provided for the mechanism of witnesses. Any node can be a witness.
When the initiator node a wants to create an anonymous tunnel, it selects the first intermediate node b and the witness w from its list of neighbors. Witness w acts as a third trusted party in the process of choosing the next tunnel node after b - let's call it c . w allows initiator a to establish a common key with node c through b , without revealing key material to node b .
Figure 3 (from Rennhard & Plattner 2002) shows how the process of selecting the next tunnel node with the help of a witness takes place in MorphMix. It is assumed that the connection between a and b is already established.
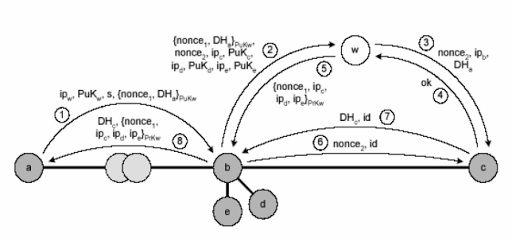
Figure 3. The process of selecting the next (after b ) tunnel node in MorphMix.
1. a selects a witness w from among the nodes known to him. It then generates half of the key information DH a , adds to it the value of the current time ( nonce 1 ) and encrypts all this with the public key w - {nonce 1 , DH a } PuKw . Note that the indication of the current time nonce 1 is used to prevent replay attacks . s - indicates b how many nodes it should select (from these nodes the next node for the tunnel will be selected). b does not receive any information about key information DH a , because it is encrypted in the public key w .
2. After b received the message, he forwards DH a (as part of an encrypted message {nonce 1 , DH a } PuKw ) to witness w along with the selected nodes and their public keys ( {ip c , PuK c , ip d , PuK d , ip e , PuK e } ).
3. w performs two actions. First, it decrypts {nonce 1 , DH a } PuKw to get DH a . Then w randomly selects the next tunnel node c . Next, w sends DH a and information about node b and its public key {ip b , PuK b } to node c .
4. If he agrees to become the next node of the tunnel, he sends w the message “Ok”.
5. w signs the list of selected b node along with nonce 1 , with the selected node c indicated first after nonce 1 . And sends b .
6. b receives the message from w . He learns that the next node in the tunnel should be with . It generates the id of the anonymous connection between b and c . Then it sends the id and the new value of the current time nonce 2 to the node c .
7. In response, c generates and sends b its half of the key information DH with along with the indication of id .
8. b sends a DH with and a list of selected nodes signed by the witness w .
In MorphMix, nodes do not have to know about all other nodes in the network.
Translator Notes
* When translating, we encountered some inconsistencies in the description of the work of MorphMix. We tried to level them with the help of a non-literal free translation, which gives a sufficient idea of the work of the network in this context, but cannot claim to be 100% accurate. Therefore, if you need accurate information on how MorphMix works, refer to the relevant documents.
Tarzan
Tarzan is another low latency anonymizing system. It is also based on the ideas of Chaum and, like others, was created to ensure anonymity when using web applications and instant messengers. Unlike Tor, Tarzan is based on peer-to-peer architecture. Each Tarzan-node can be both a client and a transfer node. This eliminates the timing of the analysis of traffic between the input and output nodes. After all, at any moment, anyone can join or leave the network, and any node can be a potential flow initiator (client). A protocol based on the gossip mechanism (similar to that described in the work (Harchol-Balter, Leighton & Lewin 1999)) is used to disseminate information about the nodes available in the network. Due to the peer-to-peer architecture, an attacker can pose as many Tarzan nodes as he wants. Therefore, Tarzan has a mechanism for reducing the likelihood of choosing a malicious node. The mechanism involves categorizing nodes based on the hashes of their IP addresses.
The final recipient of an anonymous stream does not have to be a Tarzan node - access to the outside world is carried out using PNAT (see below). Tarzan authors argue that their network is able to withstand a global observer. This is achieved through a variety of covering traffic, which is called “mimic traffic”. To ensure that the fake traffic does not overload the network, each Tarzan node establishes a fake connection with only a few other nodes.
Here's how it works: when a node connects to the network, after receiving a list of all other Tarzan nodes, it selects some of them to simulate traffic (generates a list of simulators). One of these selected nodes will be used later, when an anonymous connection is required, as the next transfer node.
')
For example, Tarzan a wants to establish an anonymous connection with the srv web server. At the same time, node a wants the length of the tunnel to be l + 1, where l is the number of nodes in the tunnel. Then a performs the following actions:
- a selects the first transmission node n1 from among its simulators
- a asks n1 for a list of its simulators l n1
- a selects the second transmission node n2 from the list l n1
- a asks n2 for a list of its simulators l n2 . The request goes through n1 , while n1 does not know what exactly it sends.
- a selects the third transmission node n3 from the list l n2
- Thus, a tunnel grows until it has l nodes.
- In the end, a randomly selects the last node from among all the nodes in the network. This last node in Tor is called the exit node, and in Tarzan - PNAT .
This results in the following way: a -> n1 -> n2 -> ... -> nl -> PNAT -> svr
It is important that PNAT is selected from all nodes, and not just from among the nl node simulators. Figure 2 shows the Tarzan network and the tunnel created. In the example, each Tarzan node has 6 simulators.

Figure 2. Tarzan architecture based on simulators
MorphMix *
MorphMix (Rennhard & Plattner 2002, Rennhard & Plattner 2004) is another system for anonymous communication with low latency. MorphMix follows peer-to-peer architecture. Like Tor, MorphMix uses chains of fixed-length transmission nodes and layer-by-layer encryption (each node can only deploy its own layer). As in Tor, there is no cover traffic in MorphMix - it is considered that it is ineffective.
MorphMix developers use the following terminology:
chain of transmission nodes - anonymous tunnel ( anonymous tunnel )
the first node is the initiator
the last node is the last node
the nodes between the first and the last node are intermediate nodes
Unlike Tor and Tarzan, where the initiator assigns nodes for the organization of the tunnel, in MorphMix each intermediate node chooses its own successor. To confirm that the choice of the next node is honestly provided for the mechanism of witnesses. Any node can be a witness.
When the initiator node a wants to create an anonymous tunnel, it selects the first intermediate node b and the witness w from its list of neighbors. Witness w acts as a third trusted party in the process of choosing the next tunnel node after b - let's call it c . w allows initiator a to establish a common key with node c through b , without revealing key material to node b .
Figure 3 (from Rennhard & Plattner 2002) shows how the process of selecting the next tunnel node with the help of a witness takes place in MorphMix. It is assumed that the connection between a and b is already established.

Figure 3. The process of selecting the next (after b ) tunnel node in MorphMix.
1. a selects a witness w from among the nodes known to him. It then generates half of the key information DH a , adds to it the value of the current time ( nonce 1 ) and encrypts all this with the public key w - {nonce 1 , DH a } PuKw . Note that the indication of the current time nonce 1 is used to prevent replay attacks . s - indicates b how many nodes it should select (from these nodes the next node for the tunnel will be selected). b does not receive any information about key information DH a , because it is encrypted in the public key w .
2. After b received the message, he forwards DH a (as part of an encrypted message {nonce 1 , DH a } PuKw ) to witness w along with the selected nodes and their public keys ( {ip c , PuK c , ip d , PuK d , ip e , PuK e } ).
3. w performs two actions. First, it decrypts {nonce 1 , DH a } PuKw to get DH a . Then w randomly selects the next tunnel node c . Next, w sends DH a and information about node b and its public key {ip b , PuK b } to node c .
4. If he agrees to become the next node of the tunnel, he sends w the message “Ok”.
5. w signs the list of selected b node along with nonce 1 , with the selected node c indicated first after nonce 1 . And sends b .
6. b receives the message from w . He learns that the next node in the tunnel should be with . It generates the id of the anonymous connection between b and c . Then it sends the id and the new value of the current time nonce 2 to the node c .
7. In response, c generates and sends b its half of the key information DH with along with the indication of id .
8. b sends a DH with and a list of selected nodes signed by the witness w .
In MorphMix, nodes do not have to know about all other nodes in the network.
Translator Notes
* When translating, we encountered some inconsistencies in the description of the work of MorphMix. We tried to level them with the help of a non-literal free translation, which gives a sufficient idea of the work of the network in this context, but cannot claim to be 100% accurate. Therefore, if you need accurate information on how MorphMix works, refer to the relevant documents.
Source: https://habr.com/ru/post/117586/
All Articles