Denial of service attack with slow HTTP POST
Good day, dear habrovchane!
I want to tell you about the relatively new and interesting, in my opinion, the mechanism of attack against denial of service - Slow HTTP POST .
The search showed no information on the topic on Habr, which somewhat surprised me, and I decided to fill this unfortunate omission. The topic is not new, but, as shown by my small research, it is more than relevant. Looking ahead, I’ll say that the results I received suggest that there is a widely available technology that allows you to “install” small and medium-sized sites from a single computer with a small channel, and when using several machines with high-speed Internet access everywhere, cause a lot of problems and more serious projects. All interested in the most humbly welcome under habrakat.
Like all brilliant, the technology of this attack is very elegant and simple. The attack is based on a vulnerability in the HTTP protocol. Slow HTTP POST attack works as follows: the attacker sends a POST header with a legitimate Content-Length field, which allows the web server to understand how much data is coming to it. As soon as the header is sent, the body of the POST message begins to be transmitted at a very slow speed, which allows you to use server resources for much longer than necessary and, as a result, prevent the processing of other requests. Several thousand such connections can put a web server for a few minutes. If your system has a web interface, then this type of attack will allow you to "put" it without any problems.
The attack was first demonstrated to the public at the OWASP 2010 Application Security Conference. Researcher Wong Onn Chee first discovered the attack in 2009 with a team of researchers from Singapore. Later attacks were investigated (including by Microsoft). Vulnerability in the protocol is now officially recognized. Initially, such attacks were carried out in China. Online games were used to recruit bots - the computers of hapless players were used to send specially crafted HTTP requests to the target system.
The simplicity of the attack implementation made it possible to effectively use for this a simple Java applet that was launched during an online game. As soon as the victim accepted the self-signed applet, the applet began to perform the attack while the user was playing the online game. After exiting the game and closing the browser, the attack stopped, and the applet was removed. Finding that you have become a source of attack is quite problematic - after all, a computer does not become infected in the classical sense of the word, and it is difficult to distinguish traffic from legal HTTP traffic. In addition, the Internet channel is almost not overloaded.
The attack leads to the collapse of web servers with Microsoft IIS and Apache (as shown by my experience, the list of vulnerable web servers is not limited to them) within the HTTP or HTTPS protocols and, obviously, any "secure" connections like SSL, VPN and others. Also, the attack can be adapted to work with SMTP and even DNS-servers. The load balancing software currently used to prevent similar-type DDOS attacks (Slowloris) is not effective against the new technique.
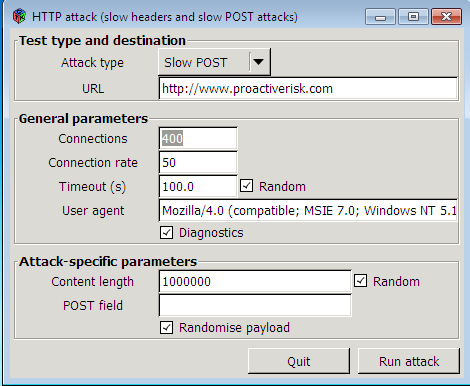
Programs that implement the attack (RU Dead Yet? And the OWASP HTTP POST Tool, which I used, then we are talking about it), are in the public domain and easy to googling. Program settings are very simple, there is a detailed help and even a graphical shell (the program itself is console). Source codes are also available.
')
All this I, of course, checked in practice. I downloaded the OWASP HTTP DoS Tool, entered the address of one site under my control. Incredulously clicked on the button. A minute later the site lay. This is despite the fact that I am deprived of good internet at home, and my speed on upload is only half a megabit. Saytik weak, this is a forum (vBulletin) for a hundred people, shared hosting, nginx server. But, nevertheless, you see, even such a small site to hang out from under a half-megabit channel ... is at least surprising.
Science went further. Realizing that even a very small channel is enough for the attack, I launched an attack through AdvTor (we read about TOR here ). As if stupid and improbable it did not sound, the site fell. Later, using several computers with a wider Internet channel, I managed to get through the same AdvTor, purely of scientific interest, to send more serious sites to Down (having argued previously with the owner that I would put his brainchild without the help of a botnet). Further more. A script was written that implements a continuous attack (the OWASP program has a limitation on this case - after 40,000 requests it turns off), from time to time switching the output TOR node, clearing its cache and restarting both programs. By the way, in this mode of use, they started to flow very well. The processor was loaded at 100%, and AdvTor shamelessly devoured memory. In general, TOR was far from being delighted with such use, but it was surprisingly good, although it sometimes hung tight. To use the TOR network for this, of course, is sheer barbarism, butitching science requires sacrifice. Tests were carried out on several other sites of different levels (again, by agreement with the owners, except once, when I decided to play a trick on a friend). The result was sad. It turned out. that putting almost any average website is relatively easy and more than possible.
1) Slow HTTP POST allows you to organize denial of service attacks, with the previously unattainable ratio of the required power / channel of the attacking computer (s) and the server being attacked.
2) A huge number of small and medium sites today are subject to this attack. Moreover, it is often difficult from the server side to even diagnose that the site is being attacked - the traffic does not exceed normal values.
3) The implementation of the attack is very simple, and requires almost no investment. Moreover, this is the only science known denial-of-service attack that can actually be organized through a proxy!
4) The similarity of traffic attacks with legal traffic complicate the filtering of "harmful" packets, as well as make it difficult to organize a difficult-to-find botnet.
Information does not claim to be new or complete. It is rather a collective free translation from many sources, plus some interesting experience. It was written in a rare free night (good work is enough), so I apologize for the mistakes, correct. If this topic is of interest to anyone, I am ready to write in more detail about the attack mechanism and methods of protection.
Official page of the program from OWASP
Excellent article (for friends with English)
Official presentation on the topic (PDF), again for English speakers
A detailed study describing the methods of protection (and again English)
General information on the topic on the site OWASP
This LJ was a post on
Dear Habrayuser Sicness was not lazy, and compiled the OWASP HTTP POST Tool under Ubuntu. Under the link archive with a binary and library, necessary for its work. Source code is available here .
I want to tell you about the relatively new and interesting, in my opinion, the mechanism of attack against denial of service - Slow HTTP POST .
The search showed no information on the topic on Habr, which somewhat surprised me, and I decided to fill this unfortunate omission. The topic is not new, but, as shown by my small research, it is more than relevant. Looking ahead, I’ll say that the results I received suggest that there is a widely available technology that allows you to “install” small and medium-sized sites from a single computer with a small channel, and when using several machines with high-speed Internet access everywhere, cause a lot of problems and more serious projects. All interested in the most humbly welcome under habrakat.
Theory
Like all brilliant, the technology of this attack is very elegant and simple. The attack is based on a vulnerability in the HTTP protocol. Slow HTTP POST attack works as follows: the attacker sends a POST header with a legitimate Content-Length field, which allows the web server to understand how much data is coming to it. As soon as the header is sent, the body of the POST message begins to be transmitted at a very slow speed, which allows you to use server resources for much longer than necessary and, as a result, prevent the processing of other requests. Several thousand such connections can put a web server for a few minutes. If your system has a web interface, then this type of attack will allow you to "put" it without any problems.
The attack was first demonstrated to the public at the OWASP 2010 Application Security Conference. Researcher Wong Onn Chee first discovered the attack in 2009 with a team of researchers from Singapore. Later attacks were investigated (including by Microsoft). Vulnerability in the protocol is now officially recognized. Initially, such attacks were carried out in China. Online games were used to recruit bots - the computers of hapless players were used to send specially crafted HTTP requests to the target system.
The simplicity of the attack implementation made it possible to effectively use for this a simple Java applet that was launched during an online game. As soon as the victim accepted the self-signed applet, the applet began to perform the attack while the user was playing the online game. After exiting the game and closing the browser, the attack stopped, and the applet was removed. Finding that you have become a source of attack is quite problematic - after all, a computer does not become infected in the classical sense of the word, and it is difficult to distinguish traffic from legal HTTP traffic. In addition, the Internet channel is almost not overloaded.
The attack leads to the collapse of web servers with Microsoft IIS and Apache (as shown by my experience, the list of vulnerable web servers is not limited to them) within the HTTP or HTTPS protocols and, obviously, any "secure" connections like SSL, VPN and others. Also, the attack can be adapted to work with SMTP and even DNS-servers. The load balancing software currently used to prevent similar-type DDOS attacks (Slowloris) is not effective against the new technique.
Programs that implement the attack (RU Dead Yet? And the OWASP HTTP POST Tool, which I used, then we are talking about it), are in the public domain and easy to googling. Program settings are very simple, there is a detailed help and even a graphical shell (the program itself is console). Source codes are also available.
OWASP HTTP POST Tool

')
Practice
All this I, of course, checked in practice. I downloaded the OWASP HTTP DoS Tool, entered the address of one site under my control. Incredulously clicked on the button. A minute later the site lay. This is despite the fact that I am deprived of good internet at home, and my speed on upload is only half a megabit. Saytik weak, this is a forum (vBulletin) for a hundred people, shared hosting, nginx server. But, nevertheless, you see, even such a small site to hang out from under a half-megabit channel ... is at least surprising.
Science went further. Realizing that even a very small channel is enough for the attack, I launched an attack through AdvTor (we read about TOR here ). As if stupid and improbable it did not sound, the site fell. Later, using several computers with a wider Internet channel, I managed to get through the same AdvTor, purely of scientific interest, to send more serious sites to Down (having argued previously with the owner that I would put his brainchild without the help of a botnet). Further more. A script was written that implements a continuous attack (the OWASP program has a limitation on this case - after 40,000 requests it turns off), from time to time switching the output TOR node, clearing its cache and restarting both programs. By the way, in this mode of use, they started to flow very well. The processor was loaded at 100%, and AdvTor shamelessly devoured memory. In general, TOR was far from being delighted with such use, but it was surprisingly good, although it sometimes hung tight. To use the TOR network for this, of course, is sheer barbarism, but
findings
1) Slow HTTP POST allows you to organize denial of service attacks, with the previously unattainable ratio of the required power / channel of the attacking computer (s) and the server being attacked.
2) A huge number of small and medium sites today are subject to this attack. Moreover, it is often difficult from the server side to even diagnose that the site is being attacked - the traffic does not exceed normal values.
3) The implementation of the attack is very simple, and requires almost no investment. Moreover, this is the only science known denial-of-service attack that can actually be organized through a proxy!
4) The similarity of traffic attacks with legal traffic complicate the filtering of "harmful" packets, as well as make it difficult to organize a difficult-to-find botnet.
PS
Information does not claim to be new or complete. It is rather a collective free translation from many sources, plus some interesting experience. It was written in a rare free night (good work is enough), so I apologize for the mistakes, correct. If this topic is of interest to anyone, I am ready to write in more detail about the attack mechanism and methods of protection.
Literature and links
Official page of the program from OWASP
Excellent article (for friends with English)
Official presentation on the topic (PDF), again for English speakers
A detailed study describing the methods of protection (and again English)
General information on the topic on the site OWASP
This LJ was a post on
Added by
Dear Habrayuser Sicness was not lazy, and compiled the OWASP HTTP POST Tool under Ubuntu. Under the link archive with a binary and library, necessary for its work. Source code is available here .
Source: https://habr.com/ru/post/116056/
All Articles