Features Firewall in Windows 7
This year, Windows XP is 10 years old. The age of the firewall built into the OS can be considered in different ways. Now, probably, not everyone will remember that in the original version of Windows XP, the prototype of the current firewall was called Internet Connection Firewall (ICF), had very limited functionality and was configured manually in the properties of a specific network interface. However, even then one of the most frequent questions that we received from corporate customers sounded like this: “Why did you not turn on ICF by default?”. Funny, yes?
Windows Firewall itself appeared with the release of SP2 for Windows XP, contained a number of significant improvements over ICF and was included in the OS by default. The latter fact at first often led to the inoperability of many obsolete applications, the need to specify additional settings in Windows and, of course, criticized MS. And how much was written about the lack of outbound filtering ... But already Nimda, Slammer, Blaster, other pleasant names were thundered, and it was obvious to many that having a built-in firewall is far from superfluous.
Vista and Windows Server 2008 brought even greater changes to the Windows Firewall: a new filtering platform actually appeared, on the basis of which the firewall worked and third-party solutions could be created, IPsec policies were combined with the firewall settings, and outbound filtering appeared.
')
As part of this post, I would like to highlight the features of the Windows Firewall in the "seven" and R2. These features, of course, are already listed in various articles on the same TechNet, but, as a rule, so briefly that the essence of the improvements can slip away and remain undervalued.
Several active profiles
The first and most important, as it seems to me, feature of the firewall in Windows 7 is that several profiles can be active at the same time.
Let me remind you, starting with Windows Vista, the built-in firewall supports three profiles - domain, private and public (there were two of them in XP - domain and standard). Each profile is a set of applicable firewall rules. Whenever a computer connects to a network, the OS tries to identify that network and apply the appropriate profile. In particular, if a domain controller is available on the network to which this computer belongs, the domain profile is automatically applied. If the domain controller does not have a new network to which the computer is connected, the most restrictive public profile is applied. In this case, a window appears in front of the user in which you can explicitly select a profile for this network (see Figure 1).
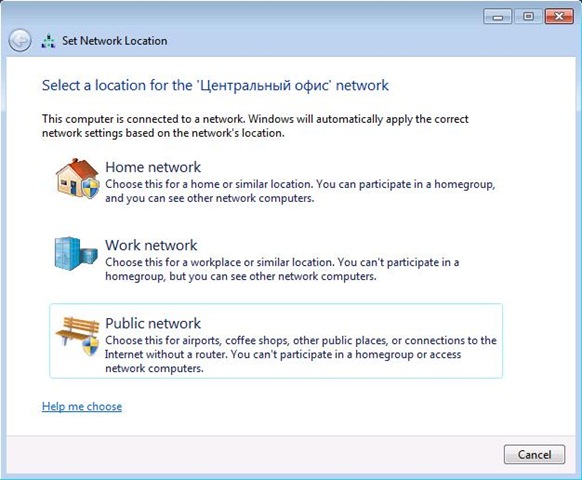
Fig. one
The Network Location Awareness (NLA) service stores network information in a special database. The next time the computer connects to this network, and the NLA successfully identifies it based on the information stored in the database, the firewall will automatically apply the appropriate profile.
So in Windows Vista at any given time, only one profile can be active. That is, at each time point, the settings of only one profile are applied to all network interfaces for which the firewall is enabled.
This causes certain problems. For example, in the domain profile, the administrator allowed inbound connections for some business application (Microsoft Office Groove, as an option). The user works on a laptop in a domain network and uses this business application. Suppose a user moves into a meeting room, from which some public WiFi network is available, say, the office of a neighboring floor or a mobile operator. The laptop's WiFi adapter automatically connects to this public network, and the public profile must be applied to it. In a situation like this, when adapters “look” at different networks, Vista always applies the most restrictive profile, that is, public, in which, in turn, all incoming connections are prohibited. As a result, our business application stops working correctly.
Another example is VPN. All the same user from his laptop is trying to access corporate resources, but from home. It establishes a VPN connection, and in front of it is the entire corporate network. However, since a private profile is used for a VPN connection, for example, the settings of the domain profile of the firewall are not applied, and the business application again does not work as it should. All this creates a certain headache for the IT department of the company.
Windows 7 supports the same three firewall profiles. However, several profiles can be active at the same time. Each network adapter uses the most appropriate profile for the network to which it is connected (see Figure 2).
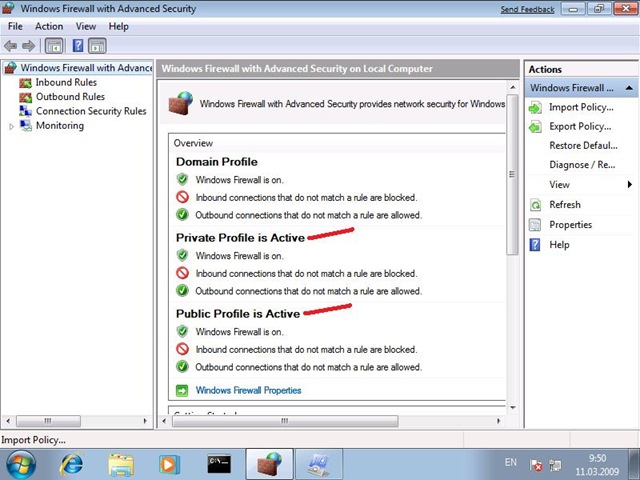
Fig. 2
So, after connecting from the Internet cafe with a VPN to the corporate network, all domain traffic through the VPN tunnel is applied to the domain profile, while all other traffic is protected by the public profile.
The following are less significant, but very useful changes that are worth paying attention to.
Setting exceptions for multiple profiles
There are several enhancements to the Windows Firewall applet interface in the control panel. Previously, when setting up exceptions, that is, specifying which application is allowed to work through the firewall, the settings were saved in the current (currently active) profile. In Windows 7, you can explicitly select one or more profiles to which this exception applies (see Figure 3).
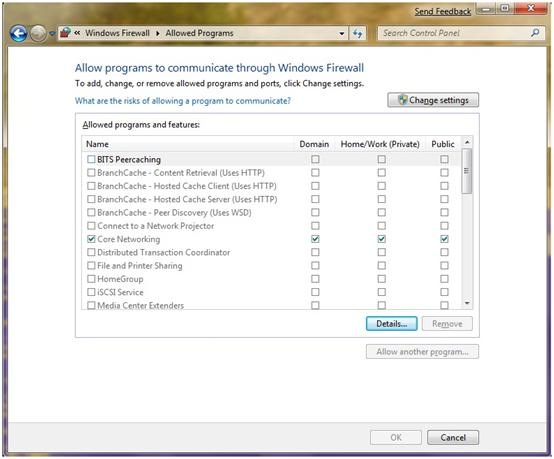
Fig. 3
There is a similar possibility when an alert appears that a certain application is trying to work through the firewall (see Figure 4).
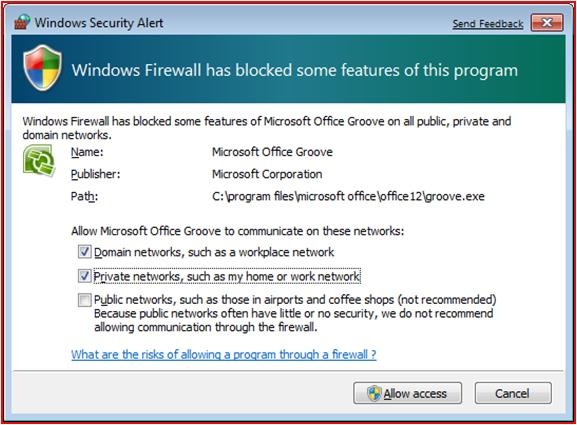
Fig. four
I emphasize that this is exactly the Windows Firewall applet. If you create a rule using Windows Firewall with Advanced Security, then in both Vista and Windows 7, the created rule can be immediately distributed to several profiles.
Enable / disable firewall for profiles
In Windows 7, you can quite easily turn the firewall on or off, as well as notifications about blocking applications for a specific profile or profiles (see Figure 5).
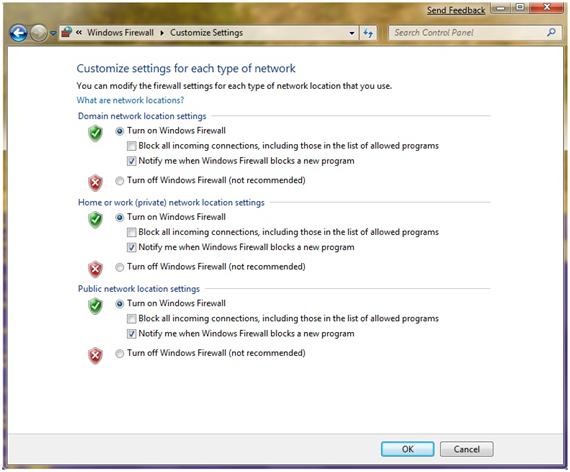
Fig. five
Additional links
With the help of additional links from the Windows Firewall applet in the “seven”, you can quickly go to the Windows Firewall console with Advanced Security, default settings, or a problem resolution tool. This trifle, which usually do not pay attention, helps to save time (Fig. 6.).
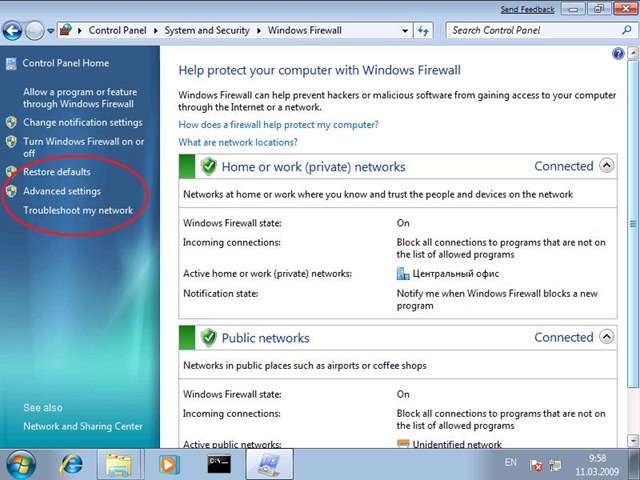
Fig. 6
Exceptions for users and computers
When creating rules in Windows Vista, you could use IPSec and specify that connections are allowed for specific users and / or computers. In Windows 7, plus, you can set exceptions for users and / or computers (see Figure 7).
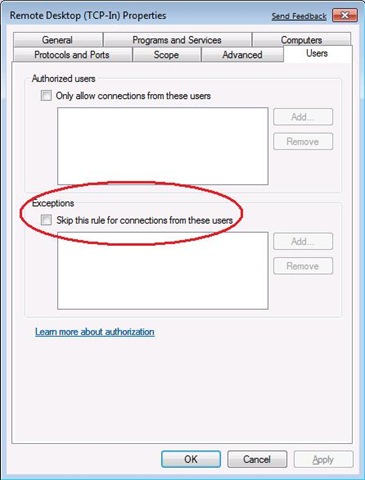
Fig. 7
Port ranges
The last detail I would like to point out is the ability to specify port ranges in the rules now. In Vista, it was possible to specify specific port numbers by separating them with a comma (see Figure 8).

Fig. eight
I also add that for third-party developers, an updated API is available compared to previous versions of the API, which allows, on the one hand, to add its functionality, on the other, to use only the necessary capabilities of the built-in firewall. For example, a developer can implement his firewall management policies, but still rely on built-in IPsec policies.
However, keep in mind that if you turn off Windows Firewall not through the API, but using standard Windows tools (control panel, netsh), then all IPsec policies are turned off. The latter leads to disabling, for example, DirectAccess on the client.
Another feature is related to the ability to configure filters for a virtual account and Service SID. Both of these mechanisms are discussed in detail here .
So, Windows Firewall is evolving with the operating system, responding to no less actively improving security threats.
Without pretending to be a powerful specialized firewall, the Windows Firewall is available out of the box, effectively managed through group policies or scripts and performs its main task - additional protection of the workstation / server from external unwanted network exposure. I think that copes with this task very well. Why not use?
Windows Firewall itself appeared with the release of SP2 for Windows XP, contained a number of significant improvements over ICF and was included in the OS by default. The latter fact at first often led to the inoperability of many obsolete applications, the need to specify additional settings in Windows and, of course, criticized MS. And how much was written about the lack of outbound filtering ... But already Nimda, Slammer, Blaster, other pleasant names were thundered, and it was obvious to many that having a built-in firewall is far from superfluous.
Vista and Windows Server 2008 brought even greater changes to the Windows Firewall: a new filtering platform actually appeared, on the basis of which the firewall worked and third-party solutions could be created, IPsec policies were combined with the firewall settings, and outbound filtering appeared.
')
As part of this post, I would like to highlight the features of the Windows Firewall in the "seven" and R2. These features, of course, are already listed in various articles on the same TechNet, but, as a rule, so briefly that the essence of the improvements can slip away and remain undervalued.
Several active profiles
The first and most important, as it seems to me, feature of the firewall in Windows 7 is that several profiles can be active at the same time.
Let me remind you, starting with Windows Vista, the built-in firewall supports three profiles - domain, private and public (there were two of them in XP - domain and standard). Each profile is a set of applicable firewall rules. Whenever a computer connects to a network, the OS tries to identify that network and apply the appropriate profile. In particular, if a domain controller is available on the network to which this computer belongs, the domain profile is automatically applied. If the domain controller does not have a new network to which the computer is connected, the most restrictive public profile is applied. In this case, a window appears in front of the user in which you can explicitly select a profile for this network (see Figure 1).

Fig. one
The Network Location Awareness (NLA) service stores network information in a special database. The next time the computer connects to this network, and the NLA successfully identifies it based on the information stored in the database, the firewall will automatically apply the appropriate profile.
So in Windows Vista at any given time, only one profile can be active. That is, at each time point, the settings of only one profile are applied to all network interfaces for which the firewall is enabled.
This causes certain problems. For example, in the domain profile, the administrator allowed inbound connections for some business application (Microsoft Office Groove, as an option). The user works on a laptop in a domain network and uses this business application. Suppose a user moves into a meeting room, from which some public WiFi network is available, say, the office of a neighboring floor or a mobile operator. The laptop's WiFi adapter automatically connects to this public network, and the public profile must be applied to it. In a situation like this, when adapters “look” at different networks, Vista always applies the most restrictive profile, that is, public, in which, in turn, all incoming connections are prohibited. As a result, our business application stops working correctly.
Another example is VPN. All the same user from his laptop is trying to access corporate resources, but from home. It establishes a VPN connection, and in front of it is the entire corporate network. However, since a private profile is used for a VPN connection, for example, the settings of the domain profile of the firewall are not applied, and the business application again does not work as it should. All this creates a certain headache for the IT department of the company.
Windows 7 supports the same three firewall profiles. However, several profiles can be active at the same time. Each network adapter uses the most appropriate profile for the network to which it is connected (see Figure 2).

Fig. 2
So, after connecting from the Internet cafe with a VPN to the corporate network, all domain traffic through the VPN tunnel is applied to the domain profile, while all other traffic is protected by the public profile.
The following are less significant, but very useful changes that are worth paying attention to.
Setting exceptions for multiple profiles
There are several enhancements to the Windows Firewall applet interface in the control panel. Previously, when setting up exceptions, that is, specifying which application is allowed to work through the firewall, the settings were saved in the current (currently active) profile. In Windows 7, you can explicitly select one or more profiles to which this exception applies (see Figure 3).

Fig. 3
There is a similar possibility when an alert appears that a certain application is trying to work through the firewall (see Figure 4).

Fig. four
I emphasize that this is exactly the Windows Firewall applet. If you create a rule using Windows Firewall with Advanced Security, then in both Vista and Windows 7, the created rule can be immediately distributed to several profiles.
Enable / disable firewall for profiles
In Windows 7, you can quite easily turn the firewall on or off, as well as notifications about blocking applications for a specific profile or profiles (see Figure 5).

Fig. five
Additional links
With the help of additional links from the Windows Firewall applet in the “seven”, you can quickly go to the Windows Firewall console with Advanced Security, default settings, or a problem resolution tool. This trifle, which usually do not pay attention, helps to save time (Fig. 6.).

Fig. 6
Exceptions for users and computers
When creating rules in Windows Vista, you could use IPSec and specify that connections are allowed for specific users and / or computers. In Windows 7, plus, you can set exceptions for users and / or computers (see Figure 7).

Fig. 7
Port ranges
The last detail I would like to point out is the ability to specify port ranges in the rules now. In Vista, it was possible to specify specific port numbers by separating them with a comma (see Figure 8).

Fig. eight
I also add that for third-party developers, an updated API is available compared to previous versions of the API, which allows, on the one hand, to add its functionality, on the other, to use only the necessary capabilities of the built-in firewall. For example, a developer can implement his firewall management policies, but still rely on built-in IPsec policies.
However, keep in mind that if you turn off Windows Firewall not through the API, but using standard Windows tools (control panel, netsh), then all IPsec policies are turned off. The latter leads to disabling, for example, DirectAccess on the client.
Another feature is related to the ability to configure filters for a virtual account and Service SID. Both of these mechanisms are discussed in detail here .
So, Windows Firewall is evolving with the operating system, responding to no less actively improving security threats.
Without pretending to be a powerful specialized firewall, the Windows Firewall is available out of the box, effectively managed through group policies or scripts and performs its main task - additional protection of the workstation / server from external unwanted network exposure. I think that copes with this task very well. Why not use?
Source: https://habr.com/ru/post/115538/
All Articles