Overview of the information security market of Ukraine
After reviewing several analytical materials that relate to the information security market in Ukraine, we could not unequivocally answer several important questions. Namely: who should be considered a market participant? What problems hinder the development of the market? What are the development prospects for this area? We will try to answer these questions below.
Let's start with the obvious facts - the information security market in Ukraine exists and develops, despite the general unfavorable market situation. In our understanding, participants in the information security (IS) market, in addition to consumers and service providers and solutions, are also Ukrainian and international regulators. More participants can be considered a new for Ukraine segment of information technology risks insurance (the service in Ukraine has just started to develop). Figure 1 shows the structure of the modern information security market of Ukraine.
')
Figure 1. The structure of participants in the information security market of Ukraine
Consider each group of market players in more detail. Let's start with the "dark horse" - insurance of information technology (IT) risks. The basis of IT risk liability insurance is:
* violation of intellectual property rights to information;
* damage or loss of information assets;
* provision of poor quality and unreliable information;
* creation of low-quality information systems or processes and means of their support;
* violation of the processes and rules for the formation of information assets;
* violation of the processes and rules for the preparation, provision and receipt of information products and services, untimely provision of information, or unreasonable refusal to provide information.
The insurers of information risks can be legal entities and individuals whose property interest is associated with the possession, distribution, use and disposal of information or information assets.
Unfortunately, at the moment most of these services are not available on the Ukrainian market (or an attempt to find suppliers of such services turns into a detective story).
With market regulators, the situation is more or less transparent, although to put it mildly ambiguous. Any work, products or services in the field of information security (in the version of the Ukrainian legislation - the sphere of information protection) are subject to licensing. The body acting as a regulator in this area and, accordingly, issuing a license is the State Service for Special Communications and Information Protection in Ukraine (www.dsszzi.gov.ua). The objects of licensing are activities in the field of technical and cryptographic protection of information. This organization is more focused on regulating the protection of information constituting a state secret, or is the property of the state, so the sector of commercial and banking secrecy remains outside the zone of attention of this department.
The issues of ensuring banking secrecy are in the sphere of regulation of the National Bank of Ukraine, which for several years has been very consistently and successfully implementing international approaches to ensuring information security. The only poorly regulated area remains a commercial secret of enterprises. Also some influence on the IS market in Ukraine is exerted by international regulators in the person of the PCI SSC card industry security committee, international exchange structures (requiring compliance with regulatory acts SOX 404, Basel II or international standards ISO 27001, PCI DSS, etc.). We will carry out a more detailed analysis of the regulatory situation in the next issues of the journal.
The providers of information security services and solutions include all companies specializing in the sale and integration of information security products (software and hardware), companies producing products (software and hardware), and audit companies providing information security consulting and consulting services. For Ukraine, a characteristic feature is the fact that highly specialized companies can be counted on the fingers. Basically, the company integrator, offers a product or solution and an information security audit after its implementation, which is fundamentally wrong, since in this case it is an interested party. It is also characteristic that service providers seek to resolve absolutely all issues in the customer's information security field, for example, designing a network intrusion detection system, implement a video surveillance system around the perimeter and simultaneously sell antivirus software. After that, an audit of compliance with information security standards is carried out. This situation is convenient for the consumer, since at first glance it is easier to manage several processes with one supplier, but on the other hand, the lack of control and specialization leads to poor implementation of individual tasks, increased costs and a long implementation period.
There is also a group of services for training or staff development of consumers of information security services. The training services are mainly offered either by consulting specialized companies or by system integrators as an additional service in the framework of implementing information security solutions.
Consumers can be divided by market segments as follows:
* public sector (state enterprises and government bodies, military formations, etc.);
* banking sector (banking and other financial institutions);
* commercial sector (enterprises of various forms of ownership and sectors of the economy).
In the commercial sector, it is necessary to distinguish a subgroup of telecommunication companies, since their activities are regulated and licensed by a separate group of laws and regulations, which often contain specific requirements for ensuring information security. Telecommunication companies should include cellular and fixed-line operators, Internet providers, content providers and other companies whose activities are regulated by the National Commission for Communications Regulation of Ukraine (NCCR).
Let us now try to consider in more detail the main players in the information security market in Figure 2.

Figure 2. Participants in the information security market of Ukraine (option).
So, with the exception of the information risk insurers market, the information security market in Ukraine is basically formed and is developing quite successfully.
Problem Aspects of the Information Security Market of Ukraine
In our opinion, the main problems for the information security market today are:
* backwardness of legislation in matters of regulating the protection of information constituting a commercial secret;
* the psychological problem of the management of most companies (first, the information security incident should be detrimental, and only after that the information protection measures begin);
* the lack of an effective mechanism for assessing the brand (inability to assess the reputational risks for the company);
* unclear segmentation of the IS market and, as a result, non-transparent pricing.
Naturally, in addition to the above, there are several other problematic aspects, but in our opinion these are the most burning ones. Let us dwell on them in more detail.
The legislative and regulatory framework quite transparently regulates issues related to state and bank secrecy. Both regulators clarified and implemented effective information security mechanisms in accountable institutions. At first glance, everything is simple - there is a state secret or confidential information that is the property of the state, so please build a comprehensive information protection system. If you decide to take up banking, the National Bank, through its supervisory authorities, will also verify that your infrastructure complies with its regulations. The National Commission for the Regulation of Communications also puts forward some requirements, mainly for ensuring the continuity of services to its ward operators and providers.
However, the picture is not so rosy if you look at the regulatory field of Ukraine more closely. In a figurative sense, this “field” is abundantly littered with “mines” of legislative traps and entangled with “barbed wire” of contradictions. Most of the regulations, including GOSTs, were adopted in the late 90s and early 2000s and are quite difficult to apply in today's multi-functional environment, which the heads of departments and departments of information security or IT deal with. Some norms have remained unchanged since their approval by the USSR State Technical Commission. Standards for the development and implementation of IT systems and information security systems are also applied without changes since the USSR. Some integrator companies simply ignore their requirements, since the implementation of the system can drag on for years, and young specialists, the main implementers of information security projects, are not even aware of their existence. International standards are recommendatory in Ukraine, which in modern conditions means that if it is not required, it is not necessary.
Here we come close to the psychological aspect of information security. It lies in the inertia of the management of enterprises, since the main task of any business is to earn money. The cost of information security is presented in this case as an investment with an unobvious result (until the thunder clap, the peasant does not cross over). But after earning money, almost no one remembers that the earned money must be saved, and this is one of the main tasks of the information security. Maintaining the required level of confidentiality, integrity and availability of information for business processes are the most important tasks of the information management system.
There is also a certain degree of management misconception that the implementation of IS projects is an additional task of the IT department of the company. In fact, both IT and IS projects cannot be implemented without interfering with the company's management system and / or the company's business processes.
Also, the calmness of management is most likely based on the inability to determine and quantitatively or qualitatively express the company's reputational risks associated with the loss of confidential data or system downtime. A recent example of the iBox instant payment system shows how disruptive a reputation can be for a break in work. Looking at the global trend of threats to information security, you should think, maybe you should not wait until thunder breaks out?
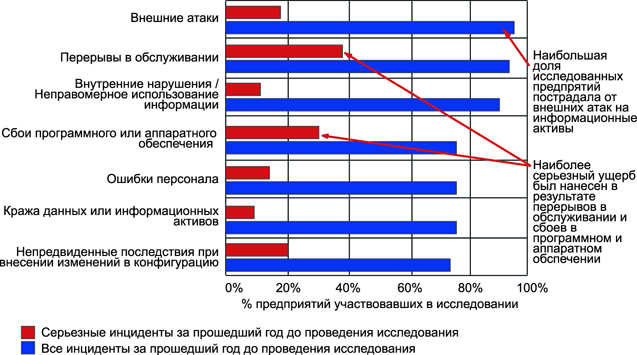
Figure 3. The main threats to IS as of March 2010
(Source Initial consolidated results. Information Security Forum Benchmark.)
And the most important, in our opinion, problem is the lack of segmentation or classification of the information security market. Today, there are several categories of companies offering information security services on the market - these are branches of fairly well-known international companies in the field of information security, local companies with their own capital and, separately, it is also worth highlighting Russian companies. As a result of such a representative composition, prices for the same services can be quite different. On the other hand, most of the decisions in the field of information security are unique and it is impossible to tell the exact amount before executing the project as at the exit from the supermarket. However, the practice of clear and transparent pricing has been adopted all over the world, based on various factors that are relatively problematic in Ukraine, as long as all companies act on their own without any coordination from regulators or a trade union.
It adds confusion and the fact that many IT integrators or related fields implement products and services in the field of information security. At the same time, this business is not their core business, and the quality of implementation leaves much to be desired.
Strange as it may sound, but 2010 and 2011 are crucial for our market in the field of information security. First of all, thanks to the initiative of the National Bank of Ukraine, which is preparing the adoption of an industry standard based on the provisions of the international standard ISO 27001. Thus, the banking sector will get even more transparent rules of the game, and the IS service providers will have new opportunities to implement projects. In addition, the influence of global trends to neutralize information security threats is increasing, since Ukraine cannot remain a weak link in the global information community. It is expected that foreign investors and international institutions will be under pressure to reduce the likelihood of major IS threats.
It is also obvious that the implementation of projects in the field of information security will be mainly carried out by professional companies specializing in a narrow area of information security. Managers and IT directors of companies will be guided by the paradigm: "risk assessment - information security audit - introduction of products and measures based on audit results - certification for compliance with the standard." We hope that the formula “something needs to be done, let's buy the firewall (antivirus, UTM, spam filter ...) underline the necessary” will sink into oblivion.
Information security market structure
Let's start with the obvious facts - the information security market in Ukraine exists and develops, despite the general unfavorable market situation. In our understanding, participants in the information security (IS) market, in addition to consumers and service providers and solutions, are also Ukrainian and international regulators. More participants can be considered a new for Ukraine segment of information technology risks insurance (the service in Ukraine has just started to develop). Figure 1 shows the structure of the modern information security market of Ukraine.

')
Figure 1. The structure of participants in the information security market of Ukraine
Consider each group of market players in more detail. Let's start with the "dark horse" - insurance of information technology (IT) risks. The basis of IT risk liability insurance is:
* violation of intellectual property rights to information;
* damage or loss of information assets;
* provision of poor quality and unreliable information;
* creation of low-quality information systems or processes and means of their support;
* violation of the processes and rules for the formation of information assets;
* violation of the processes and rules for the preparation, provision and receipt of information products and services, untimely provision of information, or unreasonable refusal to provide information.
The insurers of information risks can be legal entities and individuals whose property interest is associated with the possession, distribution, use and disposal of information or information assets.
Unfortunately, at the moment most of these services are not available on the Ukrainian market (or an attempt to find suppliers of such services turns into a detective story).
With market regulators, the situation is more or less transparent, although to put it mildly ambiguous. Any work, products or services in the field of information security (in the version of the Ukrainian legislation - the sphere of information protection) are subject to licensing. The body acting as a regulator in this area and, accordingly, issuing a license is the State Service for Special Communications and Information Protection in Ukraine (www.dsszzi.gov.ua). The objects of licensing are activities in the field of technical and cryptographic protection of information. This organization is more focused on regulating the protection of information constituting a state secret, or is the property of the state, so the sector of commercial and banking secrecy remains outside the zone of attention of this department.
The issues of ensuring banking secrecy are in the sphere of regulation of the National Bank of Ukraine, which for several years has been very consistently and successfully implementing international approaches to ensuring information security. The only poorly regulated area remains a commercial secret of enterprises. Also some influence on the IS market in Ukraine is exerted by international regulators in the person of the PCI SSC card industry security committee, international exchange structures (requiring compliance with regulatory acts SOX 404, Basel II or international standards ISO 27001, PCI DSS, etc.). We will carry out a more detailed analysis of the regulatory situation in the next issues of the journal.
The providers of information security services and solutions include all companies specializing in the sale and integration of information security products (software and hardware), companies producing products (software and hardware), and audit companies providing information security consulting and consulting services. For Ukraine, a characteristic feature is the fact that highly specialized companies can be counted on the fingers. Basically, the company integrator, offers a product or solution and an information security audit after its implementation, which is fundamentally wrong, since in this case it is an interested party. It is also characteristic that service providers seek to resolve absolutely all issues in the customer's information security field, for example, designing a network intrusion detection system, implement a video surveillance system around the perimeter and simultaneously sell antivirus software. After that, an audit of compliance with information security standards is carried out. This situation is convenient for the consumer, since at first glance it is easier to manage several processes with one supplier, but on the other hand, the lack of control and specialization leads to poor implementation of individual tasks, increased costs and a long implementation period.
There is also a group of services for training or staff development of consumers of information security services. The training services are mainly offered either by consulting specialized companies or by system integrators as an additional service in the framework of implementing information security solutions.
Consumers can be divided by market segments as follows:
* public sector (state enterprises and government bodies, military formations, etc.);
* banking sector (banking and other financial institutions);
* commercial sector (enterprises of various forms of ownership and sectors of the economy).
In the commercial sector, it is necessary to distinguish a subgroup of telecommunication companies, since their activities are regulated and licensed by a separate group of laws and regulations, which often contain specific requirements for ensuring information security. Telecommunication companies should include cellular and fixed-line operators, Internet providers, content providers and other companies whose activities are regulated by the National Commission for Communications Regulation of Ukraine (NCCR).
Let us now try to consider in more detail the main players in the information security market in Figure 2.

Figure 2. Participants in the information security market of Ukraine (option).
So, with the exception of the information risk insurers market, the information security market in Ukraine is basically formed and is developing quite successfully.
Problem Aspects of the Information Security Market of Ukraine
In our opinion, the main problems for the information security market today are:
* backwardness of legislation in matters of regulating the protection of information constituting a commercial secret;
* the psychological problem of the management of most companies (first, the information security incident should be detrimental, and only after that the information protection measures begin);
* the lack of an effective mechanism for assessing the brand (inability to assess the reputational risks for the company);
* unclear segmentation of the IS market and, as a result, non-transparent pricing.
Naturally, in addition to the above, there are several other problematic aspects, but in our opinion these are the most burning ones. Let us dwell on them in more detail.
The legislative and regulatory framework quite transparently regulates issues related to state and bank secrecy. Both regulators clarified and implemented effective information security mechanisms in accountable institutions. At first glance, everything is simple - there is a state secret or confidential information that is the property of the state, so please build a comprehensive information protection system. If you decide to take up banking, the National Bank, through its supervisory authorities, will also verify that your infrastructure complies with its regulations. The National Commission for the Regulation of Communications also puts forward some requirements, mainly for ensuring the continuity of services to its ward operators and providers.
However, the picture is not so rosy if you look at the regulatory field of Ukraine more closely. In a figurative sense, this “field” is abundantly littered with “mines” of legislative traps and entangled with “barbed wire” of contradictions. Most of the regulations, including GOSTs, were adopted in the late 90s and early 2000s and are quite difficult to apply in today's multi-functional environment, which the heads of departments and departments of information security or IT deal with. Some norms have remained unchanged since their approval by the USSR State Technical Commission. Standards for the development and implementation of IT systems and information security systems are also applied without changes since the USSR. Some integrator companies simply ignore their requirements, since the implementation of the system can drag on for years, and young specialists, the main implementers of information security projects, are not even aware of their existence. International standards are recommendatory in Ukraine, which in modern conditions means that if it is not required, it is not necessary.
Here we come close to the psychological aspect of information security. It lies in the inertia of the management of enterprises, since the main task of any business is to earn money. The cost of information security is presented in this case as an investment with an unobvious result (until the thunder clap, the peasant does not cross over). But after earning money, almost no one remembers that the earned money must be saved, and this is one of the main tasks of the information security. Maintaining the required level of confidentiality, integrity and availability of information for business processes are the most important tasks of the information management system.
There is also a certain degree of management misconception that the implementation of IS projects is an additional task of the IT department of the company. In fact, both IT and IS projects cannot be implemented without interfering with the company's management system and / or the company's business processes.
Also, the calmness of management is most likely based on the inability to determine and quantitatively or qualitatively express the company's reputational risks associated with the loss of confidential data or system downtime. A recent example of the iBox instant payment system shows how disruptive a reputation can be for a break in work. Looking at the global trend of threats to information security, you should think, maybe you should not wait until thunder breaks out?

Figure 3. The main threats to IS as of March 2010
(Source Initial consolidated results. Information Security Forum Benchmark.)
And the most important, in our opinion, problem is the lack of segmentation or classification of the information security market. Today, there are several categories of companies offering information security services on the market - these are branches of fairly well-known international companies in the field of information security, local companies with their own capital and, separately, it is also worth highlighting Russian companies. As a result of such a representative composition, prices for the same services can be quite different. On the other hand, most of the decisions in the field of information security are unique and it is impossible to tell the exact amount before executing the project as at the exit from the supermarket. However, the practice of clear and transparent pricing has been adopted all over the world, based on various factors that are relatively problematic in Ukraine, as long as all companies act on their own without any coordination from regulators or a trade union.
It adds confusion and the fact that many IT integrators or related fields implement products and services in the field of information security. At the same time, this business is not their core business, and the quality of implementation leaves much to be desired.
Prospects for the development of information security market
Strange as it may sound, but 2010 and 2011 are crucial for our market in the field of information security. First of all, thanks to the initiative of the National Bank of Ukraine, which is preparing the adoption of an industry standard based on the provisions of the international standard ISO 27001. Thus, the banking sector will get even more transparent rules of the game, and the IS service providers will have new opportunities to implement projects. In addition, the influence of global trends to neutralize information security threats is increasing, since Ukraine cannot remain a weak link in the global information community. It is expected that foreign investors and international institutions will be under pressure to reduce the likelihood of major IS threats.
It is also obvious that the implementation of projects in the field of information security will be mainly carried out by professional companies specializing in a narrow area of information security. Managers and IT directors of companies will be guided by the paradigm: "risk assessment - information security audit - introduction of products and measures based on audit results - certification for compliance with the standard." We hope that the formula “something needs to be done, let's buy the firewall (antivirus, UTM, spam filter ...) underline the necessary” will sink into oblivion.
Source: https://habr.com/ru/post/111558/
All Articles