Anonymous channel as a means of improving the existing e-voting protocol
As a prototype, the e-voting system, which was used in Estonia in elections to local government bodies in 2005, was considered. On Habré there is already material about the Estonian elections. For example, here . There was an article about the Estonian ID card that was used to participate in the elections. But I did not find the material about the e-voting scheme itself, but it is quite interesting, although it has flaws. I would like to present you this scheme and show how this important property for the e-voting system can be improved, such as the anonymity of voters. But first things first.
Details about it can be read here .
In order to participate in elections, the voter must have an identification smart card. At that time (August 2005), more than 800,000 ID cards were issued, which made it possible to provide them with the majority of the electorate. (The identification smart card is a kind of electronic passport.)
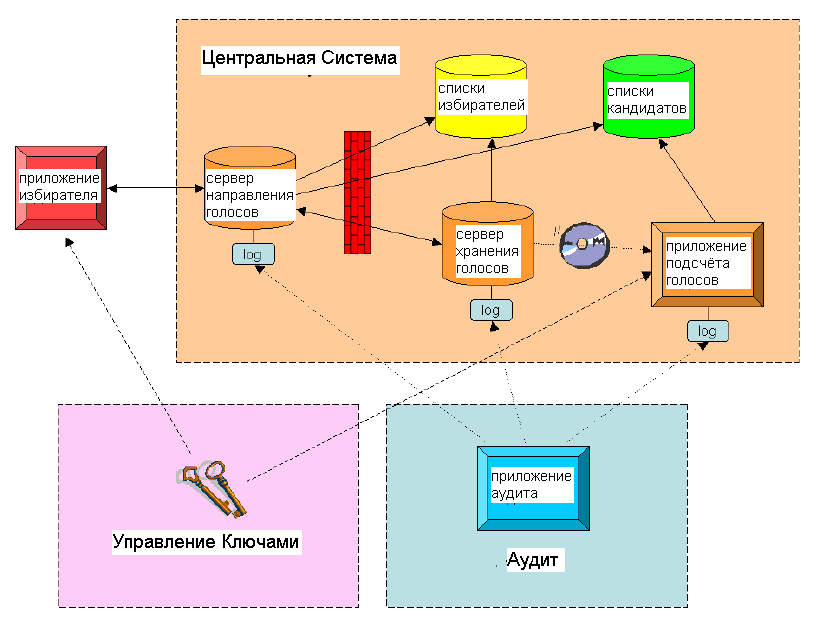
The voting process is as follows (the scheme is presented above):
1. A voter, through the HTTPS protocol, gains access to the Voice Redirect Server (LNG) and authenticates his identity with an identification card.
2. The LNG sends a request to the voter database using the voter’s personal identification code (LIC) and receives information about its membership in a specific electoral district. If the voter does not have the right to vote, a corresponding message is displayed and he / she is sent to the X-tee service provided by the Population Accounting System, where the voter can check his status in relation to the right to vote.
3. The LNG requests the Voice Storage Server (SHS) for information on whether the voter has already voted. If the answer is yes, then the voter is informed about it.
4. The LNG sends a request using data from the voter database, and receives a list of candidates from the constituency to which the voter belongs. This list is displayed on the screen of the voter.
5. The voter selects the candidate.
6. The voter application asks you to confirm his / her choice.
7. The application encrypts the voice and a random number with the public key of the Votes Count (GPR) application. The voter signs the cryptogram (hereinafter: the voice) with his digital signature.
8. The voter's application program transmits an envelope, signed with an electronic signature, to the LNG, which verifies the formal correctness of the material received and whether the person who certified his identity at the beginning of the session, put the digital signature.
9. LNG sends the received vote to the VSS. The VSS gains access to the validation confirmation server and receives a certificate confirming the validity of the digital signature, which is then added to the confirmed voice.
10. If the procedure is successful, the VSS sends the LNG confirmation that a vote has been received. A corresponding message is also delivered to the voter. A record is made in the system log in the form [LIC, Hash] that a voice is received.
11. A voter may vote several times. However, only the result of the last vote is taken into account. All votes are transmitted through LNG in the VSS.
12. After the end of the electronic voting, the LNG stops all information transfer processes.
13. Repeat voices removed. Voices are sorted by county. The necessary entries are made in the system logbook.
14. Voices and digital signature are separated. (The digital signature must be stored separately.)
15. Voices are sent to BTS.
16. The votes are counted in the BCP.
This e-voting protocol does not, however, ensure complete anonymity of the voting results, since this is based on the integrity of the election commission.
This protocol can be significantly improved by using the concept of an anonymous channel that is embedded between the VSS and the BCP.
')
We will use an anonymous channel, which will be an improved anonymous channel Schaum. Read more about it here .
An anonymous channel is a sequence of k servers. We will call them MIX servers. Each such server has a pair of keys (public and private).
Used by the El-Gamal Cop. The changes concern the 7th and 15th stages of the voting protocol.
1. At the 7th stage, the voter first encodes his voice on the public key of the VCA. Then it is sequentially encrypted on the public keys of all MIX servers.
2. At the 15th stage, the cryptograms are transmitted to the BCP via an anonymous channel.
Each server from the anonymous channel accepts a list of cryptograms at the entrance. It then decrypts them using its secret key and sends the result in lexicographical order to the next server. At the end of this procedure, a list of votes encrypted in the public key of the GPR is compiled in an intermixed order. In this case, the relationship is hidden between the voter and his voice, due to the fact that it is impossible to establish relationships between the input and output data of the servers, if at least one of them is “fair”. The greater the number of servers k used in the protocol, the less likely the violation of the secrecy of the vote.
1. Efficient Anonymous Channel and All Nothing Election Scheme
2. NIK of Estonia. E-voting system overview
3. Estonian ID card
Transferred from the "Future is here" to be visible not only to subscribers of the blog. I hope it will be interesting to someone in this blog.
Estonian e-voting scheme
Details about it can be read here .
In order to participate in elections, the voter must have an identification smart card. At that time (August 2005), more than 800,000 ID cards were issued, which made it possible to provide them with the majority of the electorate. (The identification smart card is a kind of electronic passport.)

The voting process is as follows (the scheme is presented above):
1. A voter, through the HTTPS protocol, gains access to the Voice Redirect Server (LNG) and authenticates his identity with an identification card.
2. The LNG sends a request to the voter database using the voter’s personal identification code (LIC) and receives information about its membership in a specific electoral district. If the voter does not have the right to vote, a corresponding message is displayed and he / she is sent to the X-tee service provided by the Population Accounting System, where the voter can check his status in relation to the right to vote.
3. The LNG requests the Voice Storage Server (SHS) for information on whether the voter has already voted. If the answer is yes, then the voter is informed about it.
4. The LNG sends a request using data from the voter database, and receives a list of candidates from the constituency to which the voter belongs. This list is displayed on the screen of the voter.
5. The voter selects the candidate.
6. The voter application asks you to confirm his / her choice.
7. The application encrypts the voice and a random number with the public key of the Votes Count (GPR) application. The voter signs the cryptogram (hereinafter: the voice) with his digital signature.
8. The voter's application program transmits an envelope, signed with an electronic signature, to the LNG, which verifies the formal correctness of the material received and whether the person who certified his identity at the beginning of the session, put the digital signature.
9. LNG sends the received vote to the VSS. The VSS gains access to the validation confirmation server and receives a certificate confirming the validity of the digital signature, which is then added to the confirmed voice.
10. If the procedure is successful, the VSS sends the LNG confirmation that a vote has been received. A corresponding message is also delivered to the voter. A record is made in the system log in the form [LIC, Hash] that a voice is received.
11. A voter may vote several times. However, only the result of the last vote is taken into account. All votes are transmitted through LNG in the VSS.
12. After the end of the electronic voting, the LNG stops all information transfer processes.
13. Repeat voices removed. Voices are sorted by county. The necessary entries are made in the system logbook.
14. Voices and digital signature are separated. (The digital signature must be stored separately.)
15. Voices are sent to BTS.
16. The votes are counted in the BCP.
This e-voting protocol does not, however, ensure complete anonymity of the voting results, since this is based on the integrity of the election commission.
This protocol can be significantly improved by using the concept of an anonymous channel that is embedded between the VSS and the BCP.
')
Anonymous channel
We will use an anonymous channel, which will be an improved anonymous channel Schaum. Read more about it here .
An anonymous channel is a sequence of k servers. We will call them MIX servers. Each such server has a pair of keys (public and private).
Used by the El-Gamal Cop. The changes concern the 7th and 15th stages of the voting protocol.
1. At the 7th stage, the voter first encodes his voice on the public key of the VCA. Then it is sequentially encrypted on the public keys of all MIX servers.
2. At the 15th stage, the cryptograms are transmitted to the BCP via an anonymous channel.
Each server from the anonymous channel accepts a list of cryptograms at the entrance. It then decrypts them using its secret key and sends the result in lexicographical order to the next server. At the end of this procedure, a list of votes encrypted in the public key of the GPR is compiled in an intermixed order. In this case, the relationship is hidden between the voter and his voice, due to the fact that it is impossible to establish relationships between the input and output data of the servers, if at least one of them is “fair”. The greater the number of servers k used in the protocol, the less likely the violation of the secrecy of the vote.
Sources used
1. Efficient Anonymous Channel and All Nothing Election Scheme
2. NIK of Estonia. E-voting system overview
3. Estonian ID card
Transferred from the "Future is here" to be visible not only to subscribers of the blog. I hope it will be interesting to someone in this blog.
Source: https://habr.com/ru/post/111526/
All Articles