Sandbox Wars - Part 1
A warning
The article describes the adventures of a friend of mine .
Prehistory
Events take place in the days of the
I lived in a student dormitory in the same room with a first-year neighbor, who, like me, studied at the VMC and was interested in information technology. For definiteness, I will call him N.
')
He loved this comrade to engage in minor network hooliganism, such as finding someone to have a simple password for VKontakte and changing the avatar, or writing something vulgar in the status. I did not approve of it, but did nothing. In addition, he had less theoretical knowledge than is needed for such actions, so he used at most ready-made programs, with a poor understanding of how they work - I did not approve of it even more.
I myself was not a guru either, but at least I tried to study theory before using the “magic” scripts and programs. Well, and directed his activities more in a constructive, not destructive way.
And I considered myself to be sufficiently protected from network attacks, because I know the basics of computer literacy, I don’t put my date of birth or phone number as passwords, I update the OS in time, I don’t launch anything from the Internet.
And then, one day, he sends me an email and slyly lybitsya. And in the letter is a file, and in the file is a label with the majority of my passwords. The most valuable passwords (to mail and domains) were not there, but I still have batthert, because how is it - I did everything right, and here is such a failure, and I do not even know where I have a problem, and what needs to be fixed ! I ask him, he refuses to explain where and how he got them.
The analysis showed that the set of passwords sent to me coincides with the set of passwords stored in Opera Wand, I put the master password on Wand in the opera. I change all the passwords, download the Cure It Live CD, reboot the computer, run a full scan. Night passes - no viruses detected. I download a similar product from the Kaspersky Lab - the result is the same. The idea comes that he could use the Live CD to steal the wand.dat - the disk is not encrypted. N says that I didn’t guess, but just in case I put the password in the BIOS to boot and to change the boot media. A terrible revenge plan is born in my head (especially since my hands were itching for a long time to do something like that, but they were holding back moral standards - and there seems to be an excuse: "he first began"). I record a Live CD with some kind of mini-Linux, I test it on my computer, everything works. I google an arrangement of key files of Windows.
The next day, while N is taking the exam, I close in the room, boot up his PC from the Live CD prepared on the eve. I copy the% AppData% directory to my USB flash drive, I also copy the SAM and SYSTEM registry files, and turn off the PC.
On my computer, I decipher the passwords from his Opera Wand, the password from the mail is also there. One of them coincides with his password on the entrance to Windows.
Also in the mailbox using the search for the words “password”, “password” I find the passwords from the services that send the password in the open form to the mail after each change.
I am writing him a response letter with his passwords. After a short time, I get disconnected from ICQ and Jabber. Realizing that he also has a database of my Miranda, I recover passwords for all used IM protocols, and I put a base encryption plugin for Miranda.
After several hours of negotiations, agree on the exchange of information about the methods of "hacking". It turned out that a few weeks ago, while I was away from the computer, I copied my% APPDATA% onto a USB flash drive. And that day I decided to go through this directory with decoder programs. It turned out that while I was considering some complicated options, he just picked up and copied the directory - where is it much easier? Since then, my computer is blocked after two minutes of inactivity, as well as manually, when I do not forget.
This incident had no effect on good-neighborly relations, since no one used other people's passwords for bad purposes, and both of them only got too much experience. In addition, they agreed not to use physical access to the neighbor’s computer in the future, because it will no longer bring experience, and protecting the PC from physical access is already beyond what we are interested in.
Story
A month has passed. And again, I see how N learned the password from the email of his classmate, and, with worthy use of perseverance, resets her password to a contact and writes everything on her behalf on the wall, in messages to friends, etc. She recovers VKontakte password via mail, and he changes it back. She doesn’t guess the password to change the mail (there’s no excuse for this either).
And my hands were itching again to do something bad, and here again there is a moral justification - N himself offends the illiterate, it means that if I get access to his passwords, there will be nothing bad in it.
Since we agreed not to use physical access to the computer, and also because it would not be interesting to repeat the focus from the Live CD, we need a less trivial way.
A glance falls on a pair of switches and a bunch of wires through which the Internet works in our room.
Network infrastructure modification
Initially, the network configuration was as follows:
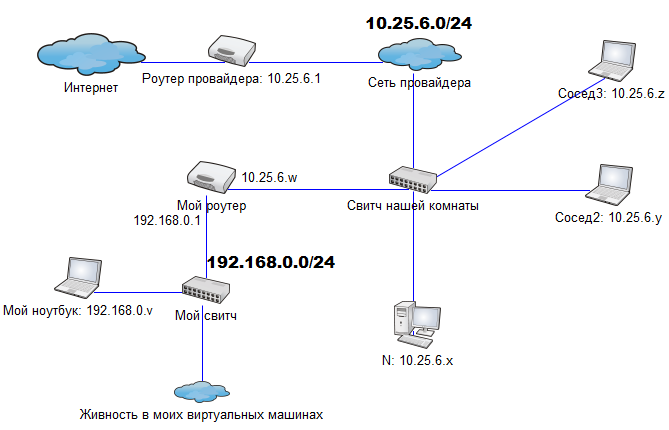
IP addresses are static, N goes to the Internet through the gateway 10.25.6.1. I am sitting at a separate router for experiments. Thus, I have a network of 192.168.0.0/24 to host the necessary machines.
First of all, you need a router that will be used by the victim instead of the provider. Of course, there is no possibility to single out a separate machine, so I do everything in VirtualBox.
The internal IP address for the virtual router will be 10.25.6.1 (since the victim will connect to this address), what to do with the external one? It cannot receive the Internet from the provider router, so then the address ranges of the external and internal networks will be the same. Let the external interface connect it to my private network: 192.168.0.0/24.
In summary: Debian is installed in Debian, the internal interface address is 10.25.6.1, the external one is 192.168.0.u. We configure NAT on it.
Since there is actually only one network adapter on the laptop inside which VirtualBox is running, you'll have to cheat. In the virtual machine settings, we will bridge both virtual machine interfaces with a single real machine interface. Thus, two logical networks now coexist in the same hardware segment: 192.168.0.0/24 and fake 10.25.6.0/24. On an ongoing basis, this is not worth doing, but in this case nothing terrible happened.
We also create another virtual machine, which will play the role of the victim until everything is debugged, we also connect it to the same internal network in bridge mode.
Now the network looks like this (the red arrows show the packet route from the virtual victim to the Internet):
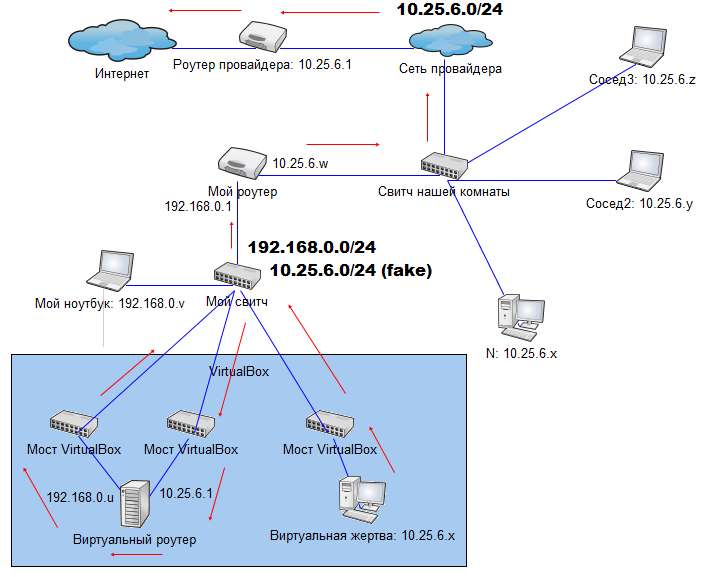
For a real victim, instead of the first two arrows, there will be one arrow directly to the switch - this will happen if you switch the wire N from the room switch to your own, and the victim will notice only a short break in communication.
You can see a lot of things at once, for which networkers will probably hang me:
- One switch is used in two logical networks, and, as a result, the packet passes through this switch twice. That is, the path with self-intersection is obtained.
- The package, during its journey, passes through two different networks 10.25.6.0/24, first through the fake network, then through the real
- traceroute from the victim to any server on the Internet will show the address 10.25.6.1 twice, an extremely unusual situation
To check, we run on the victim vkontakte.ru, on the tcpdump router, and see the following:
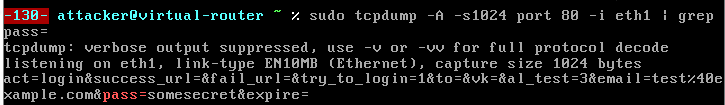
Turning off the victim virtual machine, switching the cable N from the main switch to your own one, in a few seconds we get VKontakte cookies. Having entered the cookies into your browser, we end the session (here you could behave more carefully, but to hell with it!). A few minutes later the password from VKontakte is received.
Network layout in a “combat” state:
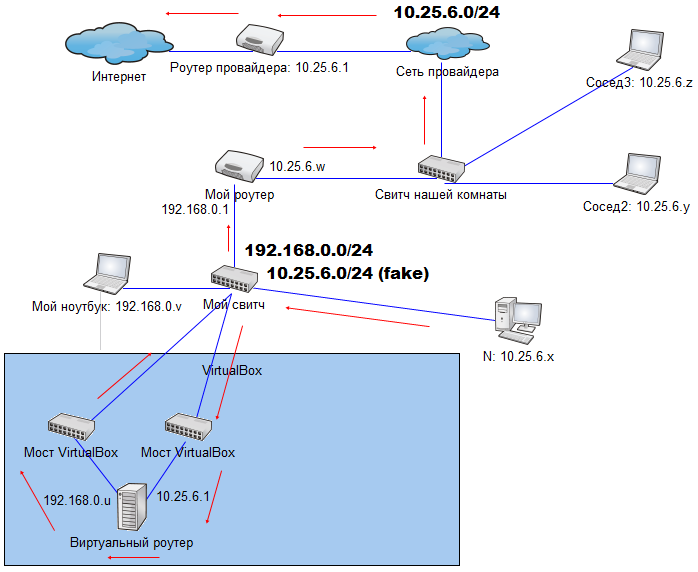
But just listening to the traffic will not do anything, most sites transmit passwords via https protocol, so the maximum that I get is a password from VKontakte, which he will then recover via email, something more interesting is needed.
findings
- use the BIOS password, or data encryption on the hard drive (TrueCrypt)
- short time to turn on the computer lock on inactivity
- Webmasters: do not transmit important data via http, use encryption. Durov, do you hear?
- Users: do not use sites that transmit your passwords via http
- Do not be “bad guys”, maybe your neighbor is just waiting for a reason
Continuation
HTTPS bypass
Source: https://habr.com/ru/post/111489/
All Articles