The option of remote access to the corporate network of the enterprise through a VPN with access control to internal resources and authentication in AD
Often (if not always), the IT department sooner or later faces the task of organizing remote access to the enterprise network, for example, seconded employees or simply sick. You can solve this problem in different ways. I want to tell about one of the solutions actually used in our holding. This solution differs from many others in three main things:
If it is interesting to you, welcome under kat
')
So, first I’ll tell you what we need, in fact, these are just two things:
We have both servers - regular virtual machines deployed on hyper-v.
You will also need two free subnets (I think this is enough for everyone) - for what it’s two, I’ll tell you further.
User access to end resources can be divided conditionally into three stages:
Below is a general wiring diagram and description of the stages.
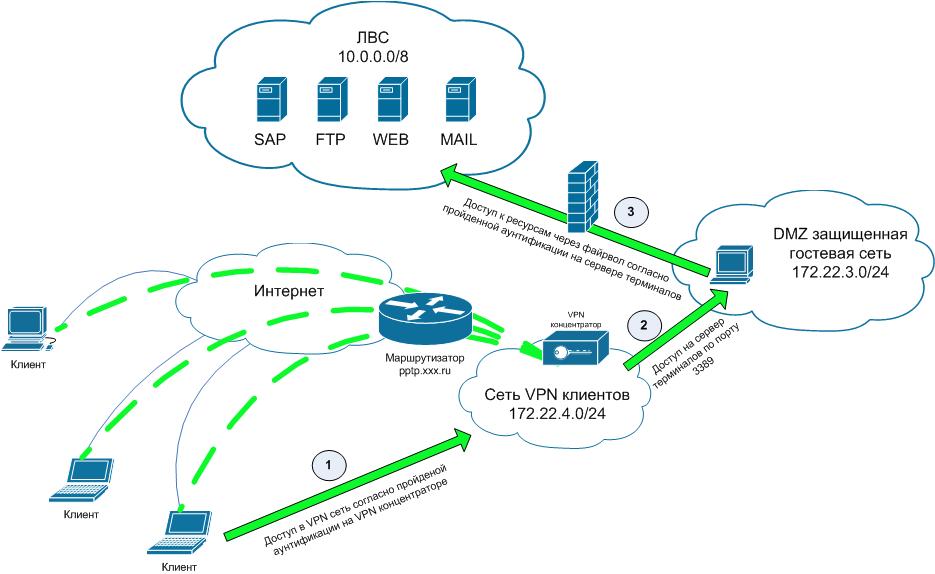
To implement this, we need any pptp server, we use cisco, but nothing prevents the forwarding of pptp from the border router / firewall to the same TMG \ ISA, which we will use to access clients to resources and raise the pptp server on it. Here is a piece of our pussy config, responsible for pptp.
The key point at this stage is the organization of a network of vpn-clients with the possibility of connecting from it ONLY to a terminal server on the rdp port.
So, our client has connected to the pptp server and has access to the terminal server, then using the remote desktop it connects to the terminal server, the credentials for this connection are the domain user account. Here it is necessary to explain a little:
In AD, security groups are created according to the mask, roughly speaking, we have for example four groups of resources, let's say, divided into projects. Project1, Project2, Project3 and general. Accordingly, in AD, we will create 4 security groups and make the first three members of the “common” group. We will enable the “common” group to log in to the terminal server. Further, to enable remote access to any AD user, we will simply add it to the appropriate group.
To implement this stage, we will need to configure TMG \ ISA, when writing this article I did not plan it as a clear instruction for action, but only as a description of the scheme, so I will not go into the details of setting up a firewall, I’ll note only a few key points.
In general, this is all that I wanted to share, I understand that everything is set out rather briefly, but the purpose of the article is to show one of the solutions, and not its concrete implementation, much can be done differently here.
- On the remote user side, minimum settings are required - all standard applications and features of Windows OS are used;
- The remote user works on the terminal server, which provides him with the necessary environment to perform his official duties.
- Very flexible access control to the company's internal resources (provided by TMG \ ISA firewall according to domain authentication)
If it is interesting to you, welcome under kat
')
So, first I’ll tell you what we need, in fact, these are just two things:
- Server with TMG or ISA
- Terminal server
We have both servers - regular virtual machines deployed on hyper-v.
You will also need two free subnets (I think this is enough for everyone) - for what it’s two, I’ll tell you further.
User access to end resources can be divided conditionally into three stages:
- Access via pptp to an isolated vpn client network
- Rdp access to terminal server
- Direct access from the terminal server to the company's LAN resources using any access mask
Below is a general wiring diagram and description of the stages.

Access via pptp to an isolated vpn client network
To implement this, we need any pptp server, we use cisco, but nothing prevents the forwarding of pptp from the border router / firewall to the same TMG \ ISA, which we will use to access clients to resources and raise the pptp server on it. Here is a piece of our pussy config, responsible for pptp.
vpdn enable
!
vpdn-group 1
! Default PPTP VPDN group
accept-dialin
protocol pptp
virtual-template 1
ip pmtu
ip mtu adjust
username ras_user password 7 010157010906550075581B0C4F044011530F5D2F7A743B62643
14255
username ras_guest password 7 120B541640185F3B7E2C713D653075005F025A
interface GigabitEthernet0/0.3
description Internet
encapsulation dot1Q 3
ip address xxxx 255.255.255.252
ip nat outside
ip virtual-reassembly max-fragments 64 max-reassemblies 256
ip policy route-map Internet-10-144-68
no cdp enable
interface Virtual-Template1
mtu 1400
ip unnumbered GigabitEthernet0/0.3
ip access-group 170 in
ip tcp adjust-mss 1360
peer default ip address pool vpn_users
no keepalive
ppp encrypt mppe auto
ppp authentication ms-chap-v2
ppp ipcp dns 172.22.1.201
!
ip local pool vpn_users 172.22.4.1 172.22.4.250
access-list 170 permit udp 172.22.4.0 0.0.0.255 host 172.22.1.201 eq domain
access-list 170 permit tcp 172.22.4.0 0.0.0.255 host 172.22.3.1 eq 3389
access-list 170 permit icmp any any
access-list 170 permit tcp 172.22.4.0 0.0.0.255 host 172.22.3.1 eq wwwThe key point at this stage is the organization of a network of vpn-clients with the possibility of connecting from it ONLY to a terminal server on the rdp port.
Rdp access to terminal server
So, our client has connected to the pptp server and has access to the terminal server, then using the remote desktop it connects to the terminal server, the credentials for this connection are the domain user account. Here it is necessary to explain a little:
In AD, security groups are created according to the mask, roughly speaking, we have for example four groups of resources, let's say, divided into projects. Project1, Project2, Project3 and general. Accordingly, in AD, we will create 4 security groups and make the first three members of the “common” group. We will enable the “common” group to log in to the terminal server. Further, to enable remote access to any AD user, we will simply add it to the appropriate group.
Direct access from the terminal server to the company's LAN resources using any access mask
To implement this stage, we will need to configure TMG \ ISA, when writing this article I did not plan it as a clear instruction for action, but only as a description of the scheme, so I will not go into the details of setting up a firewall, I’ll note only a few key points.
- In TMG, the external network will be our LAN.
- The internal network will be a network with a terminal server.
- The TMG \ ISA client MUST be installed on the terminal server so that we can bind the rules to users.
- Accordingly, all the rules in the firewall are tied to the previously created security groups Project1, Project2, Project3 and general.
In general, this is all that I wanted to share, I understand that everything is set out rather briefly, but the purpose of the article is to show one of the solutions, and not its concrete implementation, much can be done differently here.
Source: https://habr.com/ru/post/111215/
All Articles