Compile and securely execute code on the fly
Problem
In your application, you need to execute code that is not known at the compilation of the application. It can be a variety of plugins, extensions, calculations, etc.
Decision
.NET allows you to compile and execute code. Moreover, the code can be executed safely by narrowing the range of resources that the executable code can use.
')
Implementation
To compile, we need CodeDomProvider, with which you can instantiate a compiler instance for any .NET language. Let's go to the code.
- private string EvalCode ( string typeName, string methodName, string sourceCode )
- {
- string output = ":)" ;
- var compiler = CodeDomProvider. CreateProvider ( "CSharp" ) ;
- var parameters = new CompilerParameters
- {
- CompilerOptions = "/ t: library" ,
- GenerateInMemory = true
- IncludeDebugInformation = true
- } ;
- var results = compiler. CompileAssemblyFromSource ( parameters, sourceCode ) ;
- if ( ! results. Errors . HasErrors )
- {
- var assembly = results. CompiledAssembly ;
- var evaluatorType = assembly. GetType ( typeName ) ;
- var evaluator = Activator. CreateInstance ( evaluatorType ) ;
- output = ( string ) InvokeMethod ( evaluatorType, methodName, evaluator, new object [ ] { output } ) ;
- return output ;
- }
- output = " \ r \ n Houston, we have a problem at compile time!" ;
- return results. Errors . Cast < CompilerError > ( ) . Aggregate ( output, ( current, ce ) => current + string . Format ( " \ r \ n line {0}: {1}" , ce. Line , ce. ErrorText ) ) ;
- }
- [ FileIOPermission ( SecurityAction. Deny , Unrestricted = true ) ]
- private object InvokeMethod ( Type evaluatorType, string methodName, object evaluator, object [ ] methodParams )
- {
- return evaluatorType. InvokeMember ( methodName, System. Reflection . BindingFlags . InvokeMethod , null , evaluator, methodParams ) ;
- }
As you can see, there is nothing supernatural. We create a compiler, pass the code into it, we get a DLL. With the help of reflection we launch the necessary method.
Code in action:
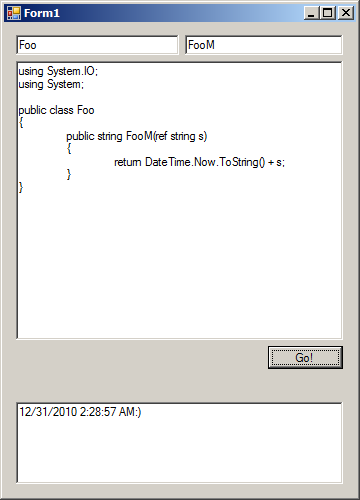
Line 27 is interesting. With it, you can limit the rights that the code has (not only dynamic). In .NET there is a mechanism of Code Access Security , through which you can manage the security of executable code.
Security error while attempting to write to disk:

Despite the fact that code execution looks very “harmless”, it is worth remembering that this is a very resource-intensive process. For example, if you execute code in the current application domain (as it was done in the demo), if the application runs for a long time, the memory may simply end (.NET cannot unload assemblies from the domain).
Demo:
DynDllFunWf.zip
Source: https://habr.com/ru/post/110999/
All Articles