OpenWRT + Asus WL 520GU + Iptables. We separate LAN, DMZ and Internet
Hello!
Just now there was a need to hide some service in the DMZ. This service runs in W2K3, and I didn’t want the OS Windows machine to look into the Internet and the local network than anything unprotected (“Windows” firewalls just go through the forest).
Remembering the successful experience with Asus WL 520GU and DD-WRT, I decided to take the beaten track, but chose OpenWRT as the firmware for the router.
Scheme of the ligament can be seen in the figure.
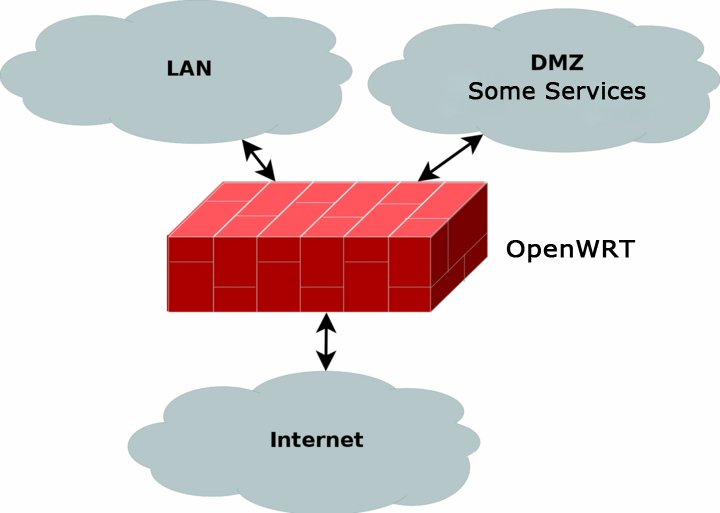
So, from the words get down to business.
Some misunderstanding of the term DMZ was noticed in the comments.
In this connection, I will quote from Wikipedia (for opponents of such quoting, I can see that this material is almost identical to what is written in the book Complete Reference Book on Cisco )
DMZ (Demilitarized Zone, DMZ) is an information perimeter protection technology in which servers responding to requests from an external network are located in a specific network segment (which is called a DMZ) and are restricted in accessing the main network segments using a firewall (firewall ), in order to minimize the damage, when hacking one of the publicly available services located in the DMZ.
For the model I have chosen, the backfire.brcm47xx firmware is required.
1. Perform a hardware reset, the so-called 30/30/30.
When the power of the router is on, press the reset button, hold for 30 seconds, without releasing the button, turn off the power and hold for another 30 seconds, without releasing the button, turn on the power and hold the reset button again for 30 seconds.
Hint: the default ip of the router is 192.168.1.1. If you ping it before a hardware reset of 30/30/30, then ttl will be equal to 64, after resetting ttl becomes equal to 100.
Now send the firmware to the router using the following command
Upon completion of the message melting, wait for 5 minutes and turn off / turn on the power router.
The next step is to set the root password and disable unnecessary services, for this we go to the web interface of the router
192.168.1.1
I disabled luci_dhcp_migrate and dnsmasq (I have DHCP and DNS on the network))


')
Asus WL 520GU has 5 ports, a WAN port and 4 LAN ports. WAN will look at the provider, LAN1-3 to the local network, and LAN4 I will allocate to a separate VLAN and send it to the DMZ.
1. / etc / config / network, in this file you can specify interface settings.
2. Let's comment out all the lines in / etc / config / firewall except
3. Configuring Iptables, for this we will add to the /etc/firewall.user file
Reboot the router and check the performance settings.
For this finish, the tasks are completed, the traffic runs as I need.
In conclusion, it is worth noting that this solution is very budget and can hardly be considered with large volumes of traffic.
When testing with iperf, the following results were obtained:
iperf server is running in dmz, client in LAN = ~ 36Mb / s
iperf server is running in dmz, client on the Internet = ~ 26Mb / s
For me this is quite enough, the provider gives us 4Mb / s, and the traffic from the local network in the DMZ is not very large.
Thank you for your attention =)
Just now there was a need to hide some service in the DMZ. This service runs in W2K3, and I didn’t want the OS Windows machine to look into the Internet and the local network than anything unprotected (“Windows” firewalls just go through the forest).
Remembering the successful experience with Asus WL 520GU and DD-WRT, I decided to take the beaten track, but chose OpenWRT as the firmware for the router.
Scheme of the ligament can be seen in the figure.

So, from the words get down to business.
Some misunderstanding of the term DMZ was noticed in the comments.
In this connection, I will quote from Wikipedia (for opponents of such quoting, I can see that this material is almost identical to what is written in the book Complete Reference Book on Cisco )
DMZ (Demilitarized Zone, DMZ) is an information perimeter protection technology in which servers responding to requests from an external network are located in a specific network segment (which is called a DMZ) and are restricted in accessing the main network segments using a firewall (firewall ), in order to minimize the damage, when hacking one of the publicly available services located in the DMZ.
We are flashing the router.
For the model I have chosen, the backfire.brcm47xx firmware is required.
1. Perform a hardware reset, the so-called 30/30/30.
When the power of the router is on, press the reset button, hold for 30 seconds, without releasing the button, turn off the power and hold for another 30 seconds, without releasing the button, turn on the power and hold the reset button again for 30 seconds.
Hint: the default ip of the router is 192.168.1.1. If you ping it before a hardware reset of 30/30/30, then ttl will be equal to 64, after resetting ttl becomes equal to 100.
Now send the firmware to the router using the following command
atftp --trace --option "timeout 1" --option "mode octet" --put --local-file openwrt-brcm47xx-squashfs.trx 192.168.1.1Upon completion of the message melting, wait for 5 minutes and turn off / turn on the power router.
The next step is to set the root password and disable unnecessary services, for this we go to the web interface of the router
192.168.1.1
I disabled luci_dhcp_migrate and dnsmasq (I have DHCP and DNS on the network))


')
On this with the web interface we’ll finish, further configuration will proceed from the console.
Asus WL 520GU has 5 ports, a WAN port and 4 LAN ports. WAN will look at the provider, LAN1-3 to the local network, and LAN4 I will allocate to a separate VLAN and send it to the DMZ.
Connect to the router
#ssh root@192.168.0.30
root@192.168.0.30's password:
BusyBox v1.15.3 (2010-11-12 00:01:06 PST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| WIRELESSFREEDOM
Backfire (10.03.1-rc4, r24045) --------------------
* 1/3 shot Kahlua In a shot glass, layer Kahlua
* 1/3 shot Bailey's on the bottom, then Bailey's,
* 1/3 shot Vodka then Vodka.
---------------------------------------------------
root@OpenWrt:~#We need to change a few configuration files.
1. / etc / config / network, in this file you can specify interface settings.
root@OpenWrt:~# cat /etc/config/network
#### VLAN configuration
config switch eth0
option enable 1
config switch_vlan eth0_0
option device "eth0"
option vlan 0
option ports "1 2 3 5*" #default vlan, LAN1-3,
# - 5*, ,
#
#http://wiki.openwrt.org/doc/uci/network/switch
config switch_vlan eth0_1
option device "eth0"
option vlan 1
option ports "0 5" # WAN
config switch_vlan eth0_2
option device "eth0"
option vlan 2
option ports "4 5" # vlan2, DMZ
#### Loopback configuration
config interface loopback
option ifname "lo"
option proto static
option ipaddr 127.0.0.1
option netmask 255.0.0.0
#### LAN configuration
config interface lan
option type bridge
option ifname "eth0.0"
option proto static
option ipaddr 192.168.0.30
option netmask 255.255.255.0
#### DMZ configuration
config interface dmz
option ifname "eth0.2"
option proto static
option ipaddr 192.168.100.1
option netmask 255.255.255.0
#### WAN configuration
config interface wan
option ifname "eth0.1"
option proto static
option ipaddr 1.2.3.4
option netmask 255.255.255.0
option gateway 1.2.3.12. Let's comment out all the lines in / etc / config / firewall except
config include
option path /etc/firewall.user3. Configuring Iptables, for this we will add to the /etc/firewall.user file
#!/bin/sh
ext_if="eth0.1"
ext_ip="1.2.3.4"
int_if="br-lan"
int_ip="192.168.0.30"
LAN="192.168.0.0/24"
dmz_if="eth0.2"
dmz_ip="192.168.100.1"
dmz_server="192.168.100.2"
lo_if="lo"
lo_ip="127.0.0.1"
IPTABLES="/usr/sbin/iptables"
$IPTABLES -P INPUT DROP
$IPTABLES -P OUTPUT DROP
$IPTABLES -P FORWARD DROP
$IPTABLES -N bad_tcp_packets
$IPTABLES -N icmp_packets
#chain icmp_packets ( echo reply[request)
$IPTABLES -A icmp_packets -p icmp -s 0/0 --icmp-type 8 -j ACCEPT
$IPTABLES -A icmp_packets -p icmp -s 0/0 --icmp-type 0 -j ACCEPT
#chain bad_tcp_packets ( iptables #)
$IPTABLES -A bad_tcp_packets -p tcp --tcp-flags SYN,ACK SYN,ACK -m state --state NEW -j REJECT --reject-with tcp-reset
$IPTABLES -A bad_tcp_packets -p tcp ! --syn -m state --state NEW -j DROP
#chain PREROUTING ( destination address IP)
$IPTABLES -t nat -A PREROUTING -p tcp -d $ext_ip -m multiport --dport 8001,31187,20113,20118 -j \
DNAT --to-destination $dmz_server
$IPTABLES -t nat -A PREROUTING -p tcp -d $ext_ip -m multiport --dport 80 -j DNAT \
--to-destination $dmz_server:8001
$IPTABLES -t nat -A PREROUTING -p udp -d $ext_ip -m multiport --dport 20113,20118 -j \
DNAT --to-destination $dmz_server
$IPTABLES -t nat -A PREROUTING -p icmp -d $ext_ip -j DNAT --to-destination $dmz_server
#FORWARD
$IPTABLES -A FORWARD -p tcp -j bad_tcp_packets
$IPTABLES -A FORWARD -p tcp -i $ext_if -o $dmz_if -s 0/0 -d $dmz_server -m multiport --dport 80,8001,31187,20113,20118 -j \ ACCEPT
$IPTABLES -A FORWARD -p udp -i $ext_if -o $dmz_if -s 0/0 -d $dmz_server -m multiport --dport 20113,20118 -j ACCEPT
$IPTABLES -A FORWARD -p tcp -i $int_if -o $dmz_if -s $LAN -d $dmz_server -m multiport --dport 31187,3389 -j ACCEPT
$IPTABLES -A FORWARD -p icmp -i $int_if -o $dmz_if -s $LAN -d $dmz_server -j icmp_packets
$IPTABLES -A FORWARD -p icmp -i $ext_if -o $dmz_if -s 0/0 -d $dmz_server -j icmp_packets
$IPTABLES -A FORWARD -p ALL -i $dmz_if -o $int_if -m state --state ESTABLISHED,RELATED -j ACCEPT
$IPTABLES -A FORWARD -p ALL -i $dmz_if -o $ext_if -m state --state ESTABLISHED,RELATED -j ACCEPT
$IPTABLES -A FORWARD -p icmp -i $dmz_if -o $ext_if -j icmp_packets
#INPUT
$IPTABLES -A INPUT -p tcp -j bad_tcp_packets
$IPTABLES -A INPUT -p icmp -j icmp_packets
$IPTABLES -A INPUT -p tcp -i $int_if -s $LAN -m multiport --dport 22,80 -j ACCEPT
$IPTABLES -A INPUT -p ALL -i $dmz_if -s $dmz_server -j ACCEPT
#OUTPUT
$IPTABLES -A OUTPUT -p tcp -j bad_tcp_packets
$IPTABLES -A OUTPUT -p icmp -o $ext_if -d 0/0 -j icmp_packets
$IPTABLES -A OUTPUT -p ALL -s $lo_ip -j ACCEPT
$IPTABLES -A OUTPUT -p ALL -s $int_ip -d $LAN -j ACCEPT
$IPTABLES -A OUTPUT -p icmp -o $dmz_if -d $dmz_server -j icmp_packets
#POSTROUTING
$IPTABLES -t nat -A POSTROUTING -o $ext_if -j SNAT --to-source $ext_ip
Reboot the router and check the performance settings.
root@OpenWrt:~# rebootFor this finish, the tasks are completed, the traffic runs as I need.
In conclusion, it is worth noting that this solution is very budget and can hardly be considered with large volumes of traffic.
When testing with iperf, the following results were obtained:
iperf server is running in dmz, client in LAN = ~ 36Mb / s
iperf server is running in dmz, client on the Internet = ~ 26Mb / s
For me this is quite enough, the provider gives us 4Mb / s, and the traffic from the local network in the DMZ is not very large.
Thank you for your attention =)
Source: https://habr.com/ru/post/109976/
All Articles