Hacking programs for dummies
 Disclaimer: everything written below is written solely for educational and research purposes, as well as an understanding of the mechanisms for protection against hacking. The author does not recommend using this information for hacking programs.
Disclaimer: everything written below is written solely for educational and research purposes, as well as an understanding of the mechanisms for protection against hacking. The author does not recommend using this information for hacking programs.In this article, I want to tell you about the three and a half main ways of hacking programs on .NET, the goal that I am pursuing is to help developers better understand the protection mechanisms of their programs, i.e. find out the most obvious threats and take appropriate measures (or not to take).
I will not go into details and use sophisticated tools for hacking. Everything will be painted “for dummies”, i.e. All tools will be simple, easily accessible and free. And the main one will be Reflector , a .NET program decompiler
')
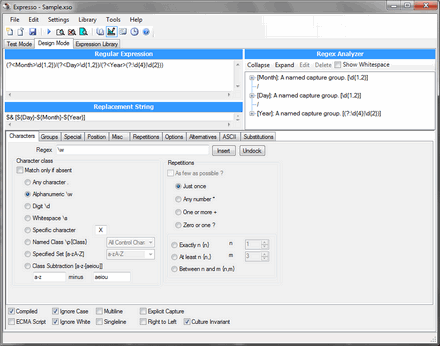 As a guinea pig, I chose Expresso , a regular expression analyzer. This program is free, the license doesn’t seem to indicate anything about hacking, but without registration it will work only 60 days. In other words, the harm of hacking this program is minimal, besides its internal device is very well suited for training. I hope that the author of this program will not be offended at me.
As a guinea pig, I chose Expresso , a regular expression analyzer. This program is free, the license doesn’t seem to indicate anything about hacking, but without registration it will work only 60 days. In other words, the harm of hacking this program is minimal, besides its internal device is very well suited for training. I hope that the author of this program will not be offended at me.For a start, a brief educational program for the .NET program structure, for those who are not familiar with the development under this Framework: all code written in any .NET language (C #, Visual Basic, F #, Delphi.NET) is compiled into a special Intermediate Language, usually called IL or MSIL . This is something like an assembler, only very clever and possessing very powerful instructions. And this is, in principle, the same equal language as C #, only the syntax is worse (and there are more possibilities). In addition, metadata is actively used in the .NET program, i.e. all information about classes, methods, attributes, attributes, and everything else is stored in an executable file.
Those. in fact, decompiling a program is not a very correct concept in this case. It already lies in its entirety in open form, and tools in the form of a Reflector are engaged in bringing the MSIL constructions to the corresponding constructions of C # or another language, increasing the readability of the code.
Let's move, in fact, to hacking.
0. Reset Trial
Actually, this is not even a hack, but a semi-legal way to extend the life of a non-activated program. It lies in the fact that there is a place where the date of the first launch is stored and changes / is destroyed. After that, all can use the program until the next term.
Let's look at our experimental reflector:
Having a little walk on the code, we find an interesting line in the MainForm constructor
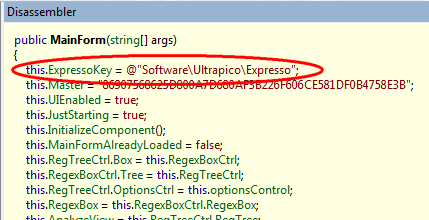
Open the registry editor, go to HKEY_CURRENT_USER \ Software \ Ultrapico \ Expresso and see the following keys:
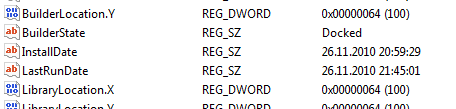
Remove them and get another 60 days of work.
This option, of course, is simple and obvious, but if it would even be more difficult, it would take a little more time in the reflector to find out all the places where the information is written and clean them.
Advice to developers who will try to write data to a hidden place: write carefully, otherwise it can turn into problems for ordinary users who for some reason will not have this place or will not have enough rights for it.
1. Writing a keygen
The most terrible option for the developer, and the most pleasant for the end evil user. The program considers itself licensed, no terrible gestures do not need to be done.
Open the reflector and look for the code for classes containing a License or Registration, we see:
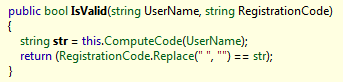
When you enter a name and a code by name, a certain hash is calculated, which is compared with the code.
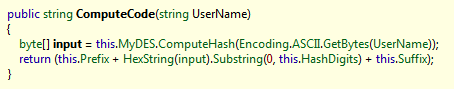
This hash uses DES and any prefixes.
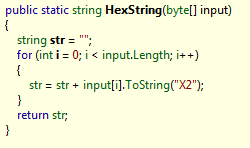
Bytes are converted to a string using this method.
Now everything turned out, open the IDE and copy all the necessary pieces of code (or implement them yourself). It remains only to find out what the values of Prefix, Suffix and the parameters of the MyDES implementation. I will not bring them, these are already technical details.
As a result, we generate a key for any name and see:
Bingo!
Protection against keygens is simple and obvious: use asymmetric encryption in any form. Those. to make it so that without knowing the private key it would be impossible to generate the code, and this key is only in one place - the author of the program.
2. Using Wrapper
Checking the correctness of the license is quite troublesome and slow. Therefore, software developers usually check the license once, and then use the received flag - valid / invalid (as an option, how valid, if several types of licenses are allowed, differing in capabilities). Here you can play on this, using the following algorithm:
- Tell the program that the license has already been verified.
- Indicate to the program that the license is correct.
How to do it? I have already mentioned the presence of metadata in executable files at the beginning, and we will use this. Let's see how the program starts and how the license is checked:
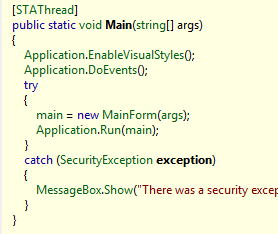
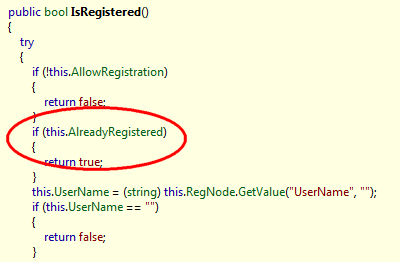
With the launch of nothing interesting, and the check shows that if the program is already registered, then she believes that everything is fine and does not do any further work on finding out the correctness of the license.
We use this:
Let's make a new project, add a Reference to Expresso.exe and run it through ourselves:
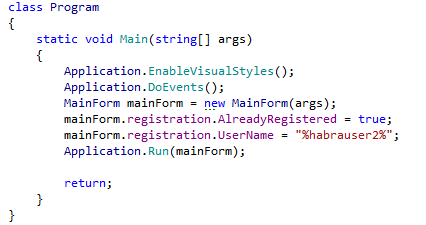
Look what happened:

Well, who would doubt.
In this case, everything turned out to be simple, but if the author of the program had replaced public properties with private ones, then all would have to use Reflection for access and everything would be reduced to the original problem.
I think it is clear how you can try to defend yourself against this — check the license periodically, watch the environment from which the program is running, make it impossible to set the desired variable.
But all these defenses will result in the attacker using
3. Physical hacking program
Everything is serious here. The program is completely decompiled in MSIL and is already going back from it (remember, I wrote that MSIL is the same language as C #?). To decompile, we need a utility from the SDK called ildasm , and to compile, the compiler from the .NET Framework is ilasm .
Run ildasm, open Expresso.exe and save the dump to an .il file. We find the already discussed IsRegistered method and add a little bit of our code (without labels):
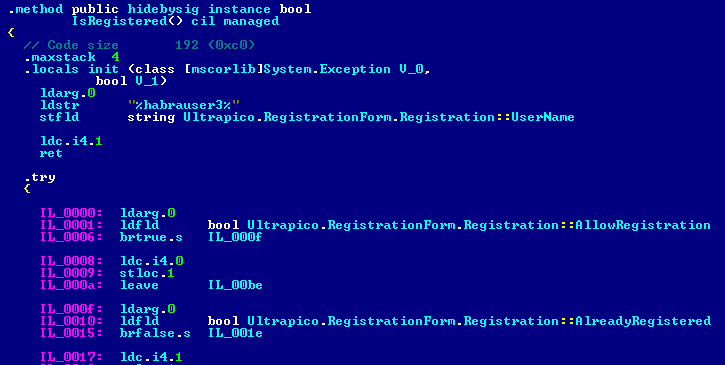
Then we take ilasm and collect everything back (without forgetting to connect resources).
What this code does: sets the desired name for registration (optional), and returns the status that everything is fine.
To make it clearer, it looks like this in a reflector, in C #
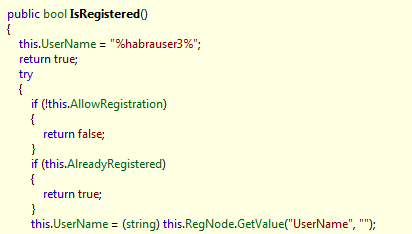
Those. it is quite obvious that now everything will be fine:
A little about the code in MSIL: this is a stack machine that does not have registers, all operations look like: push the required number of parameters onto the stack, execute a function that takes the required number of parameters and puts the result. Well and back: set the value of a variable by what lies in the stack. To better understand the work of all this, I recommend a simple technique: write a small program in a familiar language, compile, see what happened in MSILe and understand the language constructs.
At the same time, some things in MSIL can be done very nicely, for example, change two variables in places - 4 nice lines (in C # less, but not nice).
What an attacker sacrifices: the signature of the program, now it is no longer the author, but his. In some cases, this is a problem if the program uses many libraries. Then the evil hacker will have to disassemble them all and reassemble them, but if he copes with this, he will have “his” version of the program signed with his key.
There is actually little protection against all this disgrace: obfuscation or carry out a part of the logic / protection check in the native code.
Conclusion
I think I told you how easy it is to break everything into .NET if the creator has not made any effort to protect his program. And you really decide whether to do the protection and spend time and resources on it. Or maybe just make a web-system, or a free limited version. Solve the developers.
Source: https://habr.com/ru/post/109117/
All Articles